
Spam: quarterly highlights
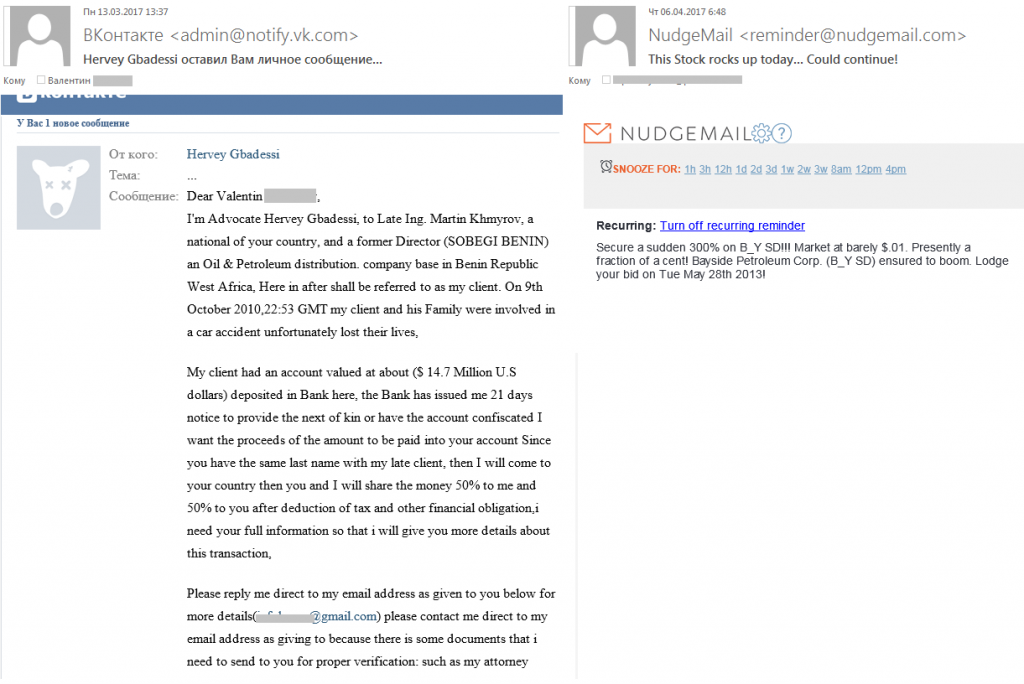
Spam from the Necurs botnet
We wrote earlier about a sharp increase in the amount of spam with malicious attachments, mainly Trojan encryptors. Most of that spam was coming from the Necurs botnet, which is currently considered the world’s largest spam botnet. However, in late December 2016, the network’s activity almost ceased completely and, as time showed, it wasn’t just a break for the festive season. The volume of spam sent from this botnet remained at an extremely low level for almost the entire first quarter of 2017.
In Q1 2017, the percentage of spam in email traffic amounted to 55.9%.
Tweet
Why has Necurs stopped distributing spam? We know that the botnet is active and the bots are waiting for commands. Perhaps the criminals behind the botnet got scared by all the fuss made about encryptors and decided to temporarily suspend their mass mailings.
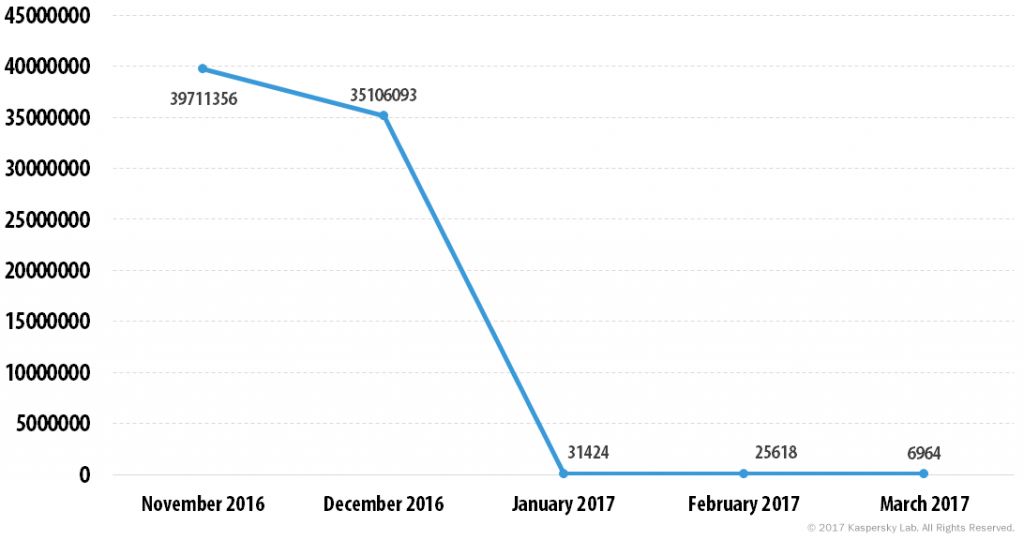
We still continue to register malicious mass mailings from what is presumably the Necurs botnet, though their volume is a fraction of the amount recorded in December:
The number of malicious messages caught by our traps that were presumably sent by the Necurs botnet
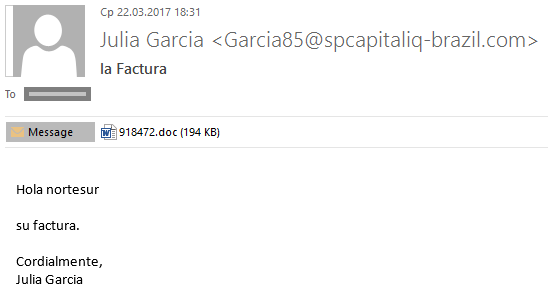
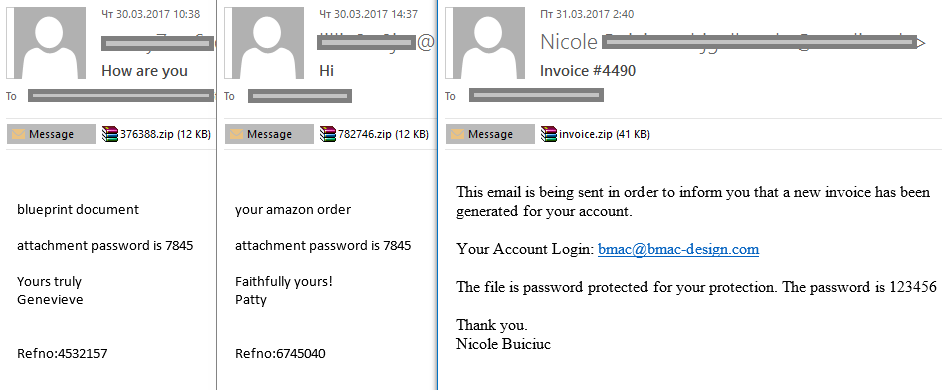
As before, the emails usually imitate various types of bills and other official documents:
The email above contained an attached MSWord document with macros that downloaded the Rack family encryptor (detected as Trojan.NSIS.Sod.jov) to the victim machine.
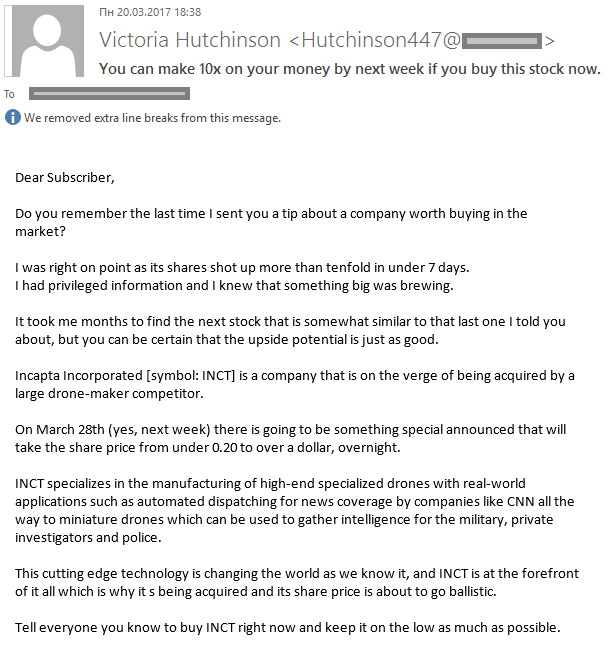
In addition to malicious mailings from the botnet, we came across a mass mailing about pump-and-dump stock schemes:
As a rule, mass mailings exploiting this subject are distributed in huge volumes over a very short period of time. This is because the fraudsters have to pump and dump shares quickly, before their scams are discovered on the stock exchange. This type of stock fraud is against the law, so cybercriminals try to wind up the affair within a couple of days. The Necurs botnet is ideal for this sort of scam due to its size – according to estimates, it currently exceeds 200,000 bots.
The average share of spam in Russia’s email traffic in Q1 2017 was 61.6%.
Tweet
Does this sharp drop mean we have reached peak crypto-spam mass mailing and it’s about to disappear? Unfortunately, no.
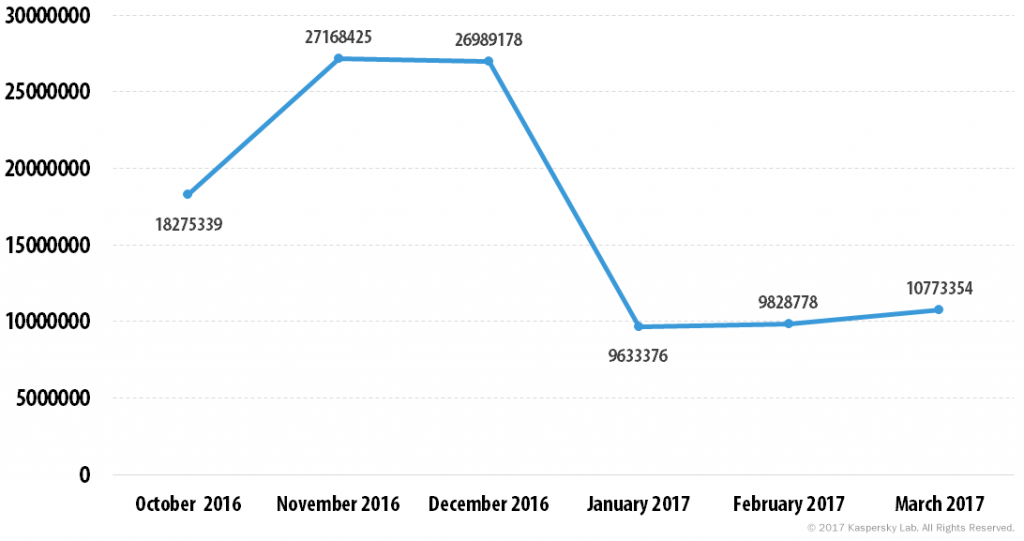
The total volume of malware detected in email decreased, but not that dramatically – 2.4 times less than the previous quarter.
The number of email antivirus detections, Q4 2016 vs Q1 2017
Malicious mass mailings are still being sent out and, although their volume has decreased, cybercriminals are using a variety of techniques to deceive both security solutions and users.
Malicious emails with password-protected archives
In the first quarter we observed a trend towards packing malware into password-protected archives to complicate detection of malicious emails.
All the classic tricks were used to make potential victims open the archives: fake notifications about orders from large stores, various bills, money transfers, resumes, or the promise of lots of money.
The attached archives usually contained office documents with macros or JavaScript scripts. When launched, the files downloaded other malicious programs on the user’s computer. Interestingly, after the decline in Necurs botnet activity, the harmful “payload” that spread via spam became much more diverse. The cybercriminals sent out ransomware and spyware, backdoors and a new modification of the infamous Zeus Trojan.
The attachments above contain Microsoft Word documents with macros that download several different modifications of a Trojan encryptor belonging to the Cerber family from onion domains in different zones. This malicious program selectively encrypts data on the user’s computer and demands a ransom for decrypting it via a site on the Tor network.
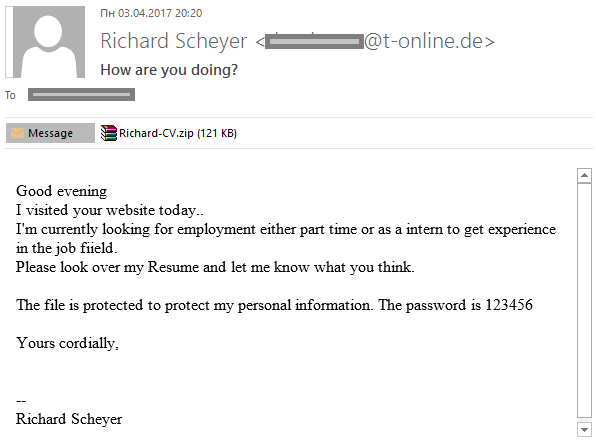
The archive in the message above contains the Richard-CV.doc file with macros that downloads representatives of the Fareit spyware family from the onion.nu domain. These malicious programs collect confidential information about the user and send it to the remote server.
There was yet another case involving downloadable spyware, this time from the Pinch family. The Trojan collects passwords, email addresses, information about the system configuration and registry settings. Among other things, it harvests information from instant messaging services and mail clients. The obtained data is encrypted and sent to the criminals by email. According to our information received from KSN, the program is most widespread in Russia, India and Iran.
Most email antivirus detections occurred in China – 18% of all spam.
Tweet
It’s worth pointing out that this spyware was spread using fake business correspondence. Emails were sent out using the names of real small and medium businesses with all the relevant signatures and contacts, rather than using the name of some made-up organization.
Unlike other emails, the example above does not contain a password-protected archive. The request to enter a password is just a trick: the fraudsters want the user to enable Microsoft Word macros to run the malicious script.
The contents of the email above include a password-protected document with a script in Visual Basic that downloads the Andromeda bot on the victim machine. The latter establishes a connection with the command center and waits for commands from the owners. It has broad functionality and can download other malicious programs on the user’s computer.
This fake notification from an e-store contains a malicious script. On entering the password and launching the malicious content, the Receipt_320124.lnk file is created in the %TEMP% catalogue. It, in turn, downloads a Trojan-banker of the Sphinx family, which is a modification of the older and infamous Zeus, on the victim computer.
As we can see, very different mass mailings with malicious attachments now contain files packed in a password-protected archive. Most likely, this trend will continue: a password-protected document is likely to appear more trustworthy to the user, while causing problems for security solutions.
Spam via legal services
Modern virtual platforms for communication (messengers, social networks) are also actively used by spammers to spread advertising and fraudulent offers. Cybercriminals register special accounts for spamming in social networks and to make their messages look more authentic they use techniques similar to those used in traditional mass mailings (for example, the personal data from the account and that sent in the email are the same). The same type of spam, for example, ‘Nigerian letters’, offering earnings, etc. can be distributed via email traffic and social networks. A notification about a message is usually sent to the recipient’s email address; in this case, the technical header of the email is legitimate, and it is only possible to detect the spam by the contents of the message. Spam distributed directly via email, can be easily detected by technical headers. The same cannot be said for messages sent via legitimate services, especially if the address of the service is added to the user’s list of trusted addresses.
Today’s email spam filters can cope effectively with the task of detecting spam that is sent in the traditional way, so spammers are forced to look for new methods to bypass filters.
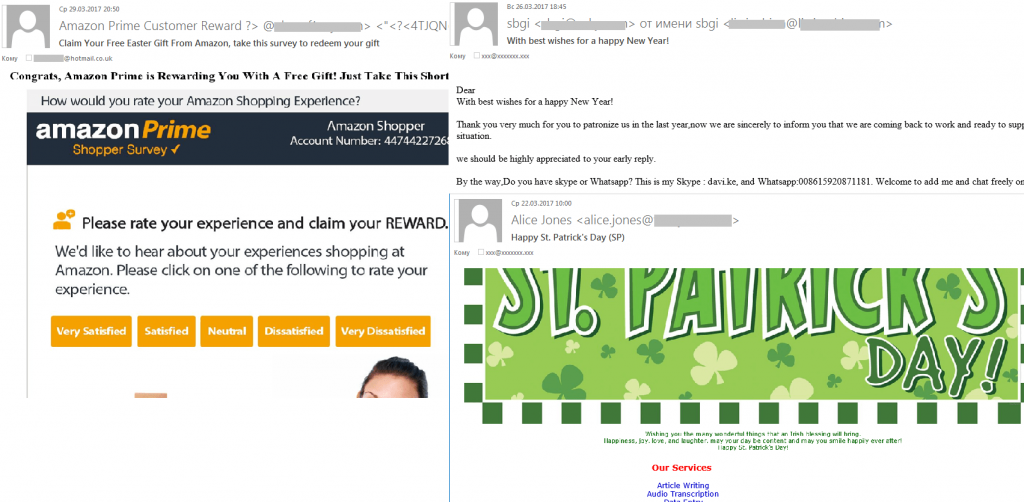
Holidays and spam
The first quarter of 2017 saw festive spam dedicated to New Year, St. Patrick’s Day, Easter and Valentine’s Day. Small and medium-sized businesses advertised their services and products and offered holiday discounts. Offers from Chinese factories were timed to coincide with the Chinese New Year, which was celebrated in mid-February.
Spammers also sent out numerous offers to participate in a survey and get coupons or gift cards from major online stores, hoping to collect the recipients’ personal information and contact details.
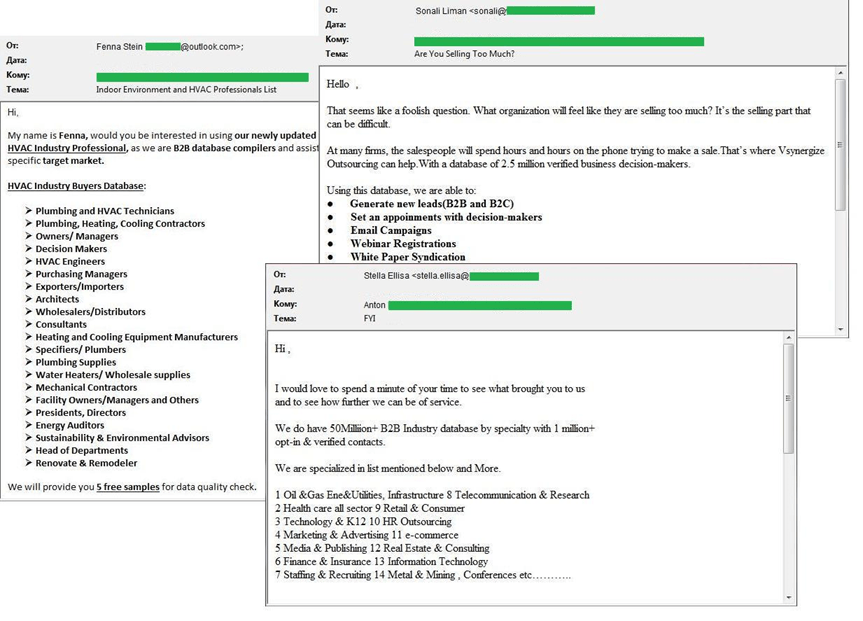
Burst of B2B spam
In the first three months of 2017, we also recorded a large number of mass mailings containing offers to buy company databases from specific industries. This type of spam remains popular with spammers and primarily targets companies or individual representatives of large businesses rather than ordinary users. Therefore, these messages are sent mainly to people or companies from a list of contacts or addresses for a particular business segment that is obtained, as a rule, in the same way – via spam.
The offers are sent on behalf of firms or their representatives, but they are often completely impersonal.
Spammers have databases of companies for any business segment, as well as the contact details of participants at major exhibitions, seminars, forums and other events. To make recipients interested in their offers, spammers often send several free contacts from their collections.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q4 2016 and Q1 2017
Compared to Q4 2016, there was a decline in the overall proportion of spam in global email traffic in the first three months of 2017. In January, the proportion fell to 55.05%, while in February the share was even lower – 53.4%. However, in March the level of spam showed an upward trend, rising to 56.9%. As a result, the average share of spam in global email traffic for the first quarter of 2017 was 55.9%.
Percentage of spam in Russia’s email traffic, Q4 2016 and Q1 2017
The spam situation in the Russian segment of the Internet was somewhat different from the global one. In January 2017, the proportion of junk email increased to almost 63% and stayed in the 60-63% range until the end of the quarter. In February, as was the case with overall global traffic, there was a decline – to 60.35% – followed by an increase to 61.65% in March. The average share of spam in Russian email traffic in the first quarter of 2017 was 61.66%.
Sources of spam by country
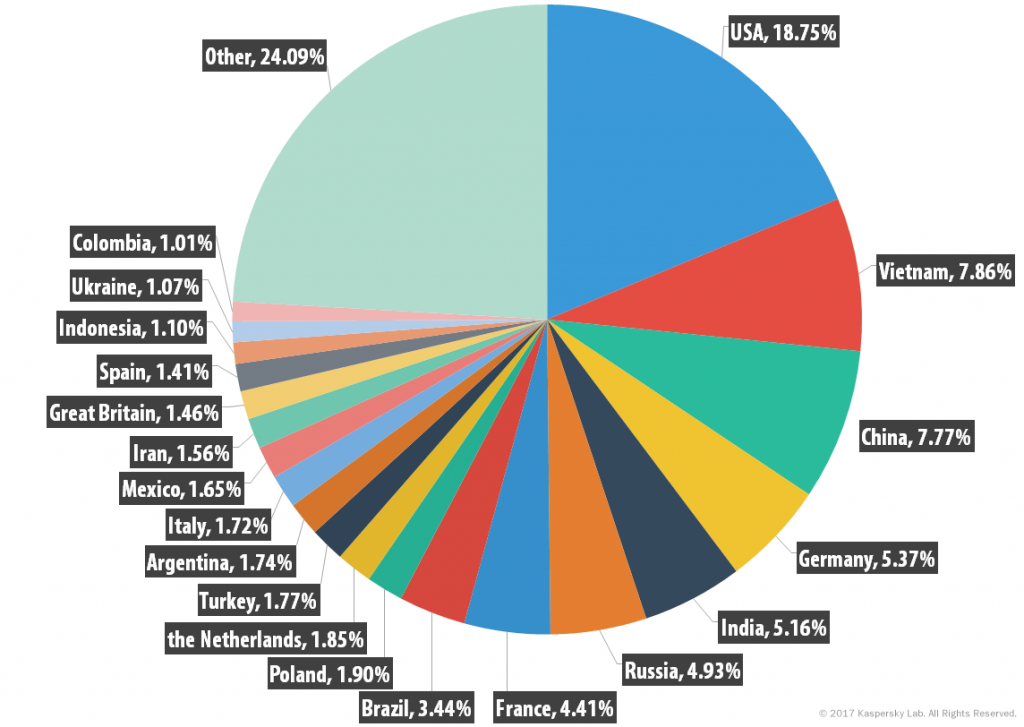
Sources of spam by country, Q1 2017
In the first quarter of 2017, the US remained the leading source of spam – its share accounted for 18.75%. Representatives from the Asia-Pacific region – Vietnam (7.86%) and China (7.77%) – came second and third.
Trojan-Downloader.JS.Agent remained the most popular malware family spread via email.
Tweet
Germany was the fourth biggest source, responsible for 5.37% of world spam, followed by India (5.16%). Russia, in sixth place, accounted for 4.93% of total spam.
The top 10 biggest sources also included France (4.41%), Brazil (3.44%), Poland (1.90%) and the Netherlands (1.85%).
Spam email size
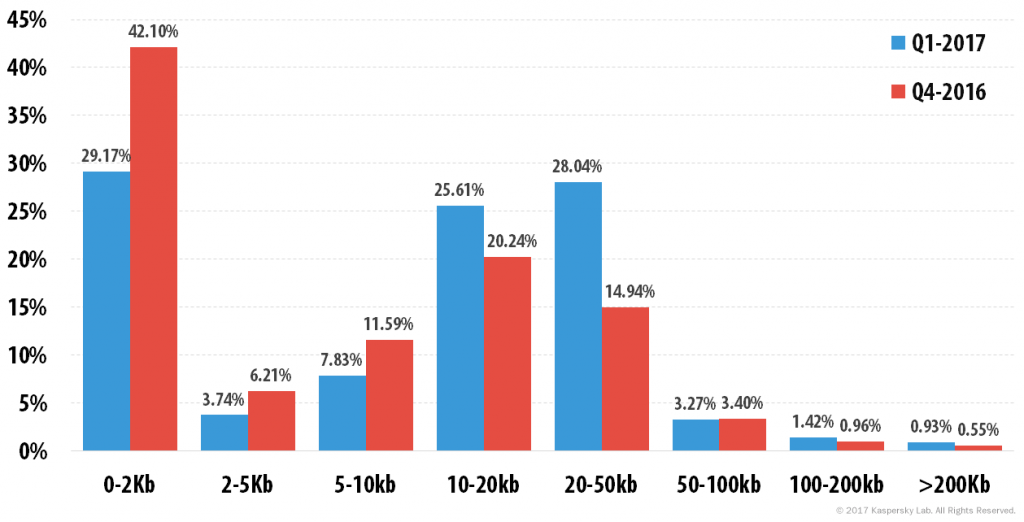
Breakdown of spam emails by size, Q4 2016 and Q1 2017
In Q1 2017, the share of small emails (up to 2 KB) in spam traffic decreased considerably and averaged 29.17%, which is 12.93 p.p. less than in the fourth quarter of 2016. The proportion of emails sized 2–5 KB (3.74%) and 5–10 KB (7.83%) also continued to decline.
Meanwhile, the proportion of emails sized 10-20 KB (25.61%) and 20-50 KB (28.04%) increased. Last year’s trend of fewer super-short spam emails and more average-sized emails has continued into 2017.
Malicious attachments in email
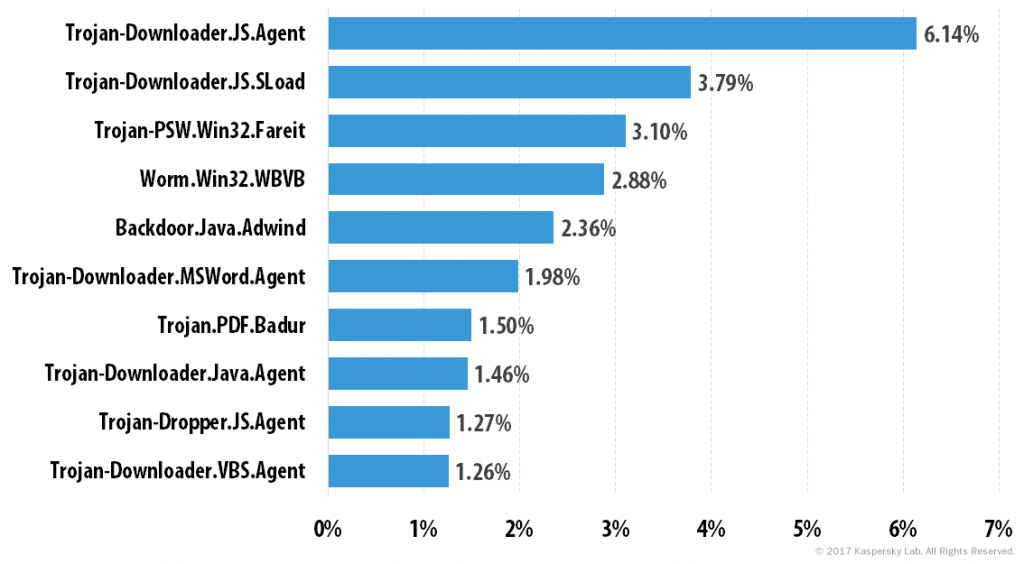
Top 10 malware families
Trojan-Downloader.JS.Agent (6.14%) once again topped the rating of the most popular malware families. Trojan-Downloader.JS.SLoad (3.79%) came second, while Trojan-PSW.Win32.Fareit (3.10%) completed the top three.
TOP 10 malware families in Q1 2017
The Backdoor.Java.Adwind family (2.36%) in fifth place is a cross-platform multifunctional backdoor written in Java and sold on DarkNet as malware-as-a-service (MaaS). It is also known under the names of AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRat. It is typically distributed via email as a JAR attachment.
A newcomer – Trojan-Downloader.MSWord.Cryptoload (1.27%) – occupied ninth place. It’s a JS script containing malware, which it installs and runs on the computer.
Trojan-Downloader.VBS.Agent (1.26%) rounded off the Top 10.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q1 2017
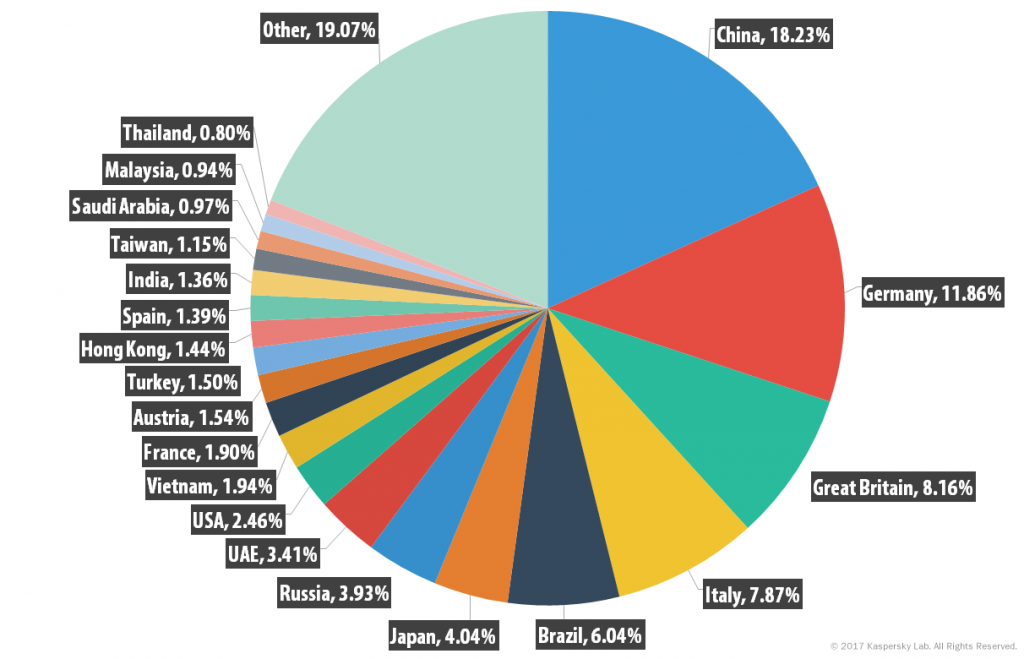
In Q1 2017, China (18.23%) was the country targeted most by malicious mailshots. Germany, last year’s leader, came second (11.86%), followed by the UK (8.16%) in third.
Italy (7.87%), Brazil (6.04%) and Japan (4.04%) came next, with Russia occupying seventh place with a share of 3.93%. The US was in ninth place with (2.46%), while Vietnam (1.94%) completed the Top 10.
Phishing
In the first quarter of 2017, the Anti-Phishing system was triggered 51,321,809 times on the computers of Kaspersky Lab users. Overall, 9.31% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q1 2017.
Geography of attacks
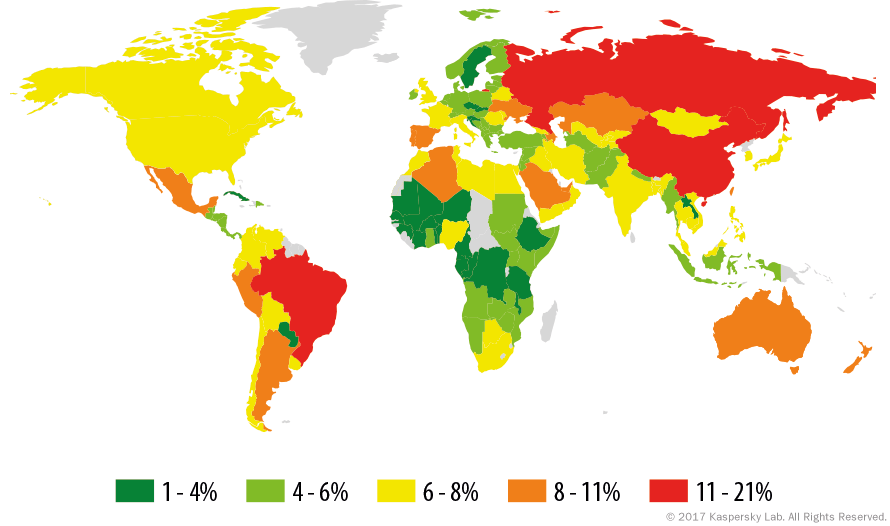
China (20.88%) remained the country where the largest percentage of users is affected by phishing attacks, although its share decreased by 1.67 p.p.
Geography of phishing attacks*, Q1 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
The percentage of attacked users in Brazil decreased by 0.8 p.p. and amounted to 19.16%, placing the country second in this ranking. Macao added 0.91 p.p. to the previous quarter’s figure and came third with 11.94%. Russia came fourth with 11.29% (+0.73 p.p.), followed by and Australia on 10.73% (-0.37p.p).
TOP 10 countries by percentage of users attacked
| Country | % |
| China | 20.87% |
| Brazil | 19.16% |
| Macao | 11.94% |
| Russia | 11.29% |
| Australia | 10.73% |
| Argentina | 10.42% |
| New Zealand | 10.18% |
| Qatar | 9.87% |
| Kazakhstan | 9.61% |
| Taiwan | 9.27% |
Argentina (10.42%, +1.78 p.p.), New Zealand (10.18%), Qatar (9.87%), Kazakhstan (9.61%) and Taiwan (9.27%) completed the top 10.
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
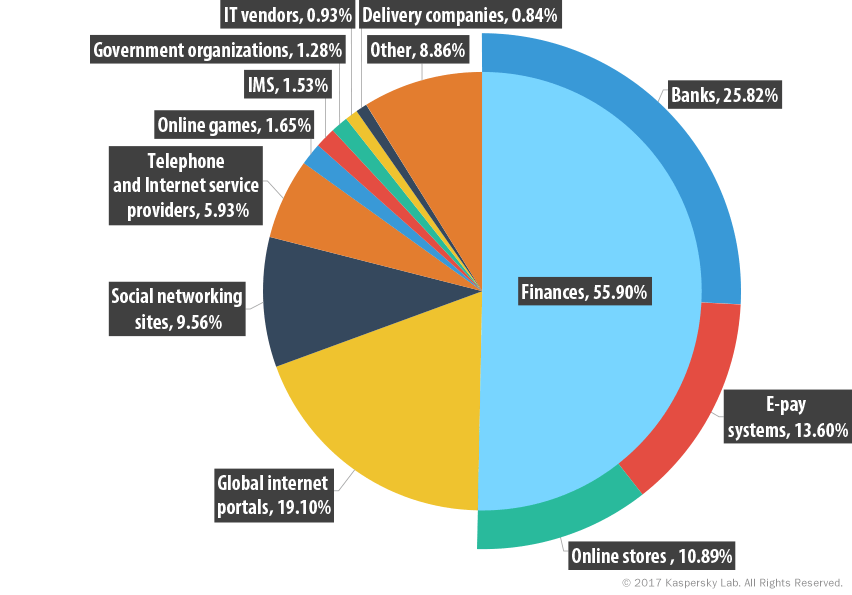
In Q1 2017, the ‘Banks’ (25.82%, -0.53 p.p.), ‘Payment systems’ (13.6%, +2.23 p.p.) and ‘Online stores’ (10.89%, +0.48 p.p.) categories accounted for more than half of all registered attacks. The total share of ‘Financial organizations’ was a little over 50% of all phishing attack
Distribution of organizations affected by phishing attacks by category, Q1 2017
In addition to financial organizations, phishers most often targeted ‘Global Internet portals’ (19.1%), although their share decreased by 5.25 p.p. from the previous quarter. ‘Social networking sites’ (9.56%) and ‘Telecommunication companies’ (5.93%) also saw their shares fall by 0.32 p.p. and 0.83 p.p. respectively. The percentage of the ‘Online games’ category accounted for 1.65% while the figure for ‘Instant messaging’ was 1.53%.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component are for phishing pages using the names of fewer than 15 companies.
In Q1 2017, Kaspersky Lab products blocked 51 million attempts to open a phishing page.
Tweet
The TOP 3 organizations attacked most frequently by phishers remained unchanged for the second quarter in a row. Yahoo! was once again the organization whose brand was mentioned most often on phishing pages (7.57%, – 1.16 p.p.). Facebook (7.24%), whose share fell by 0.13 p.p., was second, while Microsoft (5.39%, -0.83 p.p.) came third.
| Organization | % of detected phishing links |
| Yahoo! | 7.57 |
| 7.24 | |
| Microsoft Corporation | 5.39 |
In order to reach the widest possible audience with one attack, scammers often mention a variety of brands expecting the victims to react to at least one of them. This is facilitated by authentication with existing accounts, which many Internet services use trying to make life easier for their users. Therefore, a page offering to use different accounts to enter a site does not arouse suspicions. This allows fraudsters to steal user data from several different resources using just one phishing page.
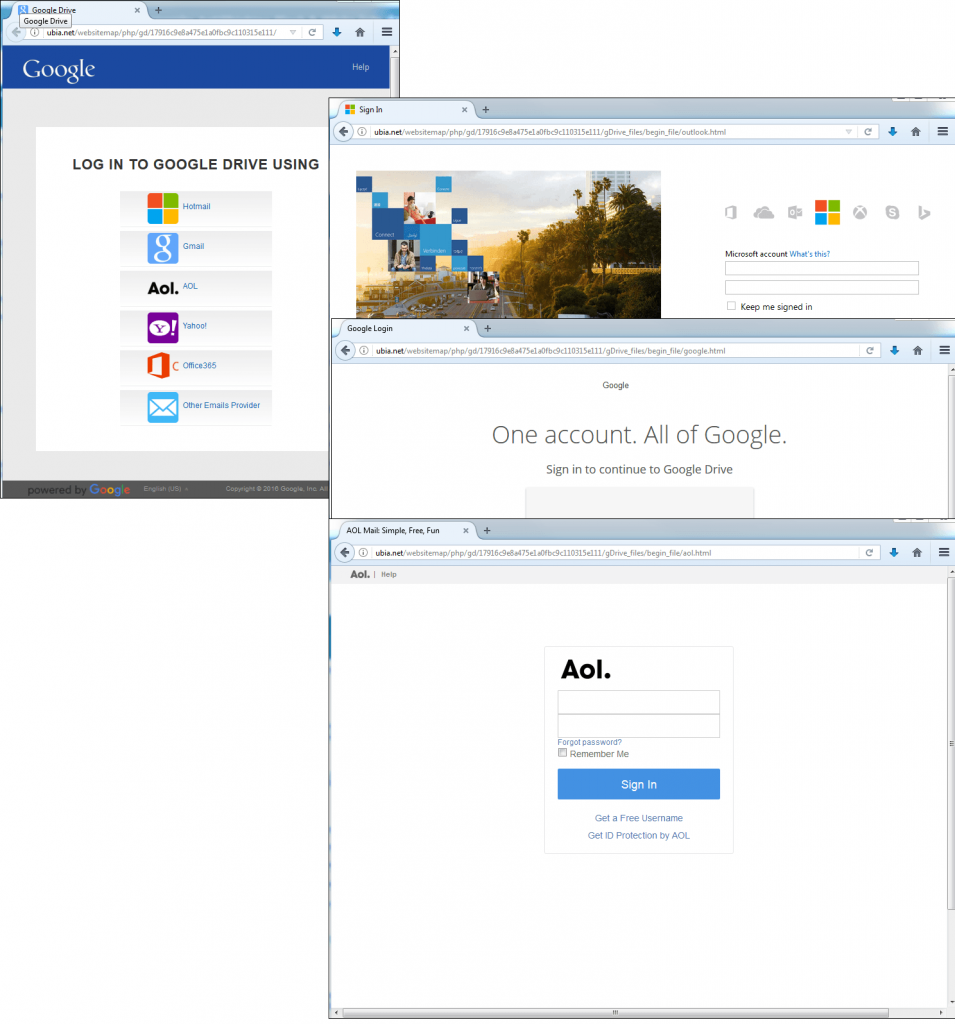
Phishing page prompting the user to login via the accounts of other web resources to access a file
This phishing page uses a similar trick under the pretext of accessing the Google Drive service
Hot topics this quarter
Payment systems
In the first quarter Q1 2017, 13.6% of detections of Kaspersky Lab’s heuristic anti-phishing component fell under the ‘Payment Systems’ category. It means that every eighth attack targeted this category, which has been popular with phishers for several quarters now.
PayPal (28.25%) came first on the list of attacked payment systems, followed by Visa (25.78%) and American Express (24.38%).
| Organization | %* |
| PayPal | 28.25 |
| Visa Inc. | 25.78 |
| American Express | 24.38 |
| MasterCard International | 16.66 |
| Others | 4.94 |
* The percentage of attacks on an organization as a total of all attacks on organizations from the ‘Payment Systems’ category
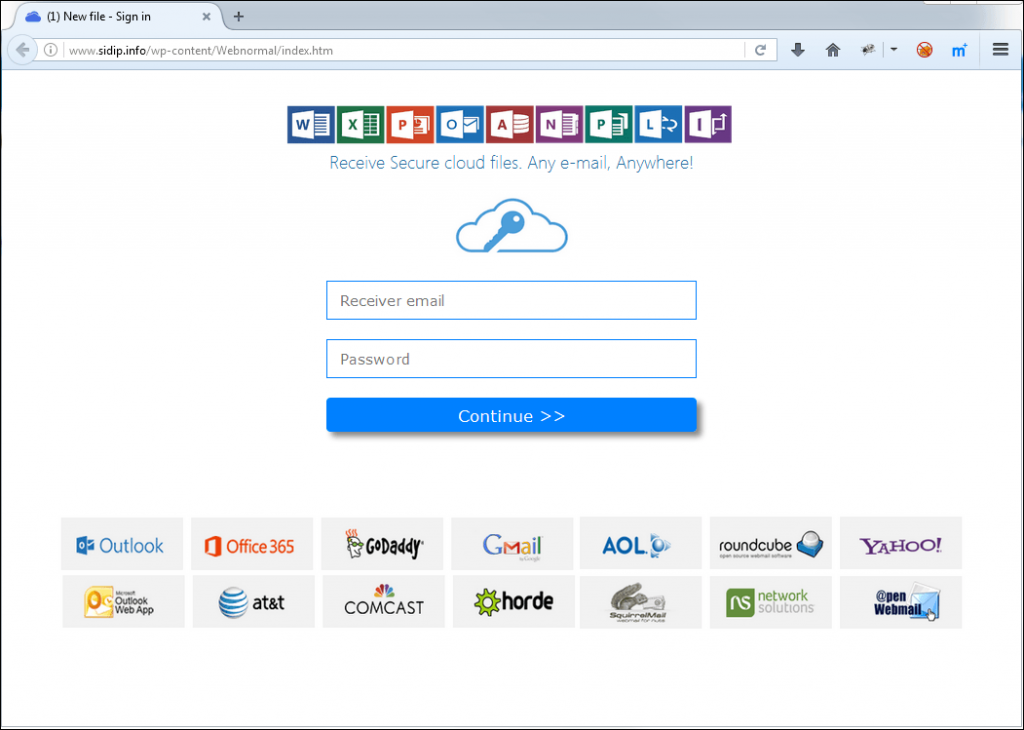
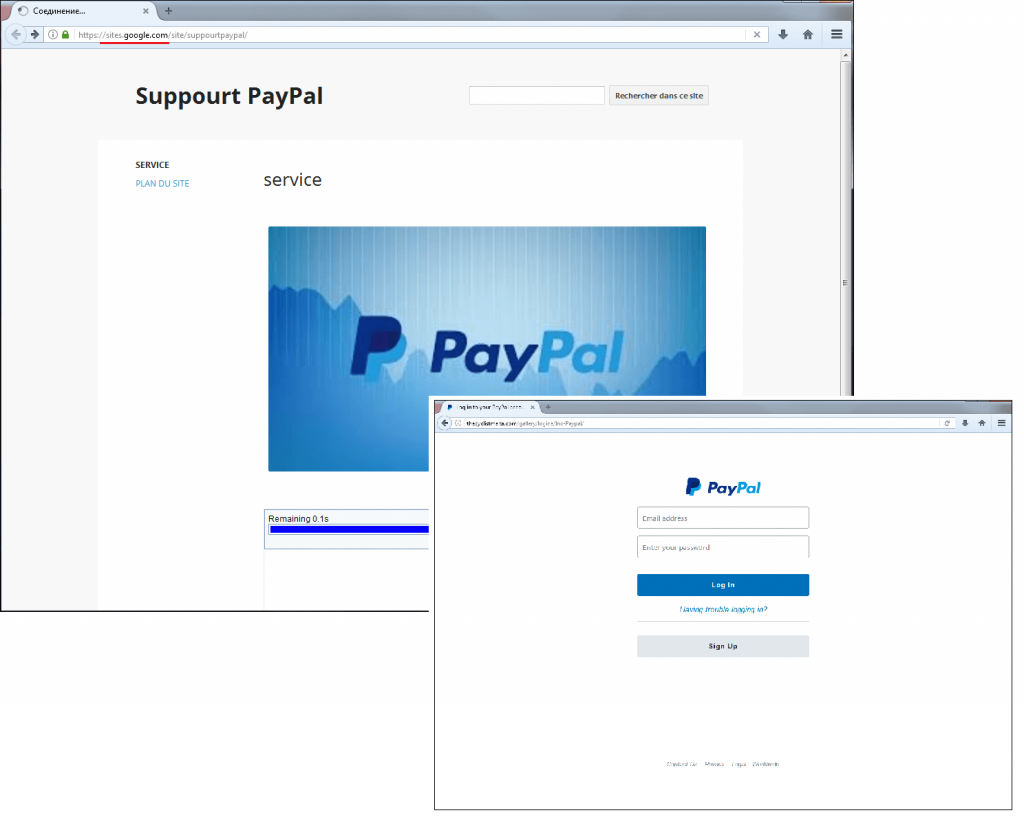
The goal of phishers attacking customers of popular payment systems is to get personal and payment data, login details for accounts, etc. Criminals often place fraudulent content on reputable resources in order to gain the trust of the user and bypass denylisting. For example, we came across a fake PayPal support page located on the Google Sites service (the primary domain is google.com). After clicking on the banner, the user is redirected to a phishing page, where they are asked to enter their account data for the payment system.
Phishing page using the PayPal brand located on the Google domain
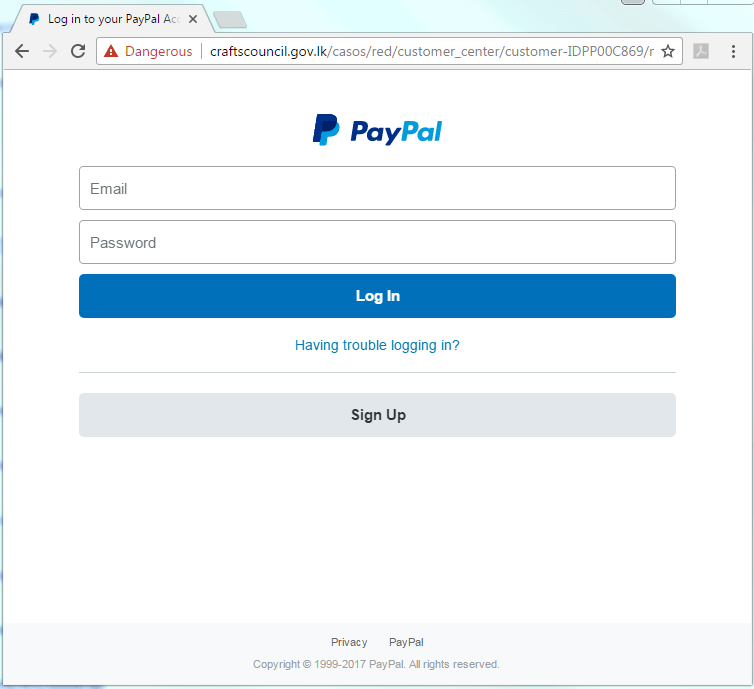
Another trick used by phishers is to place phishing content on the servers of government agencies. This is possible because a significant number of government agencies do not pay much attention to the security of their web resources.
Phishing page using the PayPal brand located on a server belonging to Sri Lankan government
Phishing page using the PayPal brand located on a server belonging to the Bangladesh government
Emails threatening to block an account or asking to update data in a payment system were used as bait.
Online stores
Every tenth phishing attack targeted users of online stores. In Q1 2017, Amazon (39.13%) was the most popular brand with phishers.
| Organization | % |
| Amazon.com: Online Shopping | 39.13 |
| Apple | 15.43 |
| Steam | 6.5 |
| eBay | 5.15 |
| Alibaba Group | 2.87 |
| Taobao | 2.54 |
| Other targets | 28.38 |
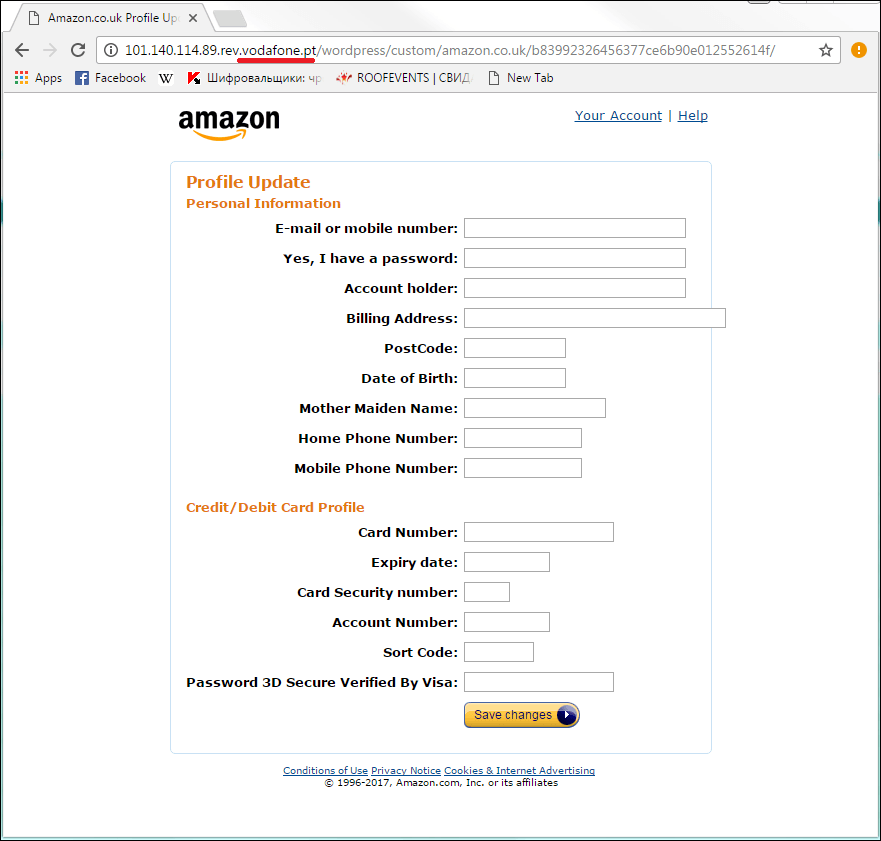
By using the Amazon brand, cybercriminals are trying not only to steal login data but also all the personal information of the user, including their bank card details. Also, they often place fake pages on domains that have a good reputation (for example, on a domain owned by Vodafone).
Phishing page using the Amazon brand located on the Vodafone domain
Earning money with anti-phishing
In addition to standard phishing emails and pages, we often come across other methods of tricking users. Scammers often exploit people’s desire to make easy money by offering cash to view advertising, automatic stock trading programs and much more.
Spam emails offering quick money on the Internet
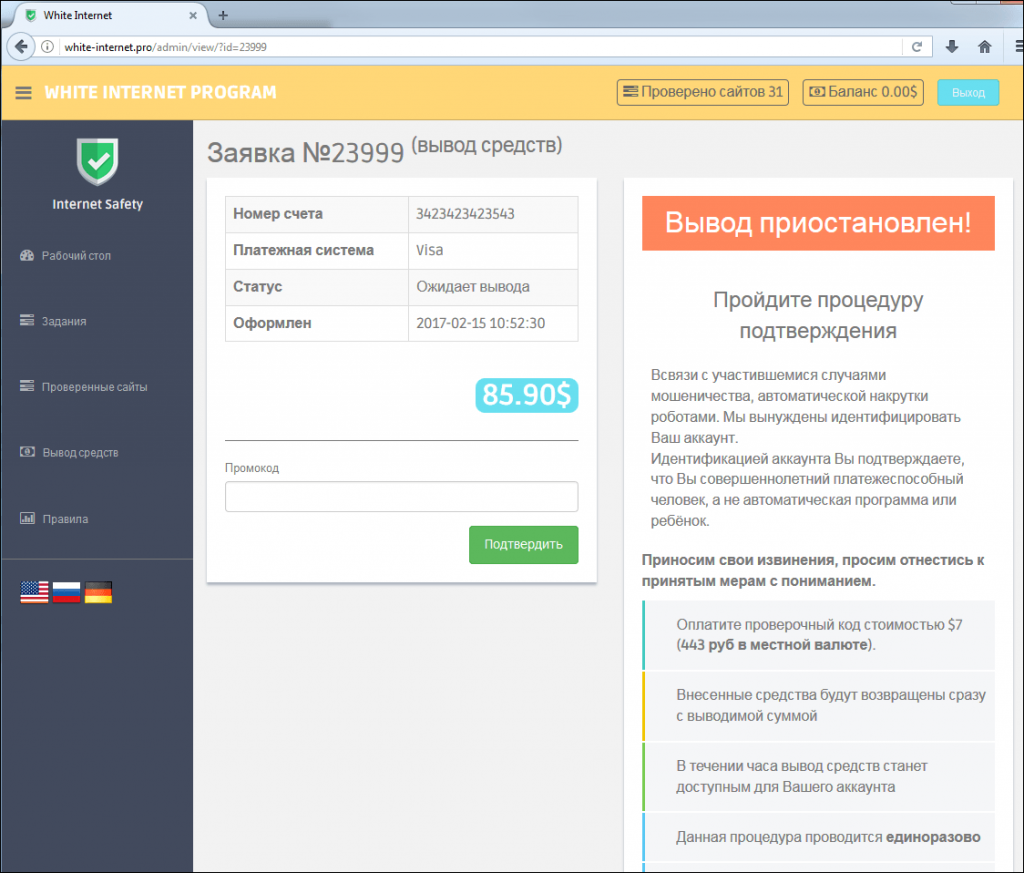
In the first quarter of 2017, we saw a rather interesting fraudulent resource which claimed to be combating phishing sites. All you had to do if you wanted to make some quick cash was to register and perform several tasks, the essence of which was to evaluate web pages using the following options: malicious, safe, does not load. Only the content of the page was evaluated, while its address was not displayed.
After checking 31 sites, it turned out that $7 needed to be paid to withdraw the money that was earned
For each ‘checked’ site, the user earned about $3. To withdraw that money, they had to transfer $7 to the owners of the resource as confirmation that they were an adult and financially solvent. Of course, no ‘earnings’ were ever received after that.
Conclusion
Although the beginning of Q1 2017 was marked by a decline in the amount of spam in overall global email traffic, in March the situation became more stable, and the average share of spam for the quarter amounted to 55.9%. The US (18.75%) remained the biggest source of spam, followed by Vietnam (7.86%) and China (7.77%).
The first quarter of 2017 was also notable for the decrease in the volume of malicious spam sent from the Necurs botnet: the number of such mass mailings decreased significantly compared to the previous reporting period. However, the lull may be temporary: the attackers may have decided to suspend mass mailings until all the hype about encryptors subsides.
Trojan-Downloader.JS.Agent (6.14%) once again topped the rating of the most popular malware families detected in email. Trojan-Downloader.JS.SLoad (3.79%) came second, while Trojan-PSW.Win32.Fareit (3.10%) completed the top three.
In Q1 2017, the Anti-Phishing system was triggered 51,321,809 times on the computers of Kaspersky Lab users. China (20.88%) topped the rating of countries most often attacked by phishers. Financial organizations remained the main target for phishers, and we expect this trend to continue in the future.


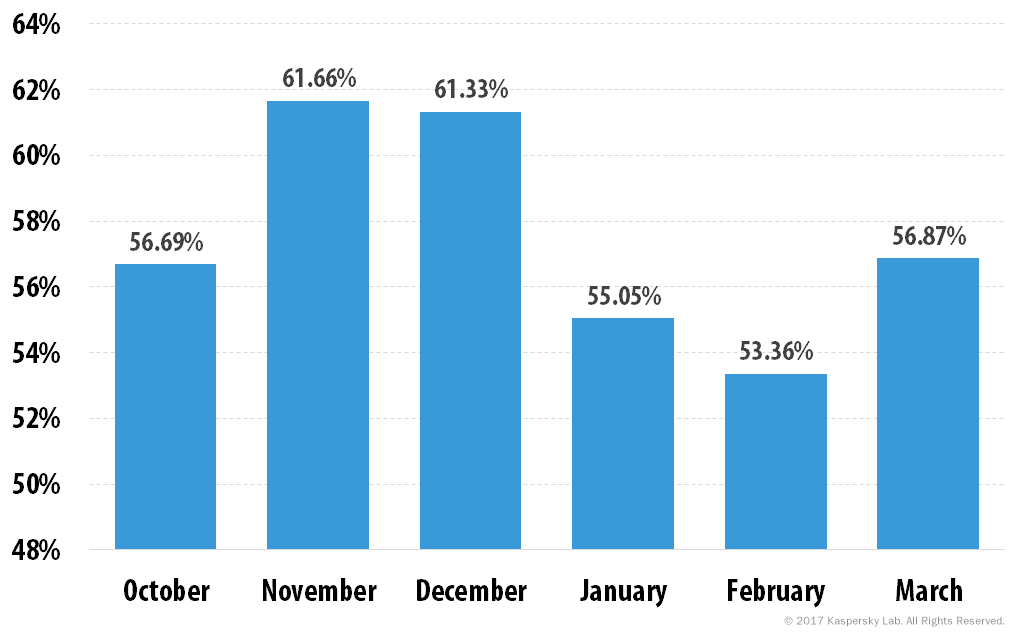
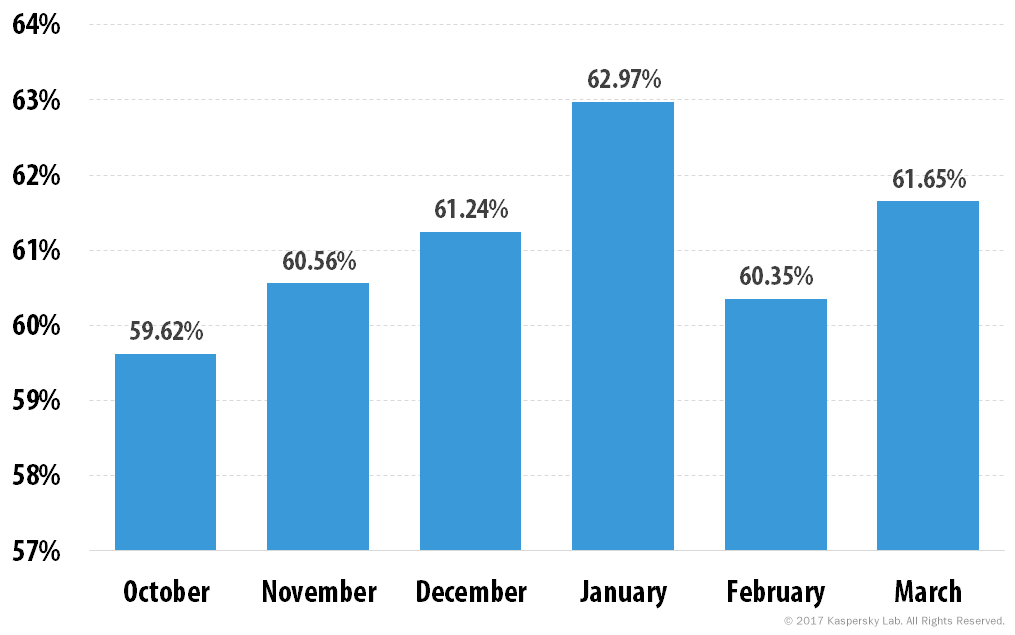




















Spam and phishing in Q1 2017