
- Computer security as a system
- People are part of the system
- Security vulnerabilities and some examples
- Conclusion
This article has not been written in order to scare users, or to push them into buying security software for their computers. It’s simply an attempt to share some thoughts which have come to mind in my work as a virus analyst, while analysing code, reading a range of forums and articles, and numerous daily messages from readers asking for help.
Computer security as a system
Information security cannot be thought of as a single, discrete, entity; it’s a whole range of measures, and should be viewed as a system. Information security is as complex as any other system which combines a number of different aspects and approaches, none of which can be regarded as more or less important. This means that no single aspect or approach can be disregarded; if one area or part of the system is ignored, the system will not function correctly.
Information security differs very little from security in general. After all, no one would install a heavy security door with a pick-proof lock on a garden shed. Similarly, a car can have excellent tires, but if the brakes are faulty, the car will be unsafe. Protection against cyber threats works on the same principle: all possible weak points should be secured, whether on a desktop computer, an organization’s server or a corporate network. Data should also be accessed via secure paths, although I’m not going to discuss how any of this should be done in this article. Those who work with information should also be viewed as a part of the system, a link in the chain which ensures both data exchange and the security of the system overall.
People are part of the system
There’s a wide variety of security software available, including firewalls, intrusion detection systems, antivirus solutions etc. Each type of software is designed to perform very specific functions, and using such software will help protect a system. However, even using the very best software, which implements the most advanced technology and the most secure algorithms, cannot guarantee 100% system security. This is because people are involved in the development and implementation of software, and people make mistakes. Consequently people, who are a part of any system, are always going to be the weak point in a security system.
The human factor is the underlying reason why many attacks on computers and systems are successful. Of course, there are a great many specific examples. Let’s take a look at how and why hackers, virus writers and other malicious users exploit the human factor, using people as the chosen method to penetrate systems.
Security vulnerabilities and some examples
A lot of users don’t understand that using software which contains vulnerabilities poses a genuine security risk to their computer or system. The majority of users see their computer as a black box; they don’t understand how it works, and in reality, they don’t really want to. They want to use computers in the same way as a vacuum cleaner, a fridge, a washing machine, or any other household appliance, without having to understand how the appliance performs its function. And many users think that viruses, hackers, and other cyber threats are simply the invention of security software vendors. In some ways, who can blame them, given that some of those working in the security industry regard viruses as ‘something that happen to stupid users’ and antivirus software is simply a waste of money. “I’ll simply install an operating system which isn’t susceptible to viruses, and software without any vulnerabilities, and then I’ll have nothing to worry about” so goes the theory.
Underestimating the severity of potential threats is only part of the problem, however. The human factor also comes into play in creating and implementing security policies and procedures, and many potentially exploitably loopholes appear at the drafting stage.
The security of wireless networks is in a lamentable state due to the fact that errors were made when wireless protocols were being developed. There are as much written about secure programming as there are program errors; however, I’m sure while programmers and testers will continue to identify loopholes which already exist, new ones will continue, albeit inadvertently, to be created. And even the most carefully developed software has to be implemented, which again brings humans into the equation: the best firewall in the world will not protect your system if you have a poorly trained system administrator.
While I was writing this article, a worm was gaining ground on the Internet. Lupper spreads via known vulnerabilities, and if an administrator regularly reads vulnerability alerts and installs patches promptly, the system won’t be vulnerable to Lupper. This is standard for all worms. The usual scenario is that a vulnerability advisory is issued, but most people don’t pay much attention to it; then proof of concept code is released showing how the vulnerability can be created, but the majority of users still don’t understand the gravity of the situation and take no action. Lupper follows this pattern, and confirms the fact that security issues are not taken seriously enough at an early stage.
Another example of an irresponsible approach to security is how users treat confidential information. An analogous situation in everyday life: who would leave their keys in the outside lock, or hang them on a hook where anyone could take them? No-one, of course. But lots of systems use an empty password, or the users’ name as a password, making it extremely easy to access the system. As an alternative, let’s take the scenario where the administrator requires users to have passwords which are difficult to guess, and therefore better from a security point of view. This is all well and good, in theory, but I’ve often seen such ‘secure’ passwords written on a piece of paper and left lying on the user’s desk, or stuck to the monitor. It’s not surprising that malicious users take advantage of this situation.
Another human failing which malicious users exploit to the full is curiousity. The vast majority of us have encountered email worms at some time and know that these worms arrive as attachments to infected messages. Sending the worm out is only half the battle, however, for the virus writer or malicious user. The worm then has to be activated in order to spread further, and this is done by opening the attachment. You might thing that users have become wary of attachments to unexpected messages, and consequently don’t open them. Unfortunately, the cyber criminals and vandals know how to pique users’ curiosity. An intriguing message referring to the attachment will be opened by the majority of users, as the graph below shows:
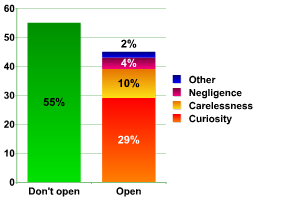
Why do you open suspicious attachments?
Interestingly, in spite of the fact that antivirus vendors constantly stress that suspicious attachments shouldn’t be opened, the number of users who open these attachments remains stable. This can be explained by the fact that virus writers are constantly finding new ways to exploit human curiosity and gullibility.
However, email worms don’t only spread attached to messages. Recently, users have been receiving a ling to the body of the worm, rather than the worm file itself. The user is still part of the activation process, and has to be persuaded to click on the link in order to launch the worm. It seems that this is very simple: let’s take Email-Worm.Win32.Monikey, which sends emails like the one shown below:
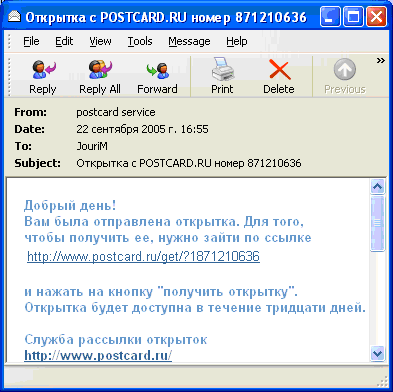
Email sent by Email-Worm.Win32.Monikey
At first glance, this seems to be a perfectly normal email, telling the user that s/he has received an e-greetings card. It’s logical for the user to click on the link in order to view the card, and the malicious users who have sent the email are counting on this: the unsuspecting user, in trying to view the alleged card, will launch the worm. So what is the answer? How can malicious emails be distinguished from genuine emails? The screenshot below is a legitimate email sent out by the POSTCARD.RU service:
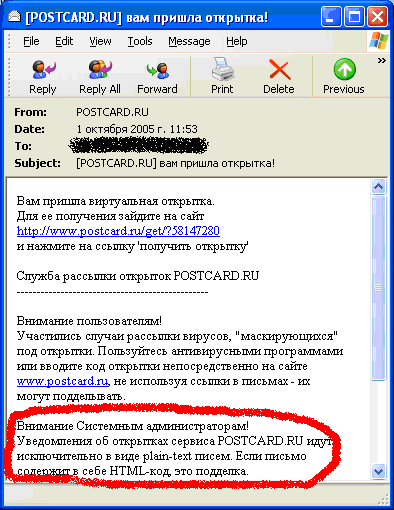
Email sent by POSTCARD.RU.
Firstly, it should be highlighted that the email shown in screenshot 1 uses HTML code – this is used to mask the URL of the address where the worm is place, making it appear to be a link to POSTCARD.RU. Screenshot 2 shows the email from POSTCARD.RU which includes a warning, stating that all emails from POSTCARD.RU are in plain text only; any message containing HTML is not legitimate, and potentially malicious. If the user wants to view their card, they should copy the link into their browser – a genuine link will then cause the e-card to be displayed. Under no circumstances should users click on HTML links; in this case, as in many others, this opens a site containing malware, which will then be activated.
A similar approach has been used recently in a spam mailing. Messages stated ‘If you wish to unsubscribe from our mailing list, please click on the link below’. You might ask what the problem is – of course users don’t want to receive mountains of spam, and will try and use the link to unsubscribe. When the user clicks on the link, an HTML page is opened, which alledgedly checks the subscriber database, and then displays a message saying ‘Your address has been removed’. However, this is all an illusion – in actual fact, two malicious programs will be downloaded to the victim machine:Trojan-Dropper.Win32.Small.gr and Trojan-Spy.Win32.Banker.s. There’s a clear lesson here – spammers are not going to worry about users wants and needs, and once they have got hold of an address, that address will receive spam regardless of any attempts to unsubscribe. In fact, attempts to unsubscribe usually result either in more spam, or in malicious code being downloaded. The best way to deal with spam is simply to delete the unwanted messages.
The summer of 2005 brought a new type of mass mailing, with cleverly designed emails which targeted a clear group. Malicious users started spamming corporate email addresses with messages appearing to come from the user’s manager. This was done by spoofing the address field. However, the real return address, which couldn’t be seen, was the malicious user’s address. Of course, conscientious employees are highly likely to do as they are told by their manager, and would therefore open the attachment and launch the malicious program. It should be noted that such incidents don’t receive much publicity; those responsible for security in organizations which are targeted usually attempt to prevent the information from reaching the wider world.
When malicious code is mass mailed, the senders often play on the popularity of antivirus solutions. This kills two birds with one stone: the user launches the malicious program, and antivirus vendors are discredited. This last point should be emphasised – if users receive enough messages appearing to be from antivirus companies, sooner or later they will start to think that the antivirus companies are sending out infected updates, and will stop updating their antivirus solutions. This, of course, makes antivirus software lose most of its efficacy. It must be stressed that no antivirus company distributes updates via mass mailing, and users should not install programs which arrive by email on their machines. Email-Worm.Win32.Swen successfully used this approach by presenting itself as a security patch issued by Microsoft. The worm managed to infect several hundred thousand computers around the world as users installed the alleged patch. The worm’s authors had carefully waited for the moment when users would be most likely to install a security patch, having been frightened by the recent Lovesan incident.
This case shows how virus writers exploit events in the world at large in order to infect more machines. They do this extremely quickly and effectively – recent cases include mass mailings of Trojans following the terrorist bombings on the London underground, the power cuts in Moscow, and Hurricane Katrina in the USA in 2005. The messages sent made reference to these and other disasters in order to entice users to open attachments or click on links.
Malicious code for instant messaging programs (ICQ, Miranda etc.) takes a very similar approach.
How do computers get infected by instant messaging malware? More often than not, the malicious user sends a link to the body of the worm, which is activated once the user clicks on the link. In order to get users to click on the link, the same methods are used as with email. However, in some cases cyber criminals have gone further, as Trojan-PSW.Win32.LdPinch shows. The authors decided that having received the link, the recipient would probably want to chat, or at least say thank you. They developed a bot which would generate likely answers to be sent to the recipients’ questions or phrases.
In spite of these new, more sophisticated methods, virus writers haven’t forgotten about an older, tried and tested one – using links, which differ only slightly from trusted addresses and where the difference is not obvious at a first, cursory glance (e.g. changing an I to an |). This continues to be used as it is an effective way of enticing users into clicking on links. An example of this was detected in summer 2005, when we intercepted a worm which spread via MSN Messenger. The link sent by the worm, http://www.vbulettin.com/xxxxxxx, supposedly led to the site of a well regarded antivirus publication. Unsurprisingly, many users trusted this link, not realizing that Virus Bulletin is actually located at www.virusbtn.com, clicked, and activated the worm.
The user receives the malicious program in some form or another in all the cases mentioned above. Although many users do launch the programs, some heed repeated warnings, and don’t click on links or open attachments. Consequently, virus writers need to find other, more effective methods, to reach these security conscious users. It would be far more effective if the user didn’t receive anything directly, but simply picked up the malicious program while surfing the web. Due to this, there has been an increase in the number of sites which have been compromised and had malicious programs placed on them. Malicious users naturally choose popular sites, often those of well-known companies. Although malicious programs placed on compromised sites usually only stay there a few days before they are removed, this is long enough for thousands of machines to be infected.
One example of this is the email worm Monikey, which was mentioned above. Infected messages contain a link to the site where the body of the worm had been placed. The worm was placed on totally legal sites, and we haven’t managed to establish exactly how this was done. However, we suspect that accounts which could be used to access the sites were stolen and the data used by the authors of Monikey. It’s surprising that the administrators of compromised sites, although they removed the body of the worm, didn’t block the accounts which had been misused. And the worm continues to appear on the same sites which often display the following announcement, assuring users that the site owners did not carry out any mass mailing, explaining that the site has been compromised, and apologizing for the inconvience.

Announcement on compromised site
Cyber vandals from Nizhni Novgorod came up with an even more inventive method of distributing their malicious code via the Internet. They offered webmasters, who agreed to place a Trojan on their site, 6 cents for every machine infected by the Trojan. It’s a cause for some concern that a fair number of webmasters agreed to do this.
All of the above shows that users are under considerable threat in a variety of ways when surfing the Internet.
There are of course other ways of exploiting human nature, and the topic of social engineering deserves a separate article. Sometimes malicious users don’t know where to start when trying to penetrate a system. One tried and tested method is to get to know someone within the target organization. This provides a foothold to conduct a range of attacks, often without resorting to technology, but simply by exploiting human fallibility. For instance, a potential hacker may call the organization being targeted, state that s/he is an employee, and be given a variety of information, ranging from telephone numbers to IP addresses. This information can then be used to attack the organization’s network.
Conclusion
Computers are becoming ever more widely used in every area of life. THe potential profits to be made from cybercrime are also increasing, and techniques used by cyber criminals are consequently evolving rapidly.
Creating a reliable and effective security system in the modern world is not at all easy. There are so many potential weak points that detecting new security loopholes and patching them is an unending process. New technologies are taking the place of old ones, and are being used to solve today’s problems – but these new technologies have their own drawbacks. But hackers, virus writers and malicious users are inventing new tricks in order to evade the security software currently being used. The result is a continued stand off between cyber criminals and security professionals, with only intermittent success for the security industry. However, users have the ability to swing the balance one way or the other: unfortunately the unpredictability (or predictability) of human behaviour can bring the most concerted efforts made to secure systems to nothing.
Despite this, I hope that this article may cause some readers to consider information security in more depth, and to pay more attention to security issues.





















The human factor and information security