
FBI’s “Operation Ghost Click” was discussed earlier by my colleague Kurt here and here and now it comes to an end.
Next Monday, 9th of July, at 06:00 (MEZ) the temporary DNS-servers setup by FBI will be shut down. But still there are still thousands of infected machines – one can wonder, what will happen to them?
Computers in the internet have their own address – the IP-address. There are two versions:
- IPv4 which is a 32-bit address e.g. 195.122.169.23 and
- IPv6 which is a 128-bit address e.g. 2001:db8:85a3:8d3:1319:8a2e:370:7347
You clearly see that these addresses are not so easy to remember compared to e.g. “kaspersky.com”. Therefore the “Domain Name System” was created which translates domain-names as “kaspersky.com” to their respective IP-address to connect to the server.
The DNS-Changer malware replaces the DNS-servers on the infected system with its own. FBI Press Release
The reason they do this is because it facilitates “Click Hijacking”. This is a technique where infected users are redirected to advertisement websites from the criminals and “Advertising Replacement” where on legitimate websites the advertisements were exchanged with one from the criminals.
Luckily, the FBI caught the criminals and installed temporary DNS-Servers in order to avoid a “black-out” for the mass of infected computers.
This temporary solution will come to an end on Monday when the servers are shut down. When this happens, the infected machines will no longer able to resolve domain names in order to connect to e.g. a website.
Of course, if you know the address of the server you can still use it instead of the name e.g. 195.122.169.23 is “securelist.com” but this is not easy solution.
We would like to point out that despite the big noise around this topic, there is no need to panic. The solution is rather simple – read below for more.
First of all, it might be interesting to point out that in 2012 we detected 101.964 attempts by DNSChanger malware to infect our users.
The good news is that the infections were blocked and the number of infection attempts is going down.
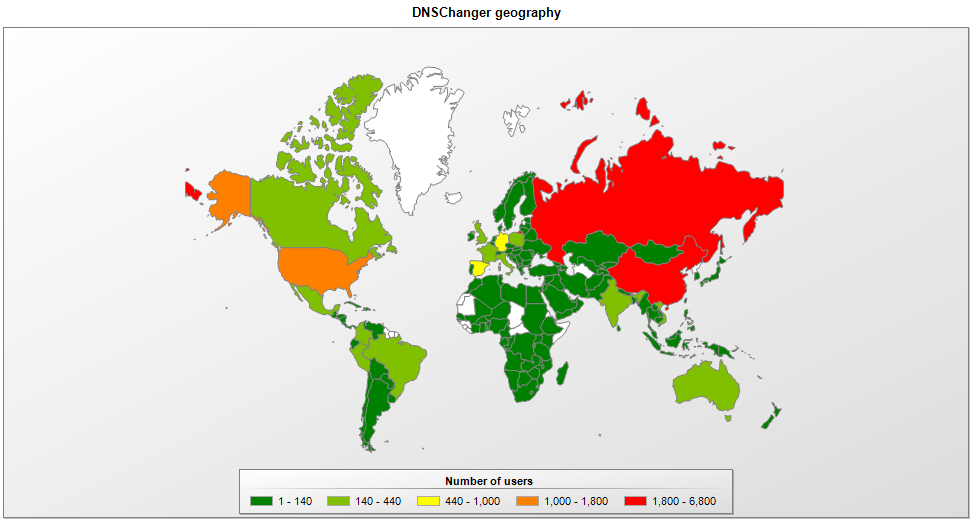
For instance, this map of the past week shows that the amount of infection attempts/detections as decreasing. Of course, computers with no or old protection are still in danger of possible unspotted infections.
So, how to check if you are infected with DNSChanger?
The DNS Changer Working Group provides helpful information on their website http://www.dcwg.org/detect/ – unfortunately, we previously mentioned that automatic websites setup for this purpose do not work 100% well. So, the manual solution of checking the DNS server IPs is better.
If you are infected, you can change your DNS entries to the free DNS-Servers from Google: 8.8.8.8 and 8.8.4.4. OpenDNS also offers two: 208.67.222.222 and 208.67.220.220, which we also recommend for additional security features.
The best solution is of course to install a security suite capable of detecting and cleaning the infection and fixing the DNS servers.
Since many DNSChanger infections are accompanied by TDSS, a rather nasty rootkit, you can also use our tool “Kaspersky TDSSKiller” in order to detect and delete the infection




















The end of DNS-Changer