
September in figures
- The amount of spam in email traffic was down 1.5 percentage points compared to August and averaged 78.5%.
- Phishing emails accounted for 0.03% of all mail traffic, the same as in August.
- Malicious files were found in 4.5% of all emails, down 1.4 percentage points from August.
Spam in the spotlight
Spam and the new financial crisis
September saw more expert commentary on an impending financial crisis. Early last year, as the previous financial problems began to ease, we wrote about how the economic cycle was reflected in spam. Echoes of the financial climate could be found in both the content of spam mails and in the behavior of the spam industry in general. This year’s recession did not take long to make itself felt, with spammers already reacting to the unstable economic situation.
Emails about the crisis
In September several spam emails sought to exploit the preoccupation with the economy. Of course, in common with any high-profile news story, many just used the recession as an attention-grabbing headline despite having nothing to do with finance.
But other messages this month exploited economic uncertainty in their body text: they offered dubious get-rich-quick schemes, promoted legal or consulting services and used notorious ‘Nigerian letter’ tactics.
These changes to the themes used in spam came as no surprise: in the 2008-09 crisis financial instability was actively used in fraudulent spam.
It seems only natural that financial instability will influence spammers: in these times easy money is always attractive, and so are legal services. Recession-related spam in September was dominated by Nigerian letters offering “anti-crisis” loans.
Fraudulent spam: new weapons in the arsenal
In our August spam report we wrote about some of the interesting new tricks spammers are using to deceive users. In September, a few new sophisticated social engineering techniques emerged. We described two of them in our blogs at the beginning of the month.
The first describes a new, very sophisticated type of phishing. The user receives a message, apparently from McDonald’s. It states that the recipient has won the chance to participate in a survey and will get $80 for doing so. The user follows the link, finds himself on a page with a customer satisfaction survey form and fills it in. After submitting the survey, he is redirected to a further form asking for full credit card details to process the promised $80 payment. Of course, the information is likely to be used to clean out the user’s account, rather than pay any cash.
The second blog describes a trick used to provoke curiosity, tempting users to open an archived attachment. The text reads like a short official message, but is wrongly encoded.
The second blog describes a trick used to provoke curiosity, tempting users to open an archived attachment. The text reads like a short official message, but is wrongly encoded.
This kind of approach could lead some to believe that fraudsters prefer to play on people’s curiosity rather than resort to threats – but the techniques described below prove that menacing mails are still thriving.
For example, the Nigerian letter below contains a direct threat to the user’s life.
The message claims to be from a contract killer with orders to murder the recipient. But for $8,000 the assassin is willing to spare the intended victim, and even betray his paymaster.
It’s hard to imagine many people being impressed with this: the message from a compassionate killer is full of holes (I particularly like the bit about not leaving the house after 8 pm). Besides, an assassin who has detailed knowledge of the target’s life and movements cannot apparently address his reader by name in the text of the message – merely confirming that the mail is a fake.
A more effective social engineering trick is an email threatening legal action against the user for distributing spam containing malware.
The recipient is invited to open an archived attachment and check the evidence of his address being used to distribute spam. The executable file in the archive was damaged so we cannot identify which particular malicious code it was spreading.
We should reiterate that this trick can be quite effective. Recipients of this type of email should not panic, however. It’s rare for such emails to include personal data about the user, or any information about the supposed plaintiff. These are the giveaway signs of a fraudulent email aiming to install malicious executable files on personal computers.
Microsoft continues its anti- botnet campaign
At the end of September Microsoft announced the closure of yet another botnet. Kaspersky Lab specialists provided technical support for the closure of the Hlux/Kelihos botnet. This victory did not destroy a huge network – the botnet only involved 40,000 machines – but the closure was nonetheless unique. For the first time in Microsoft’s anti-botnet campaign the corporation could name the botnet’s owners. More details are available on Microsoft’s official blog.
Because the botnet was not a big one, we can add that its closure did not seriously affect spam traffic.
Statistical summary
Sources of spam
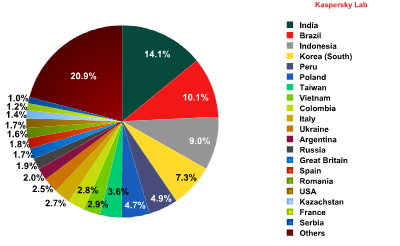
Sources of spam in September 2011.
There was little change in September’s list of the top five leading spam sources, although some countries swapped places. India was top with 14.1% of all distributed spam, followed by Brazil (10.1%), Indonesia (9%), South Korea (7.3%) and Peru (4.9%).
The total amount of spam originating from these five Asian and South American countries represented slightly more than 45% of global spam traffic. Over 60% of spam is still distributed by the top ten countries in the rating, mostly located in Asia, eastern Europe and South America. The only western European country in September’s Top Ten was Italy, with 2.7% of all distributed spam.
Indonesia saw the biggest drop in its share of spam – down almost 3 percentage points, the sharpest shift of the month. Changes in other countries did not exceed 1.5 percentage points.
Previously we grouped certain countries together, and continuing that monitoring we would like to note that:
- Spam originating from the Indonesia-Ukraine-Thailand-Peru group seems to be closely interlinked. Only Thailand is out of synch with the other members: the volume of spam distributed from that country in August and September was so negligible that the local peaks and troughs were not as clear as in the others.

The percentage of spam originating from Indonesia, Ukraine,
Thailand and Peru from 22 August to 2 October - Spam coming from the India-Brazil pairing is also quite closely linked, although indicators for these countries are still strongly affected by local factors.

The percentage of spam originating from India and Brazil
from 22 August to 2 October - Statistics for the Vietnam-Russia group reveal an interesting relationship: the spam flows originating from these countries are sent in anti-phase. It is not yet clear why this is the case.

The percentage of spam originating from Russia and Vietnam from
22 August to 2 October
Malicious attachments in mail traffic
In September, malicious files were found in 4.5% of all emails — 1.4 percentage points less than in August.
There were no significant shifts in the countries with the highest rates of email antivirus detection. The top three remains unchanged, with negligible fluctuations within a single percentage point.
India showed a significant increase in email antivirus detections (+1.5 percentage points), moving the country up two places to 4th.
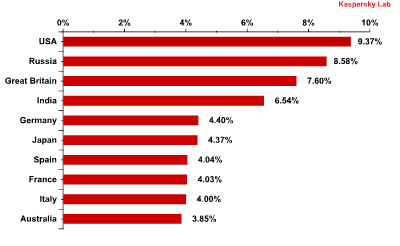
Distribution of email antivirus detections, by country: September 2011
For the first time in a long time Trojan-Spy.HTML.Fraud.gen lost its leading position as the most frequently detected malicious program.
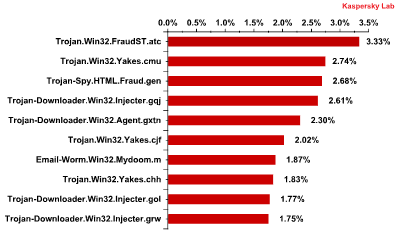
The Top 10 malicious programs spread via email in September 2011
This time the number one troublemaker is Trojan.Win32.FraudST.at, a spam bot whose speciality is spreading pharmaceutical mass mailings.
September. Like Trojan-Downloader.Win32.Agent.gxtn, which came fourth in the rating, Yakes is a classic Downloader Trojan that downloads other malicious programs once installed on a computer.
As in August, Email-Worm.Win32.Mydoom.m was the only mail worm to make the September ratings. This particular threat really only has two functions: to harvest electronic addresses on infected machines and send itself to those addresses.
Phishing
The percentage of phishing emails in total mail traffic remained unchanged at 0.03%.
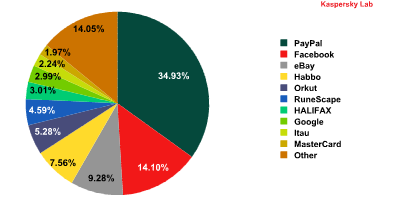
Top 10 organizations targeted by phishers*
* This rating is based on the number of phishing URLs on the Internet that attempt to obtain user logins and passwords for various online services. The rating is not demonstrative of the security level of the organizations named above, but rather the popularity of their services among users, which in turn explains their popularity among phishers.
One of the main changes in September was the rise of the social networking site Facebook from fourth to second place. The number of attacks on this service increased by 5.4 percentage points and accounted for 14.1% of the total.
In September, attacks on eBay were slightly less intensive (-0.9 percentage points) compared to August. This long-term resident is in 3rd position among the most popular phishing targets.
Phisher interest in the RuneScape online game is also increasing: the amount of attacks on it doubled in September now that the main users of these services – school children and students – are back from holidays.
Spam by category
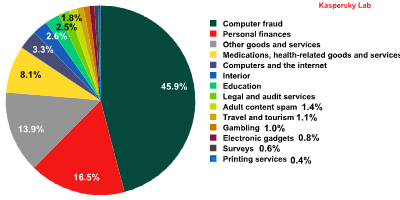
Spam by category in September 2011
Nearly half of all English-language spam in September was comprised of fraudulent emails. This echoes the patterns seen in 2008 when the percentage of malicious attachments in emails increased. In periods of financial crisis, when people’s spending power is curtailed, spammers resort to extorting money from users in a bid to maintain their level of income.
The second-most prevalent category of spam this past month was financial spam, again, understandable at a time of emerging recession.
Conclusion
Faced with a period of economic recession, we will probably see a growth in the levels of fraudulent spam mails. This type of spam aims to extort or steal money from the users both with and without the help of malware. September continued the summer trend: we saw a further increase in English-language spam that, instead of trying to sell something, was harvesting data from a victim’s computer and then using it in scams.
Users should be more cautious when dealing with any emails inviting them to download applications, follow links or submit passwords. The fraudsters are now actively enriching their arsenal of tricks, inventing methods that can disorient even an experienced user. Be careful!

























Spam report: September 2011