
Introduction
We all learn at a very young age to analyse – either consciously or unconsciously – other people’s body language and intonation. Research shows that about 60% of the time, we pay more attention to a person’s body language than what they are actually saying, and we use this information to draw conclusions about how truthful a speaker is being. These conclusions are vital in helping us avoid falling victim to scammers, fraudsters or anyone else trying to manipulate us. But fraud and deception aren’t just a threat in real life – a range of virtual scams have been increasing significantly on the Internet for some time now. This means we have to take a new approach to evaluating possible threats; there’s no body language or intonation involved in email or social networks, and generally we only have text and graphics to guide us. So does this mean that we can no longer rely on gut instinct?
This would appear to be the case, at least on the face of things. However, the Internet does offer other aspects which can be interpreted and compensate for the gut instinct we feel is lacking; however, for this to work, we need to learn what to watch out for. Cybercriminals and scammers are unlikely to reinvent the wheel, so once you’ve encountered a scam or threat once, and have learnt that it’s a scam, you can use this information in the future. This article therefore focuses on some typical examples, and explains how you can protect yourself. This article is primarily aimed at those who are new to the Internet, but who knows, maybe the examples given could also help Internet veterans learn a thing or two.
Classic email threats
If you’re new to the Internet, probably one of the first things you’re going to do is set up an email account. Not only do you want friends and family to be able to contact you, you’ll need a valid email address if you want to buy things online or sign up for forums or social networks.
Unfortunately, just as your mailbox at home can get crammed with advertising fliers which you never requested, your email address can also get filled with unwanted messages. Up to 89% of all emails sent are what is known as spam: messages you never asked for which offer you cheap credit, discount Viagra and a wide range of other products and services. These offers are in no way legitimate, and often the messages will contain links to websites which are infected with viruses, Trojans, or other nasty programs. You should delete the messages without reading, and then they won’t be able to damage your computer – the only thing you will lose is the time you spend deleting them.
It’s easy to say you should delete these emails, but sometimes they just look too tempting to throw out. Cybercriminals are smart: they’re particularly active around major holidays such as Christmas, Easter, and of course Valentine’s Day. The latter in particular is a golden opportunity for the bad guys – it’s traditionally the day where you can admit your feelings for someone without embarrassment, even if that person is just a distant acquaintance. So if you got an email on Valentine’s Day with the subject ‘I love you’, would you open it?
It’s not only holidays and hot topics that the cybercriminals make use of. The Internet is often described as the ultimate in entertainment media, and there are lots of sites dedicated exclusively to amusing articles, images and videos. We all love a bit of distraction, and cybercriminals play on this, sending messages with intriguing subjects like ‘Check out this funny video!’ or ‘Funny photo!’ But you should resist the temptation to open the file that’s attached to the message: it’s 99.99% likely to contain programs which can damage the data stored on your computer, spy on your online activity, and/or defraud you in some way. In her article, “Spam evolution: June 2009”, my colleague Tatyana Kulikova stated that 0.31% of all emails sent on the Russian Internet have malicious attachments. This might not appear to be a particularly high percentage, but given that 500,000 types of spam are sent every day, the total number of messages is going to be fairly large, especially when you consider that any one spam message will be sent to millions of email addresses.
Phishing
Probably one of the best-known scams is phishing. You receive an email which asks you to go to a site (the link is given in the email) and enter some personal information – this might be a password, a bank account number etc. The email might look as though it’s come from your bank, from eBay, from a payment system like PayPal etc. However, no matter how convincing the message might look, it’s a fake; if you click on the link and enter the information requested, cybercriminals can get hold of your data and use it for their own ends.
A lot of banks have now put additional security measures in place to combat phishing attempts, and this means that phishing emails which target the most widely-used banks are on the decline. However, this doesn’t mean that this type of scam isn’t being used anymore – it’s simply been modified to keep up with the changing times.
Phishing emails are an international phenomenon: a basic text gets translated into a range of languages, and an email is then designed to imitate the look and feel of a well-known bank or financial institution. Most of the effort goes into the design of the email, and the logos and colours used are often difficult to distinguish from a genuine communication. The text, on the other hand, is likely to be riddled with spelling and/ or grammar errors: an instant red flag. Additionally, emails that start “Dear customer” rather than using your actual name are a strong indication of a phishing attempt; these days, where even newsletters can be personalized, a legitimate communication is unlikely not to use your name. And finally, legitimate banks never request PIN numbers, TAN numbers or other sensitive information, and certainly not via email.
As mentioned above, it’s not just banks which can suffer from phishing attacks. Recently, a large number of phishing emails are designed to harvesting account data for online payment systems such as PayPal or auction sites such as eBay. Phishing mails make up 0.94% of all spam, and an incredible 60% of these messages target at PayPal. Phishing emails of this type often threaten with closure of your account, because allegedly it’s not been used for some time. To retain your account, the message says, you should log in; and of course, there’s a handy link provided in the email. If you click on it, you’ll see a page which looks like the site in question, and it asks you to enter your user name and password. Although it might look like the real thing, this website is a fake. You should never use links in emails which lead to a page where you’re requested to enter sensitive information. Use the bookmarks in your browser or enter the address yourself in the address line of your browser. Even if the link appears to be legitimate, JavaScript in the background can open a completely different address to the one displayed.
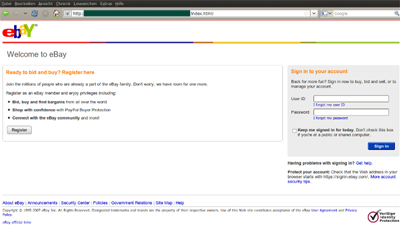
Figure 1: Even better than the real thing? An eBay phishing site
If you’re unsure if an email is valid or not, call the company in question directly or send them an email asking if the email is genuine. However, if you choose to contact a company via email, don’t just reply to the dubious message: check the company’s website for a contact address and use this instead. This ensures that your query goes to the company itself and not to an invalid return address used by scammers or spammers.
Who wants to be a money launderer?
In the current economic climate, lots of us are looking for jobs, so news of vacancies is always welcome. Suppose you get a job offer via email, which promises a good salary for a job that allows you to work from home and that requires minimum time and effort. Even if you’ve already got a good job, the idea of making an extra €1,500 to €2000 each month is obviously appealing. So what do you need to do? Simply receive sums of money from account A and transfer these to account B via Western Union, minus a certain percentage which you keep as commission.
Sadly, if something appears to be too good, it’s usually just that. The sums you’re being asked to transfer comes from phishing or other scams; your role is to ensure that the money reaches the scammers and cybercriminals account by a convoluted route. This makes the criminals far less easy to trace, but the transaction you’ve made will be very obvious. By completely such transactions you’ll become what’s known as a money mule, and guilty of money laundering or of aiding and abetting criminal activity. If you get caught, you could face a hefty fine and potentially, a criminal record. So once again, the best way of dealing with these emails is simply to hit delete, no matter how tempting the offer might sound.
Scareware
Imagine this: you’re browsing websites looking for new wallpaper for your desktop. Suddenly a message pops up telling you that your computer is infected with 527 Trojans, viruses and worms. This might seem strange; you’ve got security software on your computer, and it’s not said anything about infections or threats. Maybe it’s not working properly? Or it’s overlooked something?
Once the initial shock passes, you take a closer look at the message. It says you can download new antivirus software that will solve your problem. And best of all, the software is free! Relieved, you take advantage of the offer, download the program and install it. You run the virus scan again manually, only to find that the software has now found even more infections and this time you’re shown a different message: the malware can only be removed by the full version of the product which you have to purchase. A quick look at the website reveals prices between €30 and €80. As the security software you installed initially seems to have let you down, you pin your hopes on the newly-discovered “miracle solution”, but it, and click on “Disinfect”. All the threats seem to be quickly eliminated…. or are they?
This is a scam that’s become well-established; it plays on your fear that your computer is seriously infected. The approach taken by scareware programs of this kind can differ. The most common approach is that while you’re surfing the Internet, you get shown a popup window which appears to be carrying out a scan of your hard drive. It then shows a randomly-generated number of malware infections. A slightly less common approach is called a drive-by-download: you’re surfing an infected website, and a piece of unwanted software gets onto your computer. In the case of scareware, the software would frequently display messages informing you that your machine is infected. Even your wallpaper may get changed to remind you of the infections (which, it should be remembered, don’t actually exist). Changing the wallpaper back to the original image is a challenging task; the option to do this is removed from the settings menu, and although there are other ways to do this, they involve more technical knowledge than many people have. So what initially appears to be a “miracle solution” turns out to be software which doesn’t have any benefits for the user.
However, scareware does have benefits for the cybercriminals: they can make money from selling licenses for this fake security software. Additionally, such fake software often includes clearly malicious software which can be used to gain access to your machine, steal your personal data (which can then be resold) or turn your computer into a zombie machine which can be used to send enormous amounts of spam. Although this last might not seem to be obviously profitable, spammers will pay good money to buy or rent such machines to ensure that their messages are widely distributed – it’s just one more way to make money in the world of cybercrime.
The name scareware is entirely justified; a lot of effort is put into making sure firstly that the messages are convincing, and secondly that the scareware programs themselves look genuine. In addition, such programs often have names which sound similar to the names of legitimate security applications. This all helps to initially lend the scam an air of respectability which can fool even more experienced Internet users. So what should you do? Make sure you’ve got a reputable antivirus solution installed. If you start seeing messages like this, don’t be frightened, and certainly don’t buy the software on offer. Use your current security solution to run a full system scan.
Buyer beware: the danger of hidden subscriptions
These days, freeware – software which you don’t have to pay for – is available for almost every purpose imaginable. There’s something for everyone – games, media players, instant messenger clients etc – and a number of places where you can these programs. Let’s say you’re looking for new software for office purposes – word-processing, spreadsheets, etc. You run a search, and your search engine gives you a large number of options. The first sounds promising; a website that’s got the files you need, and it appears to be legitimate, so you click without giving it any further thought. However, before you can download what you want, the site requires you to register by entering your name, address and a valid email address. Although you think this is a bit unusual, you’ve heard of download portals where you have to register in order to benefit from the full download rate. So, a little irritated, but well-versed thanks to having registered with various online shops, social networks and forums in the past, you enter the requested data in the fields provided. You quickly activate the checkbox indicating that you agree with the terms and conditions; you don’t bother actually reading these, because after all, they’re always the same. A moment later, you’re happily downloading the program you need.
But a little while later you get a nasty shock in the form of an email demanding that you transfer €96. In agreeing to the terms and conditions, you’ve taken out a 2-year support subscription. If you don’t pay up, legal action will follow.
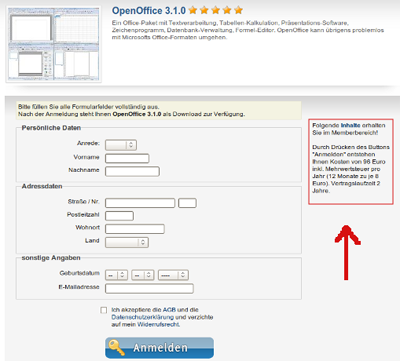
Figure 3: Buyer beware: hidden subscription
It’s estimated that 10 to 20% of victims pay up (http://www.netzwelt.de/news). However, you shouldn’t let yourself be intimidated by threats of this kind. This type of scam attempts to extract money by playing on people’s fear of the law. After all, you know that you didn’t read the terms and conditions (perhaps because you realized you had little chance of understanding them, or perhaps because you’ve never heard of any negative consequences). If you get an email like this, do some research: try and find similar cases on the Internet, or call your lawyer. It’s likely that the threat either has no legal force, or will remain just that – a threat – because the cybercriminals are content to get money from the 10 – 20% of victims that do pay up.
Scams on social networking sites
Young people in particular are attracted by social networks such as Facebook or MySpace. These sites means you can keep in touch with existing friends, exchange information, and also search for new friends.. However, there are also social networking sites for older users; you can use these to make and maintain business contacts or search for old school friends.
Whatever site you use, there are dangers here as well. Suppose a close friend asks you for help – you’ll probably say yes immediately. Now transfer this situation to a social networking site. A friend sends you a message on the site telling you he’s stuck at Heathrow, has been robbed and threatened with a weapon. Now he’s got no money, credit card or plane ticket, and he asks you to transfer $400 via Western Union so he can get home. You might hesitate a bit; why does the money have to go by Western Union? Your friend insists this is the only way that he can access the money. You ask if you can call him, but apparently the thieves have stolen his mobile phone as well. You gradually become more and more suspicious – your friend seems to be behaving in a peculiar way, and he’s using words and phrases you’ve never heard him use before. Maybe that’s just because he’s in such a stressful situation. Since you’re worried about your friend, and you don’t want to have a bad conscience, you eventually transfer the money. And then you don’t hear from him again.
So what’s actually happened? This type of scam is currently very popular and very effective because it’s relatively unknown. The explanation is quite simple: cybercriminals have gained access to your friend’s account and are trying to get money from all his contacts. If you use social networks a lot, you could have hundreds of friends, and you won’t always know where each person is, which makes the story more believable.
However, there are also clear signs that fraud is being attempted in the case described above. A European stuck in London would hardly ask another European for US dollars. The same applies to the language and phrases used. If you get a message like this, make sure you contact your friend directly. Even if he says in his message that his mobile has been stolen, try calling it: you’ll be pleasantly surprised when he picks up the phone, and not only will you get to chat to him, you’ll also make sure that the message you received was not genuine.
If you want to protect your own social network account(s) from being abused in this way, you just need to follow a few simple rules. One possible way of securing your account relates to the method for resetting your password. When you register on a social network, you often have the option of answering a “secret question”. If you forget your password, you can generate a new one by entering the answer to the question. Usually, you can only choose from three “secret questions”, which are very general – for instance, the name of your pet, or the first school you attended. If you’ve included any of this information in your profile or on your page, accessing your account will be child’s play.
In order to make your account more secure, remember that you can modify the question and answer at any time. Make sure you keep your login and password to yourself. Additionally, make sure you don’t fall victim to phishing attacks (described above) and use an up-to-date antivirus solution: this will keep your computer clean of Trojans which might steal your password and send it on to cybercriminals.
Twitter – the dangers of short URLs
Since 2006, Twitter has grown enormously. More than 25 million users want to know the answer to the site’s slogan “What are you doing?”, Twitter is a social network with a difference – the micro-blogging format limits messages to 140 characters, and this makes it difficult to include URLs which would take up a good 50% of the available characters. And this is where less well-known Internet services come in: ones which convert long, convoluted addresses into a significantly abbreviated form. These URL shortening services have their drawbacks: it’s difficult to tell where a short, cryptic URL actually leads, and this means that transparency suffers.
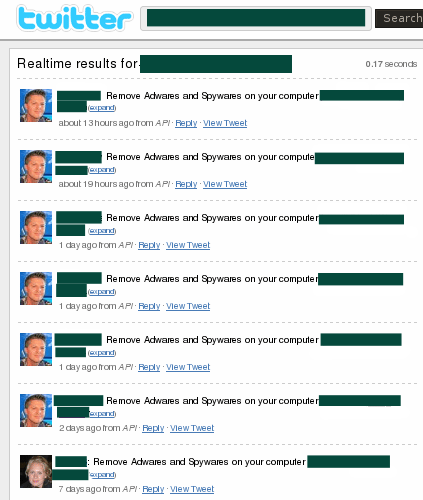
Figure 4: Messages sent automatically via Twitter which include shorten URLs
Cybercriminals have seized this opportunity, and use these services to convert addresses leading to infected websites into short form. Such messages can be spread automatically, and promise the truth about some sensational news, such as the death of a celebrity (e.g. Michael Jackson). When there’s no sensational news, the cybercriminals just invent something – for instance, the supposed death of Britney Spears was widely broadcast on Twitter, even though the singer was alive and well.
Such messages containing links to infected sites are simply a more evolved version of email scams – they’re trying to take advantage of your curiosity. Unfortunately, this type of cybercrime shows that short URLs simply can’t be trusted. You can protect yourself by using add-on tools: for instance, a popular plug-in for Firefox will reconvert a short URL to the original format when you hold your mouse cursor over the link. This gives you a good idea if the link leads to a reputable site or not.
Films, games, music…and malware
If you’re new to the Internet, the first things you might look for are films, music, TV programs or computer games. Apart from the legal aspects of downloading such content – which have been extensively detailed by others – there are other issues to consider. If you’re looking around for content like this, you might think that so-called peer-to-peer networks offer the quickest route. So you download a program which will help you access the network and start helping yourself to what you want. Although you might have read somewhere that these files might come with malware attached, you just ignore this. However, you do this at your own risk.
For instance, games available for download often contain crack tools which can be used to circumvent copy protection. These tools are provided by hackers, either because they believe that all content should be free, or because they want to make an impression on the hacker scene. And download files may come with associated malware; cybercriminals know there’s a big market for free content, and by disguising their malware as popular files, or adding their malware to popular files, they’re increasing the number of potential victims. For instance, a banking Trojan might come with a game download – although young people rarely use online banking, the computer they download the file too might belong to their parents, who regularly check their account online. This approach therefore kills two – or more – birds with one stone.
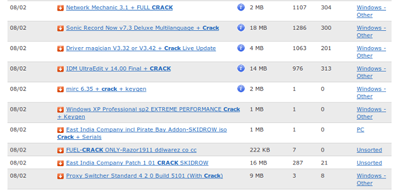
Figure 5: Crack tools on a Bit Torrent site
The chance of downloading malware via a peer-to-peer network is relatively high. So while illegally downloading a game or film may save you the purchase price, downloading a Trojan designed to steal your banking details could cost you hundreds of Euros, which quickly puts any anticipated financial gain into perspective. There’s no doubt here that honesty is the best policy.
Conclusion
Cybercriminals are very creative and are constantly adapting their scams as new Internet technologies and applications evolve. Mostly, this is a case of old scams being recycled to target new media. The best example of this is the classic spam message which contains a link to a malicious website. By now, lots of people know that you should never click on a link in an email from an unknown sender. However, when their approach was adapted to messages sent via social networking sites, the number of people who clicked increased enormously.
A few years ago, the design of a website could make it clear that the site was a fake: spelling mistakes, poor layout, etc. Now, however, cybercriminals have become far more sophisticated. If you suspect a scam, use a search engine to try and uncover further information; if there is a scam involved, other victims will probably have written about it. Search suspicious sites for contact information, and then verify this against other sources.
Finally, use your common sense. As stated above, anything that looks too good to be true probably is. If something sets alarm bells ringing, pay attention to your Internet instincts. A healthy dose of scepticism will go a long way in helping to protect you against fraud and scams: a reputable security solution and up-to-date software will take care of everything else.
Traps on the Internet






















Tonya McKelleyAllen
I found a few mistakes in the article I just read. Warning me to look out for misspelled words and a sentence or two with the wrong language use. Is this a spam example?