
We’ve noticed an increase in the prevalence of Y!/MSN-aware worms. These rely on various social engineering tricks to lure the user into a malicious website. For instance, IM-Worm.Win32.Qucan.c sends messages like this:
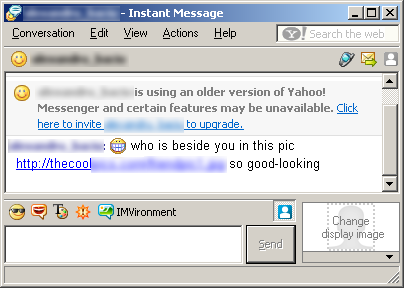
The link shows a URL nicely disguised as a JPEG file. The actual page, which contains an encrypted javascript to avoid direct inspection, uses a combination of Exploit.JS.ADODB.Stream.e and a more recent MDAC (MS06-014) exploit to install the worm in the system. Unfortunately, even though a patch for the MDAC exploit had been released in May 2006, we have quite a few Qucan.c/Sohanad.e cases reported.
Of course, if you have Firefox or Opera set as the default browser, the exploit doesn’t work.
BTW, if you’re still – for some obscure reason – using IE, it may be worth checking v7, which was just released. It works only on XP+SP2, though.






















The IM worms armada