Quarterly highlights
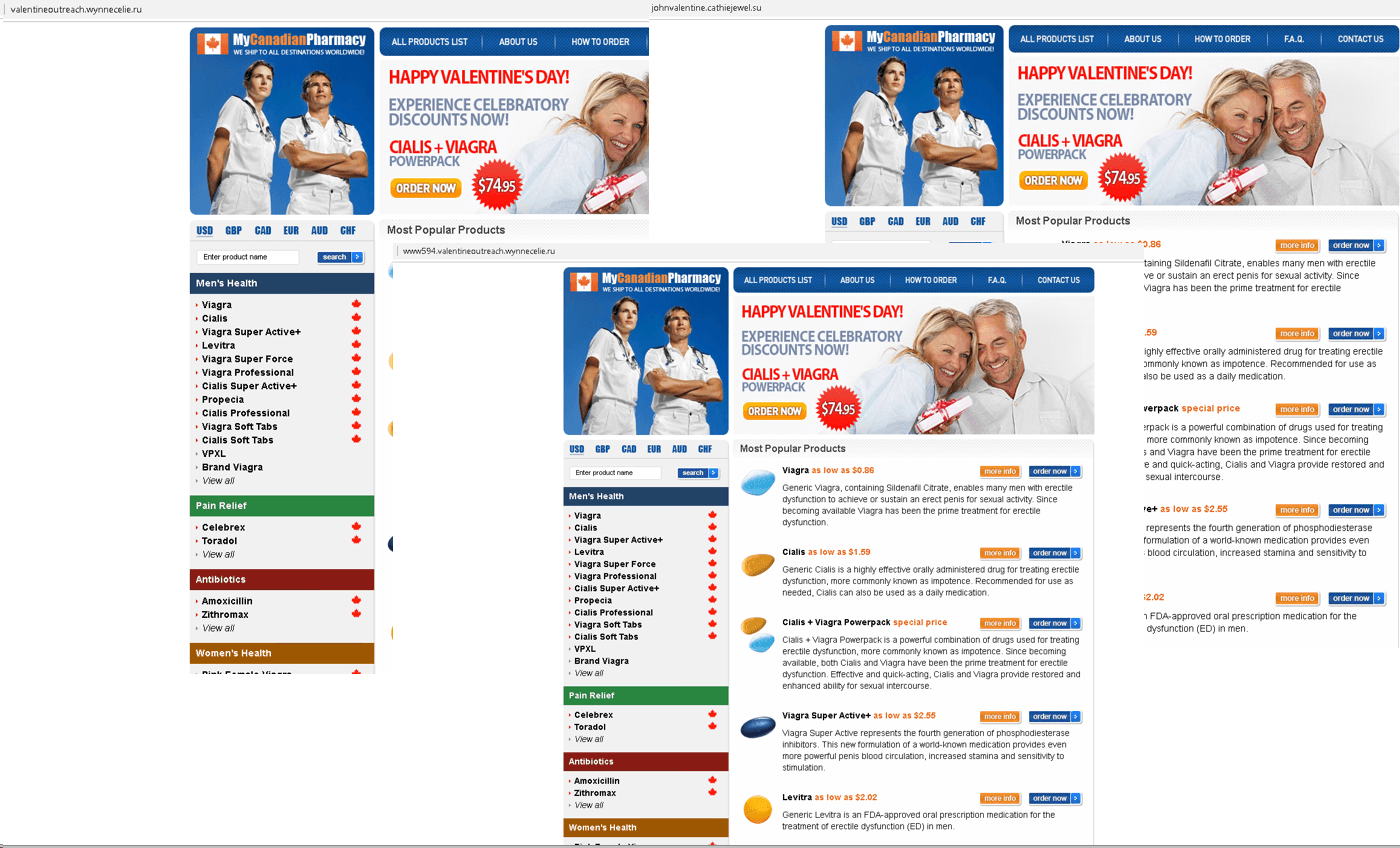
Valentine’s Day
As per tradition, phishing timed to coincide with lovey-dovey day was aimed at swindling valuable confidential information out of starry-eyed users, such as bank card details. The topics exploited by cybercriminals ranged from online flower shops to dating sites.
But most often, users were invited to order gifts for loved ones and buy medications such as Viagra. Clicking/tapping the link in such messages resulted in the victim’s payment details being sent to the cybercriminals.
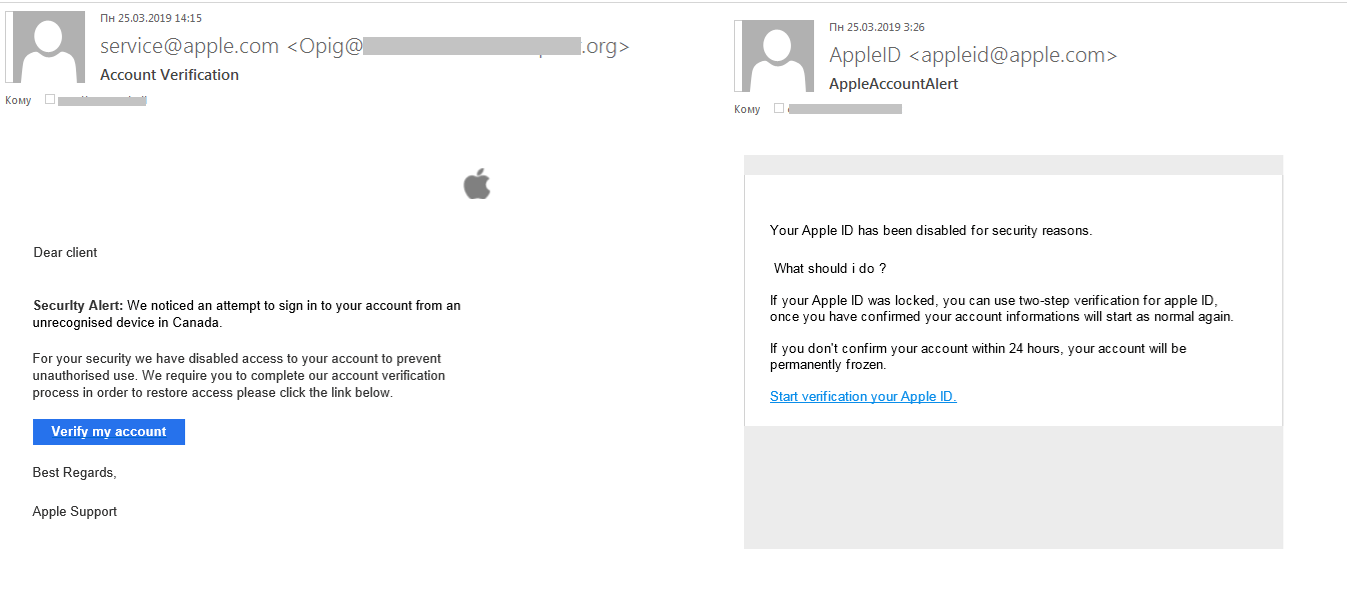
New Apple products
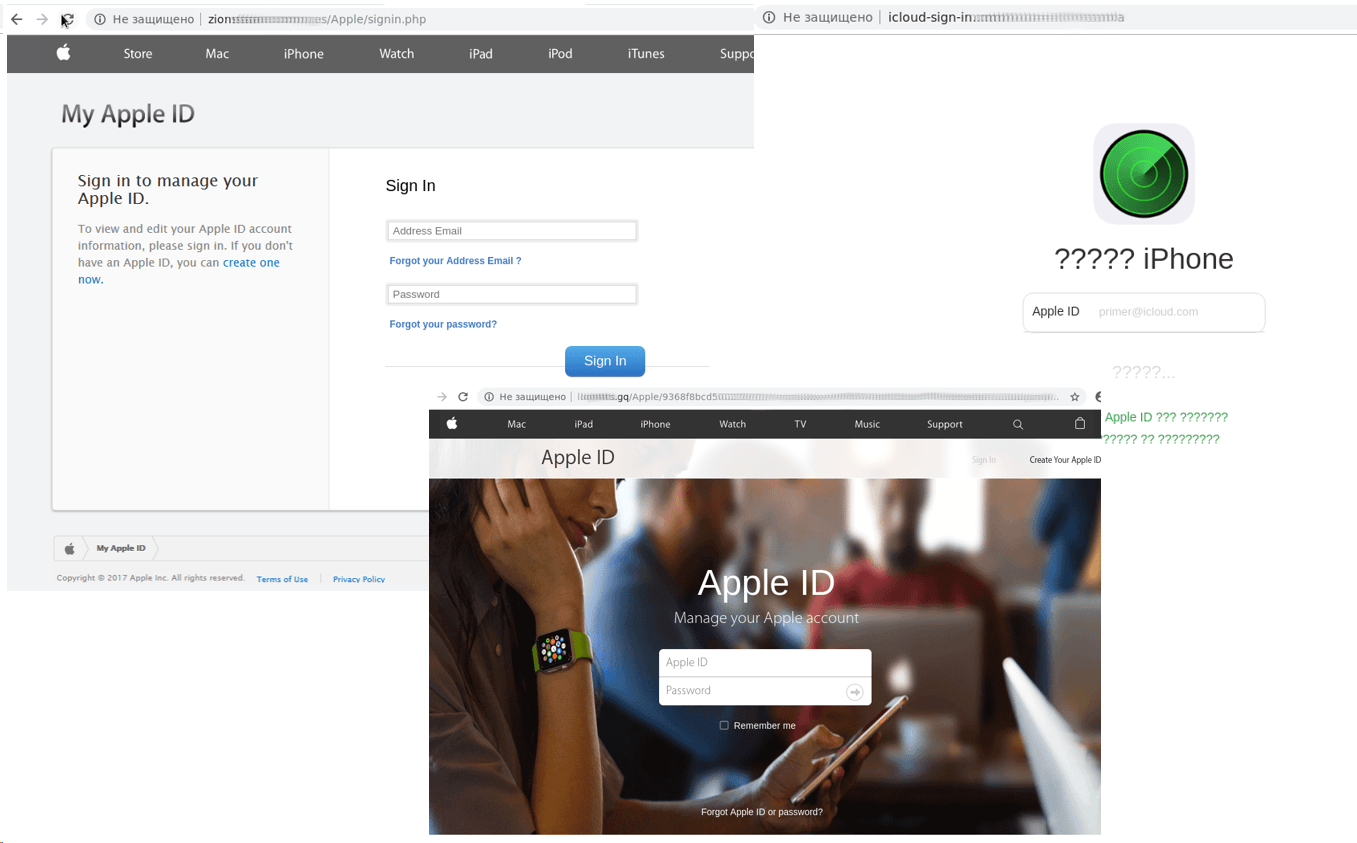
Late March saw the unveiling of Apple’s latest products, which fraudsters were quick to pounce on, as usual. In the run-up to the event, the number of attempts to redirect users to scam websites imitating official Apple services rose significantly.
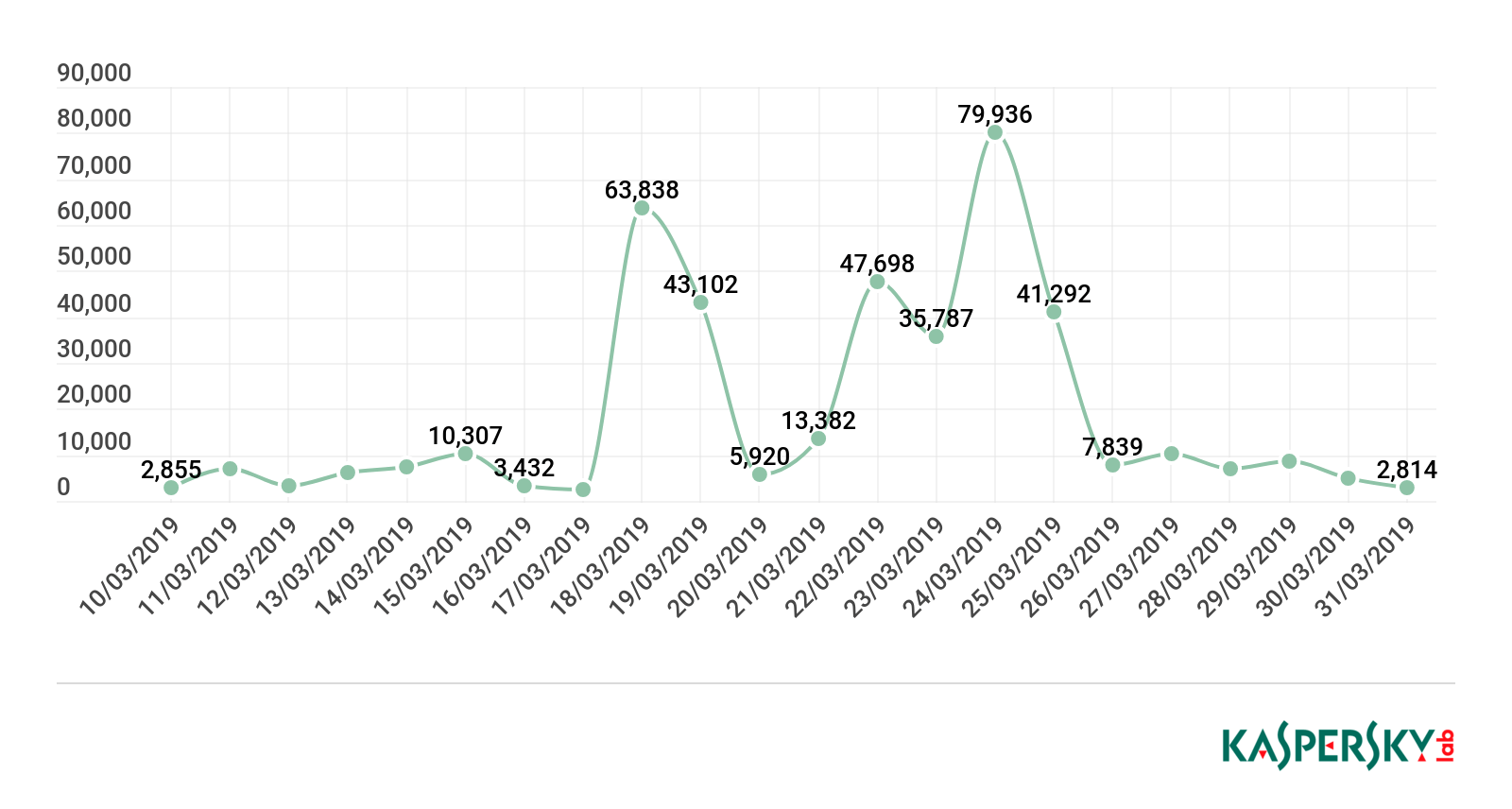
Growth in the number of attempts to redirect users to phishing Apple sites before the presentation
Scammers polluted Internet traffic with phishing emails seemingly from Apple to try to fool recipients into following a link and entering their login credentials on a fake Apple ID login page.
Fake technical support
Fake customer support emails are one of the most popular types of online fraud. The number of such messages has grown quite significantly of late. Links to fake technical support sites (accompanied by rave reviews) can be seen both on dedicated forums and social networks.
All these profiles that we detected in Q1 have one thing in common: they offer assistance in matters related to one or another company products, with the promise of specially trained, highly qualified staff supposedly ready and waiting to help. Needless to say, it is not free. Not only do users not have their issue resolved, they are likely to be defrauded as well.
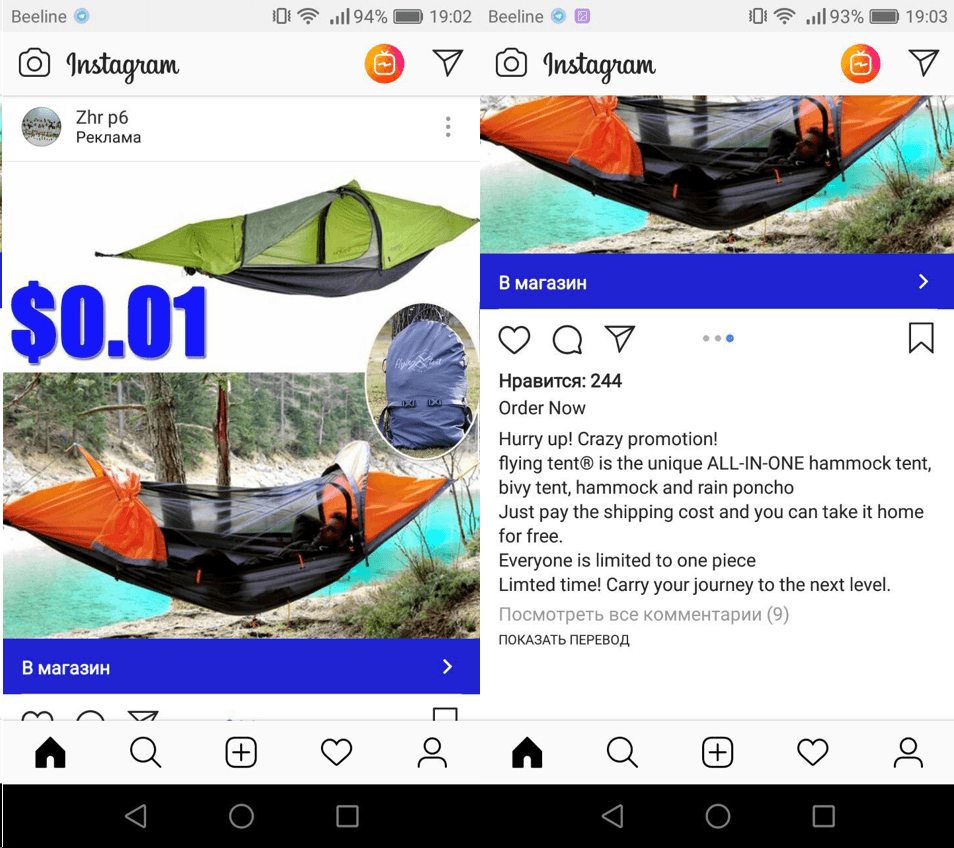
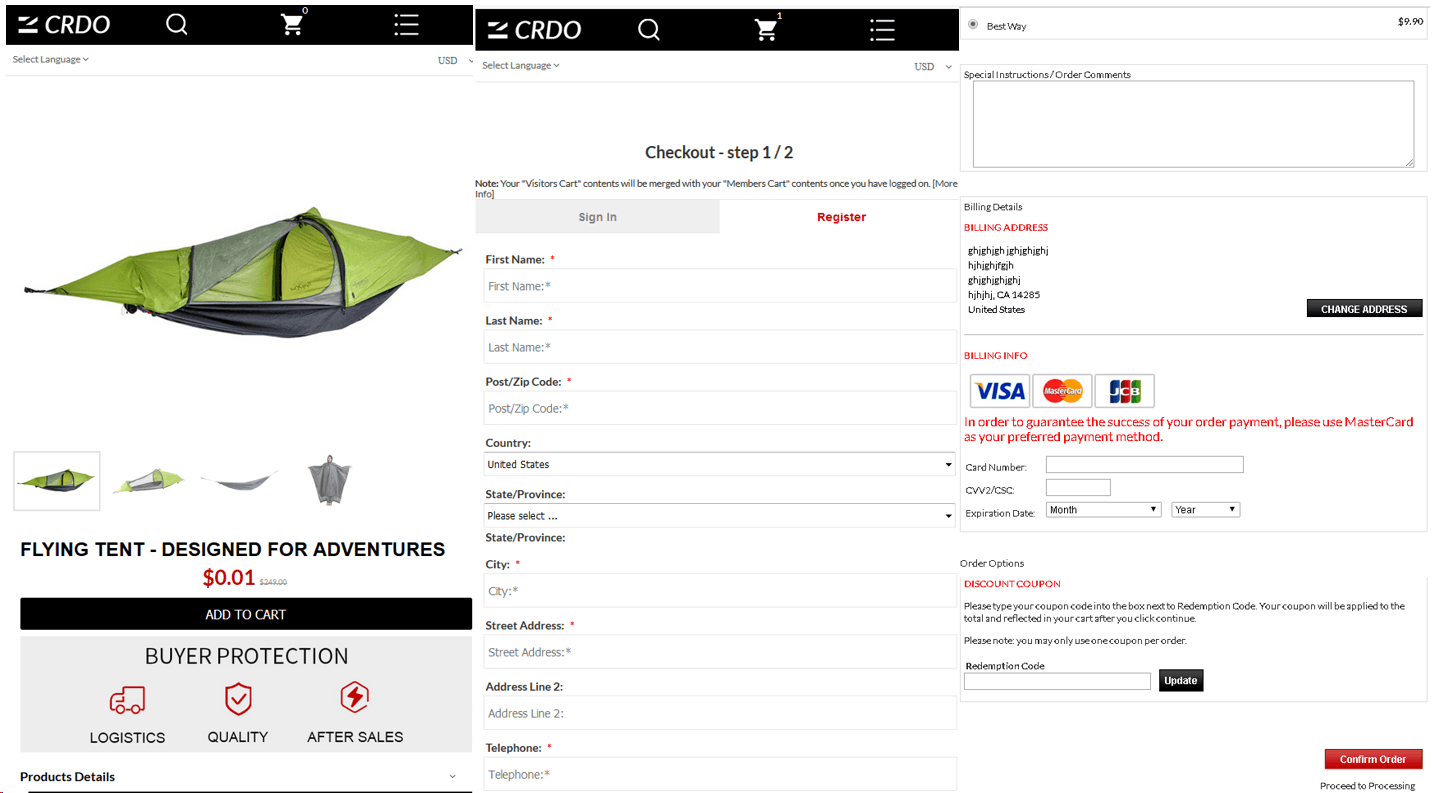
New Instagram “features”
Last year, we wrote that phishers and other scammers had moved beyond mailing lists and into the realm of the popular social network Instagram. This trend continued, with fraudsters exploiting the service to the full — not only leaving links to phishing resources in comments, but also registering accounts, paying for advertising posts, and even enticing celebrities to distribute content.
Cybercriminal advertisers use the same methods to lure victims by promising products or services at what seems a great price.
As usual in such schemes, the “buyer” is asked for all sorts of information, from name to bank details. It goes without saying that all the user gets is their private data compromised.
Mailshot phishing
In Q1, we registered several phishing mailings in the form of automatic notifications seemingly on behalf of major services in charge of managing legitimate mailing lists. Scammers tried to force recipients to follow the phishing links under the pretext of verifying an account or updating payment information. Sometimes fake domains were used with names similar to real services, while other times hacked sites redirected the victim to a fake authorization form.
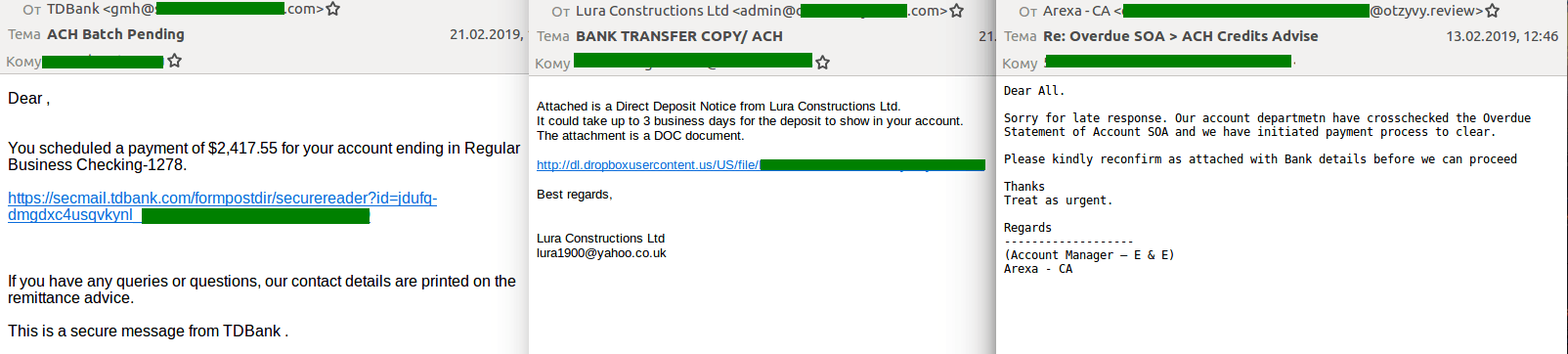
Financial spam through the ACH system
In Q1, we observed a large surge in spam mailings aimed at users of the Automated Clearing House (ACH), a US-based e-payment system that processes vast quantities of consumer and small-business transactions. These mailings consisted of fake notifications about the status of transfers supposedly made by ordinary users or firms. Such messages contained both malicious attachments (archives, documents) and links to download files infected with malware.
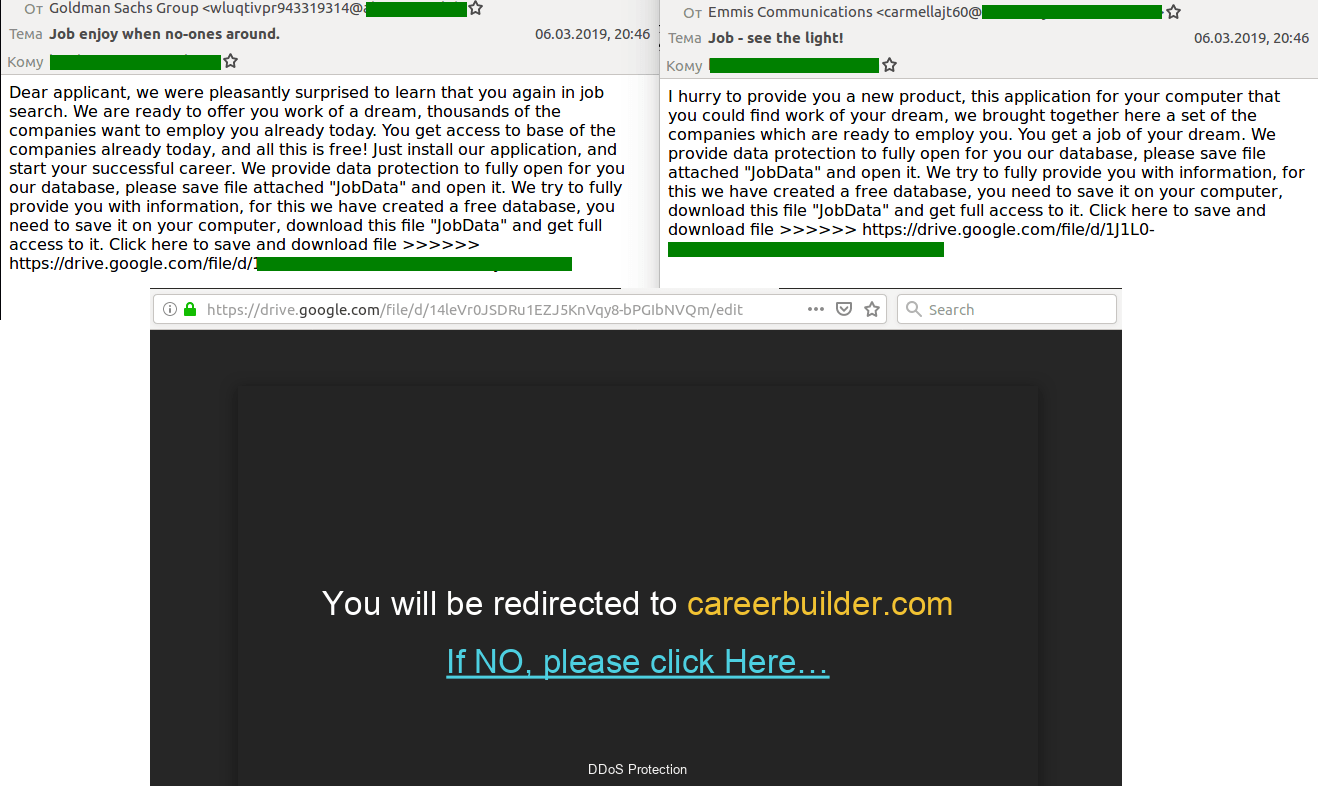
“Dream job” offers from spammers
In Q3, we registered spam messages containing “dream job” offers. This quarter, we logged another major mailing topic: messages were sent supposedly on behalf of well-known companies sure to attract lots of potential applicants. Recipients were invited to register in the job search system for free by installing a special app on their computer to access the database. When trying to download the program from the “cloud service,” the user was shown a pop-up window titled DDoS Protection and a message with a link pointing to the site of an online recruitment company (the names of several popular recruitment agencies were used in the mailing). If the user followed it, a malicious DOC file containing Trojan.MSOffice.SAgent.gen was downloaded to their computer, which in turn downloaded Trojan-Banker.Win32.Gozi.bqr onto the victim’s machine.
Ransomware and cryptocurrency
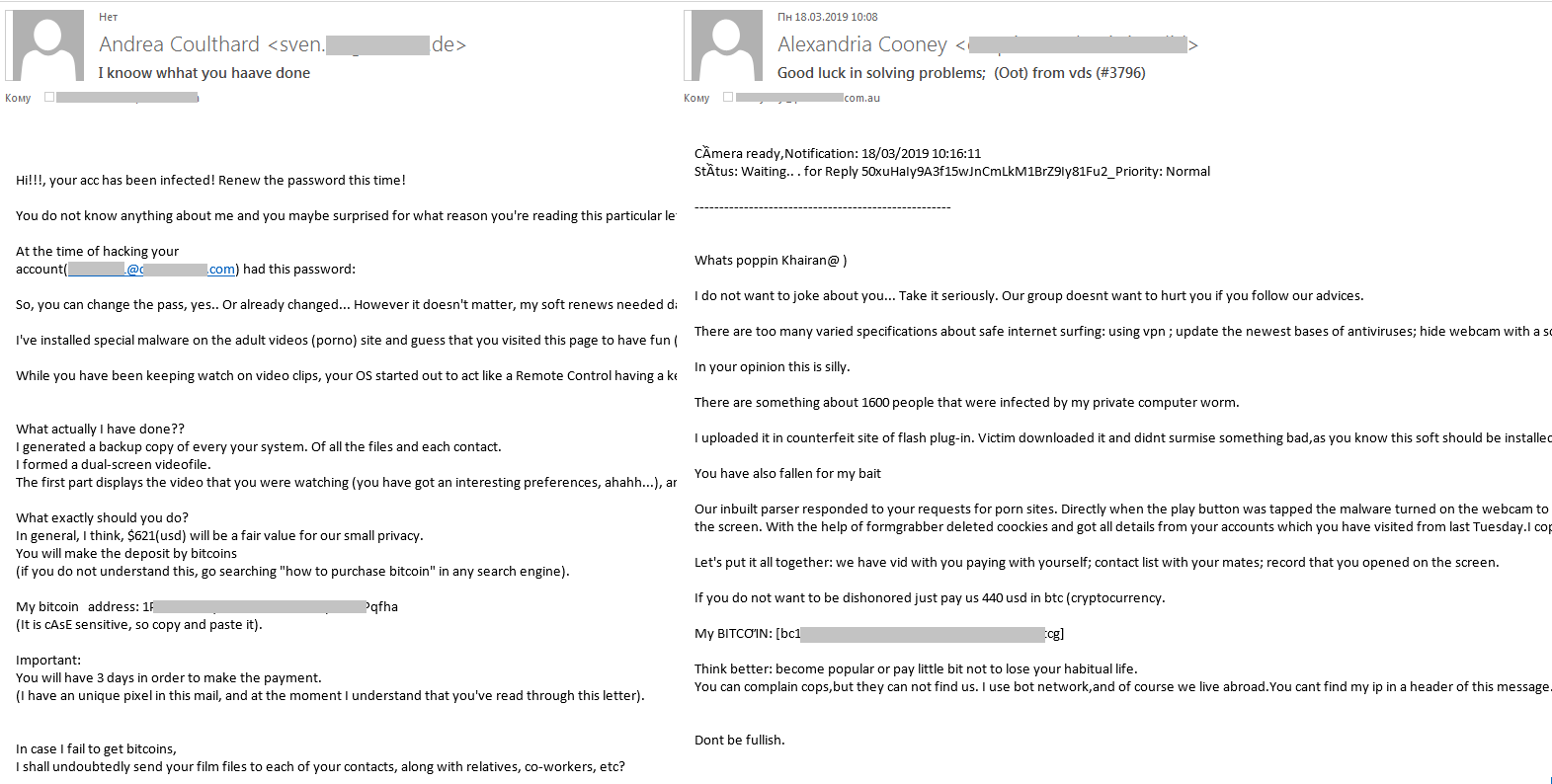
As we expected, cybercriminal interest in cryptocurrency did not wane. Spammers continue to wring cryptocurrency payments out of users by means of “sextortion” — a topic we wrote about last year.
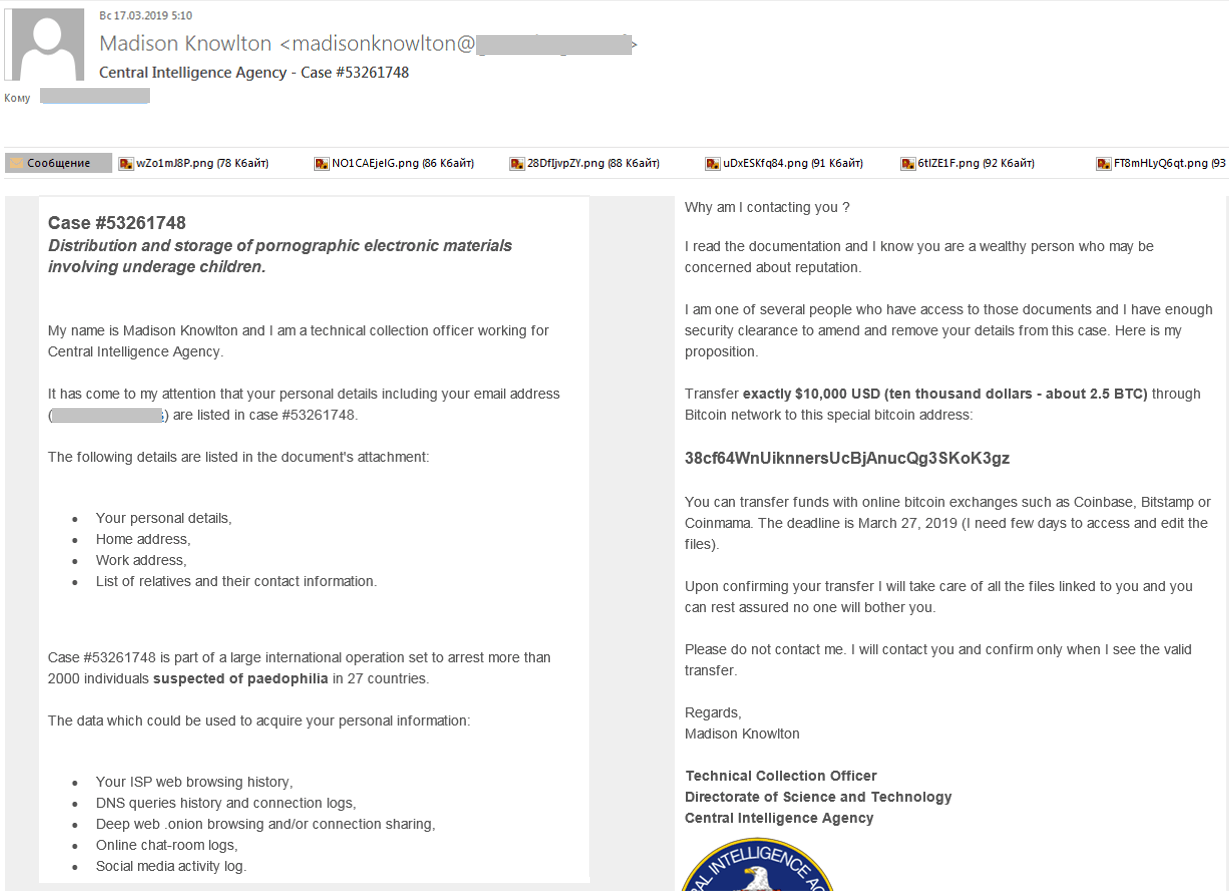
In Q1 2019, we uncovered a rather unusual scam mailing scheme whereby cybercriminals sent messages in the name of a CIA employee allegedly with access to a case file on the recipient for possession and distribution of digital pornographic materials involving minors.
The fictitious employee, whose name varied from message to message, claimed to have found the victim’s details in the case file (which were actually harvested from social networks/online chats/forums, etc.). It was said to be part of an international operation to arrest more than 2,000 pedophilia suspects in 27 countries worldwide. However, the “employee” happened to know that the victim was a well-off individual with a reputation to protect — for which a payment of 10,000 dollars in bitcoin was demanded.
Playing on people’s fear of private data being disclosed, the scammers employed the same tricks as last year, mentioning access to personal data, compromising pornographic materials, etc. But this time, to make the message more convincing and intimidating, a CIA officer was used as a bogeyman.
Malicious attacks on the corporate sector
In Q1, the corporate sector of the Runet was hit by a malicious spam attack. The content imitated real business correspondence, and the messages themselves were seemingly from partners of the victim company.
We also observed malicious mailings aimed at stealing the financial information of international companies through distributing fake messages in the name of a US company allegedly providing information services. Besides the attachment, there was nothing at all in the message. The lack of text was seemingly intended to prompt the victim to open the attached document containing Trojan.MSOffice.Alien.gen, which then downloaded and installed Trojan-Banker.Win32.Trickster.gen on the computer.
Attacks on the banking sector
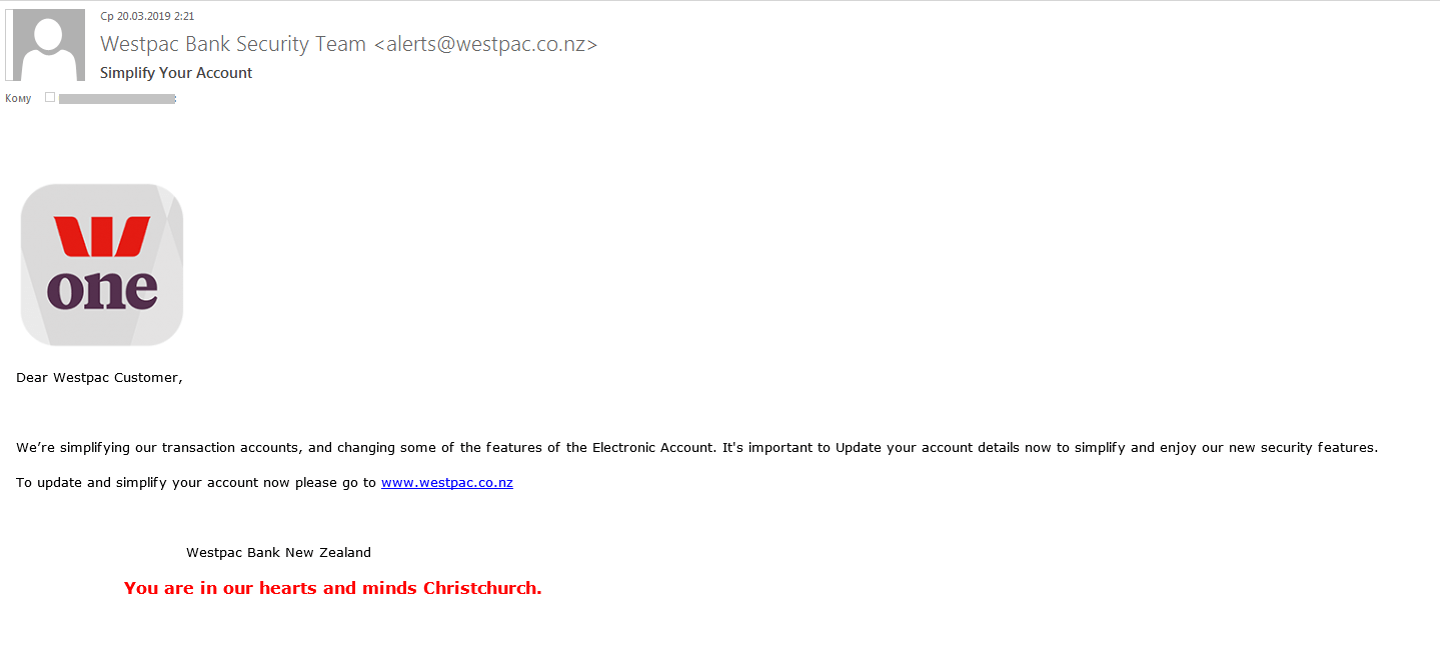
Banks are firmly established as top phishing targets. Scammers try to make their fake messages as believable as possible by substituting legitimate domains into the sender’s address, copying the layout of official emails, devising plausible pretexts, etc. In Q1, phishers exploited high-profile events to persuade victims of the legitimacy of the received message — for example, they inserted into the message body a phrase about the Christchurch terror attack. The attackers hoped that this, plus the name of a New Zealand bank as the sender, would add credibility to the message. The email itself stated that the bank had introduced some new security features that required an update of the account details to use.
The link took the user to a phishing site mimicking the login page of the New Zealand bank in question. All data entered on the site was transferred to the cybercriminals when the Login button was clicked/tapped.
Statistics: spam
Proportion of spam in mail traffic
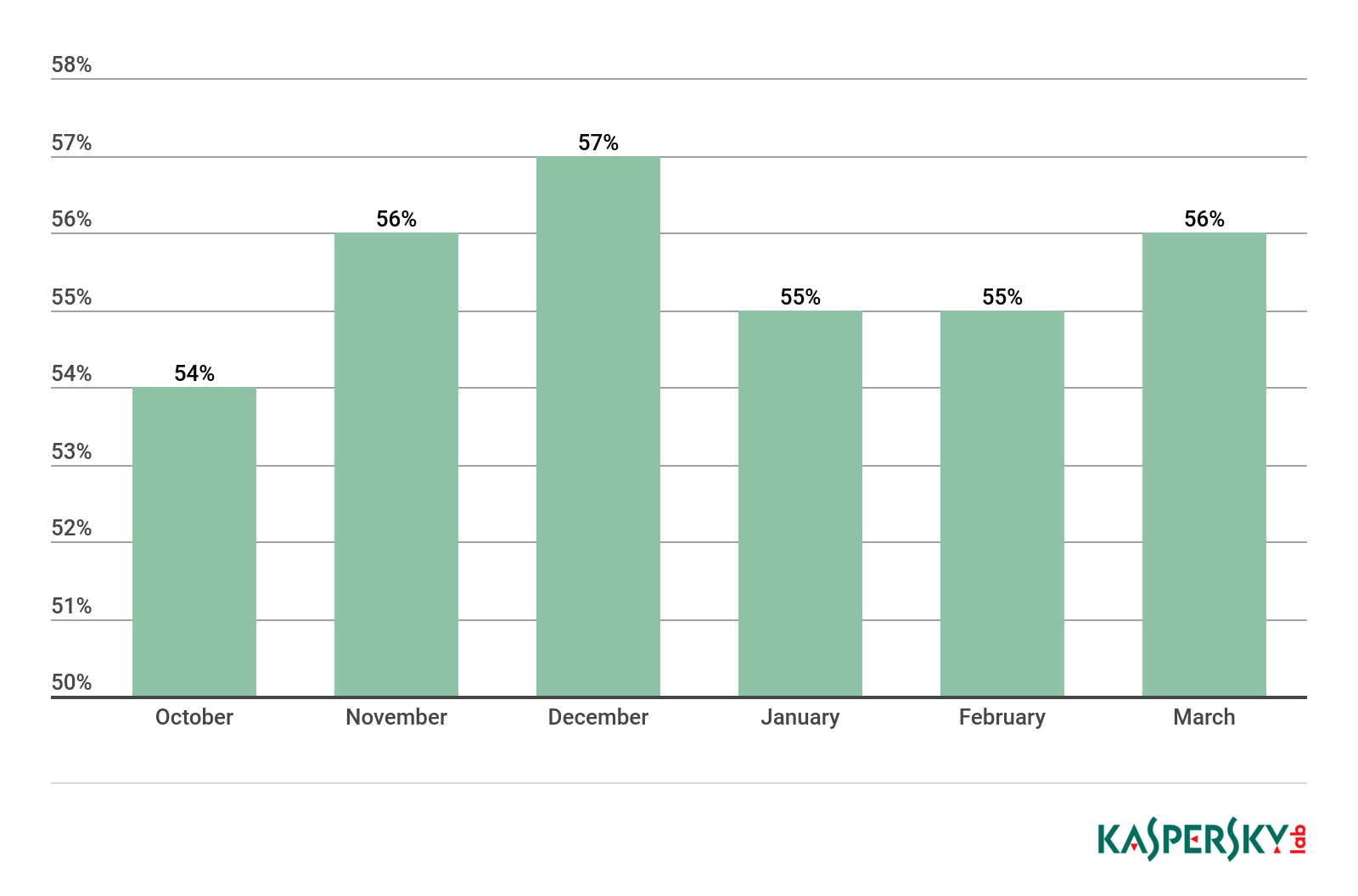
Proportion of spam in global mail traffic, Q4 2018 – Q1 2019
In Q1 2019, the highest percentage of spam was recorded in March at 56.33%. The average percentage of spam in global mail traffic came to 55.97%, which is almost identical (+0.07 p.p.) to Q4 2018.
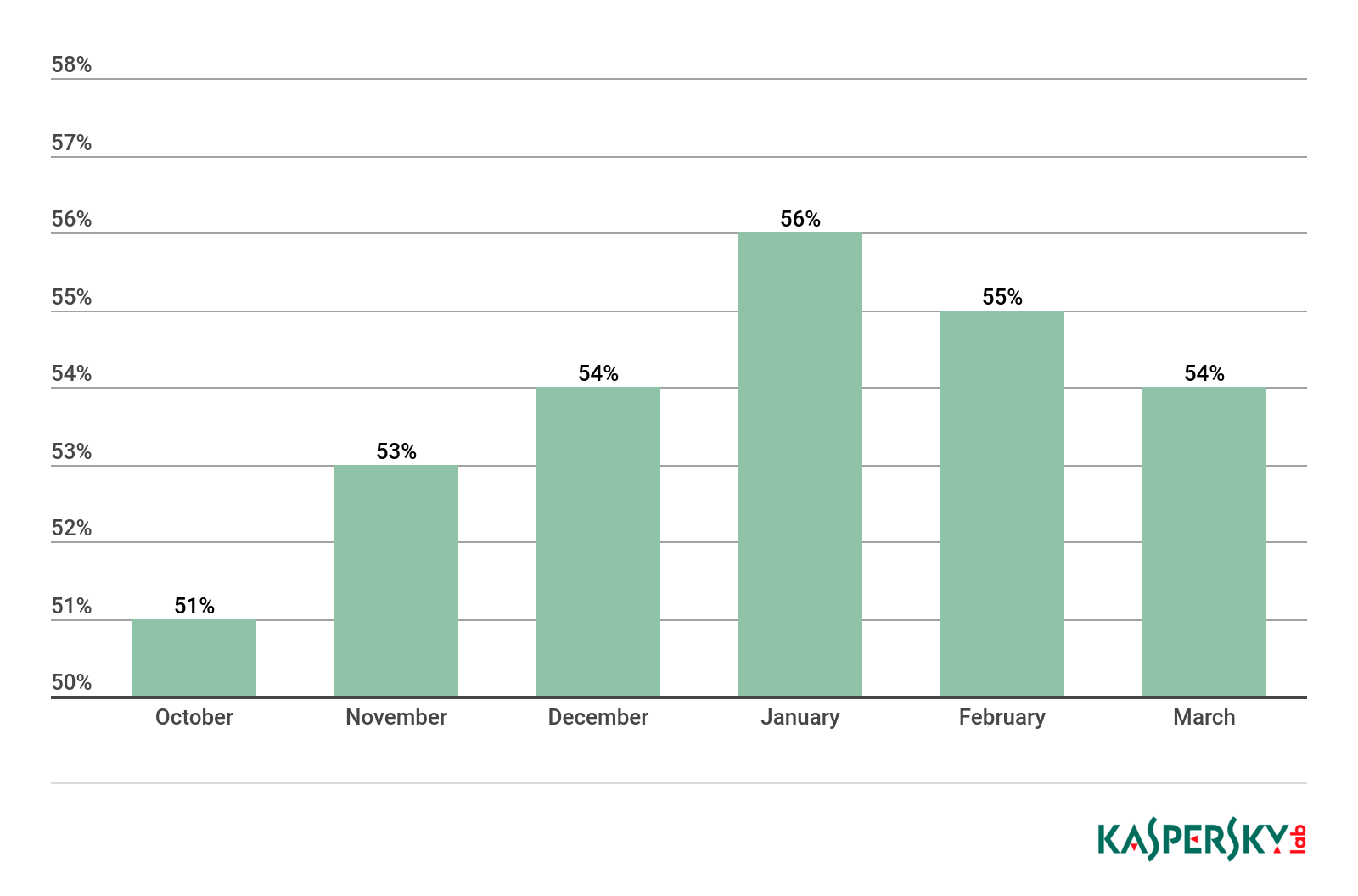
Proportion of spam in Runet mail traffic, Q4 2018 – Q1 2019
Peak spam in traffic in the Russian segment of the Internet came in January (56.19%). The average value for the quarter was 55.48%, which is 2.01 p.p. higher than in Q4.
Sources of spam by country
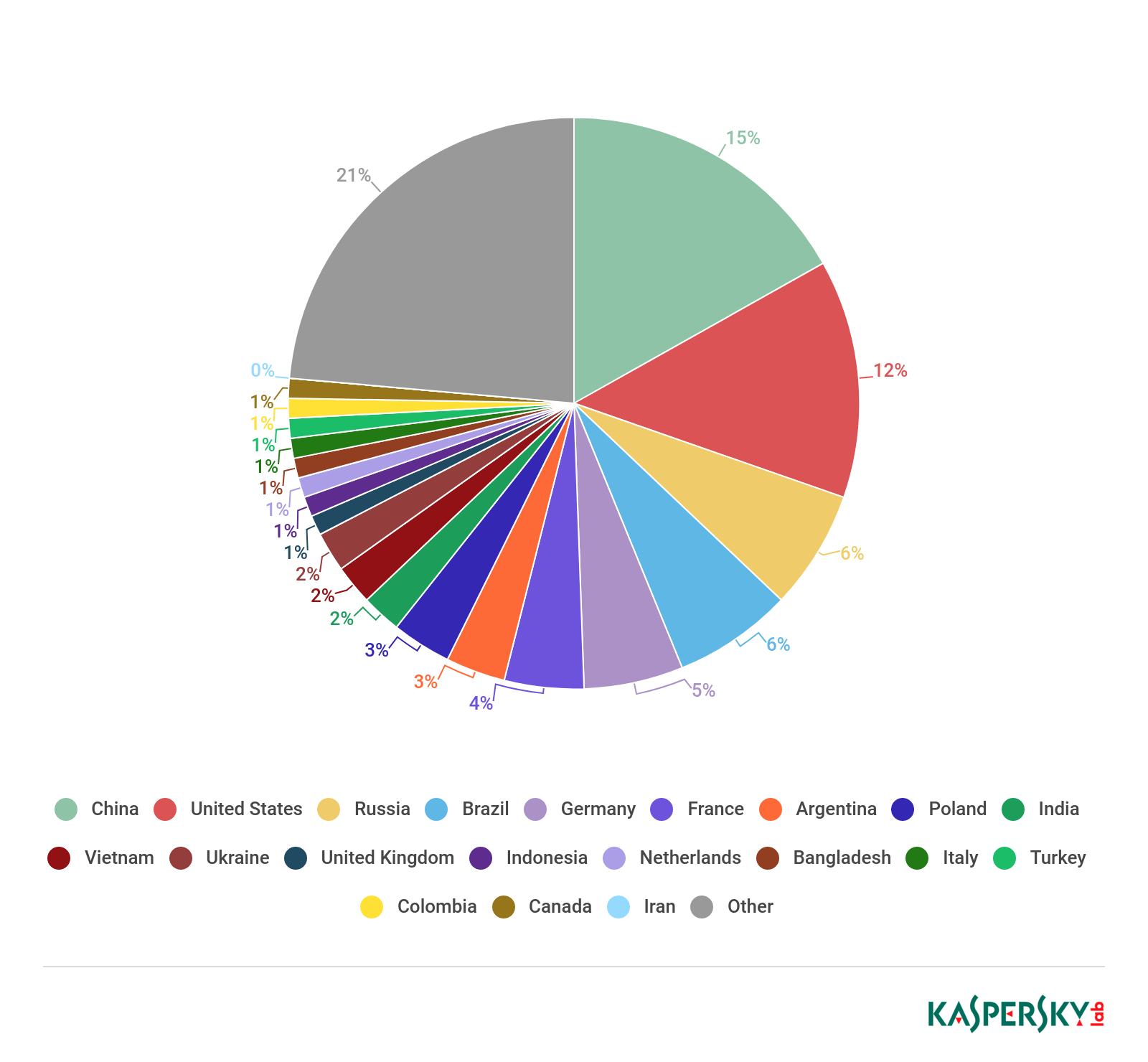
Sources of spam by country, Q1 2019
As is customary, the top spam-originating countries were China (15.82%) and the US (12.64%); the other Top 3 regular, Germany, was down to fifth place in Q1 (5.86%), ceding third place to Russia (6.98%) and allowing Brazil (6.95%) to sneak into fourth. In sixth place came France (4.26%), followed by Argentina (3.42%), Poland (3.36%), and India (2.58%). The Top 10 is rounded off by Vietnam (2.18%).
Spam email size
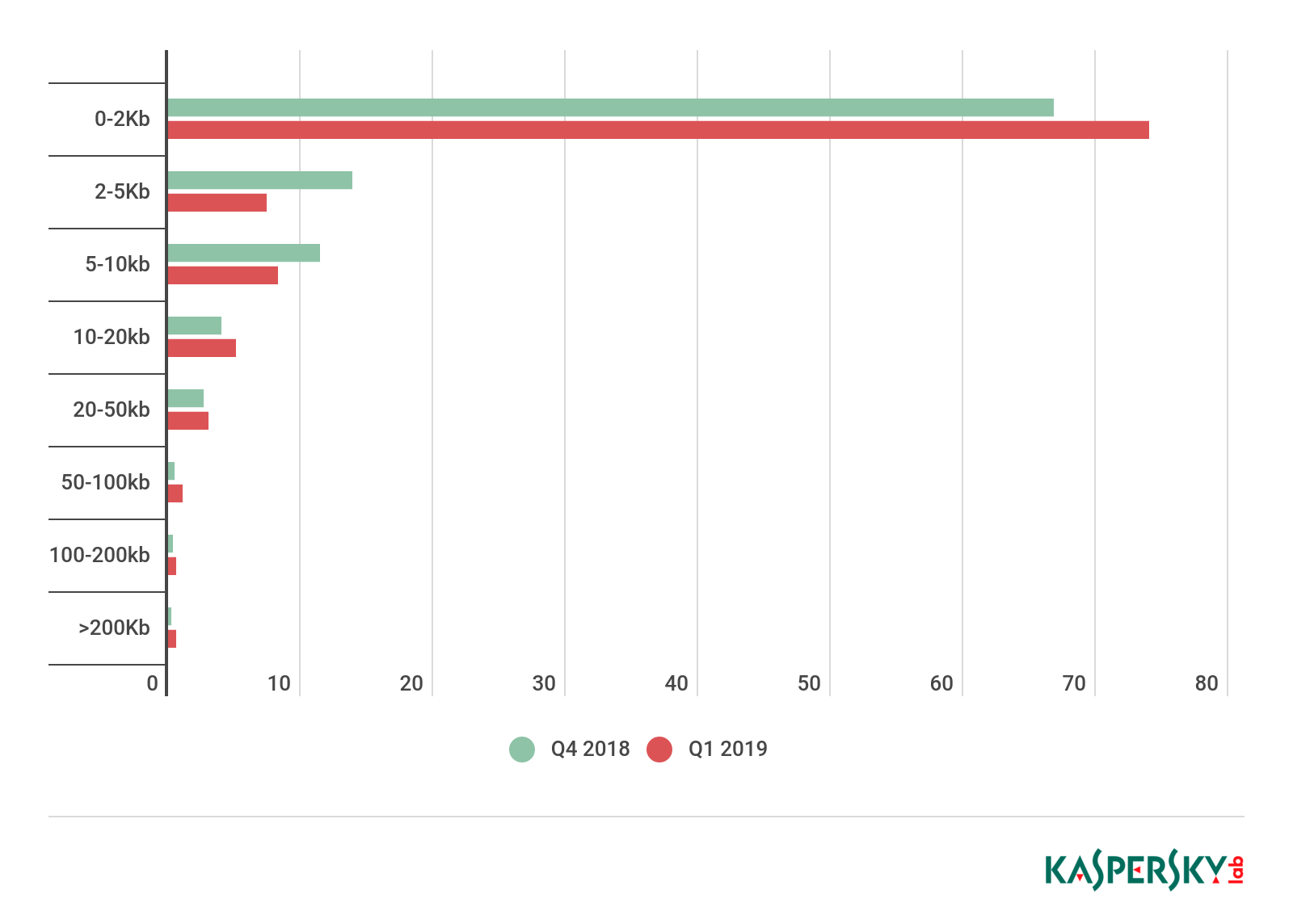
Spam email size, Q4 2018 – Q1 2019
In Q1 2019, the share of very small emails (up to 2 KB) in spam increased against Q4 2018 by 7.14 p.p. to 73.98%. The share of 2–5 KB messages fell to 8.27% (down 3.15 p.p.). 10–20 KB messages made up 5.11% of spam traffic, up 1.08 p.p. on Q4. The share of messages sized 20–50 KB amounted to 3.00% (0.32 p.p. growth against Q4 2018).
Malicious attachments: malware families
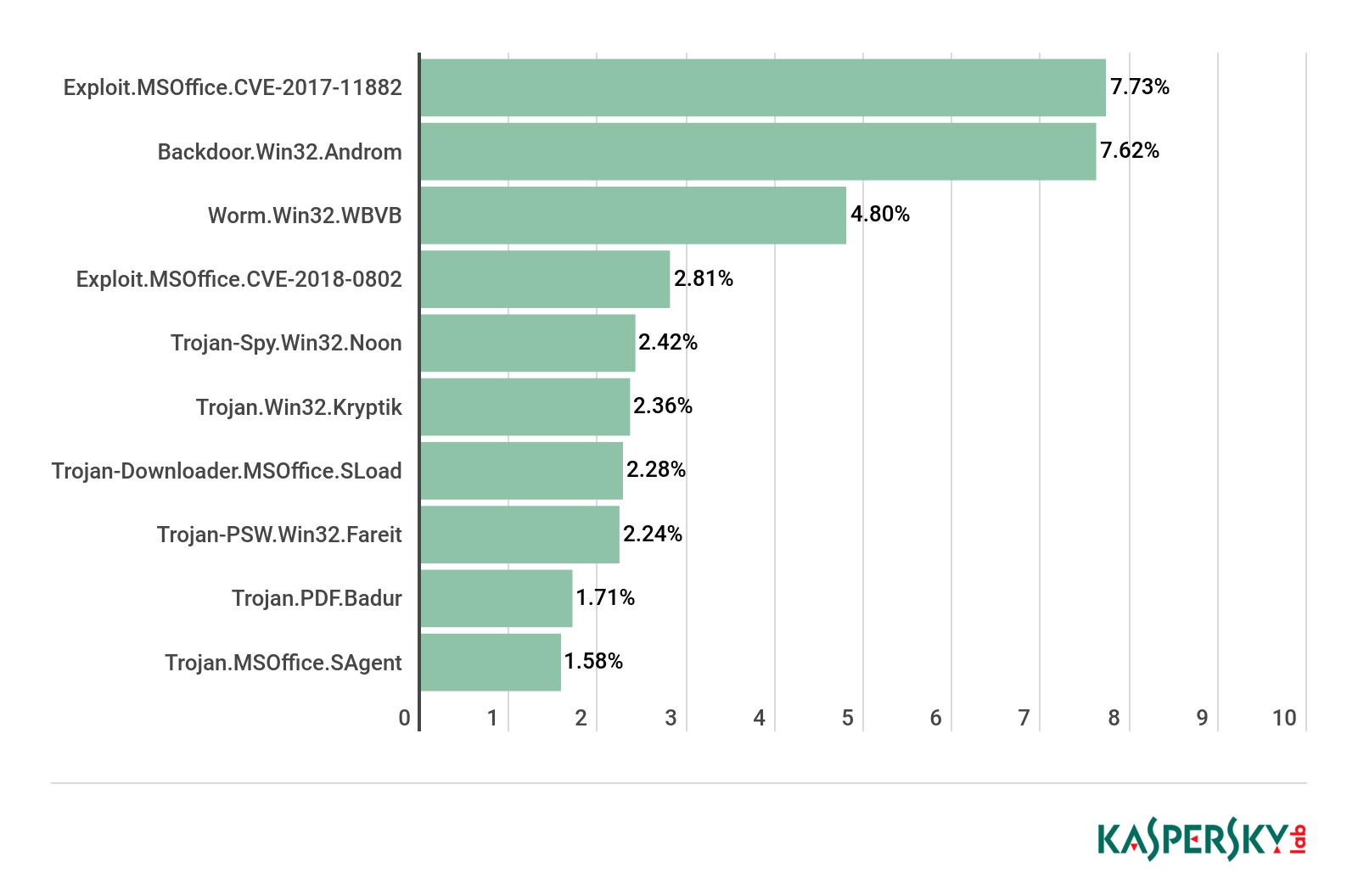
TOP 10 malicious families in mail traffic, Q1 2019
In Q1 2019, the most common malware in mail traffic turned out to be Exploit.MSOffice.CVE-2017-11882, with a share of 7.73%. In second place was Backdoor.Win32.Androm (7.62%), and Worm.Win32.WBVB (4.80%) took third. Fourth position went to another exploit for Microsoft Office in the shape of Exploit.MSOffice.CVE-2018-0802 (2.81%), while Trojan-Spy.Win32.Noon (2.42%) rounded off the Top 5.
Countries targeted by malicious mailshots
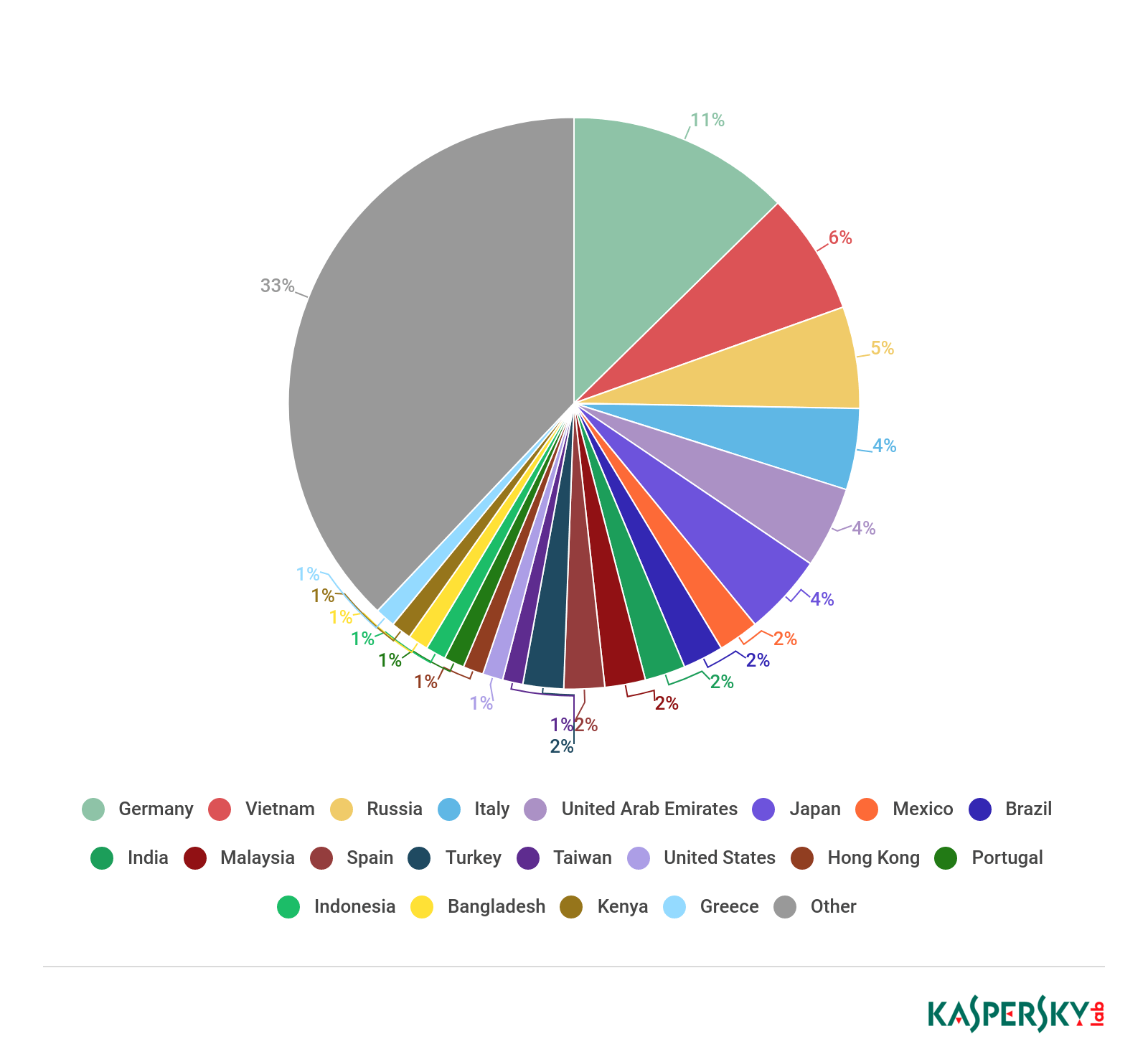
Countries targeted by malicious mailshots, Q1 2019
First place in the Top 3 countries by number of Mail Anti-Virus triggers yet again went to Germany (11.88%). It is followed by Vietnam (6.24%) in second position and Russia (5.70%) in third.
Statistics: phishing
In Q1 2019, the Anti-Phishing system prevented 111,832,308 attempts to direct users to scam websites. 12.11% of all Kaspersky Lab users worldwide experienced an attack.
Attack geography
In Q1 2019, as in the previous quarter, the country with the largest share of users attacked by phishers was Brazil with 21.66%, up 1.53 p.p.
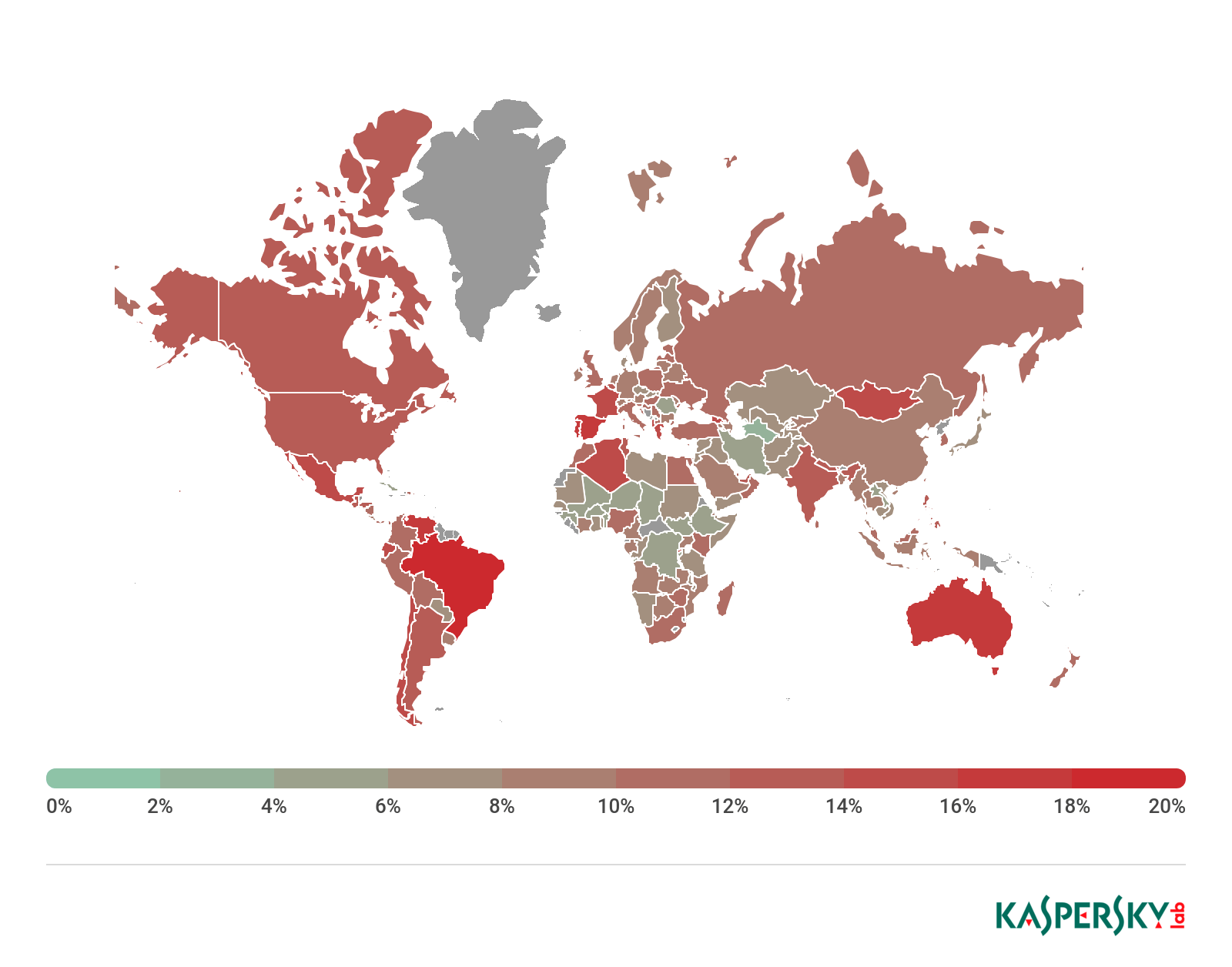
Geography of phishing attacks, Q1 2019
In second place up from eighth was Australia (17.20%), adding 2.42 p.p. but still 4.46 p.p. behind top-place Brazil. Spain rose one position to 16.96% (+0.87 p.p.), just above Portugal (16.86%) and Venezuela (16.72%) propping up the Top 5.
| Country | %* |
| Brazil | 21.66 |
| Australia | 17.20 |
| Spain | 16.96 |
| Portugal | 16.81 |
| Venezuela | 16.72 |
| Greece | 15.86 |
| Albania | 15.11 |
| Ecuador | 14.99 |
| Rwanda | 14.89 |
| Georgia | 14.76 |
*Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky Lab users in the country
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Lab’s Anti-Phishing component. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
This quarter, the banking sector remains in first place by number of attacks — the share of attacks on credit organizations increased by 5.23 p.p. against Q4 last year to 25.78%.
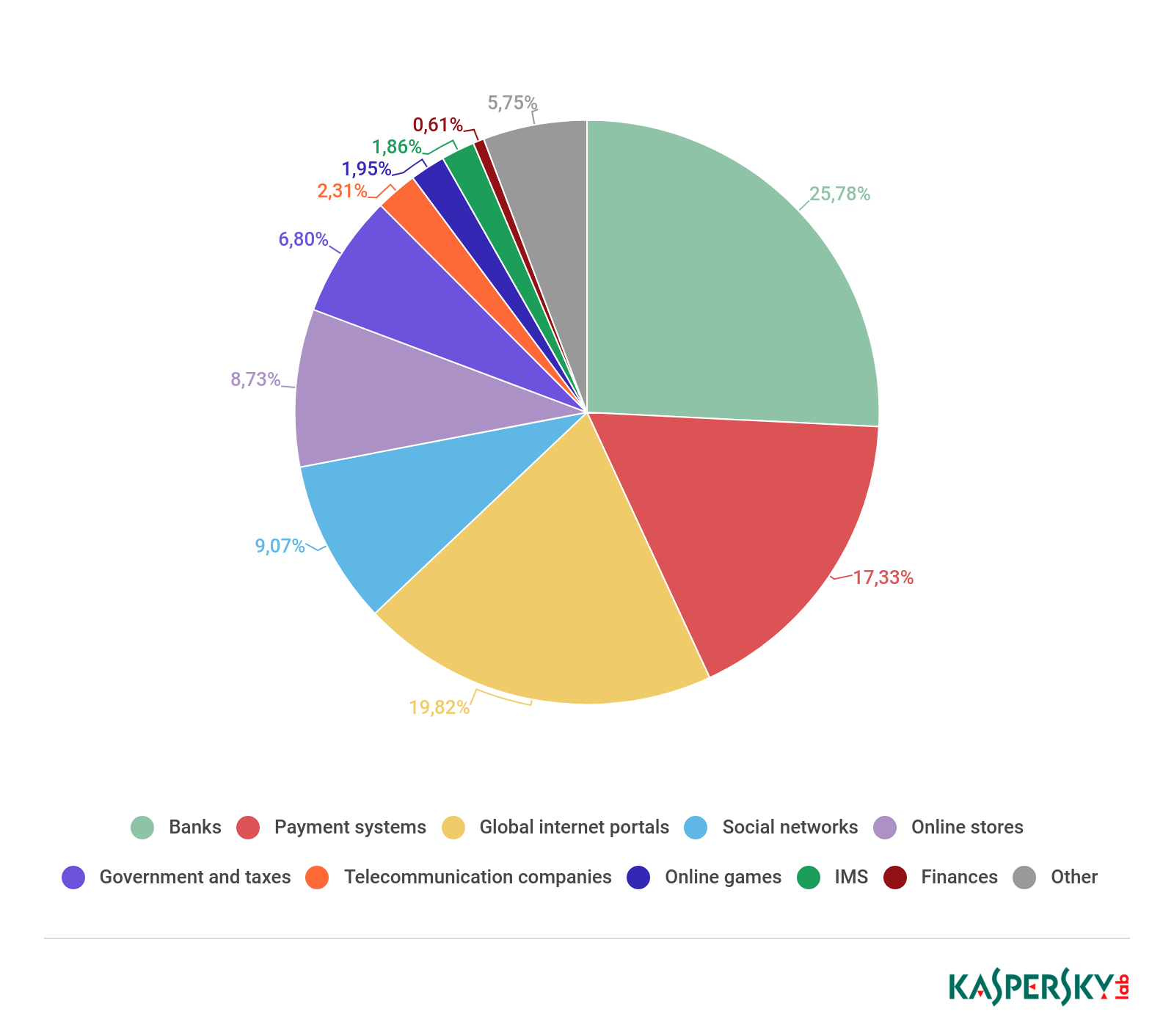
Distribution of organizations subjected to phishing attacks by category, Q1 2019
Second place went to global Internet portals (19.82%), and payment systems — another category that includes financial institutions — finished third (17.33%).
Conclusion
In Q1 2019, the average share of spam in global mail traffic rose by 0.06 p.p. to 55.97%, and the Anti-Phishing system prevented more than 111,832,308 redirects to phishing sites, up 35,220,650 in comparison with the previous reporting period.
As previously, scammers wasted no opportunity to exploit high-profile media events for their own purposes (Apple product launch, New Zealand terror attack). Sextortion has not gone away — on the contrary, to make such schemes more believable, cybercriminals have come up with new cover stories about the message senders.
On top of all that, attackers continue to use social networks to achieve their goals, and have launched advertising campaigns using celebrities to extend their reach.
Spam and phishing in Q1 2019
























Markus Freitag
I actually wonder whether the geographical statistics like “Countries targeted by malicious mailshots” are actually biased by the popularity of the Kaspersky tools in the respective countries. Maybe Germany has a high percentage of Kaspersky users compared to the other countries and therefore more mailshots could be registered. Hence, the shown statistics might be not representative.