
Figures of the year
- The share of spam in mail traffic was 56.51%, which is 4.03 p.p. more than in 2018.
- The biggest source of spam this year was China (21.26%).
- 78.44% of spam e-mails were less than 2 KB in size.
- Malicious spam was detected most commonly with the Exploit.MSOffice.CVE-2017-11882 verdict.
- The Anti-Phishing system was triggered 467,188,119 times.
- 15.17% of unique users encountered phishing.
Trends of the year
Beware of novelties
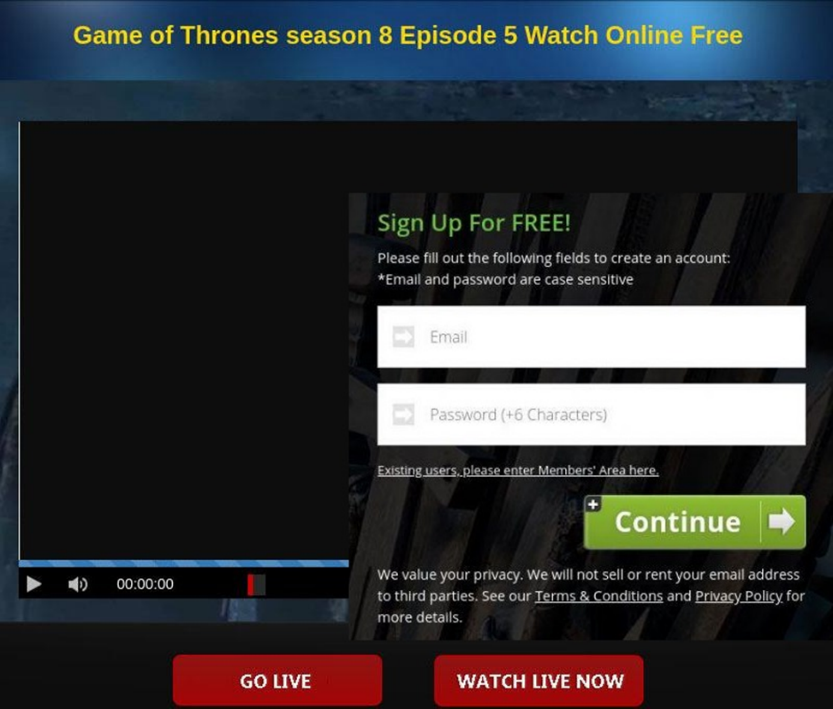
In 2019, attackers were more active than usual in their exploitation of major sports and movie events to gain access to users’ financial or personal data. Premieres of TV shows and films, and sports broadcasts were used as bait for those looking to save money by watching on “unofficial” resources.
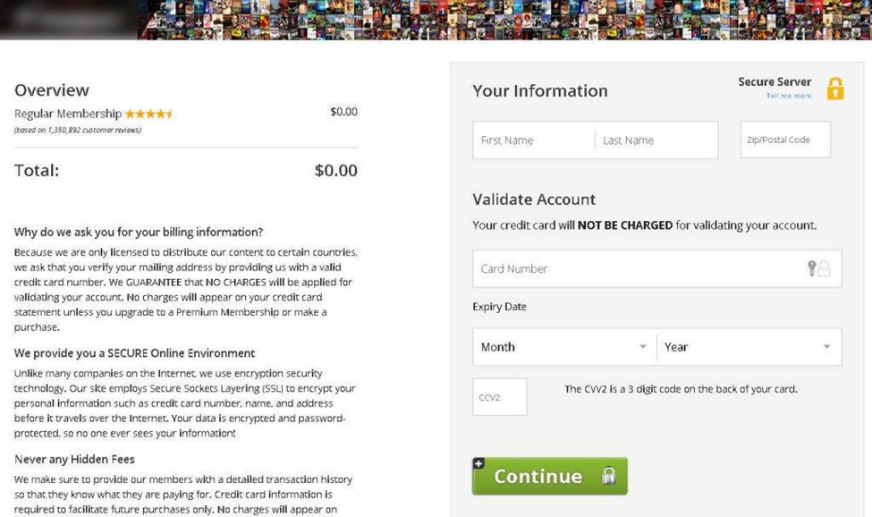
A search for “Watch latest X for free” (where X = Avengers movie, Game of Thrones season, Stanley Cup game, US Open, etc.) returned links to sites offering the opportunity to do precisely that. On clicking through to these resources, the broadcast really did begin, only to stop after a couple of minutes. To continue viewing, the user was prompted to create a free account (only an e-mail address and password were required). However, when the Continue button was clicked, the site asked for additional confirmation.
And not just any old information, but bank card details, including the three-digit security code (CVV) on the reverse side. The site administrators assured that funds would not be debited from the card, but that this data was needed only to confirm the user’s location (and hence right to view the content). However, instead of continuing the broadcast, the scammers simply pocketed the details.
New gadgets were also deployed as a bait. Cybercriminals created fake pages mimicking official Apple services. The number of fake sites rose sharply after the company unveiled its new products. And while Apple was only just preparing to release the next gadget, fraudsters were offering to “sell” it to those with itchy hands. All that victim had to do was follow a link and enter their AppleID credentials — the attackers’ objective.
The price of fame: attackers exploit popular resources
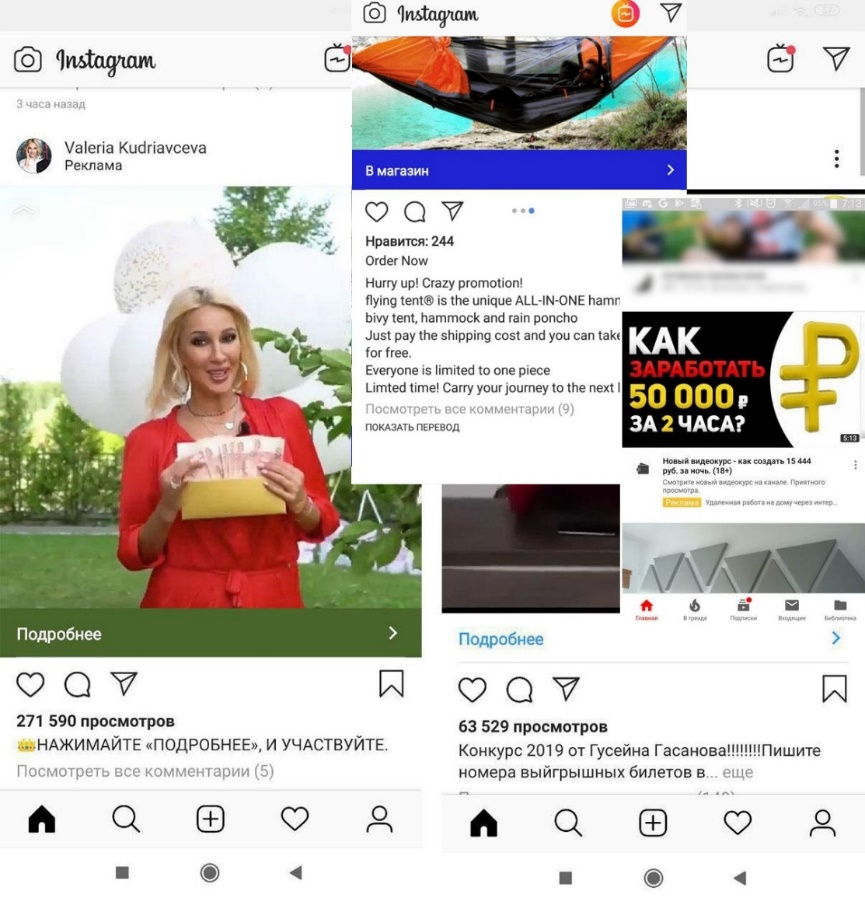
In 2019, scammers found new ways to exploit popular resources and social networks to spread spam and sell non-existent goods and services. They actively used Youtube and Instagram comments to place ads and links to potentially malicious pages, and created numerous social media accounts that they promoted by commenting on the posts of popular bloggers.
For added credibility, they left many fake comments on posts about hot topics. As the account gained a following, it began to post messages about promotions. For example, a sale of branded goods at knock-down prices. Victims either received a cheap imitation or simply lost their cash.
A similar scheme was used to promote get-rich-quick-online videos, coupled with gushing reviews from “newly flush” clients.
Another scam involved fake celebrity Instagram accounts. The “stars” asked fans to take a survey and get a cash payout or the chance to participate in a prize draw. Naturally, a small upfront fee was payable for this unmissable opportunity… After the cybercriminals received the money, the account simply disappeared.
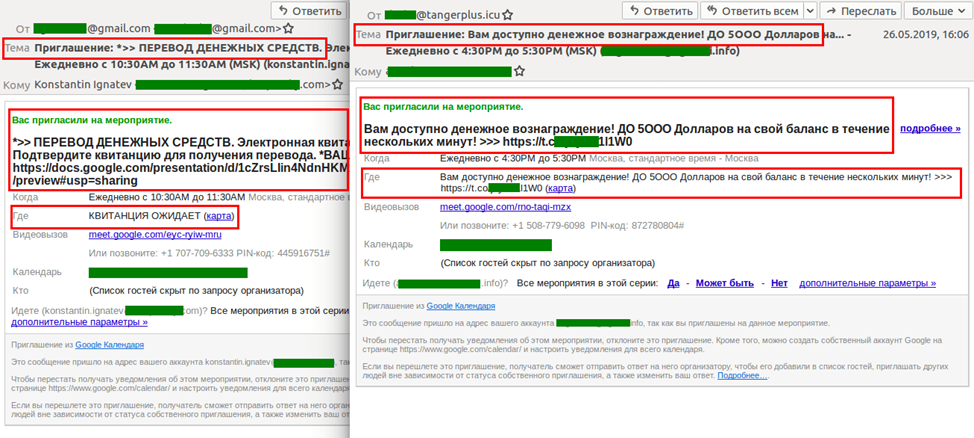
Besides distributing links through comments on social networks, scammers utilized yet another delivery method in the shape of Google services: invitations to meetings sent via Google Calendar or notifications from Google Photos that someone just shared a picture were accompanied by a comment from the attackers with links to fake promotions, surveys, and prize giveaways.
Other Google services were also used: links to files in Google Drive and Google Storage were sent inside fraudulent e-mails, which spam filters are not always able to spot. Clicking it usually opened a file with adware (for example, fake pharmaceutical products) or another link leading to a phishing site or a form for collecting personal data.
Although Google and others are constantly working to protect users from scammers, the latter are forever finding new loopholes. Therefore, the main protection against such schemes is to pay careful attention to messages from unfamiliar senders.
Malicious transactions
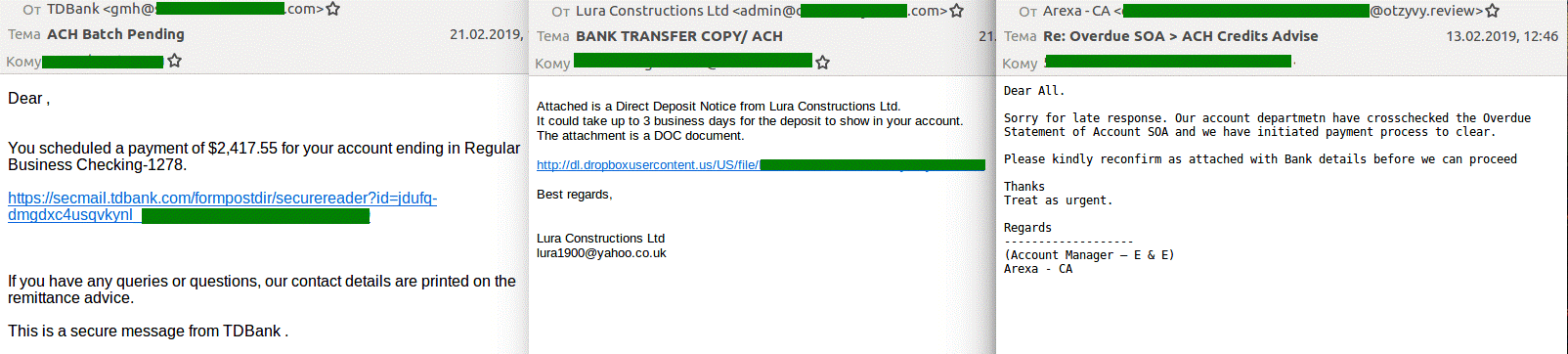
In Q1, users of the Automated Clearing House (ACH), an electronic funds-transfer system that facilitates payments in the US, fell victim to fraudsters: we registered mailings of fake ACH notifications about the status of a payment or debt. By clicking the link or opening the attachment, the user risked infecting the computer with malware.
Anyone order bitcoin?
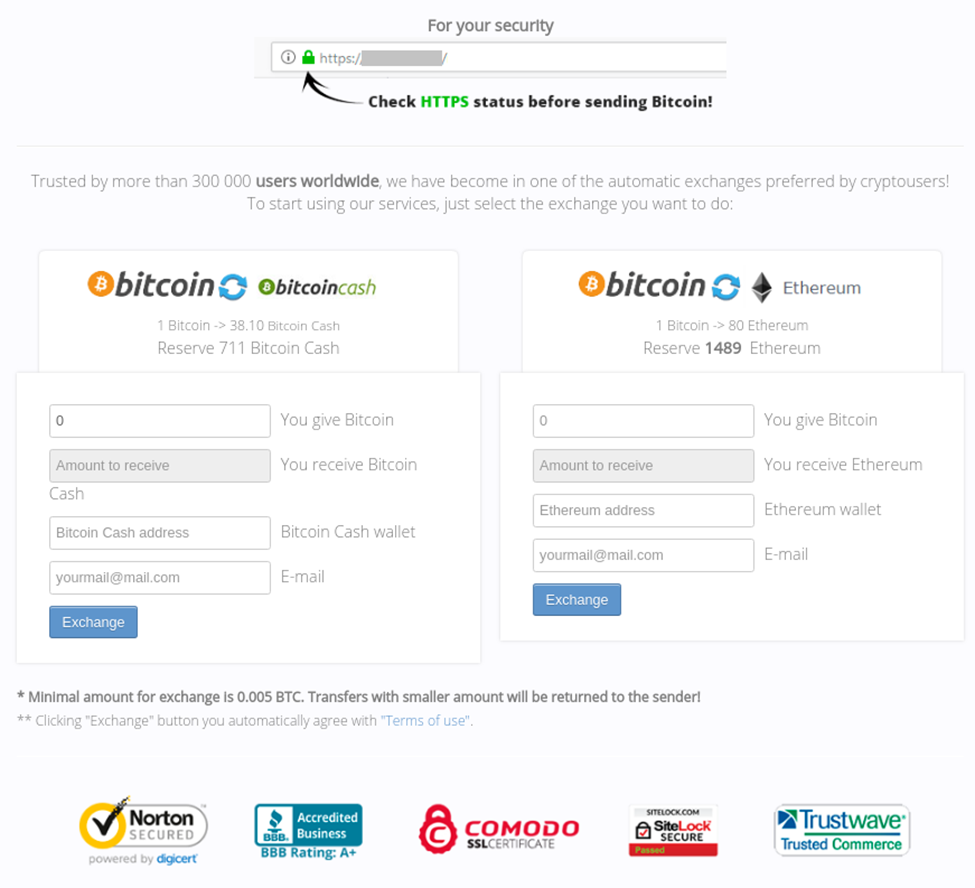
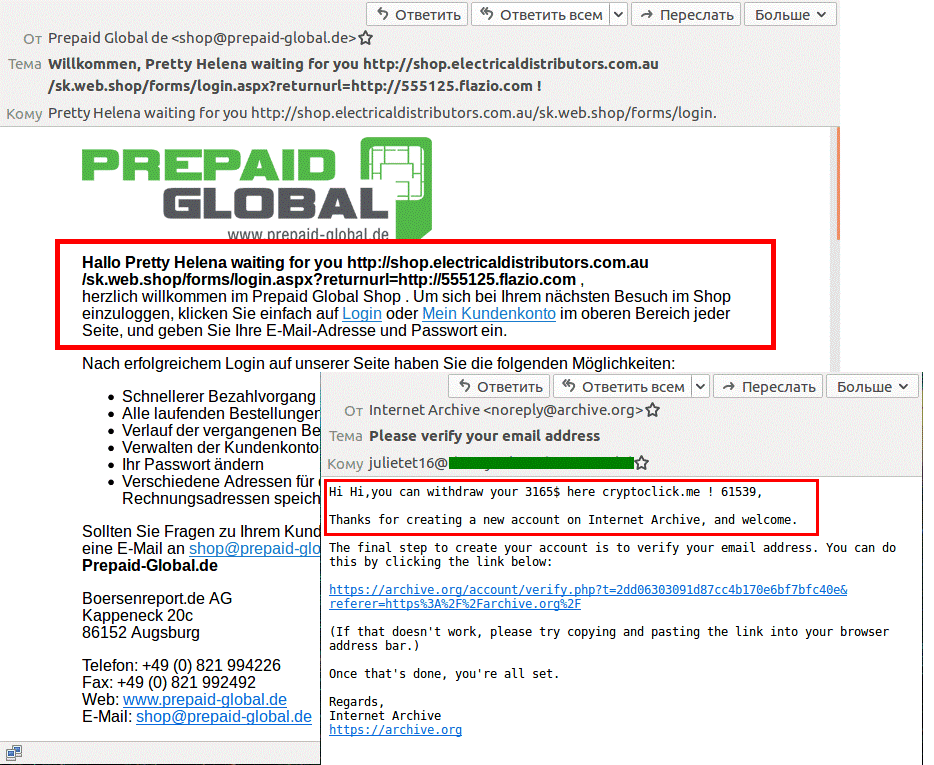
Cryptocurrency continues to be of interest to scammers. Alongside the standard fakes of well-known cryptocurrency exchanges, cybercriminals have started creating their own: such resources promise lucrative exchange rates, but steal either personal data or money.
Cryptocurrencies and blackmail
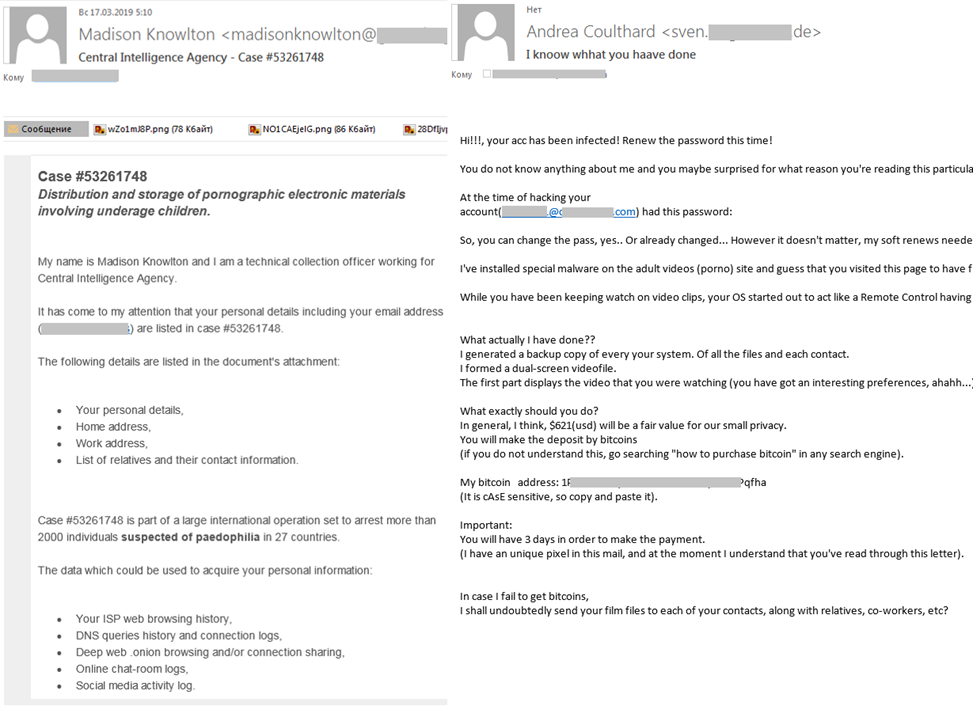
If in 2018 cybercriminals tried to blackmail users by claiming to have malware-obtained compromising material on them, in 2019 e-mails began arriving from a CIA agent (the name varied) supposedly dealing with a case opened against the message recipient pertaining to the storage and distribution of pornographic images of minors.
The case, the e-mail alleged, was part of an international operation to arrest more than 2,000 pedophilia suspects in 27 countries worldwide. However, the “agent” happened to know that the recipient was a well-heeled individual with a reputation to protect, and for $10,000 in bitcoin would be willing to alter or destroy the dossier (all information about the victim to add credence to the e-mail was harvested in advance from social networks and forums). For someone genuinely afraid of the potential consequences, this would be a small price to pay.
Legal entities found themselves in an even more desperate situation when faced with similar threats. However for them it was not about sextortion, but spamming. The blackmailers sent a message to the company using its public e-mail address or online feedback form in which they demanded a ransom in bitcoin. If refused, the attackers threatened to send millions of spam e-mails in the company’s name. This, the cybercriminals assured, would prompt the Spamhaus Project to recognize the resource as a spammer and block it forever.
Corporate sector in the crosshairs
The growing trend for attacks on the corporate sector is reflected not only in the attempts to cyber-blackmail companies. The reputation of many firms has been compromised by spam mailings through feedback forms. Having previously used such forms to attack the mailboxes of company employees, in 2019 cybercriminals evolved their methods.
As such, messages about successful registation on a particular website were received by people who had never even heard about it. After finding a security hole in the site, spammers used a script to bypass the CAPTCHA system and mass-register users via the feedback form. In the Username field, the attackers inserted message text or link. As a result, the victim whose mailing address was used received a registration confirmation e-mail from a legitimate sender, but containing a message from the scammers. Moreover, the company itself had no idea that this was going on.
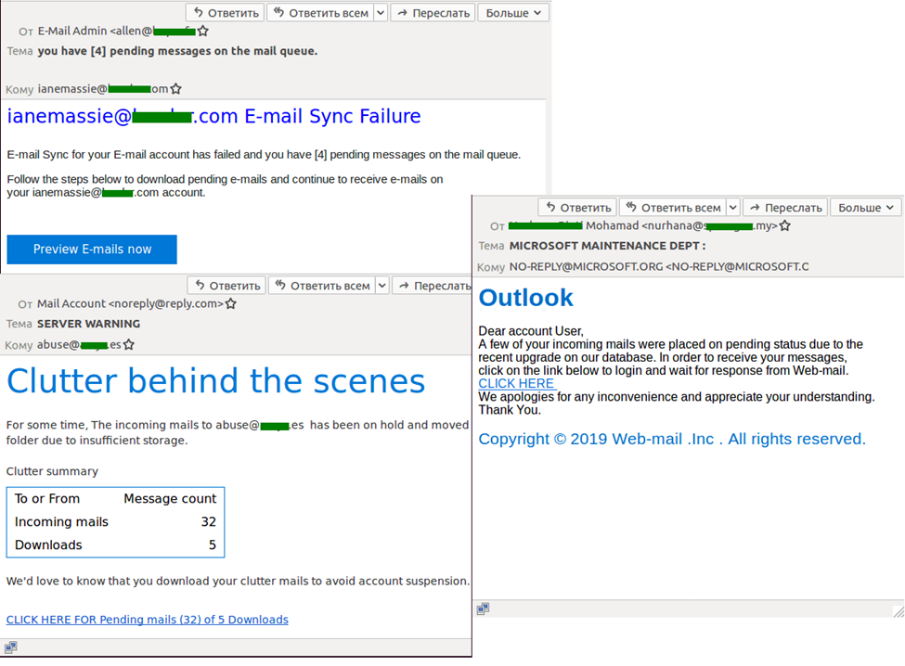
A far more serious threat came from mailings masked as automatic notifications from services used to compile legitimate mailing lists: the scammers’ messages were carefully disguised as notifications about new voice messages (some business products have a feature for exchanging voice messages) or about incoming e-mails stuck in the delivery queue. To access them, the employee had to go through an authentication process, whereupon the corporate account credentials ended up in the hands of the attackers.
Scammers devised new methods to coax confidential data out of unsuspecting company employees. For example, by sending e-mails requesting urgent confirmation of corporate account details or payment information with a link conveniently supplied. If the user swallowed the bait, the authentication data for their account went straight to the cybercriminals.
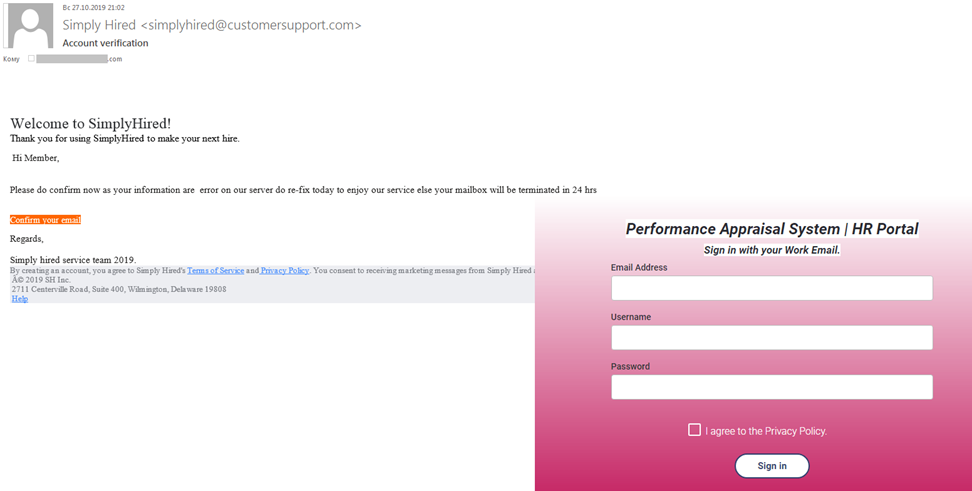
Another attack aimed at the corporate sector employed a more complex scheme: the attackers tried to dupe e-mail recipients into thinking that the company management was offering a pay rise in exchange for taking a performance review.
The message appeared to come from HR and contained detailed instructions and a link to a bogus appraisal form. But before going through the procedure, the recipient had to enter a few details (in most cases it was specified that the e-mail address had to be a corporate one). After clicking the Sign in or Appraisal button, the entered credentials were duly forwarded to the attackers, granting them access to business correspondence, personal data, and probably confidential information too, which could later be used for blackmail or sold to competitors.
A simpler scheme involved sending phishing e-mails supposedly from services used by the company. The most common were fake notifications from HR recruiting platforms.
Statistics: spam
Proportion of spam in mail traffic
The share of spam in mail traffic in 2019 increased by 4.03 p.p. to 56.51%.

Proportion of spam in global mail traffic, 2019 (download)
The lowest figure was recorded in September (54.68%), and the highest in May (58.71%).
Sources of spam by country
In 2019, as in the year before, China retained its crown as the top spam-originating country. Its share grew significantly from the previous year (up 9.57 p.p.) to 21.26%. It remains ahead of the US (14.39%), whose share increased by 5.35 p.p. In third place was Russia (5.21%).
Fourth position went to Brazil (5.02%), despite shedding 1.07 p.p. Fifth place in 2019 was claimed by France (3.00%), and sixth by India (2.84%), which ranked the same as the year before. Vietnam (2.62%), fourth in the previous reporting period, moved down to seventh.
The TOP 10 is rounded out by Germany, dropping from third to eighth (2.61%, down by 4.56 p.p.), Turkey (2.15%), and Singapore (1.72%).

Sources of spam by country, 2019 (download)
Spam e-mail size
In 2019, the share of very small e-mails continued to grow, but less dramatically than the year before — by just 4.29 p.p. to 78.44%. Meanwhile, the share of e-mails sized 2–5 KB decreased against 2018 by 4.22 p.p. to 6.42%.

Spam e-mails by size, 2019 (download)
The share of larger e-mails (10–20 KB) changed insignificantly, down by 0.84 p.p. But there was more junk mail sized 20–50 KB: such messages accounted for 4.50% (+1.68 p.p) In addition, the number of 50–100 KB sized e-mails rose by almost 1 p.p, amounting to 1.81%.
Malicious mail attachments
Malware families

Number of Mail Anti-Virus triggerings, 2019 (download)
In 2019, our security solutions detected a total of 186 005 096 malicious email attachments. November was the most active month with 19 million Mail Anti-Virus triggerings, while December was the “calmest” — with 7 million fewer.

TOP 10 malware families, 2019 (download)
In 2019, like the year before it, Exploit.Win32.CVE-2017-11882 malicious objects were the most commonly encountered malware (7.24%). They exploited a vulnerability in Microsoft Office that allowed arbitrary code to be executed without the user’s knowledge.
In second place is the Trojan.MSOffice.SAgent family (3.59%), whose members also attack Microsoft Office users. This type of malware consists of a document with a built-in VBA script that secretly loads other malware using PowerShell when the document is opened.
The Worm.Win32.WBVB family (3.11%), which includes executable files written in Visual Basic 6 and classed as untrusted by KSN, rose from fourth place in the rating to third.
Backdoor.Win32.Androm.gen (1.64%), which ranked second in the previous reporting period, dropped to fourth position. This modular backdoor is most often used to download malware onto the victim’s machine.
Fifth place in 2019 was taken by the Trojan.Win32.Kryptik family (1.53%). This verdict is assigned to Trojans that use anti-emulation, anti-debugging, and code obfuscation to make them difficult to analyze.
Trojan.MSIL.Crypt.gen (1.26%) took sixth place, while Trojan.PDF.Badur (1.14%) — a PDF that directs the user to a potentially dangerous site — climbed to seventh.
Eighth position fell to another malicious DOC/DOCX document with a malicious VBA script inside — Trojan-Downloader.MSOffice.SLoad.gen (1.14%), which, when opened, may download ransomware onto the victim’s computer.
In ninth place is Backdoor.Win32.Androm, and propping up the table is Trojan.Win32.Agent (0.92%).
Countries targeted by malicious mailings
As in the previous year, Germany took first place in 2019. Its share remained virtually unchanged: 11.86% of all attacks (+0.35 p.p.). Second place was claimed jointly by Russia and Vietnam (5.77% each) — Russia held this position in the previous reporting period, while Vietnam’s rise to the TOP 3 came from sixth position.

Countries targeted by malicious mailings, 2019 (download)
Lagging behind by just 0.2 p.p. is Italy (5.57%), while the UAE is in fifth place (4.74%), Brazil in sixth (3.88%), and Spain in seventh (3.45%). The TOP 10 is rounded out by the practically neck-and-neck India (2.67%), Mexico (2.63%), and Malaysia (2.39%).
Statistics: phishing
In 2019, the Anti-Phishing system was triggered 467 188 119 times on Kaspersky user computers as a result of phishing redirection attempts (15,277,092 fewer than in 2018). In total, 15.17% of our users were attacked.
Organizations under attack
The rating of organizations targeted by phishing attacks is based on the triggering of the heuristic component in the Anti-Phishing system on user computers. This component detects all instances when the user tries to follow a link in an e-mail or on the Internet to a phishing page in cases when such link has yet to be added to Kaspersky’s databases.
Rating of categories of organizations attacked by phishers
In contrast to 2018, in this reporting period the largest share of heuristic component triggers fell to the Banks category. Its slice increased by 5.46 p.p. to 27.16%. Last year’s leader, the Global Internet Portals category, moved down a rung to second. Against last year, its share decreased by 3.60 p.p. (21.12%). The Payment Systems category remained in third place, its share in 2019 amounting to 16.67% (-2.65 p.p.).

Distribution of organizations subject to phishing attacks by category, 2019 (download)
Attack geography
Countries by share of attacked users
This period’s leader by percentage of attacked unique users out of the total number of users was Venezuela (31.16%).
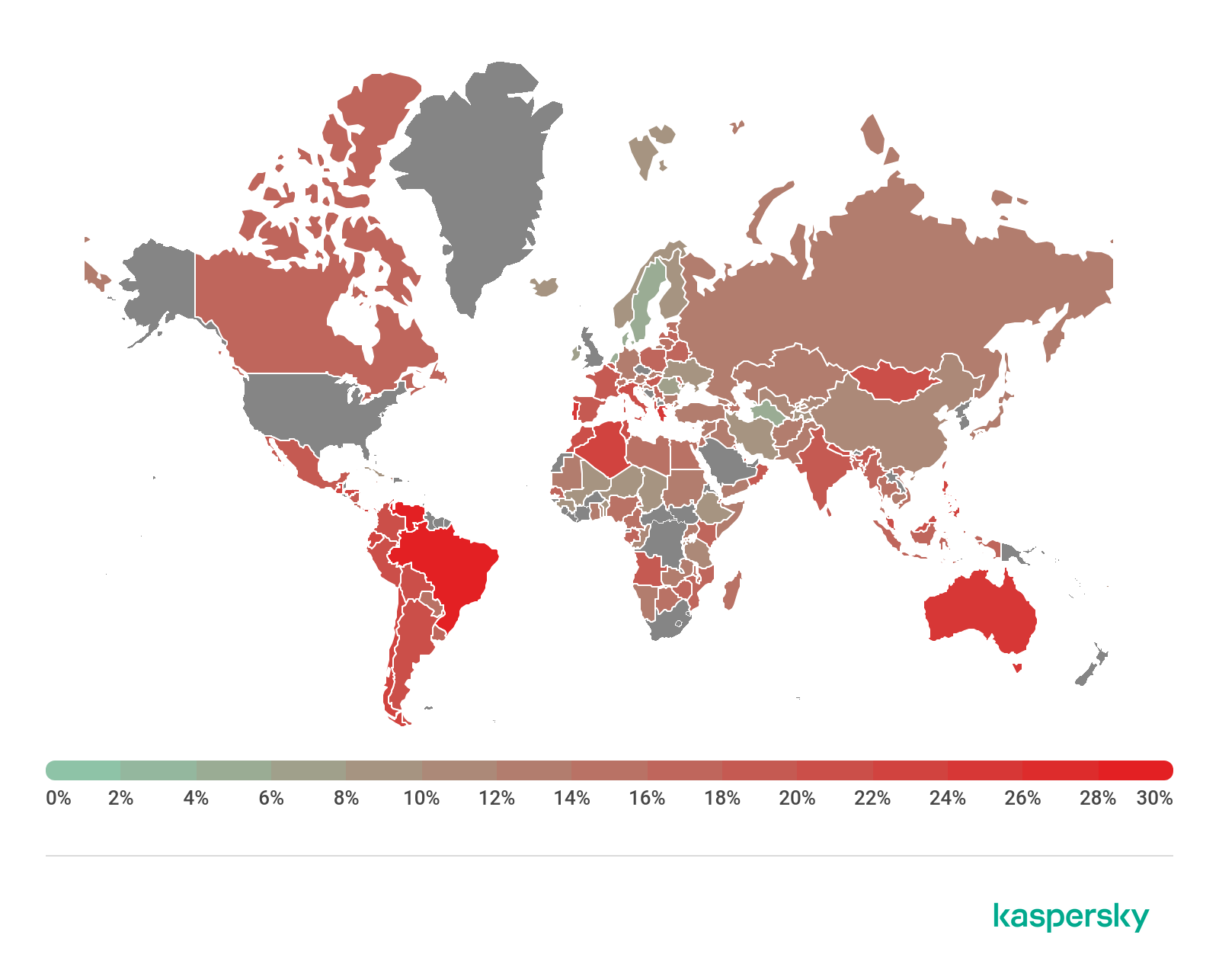
Percentage of users on whose computers the Anti-Phishing system was triggered out of all Kaspersky users in the country, 2019 (download)
TOP 10 countries by share of attacked users
| Country | % |
| Venezuela | 31.16 |
| Brazil | 30.26 |
| Greece | 25.96 |
| Portugal | 25.63 |
| Australia | 25.24 |
| Algeria | 23.93 |
| Chile | 23.84 |
| Réunion | 23.82 |
| Ecuador | 23.53 |
| French Guiana | 22.94 |
TOP 10 countries by share of attacked users
Last year’s leader, Brazil (30.26%), this year found itself in second place, shedding 1.98 p.p. and ceding top spot to Venezuela (31.16%), which moved up from ninth position, gaining 11.27 p.p. In third place was TOP 10 newcomer Greece (25.96%).
Wrap-up
TV premieres, high-profile sporting events, and the release of new gadgets were exploited by scammers to steal users’ personal data or money.
In the search for new ways to bypass spam filters, attackers are developing new methods of delivering their messages. This year, they made active use of various Google services, as well as popular social networks (Instagram) and video hosting sites (YouTube).
Cybercriminals continue to use the topic of finance in schemes aimed at gaining access to users’ personal data, infecting computers with malware, or stealing funds from victims’ accounts.
The main trend of 2019 was the rise in the number of attacks on the corporate sector. Fraudulent schemes previously used to repeatedly attack ordinary users changed direction, adding new intricacies to cybercriminal tactics.






















Spam and phishing in 2019