
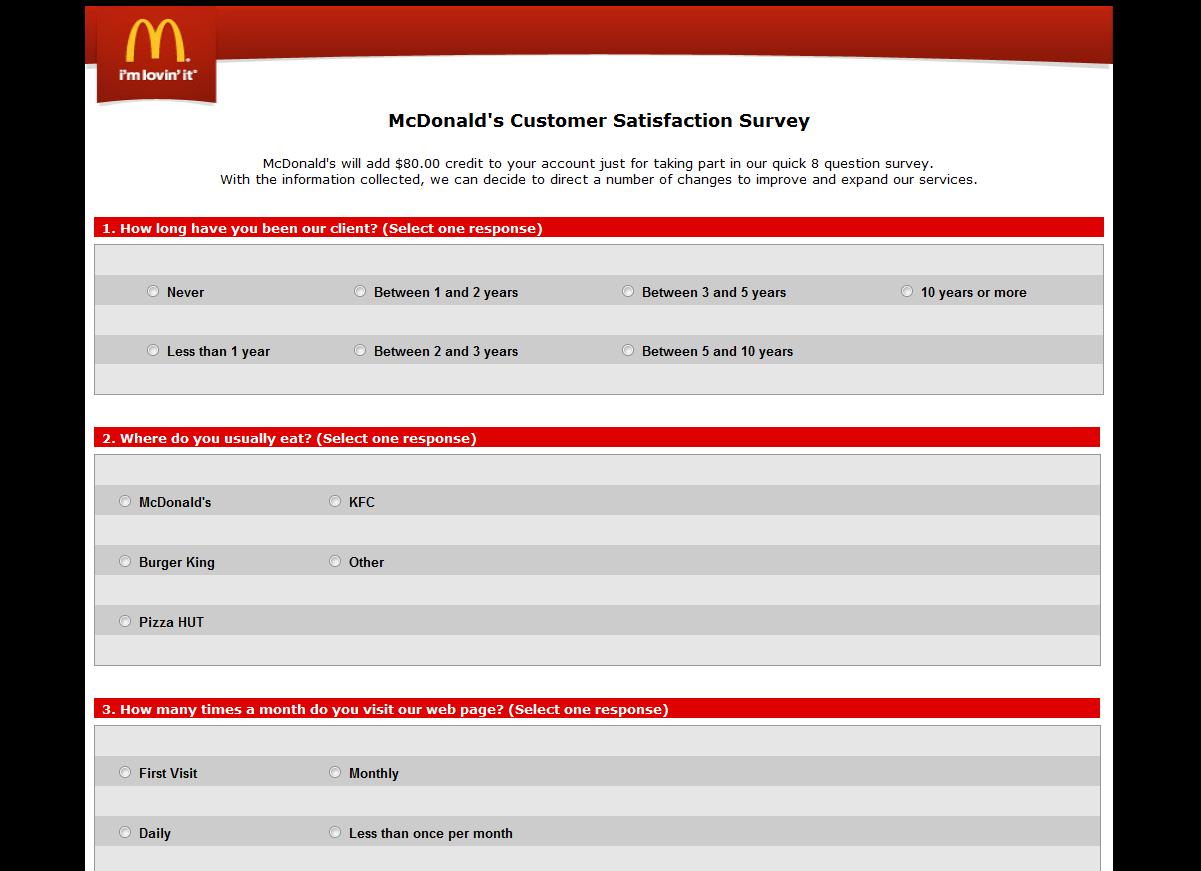
Today we came across a new, very sophisticated type of phishing. The user receives a message that, at first glance, appears to be from McDonald’s. It states that the recipient has won the chance to participate in a survey and immediately receive remuneration of $80 for doing so.
There is nothing to suggest that something fishy is going on: the user follows the link, finds himself on a page with a customer satisfaction survey form, takes the survey and clicks on a button…
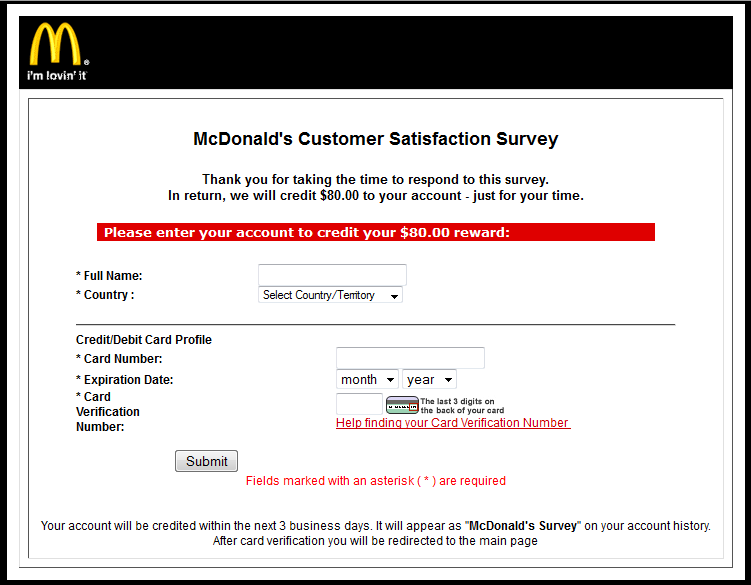
… after which he is redirected to another form where all he has to do is to write the number of his credit card, expiry date and cvv code in order to receive the $80. Of course, instead of receiving any money the user’s account is likely to be cleaned out by the criminals behind the scam.
Interestingly, the address in the “From” field is mcdonalds@mcdonaldss.com. Please note the additional “s” in the domain name: creating addresses which differ from the authentic ones by just one letter is a common trick.
To circumvent filters and denylists the cybercriminals resorted to infected websites: the user follows the link contained in the message and first finds himself on a web page which only contained a short javascript code that redirects the user to the cybercriminals’ main site.

It stands to reason that the so-called survey was merely a ruse to trick unsuspecting users. The main page in the scam is the last one, where the user sends his credit card number to the fraudsters before being redirected to the official McDonald’s website.
Be careful, this scam is currently active! Do not follow links in spam emails! You can always check the official site of the company in question if you have any doubts whatsoever about the authenticity of any offers.



















Phishers are lovin’ McDonald’s