
Over the last few months I have been closely monitoring so-called Darknet resources, mostly the Tor network. And one thing that is immediately obvious is that the cybercriminal element is growing. Although, the Tor infrastructure and cybercriminal resources are not on the same scale as the conventional Internet, we managed to find approximately 900 hidden services online at the current time. There are also approximately 5,500 nodes in total and 1,000 exit nodes, but the possibility of creating an anonymous and abuse-free underground forum, market or malware C&C server is attracting more and more criminals to the Tor network.
Malware
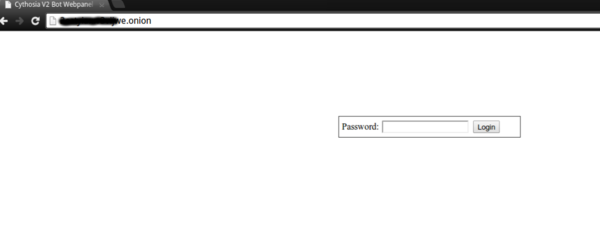
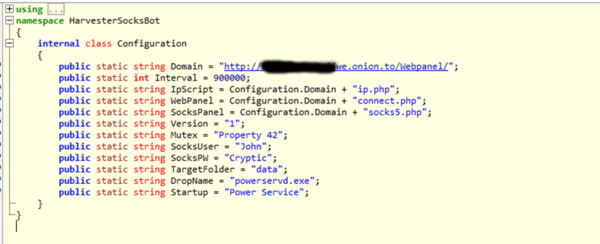
Cybercriminals have started actively using Tor to host malicious infrastructure. We found Zeus with Tor capabilities, then we detected ChewBacca and finally we analyzed the first Tor Trojan for Android. A quick look at Tor network resources reveals lots of resources dedicated to malware – C&C servers, admin panels, etc.
Hosting C&C servers in Tor makes them harder to identify, denylist or eliminate.
Although creating a Tor communication module within a malware sample means extra work from the malware developers, there will be a rise in new Tor-based malware, as well as Tor support for existing malware.
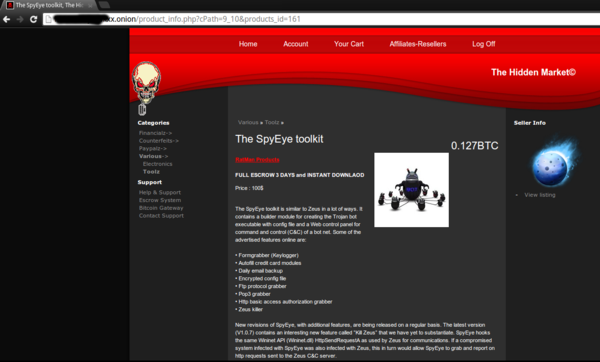
Cybercriminal forums and marketplaces are widely known on the Internet. Some of them are public, some are private and you need the approval or an invitation from an existing member or need to be a respected personality in underground scene. Now another layer has been added – Tor underground marketplaces. It all started from the notorious Silk Road market and evolved to dozens of specialist markets: drugs, arms and, of course, malware.
A simple registration procedure, trader ratings, guaranteed service and a user-friendly interface – these are standard features of a Tor underground marketplace. Some of the stores require sellers to deposit a pledge – a fixed sum of money – before starting to trade. This is to ensure that a trader is genuine and his services are not a scam or of poor quality.
Financial fraud
Carding shops are firmly settled in the Darknet. Stolen personal info is for sale with a wide variety of search attributes such as country, bank etc. Tor credit card online shops that have been criticized by cybercriminals for bad quality or for being fake can find a second lease of life in the Darknet.
Offers are not limited to credit cards – dumps, skimmers and carding equipment are for sale too.
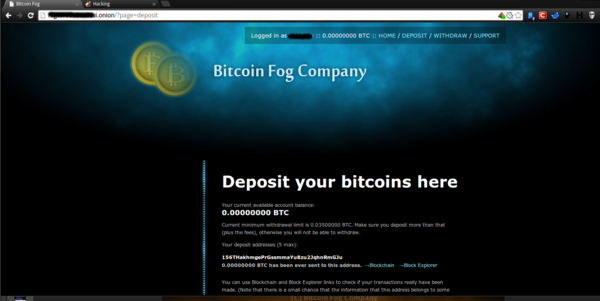
Money Laundering
Bitcoins play an important role in underground financial operations. Almost everything on the Tor network is bought and sold using bitcoins. Although iIt’s almost impossible to make a connection between a bitcoin wallet and real person, it is possible to: track bitcoin transactions as all of them are transparent and public, to build up a scheme of what’s going on, and find out the most valuable transactions made via bitcoin exchange services. That’s why money laundering services exist on Tor. Cybercriminals can create an account, deposit bitcoins and they will be broken up into various quantities, transferred through dozens of different wallets to make any investigation highly complicated.
Conclusions
- A growing number of Tor hidden services and the ease with which they are can be deployed attracts more and more cybercriminals in the Darknet.
- Malware developers are using Tor more and more for a variety of malware-related tasks
- Financial fraud and money laundering are important aspects of the Tor network.






















Tor Hidden Services – a Safe Haven for Cybercriminals