
I decided to introduce a bit of variety into my daily commute today by scanning the Wifi networks on the way to the office.
I used my Sony pcg-fxa53 laptop with a senao NL-2311CD Plus Ext2 pcmcia wifi card, an external antenna, and a garmin legend gps navigator. As for software, I used Linux SuSE OSS 10, kismet, gpsd, gpsmap and google api.
Once I’d thrown all that together (and of course I could write an article on that) I set off for work.
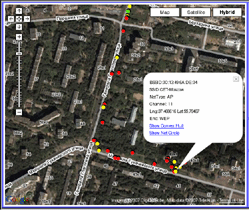
I live pretty close to the office, and my commute only takes about ten minutes – even in that time I was able to collect a fair bit of data which is shown in the picture below.
Overall, I detected 40 Wifi networks: the totally unprotected networks are marked with a red dot, those with WEP enabled are marked with a yellow dot, and those with WPA are marked with a green dot.
Just another little bit of data to add to our continuing research on wifi networks and encryption around the world.




















Just for fun