
Telehealth today doesn’t just involve chatting with a doctor via a video-conferencing application. It’s become an entire collection of rapidly developing technologies and products that includes specialized applications, wearable devices, implantable sensors, and cloud databases, many of which have only appeared in the past couple of years.
However, telehealth in its current form began to take shape at the end of the 20th century when video consultations first appeared. Developments in the telehealth area were considered promising even before the pandemic. For example, the startup Proteus Digital Health back in 2014 created sensor-enabled pharmaceuticals that received hundreds of millions of dollars in investments. The goal of this project was to help medical professionals track their patients’ medication. After being taken by the patients, the tablets were supposed to send a signal to a wearable patch; from there, the data would be sent to a special application. However, almost as soon as development began, serious questions arose about the security of the service’s data storage and the possibility of it being misused. In 2020, Proteus went bankrupt.
With the onset of the pandemic, there has been a new impetus to develop the telehealth market. With numerous public health restrictions in place, the ability to help patients remotely has become a lifeline for many, with clinics rushing to organize at least some kind of interface for people to chat with doctors in a way that reduces the risk of COVID-19 infection. Research by the company McKinsey shows that the use of telemedicine grew 38 times in comparison with the pre-COVID period. According to data from the CDC Organization, around 30% of all doctors’ consultations in the U.S. from June 26 to November 6, 2020, occurred remotely, and in India telehealth began receiving support from the government starting in March 2020. Kaspersky’s own research found that as of 2021 91% of global medical providers had implemented telehealth capabilities.
Now, more than two years since the start of the pandemic, some of the homebrew telehealth projects have since grown and become more stable and secure. However, many of these recently developed solutions are still composed of various unverified third-party services, meaning they don’t always contain the appropriate security measures to keep patient data safe.
The resulting trend is one where medical services are rapidly being digitalized, affecting highly sensitive data of millions of people, while the solutions being implemented are often barely used technologies or hastily developed methodologies. So it’s reasonable to assume that cybercriminals have noticed this trend—and are looking to exploit it. That’s why we decided to test our assumption and delve into the security landscape of telehealth in 2020 and 2021.
Medical data leaks
It is not always possible to draw a clear line between security incidents that occur as part of in-person care and those that involve telehealth. Let’s say that a database of patient data was leaked from an offline hospital—is this a telehealth security incident? Perhaps not. However, the pandemic has pushed many medical organizations towards remote communication with patients, meaning at least part of the data stored in their databases has been collected as a result of virtual consultations. And that means that many patient data leaks have, in theory, a connection to telemedicine.
According to a report by Constella, in 2020 the number of personal data leaks in the medical sector grew by 1.5 times against 2019. This was based on an analysis of information published on the dark web. The HIPAA Journal, which is focused on leaks in the U.S. reported by medical organizations, has also noted the increase in both the number of leaks and the average number of victims as a result of them. In 2021, HIPAA noted 642 data leaks from medical organizations versus 512 in 2019.
Number of data leaks from medical organizations, 2009–2020. Source: HIPAA Journal
In 2021, the situation did not improve. Starting from December 2020, according to data from the Office for Civil Rights at the Department of Health and Shuman Services (OCR HHS) in the U.S., the number of victims of healthcare data leaks grew by more than 1.5 times when compared to the number of victims of leaks in 2020 in the U.S. alone. According to the HIPAA Journal, the number of actual leaks also increased.
The vulnerability landscape in telehealth applications and wearables
No known vulnerabilities = nothing to be afraid of?
In the summer of 2021, we reviewed 50 popular telehealth applications for the presence of known vulnerabilities. In addition, we checked for known malicious code used to mimic such applications or attempts to access data from them.
Currently, we have not uncovered known vulnerabilities in any of the 50 applications examined. This news is both good and concerning.
The lack of known vulnerabilities, unfortunately, does not mean that such applications are safe. It means that researchers simply have not analyzed their safety or have done so only superficially. At the same time, if before the pandemic such telehealth projects were isolated, then in 2020 interest in such applications grew so quickly that only laggards did not attempt to develop their own telehealth app. However, there is currently no global practice for regulating this sector: different countries license and control such apps in their own way. In some places, there is no regulation at all. In others, only direct medical services are subject to licensing, while apps that assist in providing such services are of no interest to regulators. What’s more, there are large, international applications, such as GTHE, which allow patients to consult doctors in another country, which further complicates the legal regulation of telehealth.
In the absence of centralized quality control of telehealth at the application level, their security can significantly vary from product to product. Another unfortunate fact is that smaller companies, like start-ups, simply do not have enough hands and resources to control the quality and safety of their applications. Accordingly, such applications may contain many vulnerabilities currently unknown to the public that cybercriminals can find and use.
On the other hand, with such a large number of applications, criminals tend to be less interested in each separate application than they would if there were fewer of them or if, say, all the clinics in one specific region used the same service. That said, this only lowers the likelihood of an attack on a specific application; it does not entirely eliminate it.
Vulnerabilities in wearables and sensors
Telemedicine, as mentioned earlier, isn’t just video-chatting with a doctor. It includes a whole range of new patient-care possibilities previously unseen in traditional medicine. Specifically, these are wearable devices and sensors, which can continually or during specific diagnostic intervals monitor indicators of health, such as cardiac activity.
In traditional medicine, until the appearance of “tele”, to monitor cardiac activity Holter monitors were used. The monitor detects cardiac activity with a number of electrodes attached to the chest, and the patient had to wear the whole apparatus for at least a day, which was not always comfortable. Holter monitors still exist, but there also are more comfortable and compact wearable sensors that calculate the same readings without attaching external electrodes to the body and transmit them to a mobile device wirelessly.
Let’s see if there are any informational security issues with these wearables. The most widespread protocol used for transferring data from wearable devices and sensors is MQTT and the most commonly used port is 1883. Authentication for data transfer using this port is completely optional, and even when authentication is present, there is no encryption; in other words, the authentication data is sent as readable text. All of this makes the protocol susceptible to man-in-the middle attacks, since, in most cases, MQTT runs on top of TCP/IP. For the user, this means that if the wearable device is openly connected to the internet, then attackers can easily intercept the data it sends.
Vulnerabilities in the MQTT protocol
The MQTT protocol is very convenient to use for devices that belong to the Internet of Things (IoT), and, therefore, it can be found not just in wearable devices but in almost any smart gadget. As interest in IoT devices grows, so, too, does interest in MQTT—which is concerning from a security standpoint. The graph below shows the changes in the number of vulnerabilities in the MQTT protocol from 2014 to 2021. The red column represents those vulnerabilities that are critical and high-priority. To this day, few of the vulnerabilities from this chart have been patched.

Number of vulnerabilities found in the MQTT protocol, 2014–2021 (download)
Vulnerabilities are located not just in the protocol for the IoT, but also in specific devices and platforms. Among such wearables, one of the platforms with the most vulnerabilities is Qualcomm Snapdragon. Since its launch as part of various wearable devices, more than 400 vulnerabilities have been found, and far from all of them patched. Though, as noted above, the number of vulnerabilities indicates that not only is the product dangerous from a security standpoint, but that the product has passed many tests and checks by analysts and developers who know about the vulnerabilities in this platform.
Number of vulnerabilities discovered in Qualcomm Snapdragon, 2019–January 2022, Source: https://nvd.nist.gov/
Several known vulnerabilities have also been found in other vendors’ wearables used for patient monitoring, such as FitBit.
Vulnerabilities like the one mentioned above enable cybercriminals to hack into users’ devices, and steal their most sensitive data, that is, medical information. It’s also important to keep in mind that certain wearables, like Apple Watch, don’t just track healthcare data, but also location and movements. This opens up the possibility of not just data theft, but also stalking.
Bait and hook—with a medical theme
Since the start of the pandemic, many companies working in the information security sphere, including Kaspersky, have discussed the fact that medicine has become a more common bait in cybercriminal scams. This trend, first noted in 2020, continued in 2021.
With the active development of telehealth, medicine will only become a more commonly used bait, just as the digitalization of banks has turned banking phishing into one of the most popularly used types of phishing.
Since the topic of telemedicine in phishing and malicious attacks is extremely difficult to separate from medical topics in general, the following statistics refer to the use of any type of medical topic as bait. Note also that it is this digitalization of medical services that has made medicine-themed phishing and the distribution of malicious code under the guise of websites and messages from medical organizations possible.
From June to December of 2021, we found more than 150,000 phishing attacks that used the medical theme.
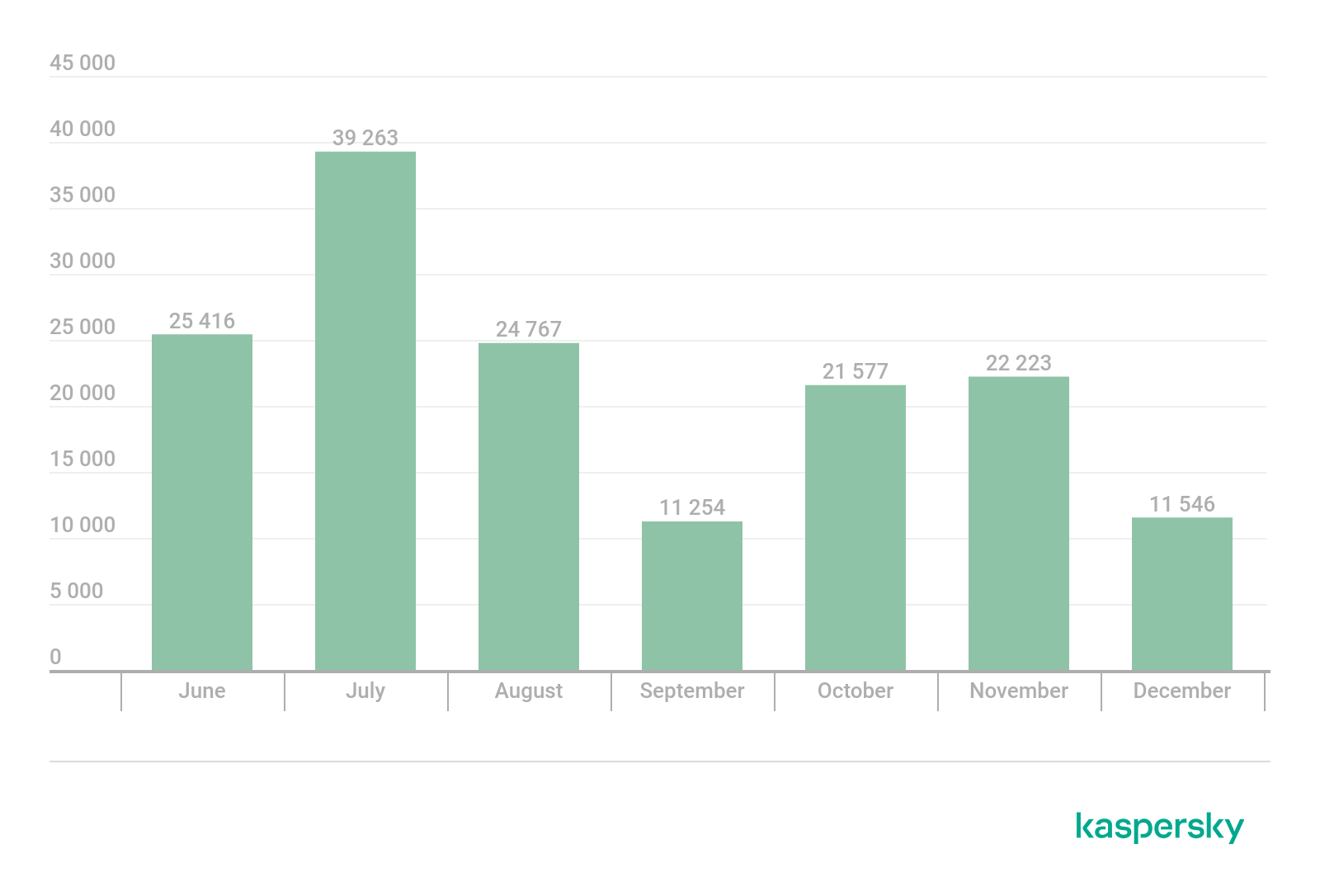
Number of phishing attacks that used medical themes as bait, June–December 2021 (download)
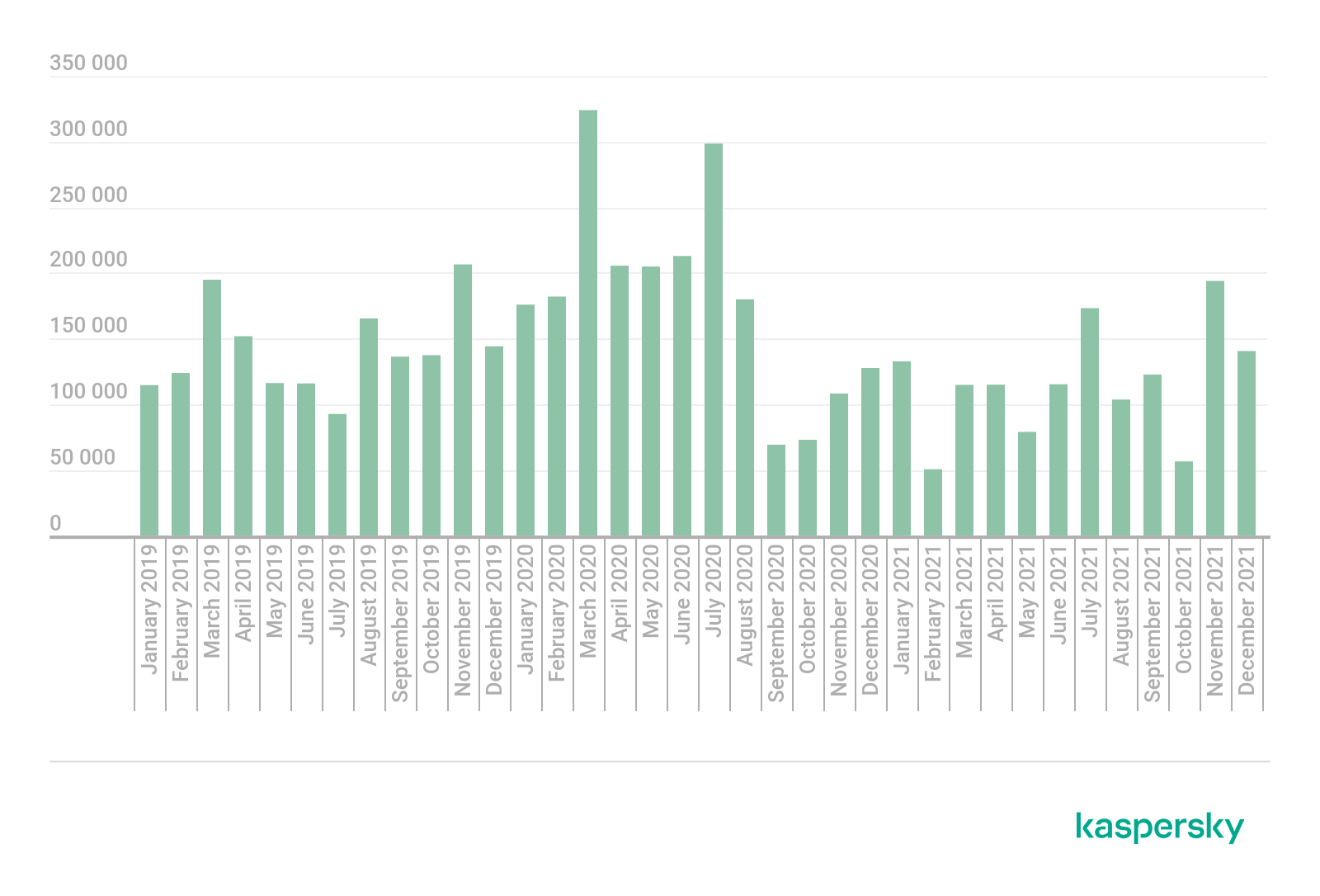
Number of web attacks exploiting medical sites, January 2019–December 2021 (download)
Conclusion
Telehealth will remain an important topic in the healthcare sector for years to come. According to all forecasts, this market will continue to grow regardless of whether the pandemic is defeated, as healthcare providers seek to rethink how patient care is delivered. Therefore, it is critical that those who work in this area are aware of the security dangers.
Phishing and malware attacks that exploit the medical theme will continue, and, with the development of telemedicine, the number of services that fraudsters use as bait will only increase. Moreover, it’s likely that cybercriminals will try to hack telehealth services. To make sure their data stays secure, users of telehealth should do the following:
- Before transferring personal data to any kind of telehealth service, try to find out how this data will be stored and who will have access to it. Try not to use services that do not care about data safety.
- When registering for telehealth services, always use a strong password; however securely the service stores data, a simple password can allow an attacker to gain access to it.
- Never click on links in emails from strangers, even if the topic is interesting. Even if you get an unexpected notification from a telehealth service, always open the application itself rather than click on a link in an email.
Healthcare professionals that use telehealth should protect their work accounts with strong passwords, as well as use two-factor authentication. If frontline workers have a say in the decision about which telehealth application will be used in a clinic, then the security of each proposed application should be carefully studied.
Application developers need to understand that vulnerabilities in an application and a lack of security in general can make it possible for cybercriminals to gain access to personal conversations between doctors and patients, user databases, payment details, and other highly sensitive information.
Overall, we expected that 2021 would be a year of greater collaboration between the medical sector and IT security specialists. In some ways, our expectations were met, but the explosive growth of telehealth has brought new challenges to this collaboration which have yet to be solved.
























Telehealth: a new frontier in medicine—and security