
Kaspersky Anti-Spam protects users all over the world. The Anti-Spam Lab processes more than one million messages caught in our traps every day. Content filtering, technical header analysis, unique graphical signatures and cloud technologies all combine to ensure users are protected, with our analysts creating new signatures 24/7.
Summary
- In Q3 of 2011, the share of spam in mail traffic was down 2.7 percentage points compared to the previous quarter, averaging 79.8%.
- The percentage of fraudulent emails in spam traffic increased twenty times, reaching 2%.
- Asia and Latin America remain the most prominent sources of spam.
- The share of partner program spam went up 5.7 times, accounting for 29% of all spam.
- The percentage of emails with malicious attachments grew by 1.17 percentage points and averaged 5.03%.
- The share of phishing emails averaged 0.03%. Three social networks were among the Top 5 organizations targeted by phishers.
Social engineering: don’t get hooked!
In Q3 2011 the percentage of fraudulent emails increased sharply compared to the previous quarter, accounting for 2% of all spam messages. The quantity of fraudulent messages is striking, but so is the variety of social engineering techniques deployed: the attackers used tried-and-tested tricks as well as new methods tapping into world events and actively exploiting people’s interest in what is going on in the world.
Phishing tricks
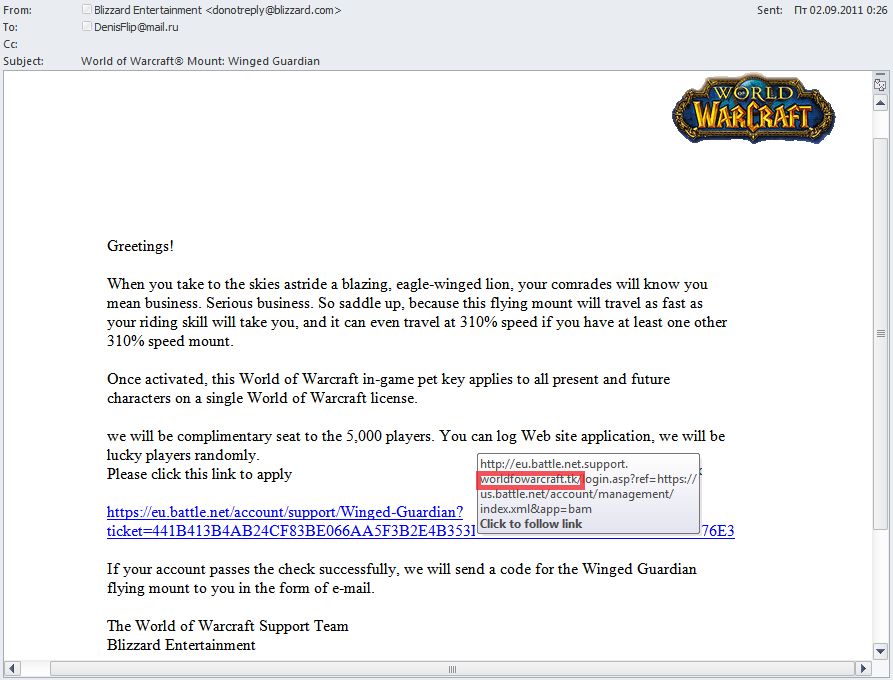
Games with gamers
Blizzard online gamers have long been one of the most popular targets for phishers. The fraudsters send emails offering a host of add-ons and upgrades for games. To make the messages look legitimate the phishers successfully imitate technical details in the email. They do their best to make the name of the fake domain look exactly like that of the original site.
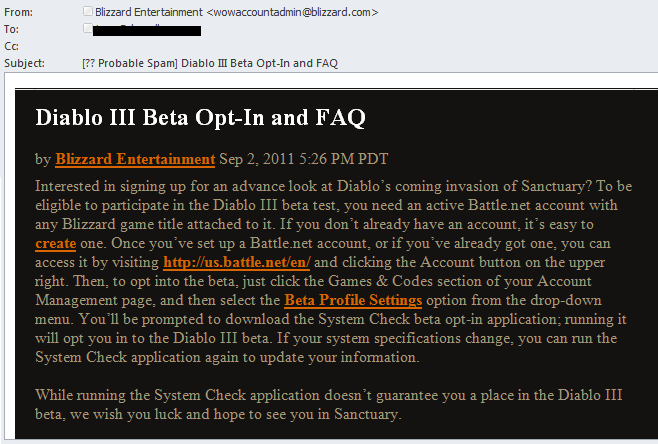
The fraudsters also make detailed preparations for the appearance of new versions of popular games. For instance, around the time Diablo III was released in Q3 2011 we recorded quite a few phishing attacks designed to steal gamers’ usernames and passwords. The users were invited to participate in beta testing conducted by Blizzard.
Blizzard sent very similar official invitations to their users, which is why it was so difficult to tell them apart. The only difference was the link in the emails – the original invitations asked users to visit the site and log in, while the link in the fake messages did not lead to the official site.
Serious emails from serious organizations
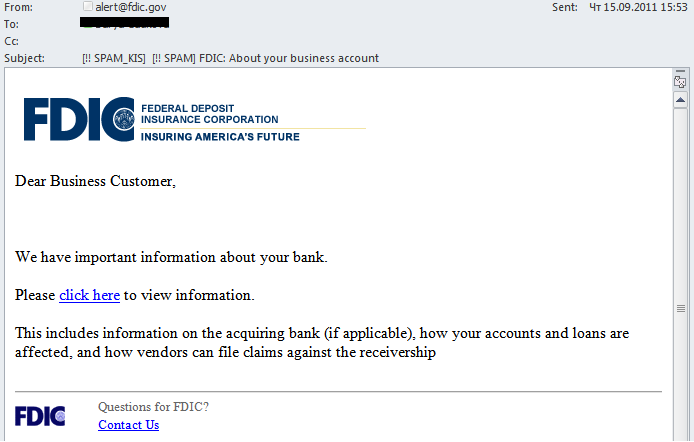
Some users also received an email that appeared to come from the Federal Deposit Insurance Corporation (a US Federal agency created to insure deposits placed with banks).
Users were invited to click the link to view important information about the bank or its credit conditions. The link led to a site where phishers tried to extract confidential data from their potential victims. Hopefully, users won’t be so naïve as to follow the link in an email sent by a ‘serious’ organization which does not contain the name of either the recipient or the bank.
These fake FDIC emails are nothing new for US users. This time, though, they were distributed in other countries, which is rather strange considering FDIC is not a well-known organization outside the US.
Who wants a phishburger?
Q3 2011 also saw less traditional types of phishing attacks. For example, we registered a multi-stage attack. The user received a message, apparently from McDonald’s. It stated that the recipient had won the chance to participate in a survey and would get $80 for doing so. Users followed the link, found themselves on a page with a customer satisfaction survey form and filled it in. After submitting the survey, they were redirected to a further form asking for full credit card details to process the promised $80 payment. Of course, the information was likely to be used to clean out users’ accounts, rather than pay any cash.
There was in fact another stage in the scheme: having followed the link the user was directed first to a compromised official site and was then redirected to the fake survey page with the help of javascript code.
Think before opening attachments
Malware delivered to your doorstep
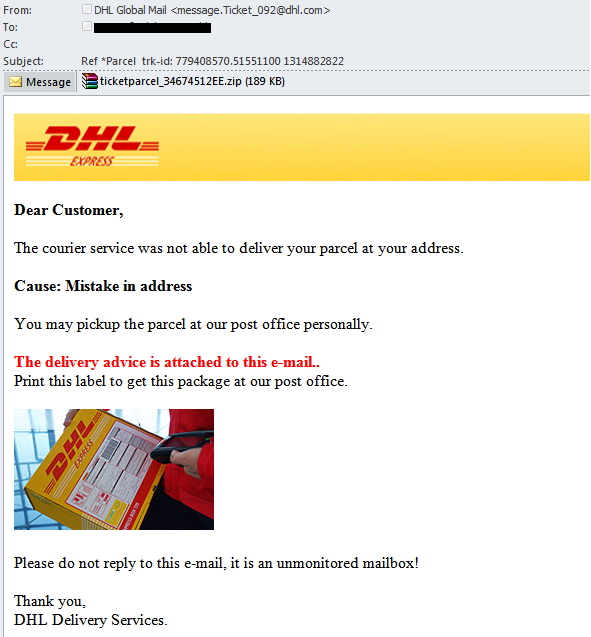
In a previous spam report we wrote about malicious spam imitating notifications from different major delivery services such as UPS and DHL. In the third quarter of 2011 it continued to appear in email boxes.
The attachment contained Trojan-Spy.Win32.Zbot.ccvt, a Trojan-spy program designed to steal users’ data and transmit the harvested information to fraudsters.
The secret code
As is known, social engineering techniques include both the carrot and the stick, and the latter is used quite often. In Q3 2011 fraudsters sent out spam that was just a random array of letters. The symbols were arranged so that the pseudo text looked like an email in incorrect coding or like an encrypted message. The subject of the email attempted to scare recipients into thinking their company had failed to pay taxes. The message contained a ZIP file attachment.
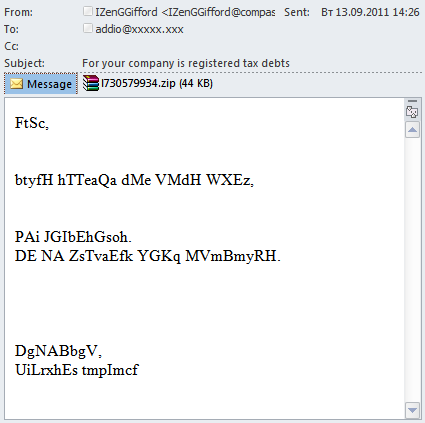
The fraudsters were obviously hoping that worried users who couldn’t read the contents of the email would open the attachment. However, it contained Trojan.Win32.FraudST.atc, a malicious program that specializes in the distribution of pharmaceutical spam from an infected computer.
Another email from a ‘compassionate’ assassin who threatened recipients was described in detail in our spam report for September.
Honest “Nigerians”
In Q3 2011 malicious users were still making use of their time-honored tricks. We haven’t mentioned ‘Nigerian’ frauds for a long time because we thought it had been studied inside out. However, this type of fraud is still in use – suggesting it is as effective as ever and there are users who still fall victim to ‘Nigerian letters’.
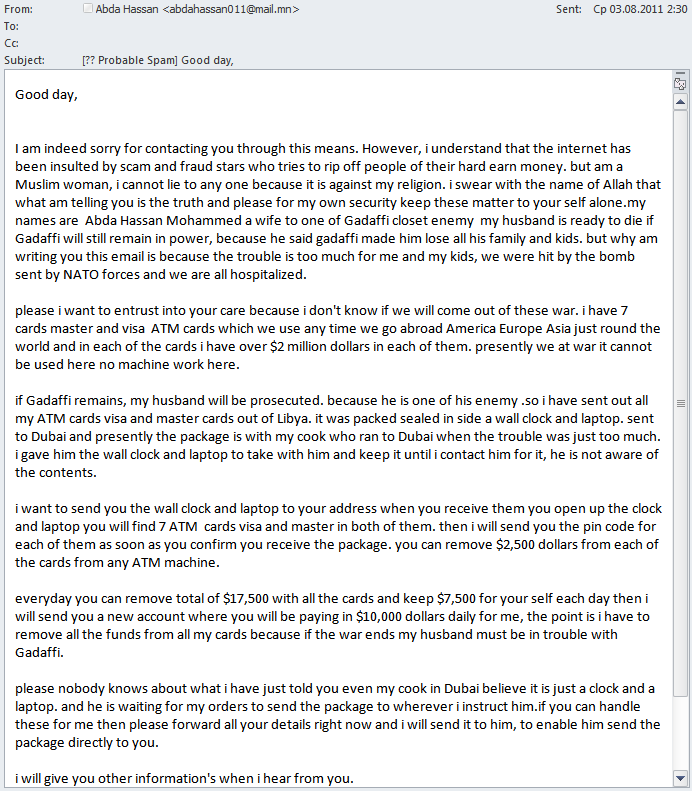
We must admit that over the years the people behind these scams have perfected their social engineering techniques and they are well aware which of them are most effective. In Q3 2011 we came across an email which could touch almost anyone’s heart: “I am indeed sorry for contacting you through this means. However, I understand that the Internet has been insulted by scam and fraud stars who try to rip off people of their hard earn money. But I am a Muslim woman and I cannot lie to anyone because it is against my religion.”
The email goes on to describe the hard life a family has endured as an enemy of the Gaddafi regime and ends with a request to remove considerable sums of cash from seven credit cards.
To recap, these fraudulent schemes employ one of the three following scenarios:
- the fraudsters use various excuses to make a user provide his account number in order to steal his money;
- after agreeing to help, the user is asked to send a certain sum to cover “accompanying expenses” after which the communication will be terminated;
- the fraudsters use their victim as a stooge, shifting responsibility for their scams onto him and potentially leading to criminal action against the unsuspecting recipient.
Spammer methods and tricks: hiding the evidence
Hacking legitimate sites and doctoring them with javascript code is not the only trick spammers use to keep their sites off of denylists.
In Q3 2011 we came across spam emails containing links to legitimate web resources but, at the same time, carrying an SQL injection. Once a user followed the link he entered a site vulnerable to SQL injections, from where he was redirected to the spammer’s online store.
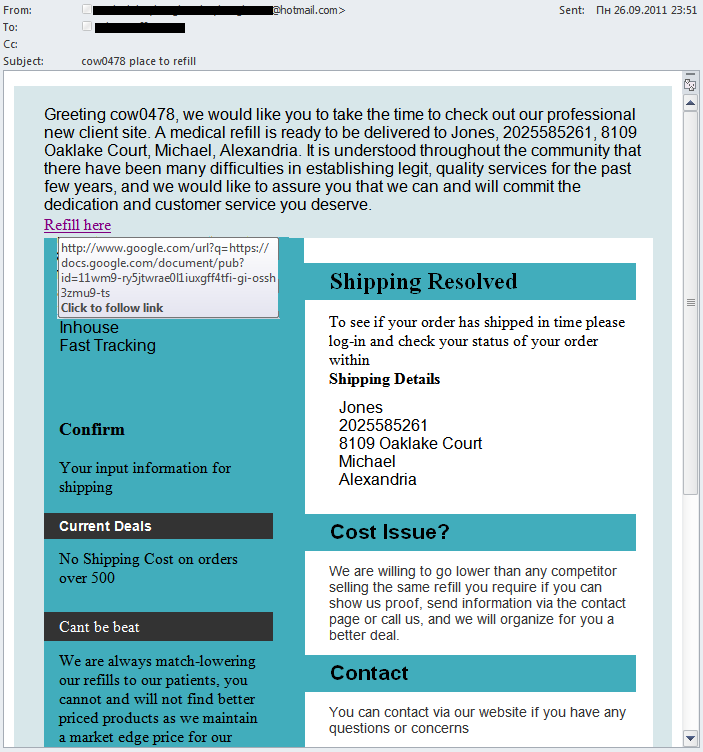
In addition, spammers continue to actively use Google cloud services to bypass filtering. In the email below, the link leads to a document in the cloud which in turn has links through to the site advertised by the spammers.
Statistical summary
Spam in mail traffic
In Q3 of 2011 the share of spam in mail traffic fell 2.7 percentage points compared to Q2 and averaged 79.8%.
Spam levels fell steadily throughout the quarter, except for a spike in the last week of September when the share reached 82.1%. This trend is shown on the graph below:
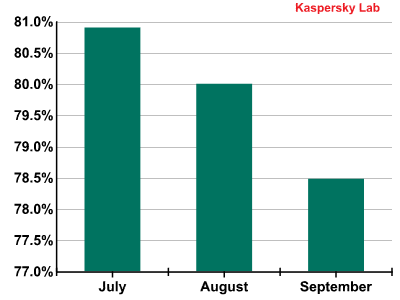
Spam in mail traffic in Q3 2011
It seems likely that the spike in September will herald further increases in spam in October.
Sources of spam by country and by region
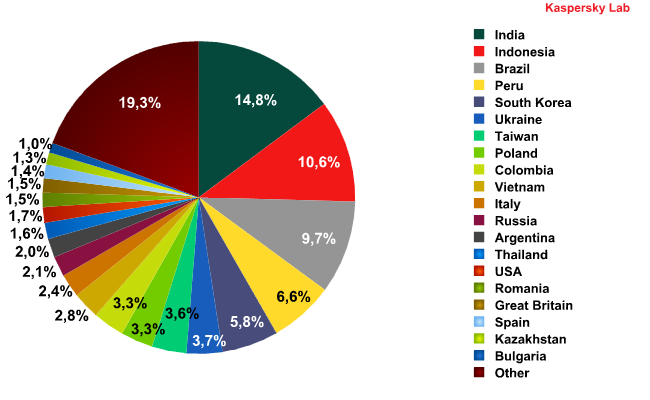
2011’s major trend continued in Q3: more and more spam is coming from developing countries. India (+0.7 percentage points), Indonesia (+4.7 percentage points) and Brazil (+0.8 percentage points) were the top three sources of spam.
Sources of spam by country in Q3 2011
Notably, no western European country is in the top 10. Russia and the US are also outside the leading group. From eastern Europe, only Ukraine and Poland retained their positions from Q2.
In addition, 2011’s other key trend continues: stability. Regional rates remained practically unchanged throughout the quarter.
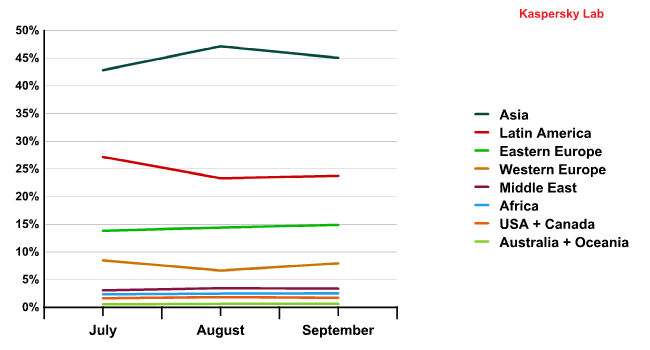
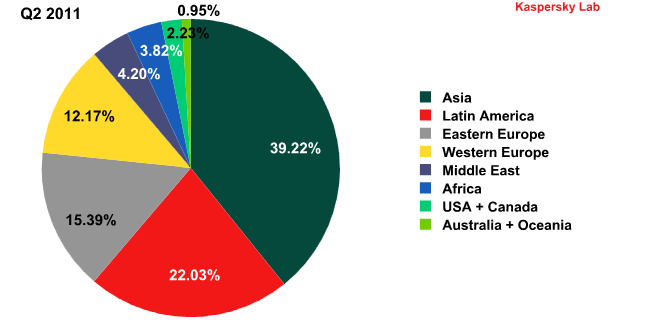
The dynamics of spam distribution by region (Q3 2011)
In Q3 the contribution of all regions outside of Asia and Latin America decreased compared with the previous quarter.
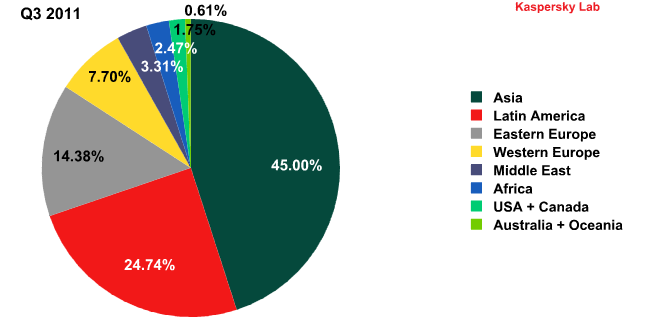
Sources of spam by region in Q2 and Q3 2011
Asia and Latin America’s dominance of spam distribution has become commonplace. But this is a relatively recent trend: one year ago, in Q3 2010, the total amount of spam originating from western Europe and the US accounted for 36%, over a third of all spam, while Latin America spread just 10.7% of unsolicited emails.
Spam by category
Q3 2011 saw considerable shifts in the distribution of spam by category.
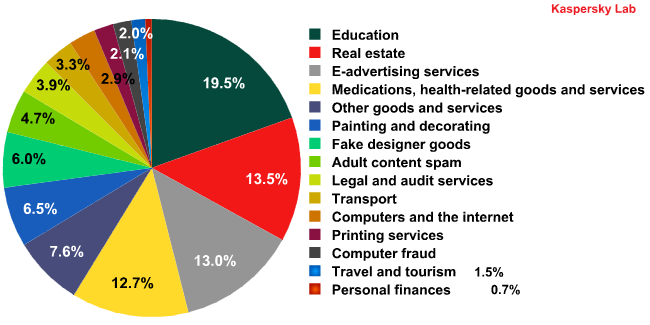
Spam by category on the Russia Internet in Q3 2011
In Q3 education-related spam went down sharply (-39.9 percentage points) compared to the previous quarter. There were also declines in other spam categories, such as Travel and Tourism (-4.3 percentage points) and Other Goods and Services (-1.6 percentage points). In their place, we saw a growth in spam distributed via partner programs: Medications and Health-Related Goods and Services (+10.9 percentage points), Replicas of Designer Goods (+5.2 percentage points), Adult Content Spam (+4.1 percentage points) and Computer Fraud (+1.9 percentage points).
The amount of spam in the Spammer Services category increased considerably (+9 percentage points). This is partially down to some spammer advertising campaigns being particularly aggressive with millions of emails being sent out. In some cases the same messages were sent repeatedly (5-10 times) to the same addresses. The spammers may have used this tactic to break through filters, but in fact it is precisely this kind of multiple mailing which makes them easier to block.
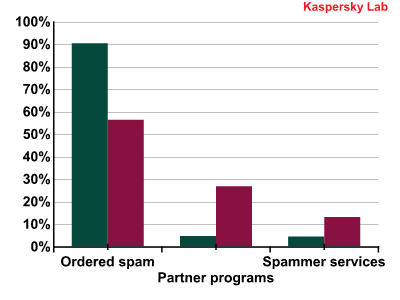
The breakdown of ordered spam, partner spam and spammer services in Q2 and Q3 2011
As can be seen from the graph, the share of spam distributed with the help of partner programs is growing. Partner programs are often used to spread pornography, malicious attachments and adverts for counterfeit goods – meaning more and more spam is either dangerous to your computer or linked to criminal activities. Partner programs are an ideal medium for criminal spam as they offer anonymity to all participants in the process: the owner of the partner program, the spammer and the client do not know each other.
Spam and politics
Political spam deserves a special mention this quarter. In most countries it does not fall under the anti-spam statute as it is not commercial. However, Kaspersky Lab classifies any unsolicited mailing as spam.
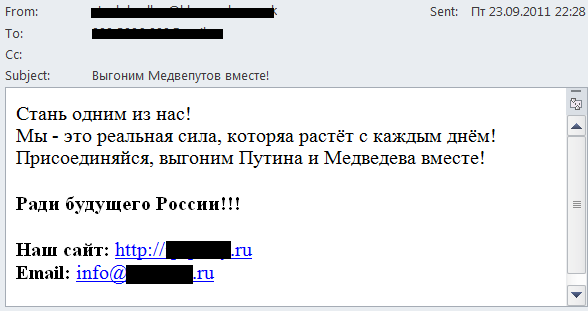
In late 2011 Russia will hold elections to the State Duma (parliament) and in March 2012 the country will vote for a new president. These events are not in the immediate future but political spam is already gaining momentum. Generally, candidates use pre-election spam to win over voters and to denigrate rivals. However, in Q3 2011 we registered several extremist mailings: instead of encouraging people to vote for this or that party, the messages urged recipients “to wreck the anti-national pseudo-elections” and described the present state authority as “a bloody junta”. Below is the most inoffensive of these mailings:
Translation:
Become one of us! We are growing in strength with every day! Let’s join together and get rid of Putin and Medvedev!
For the future of Russia!!!
Malware in mail traffic
Emails with malicious attachments
In Q3 of 2011 the average proportion of emails with malicious attachments increased by 1.17 percentage points, reaching 5.03%. The graph below shows the distribution of malicious spam by month in Q3 2011.
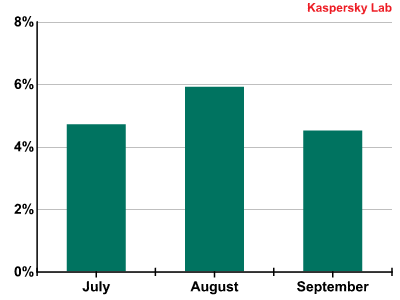
The percentage of spam with malicious attachments in Q3 2011
As can be seen from the graph, a peak was registered in August (nearly 6%). But even in July and September the percentage of malicious spam remained high, exceeding the average figures for the previous quarter.
It’s worth pointing out that the unstable economic situation will only encourage partner programs distributing malicious code, which in turn will push up the number of mailings containing malicious attachments.
Email antivirus detection levels for different countries
Email antivirus detection rates for different countries in the third quarter of 2011 were as follows:
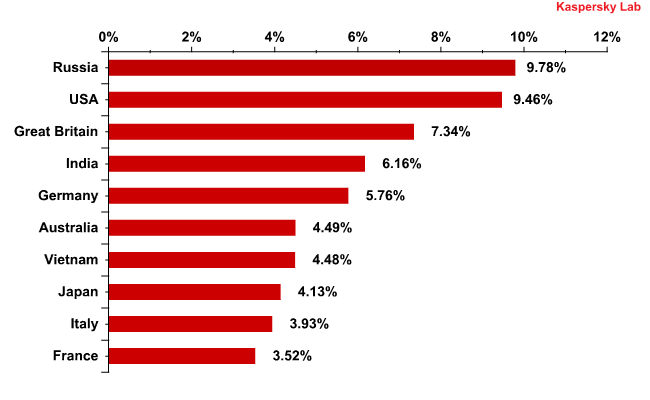
Email antivirus detection levels in Q3 2011
As in the previous two quarters, most malicious attachments in Q3 were found in Russian mail traffic (9.8%), although this figure was down 2.7 percentage points on Q2. There was a similar fall in the US’s share, with the country remaining in second place. Vietnam fell four places from third to seventh, with the UK climbing to third. Britain had 7.3% of all detected malicious attachments, up 1.1 percentage points. India remained fourth, with an increase of 1.5 percentage points and accounted for the same share as it did in Q1.
The last six months featured two interesting trends:
- Email antivirus detections in the US and India operate in inverse cycles: the more malicious emails that are detected in the US, the fewer that are recorded in India, and vice-versa.
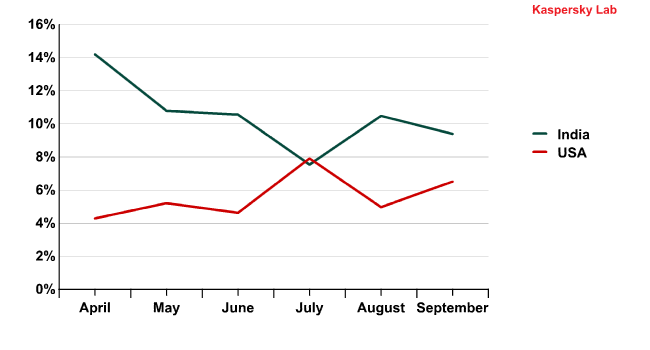
Email antivirus detection activity in the US and India in Q2 and Q3 2011
It is not yet clear why this is the case but we will continue to monitor the situation.
- In the US and Australia detection rates are more or less synchronous, which may be caused by the similar Internet landscape of these countries.

Email antivirus detection activity in the US and Australia in Q2 and Q3 2011
The Top 10 malicious programs distributed via mail traffic
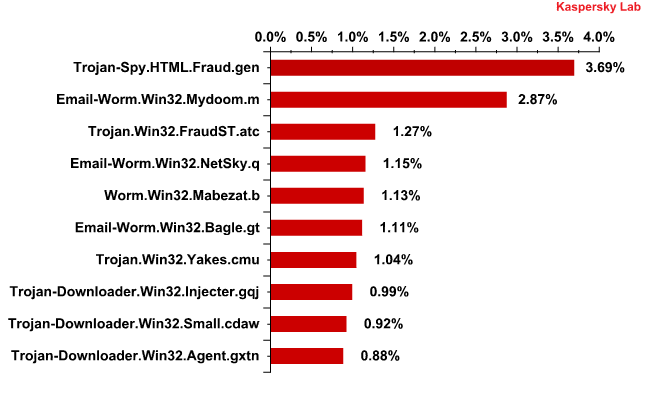
The Top 10 malicious programs distributed via mail traffic in Q3 2011
Trojan-Spy.HTML.Fraud.gen remained the mostly widely-distributed malicious program in Q3. This Trojan uses spoofing technology and imitates an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password. More details about this program can be found here.
But its place at the top is threatened by Trojan.Win32.FraudST.at, a spam bot which specializes in spreading pharmaceutical mass mailings and which topped the charts in September.
Mail worms are no longer so widespread: in Q3, only three representatives of this family entered the Top 10 – Email-Worm.Win32.Mydoom.m (2nd place), Email-Worm.Win32.Netsky.q (4th place) and Email-Worm.Win32.Bagle.gt (6th place). To recap, the main purpose of the first two worms is to harvest email addresses and spread themselves via mail traffic. The functionality of Bagle.gt is more sophisticated: it not only collects email addresses and distributes itself via mail traffic, but also installs other malicious programs once it has penetrated a victim’s computer.
Phishing
In the third quarter of 2011 the volume of phishing emails increased very slightly and accounted for just 0.03% of all mail traffic.
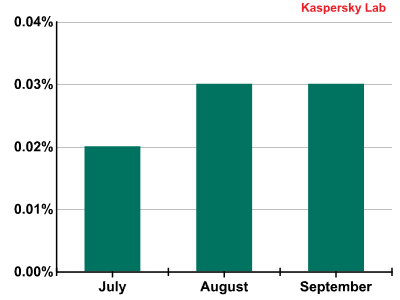
The percentage of phishing emails in mail traffic during Q3 2011
PayPal (-15.28 percentage points) and eBay (+4.23 percentage points) remained the most popular targets for phishers. Despite such a significant decrease, PayPal still accounted for over a third of all attacks throughout the quarter.
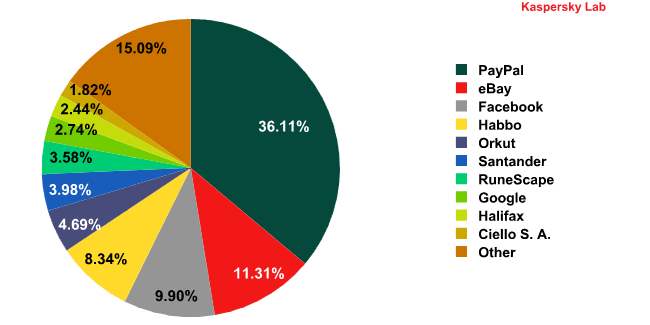
The Top 10 organizations targeted by phishers in Q3 2011*
* The rating is based on the number of phishing URLs on the Internet that attempt to obtain user logins and passwords for various online services. The rating is not demonstrative of the security level of the organizations named above, but rather the popularity of the services among users, which in turn explains their popularity among phishers.
The two leaders are followed by three social networks: Facebook (+4.94 percentage points), Habbo (+3.3 percentage points) and Orkut (+3.05 percentage points). Google’s social network, Google+, was also targeted, pushing Google as a whole into 8th position (+1.34 percentage points).
Free-to-play online game Runescape overhauled subscription-based World of Warcraft in the phishing rating. Runescape went up to 7th place (0.96% of all phishing attacks), while WoW dropped out of the top 10.
Traditional banking services were also less attractive to phishers: Santander (-1.33 percentage points) and Halifax (+0.82 percentage points) only came 6th and 9th respectively. Latin America’s leading e-pay system, Ciello S.A., was a newcomer this quarter, entering at 10th place.
In previous spam reports we have mentioned how phishers have lost interest in traditional banks, but we saw just two banks feature in the Top 10 for the first time ever in Q3 2011. This is because the theft of real money is more risky than stealing virtual money for phishers. Moreover, both forms are practically of equal value.
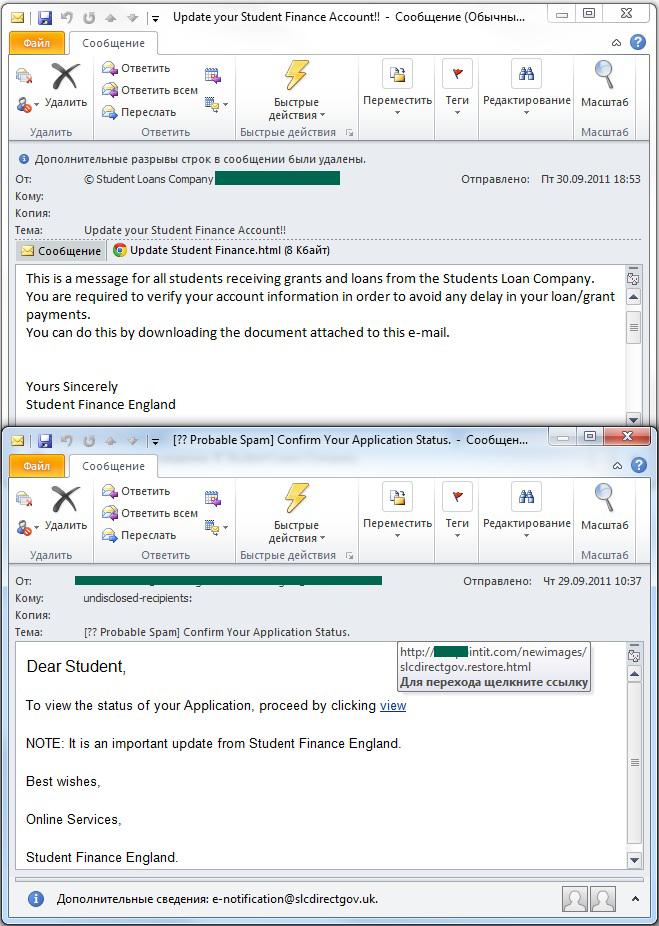
Additionally, the end of September saw the appearance of spam targeting students who received grants and loans at the start of the academic year.
The students were redirected to phishing sites where they were asked to fill in a form allegedly provided by a student loan company in order to verify their account information. Of course, this form had nothing to do with official lenders and anyone filling in the forms fell victim to scammers.
Conclusion
In Q3 2011 the joint efforts of Kaspersky Lab and Microsoft resulted in the closure of yet another botnet – Hlux/Kelihos. The last two years of the anti-botnet campaign has shown that closing botnets is the most effective way of combating spammers.
However, despite the decrease in the amount of spam in mail traffic its content has become more dangerous. The average percentage of spam with malicious attachments reached a record-breaking high of 5.3% throughout Q3. The spike, and a similar rise in adult content spam, could be a result of the summer holiday season and the “second wave” of the global economic crisis. During the summer slowdown, and prompted by the uncertain financial climate, spammers look for scams that can keep them in business. Distributing malicious code, as well as links to porn sites which can spread computer infection, remain profitable for the participants of partner programs: users continue to watch x-rated videos or to download suspicious archives regardless of the state of economy.
We expect further growth in the amount of the partner spam in the next quarter if the situation surrounding the world economy remains uncertain. This not only refers to spam containing malicious attachments and adult content but also to other partner program spam such as pharmaceutical goods, counterfeit goods and cut-price software.
There will also be more ‘Nigerian letters’ in mail traffic: if the economy shows no sign of recovery, more people will be ready to take even some of the more outlandish money-making opportunities at face value – and the ‘Nigerian’ spammers will take full advantage.
We expect a reduction in orders to distribute spam, matched with a parallel increase in emails advertising spammer services. However, the economic crisis of 2008-2009 showed that a decrease in the amount of ordered spam on the Russian Internet can result in a slight reduction in the total amount of spam traffic.























Spam in Q3 2011