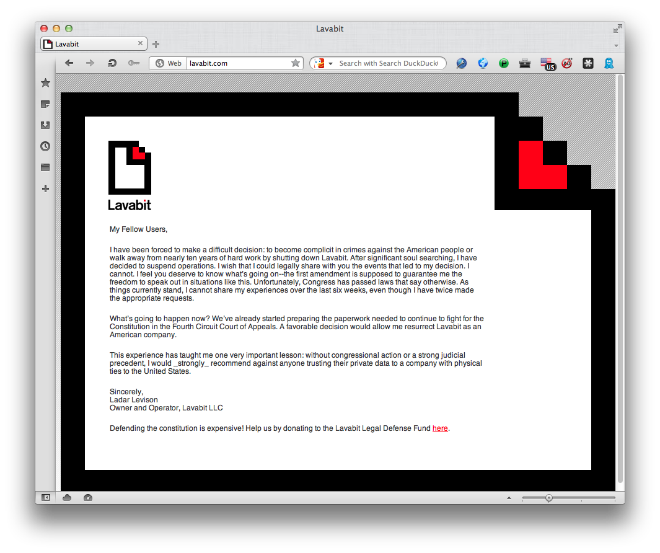
Yesterday, Lavabit – a secure e-mail provider – announced that it’s closing down their operations. The official text and the Website looks like this:
Lavabit was one of the very few secure e-mail service providers bringing security for its paid customers by encrypting all locally stored e-mail messages with an asymmetric key and AES-256. This means that in order to decrypt the messages, an attacker would need to compromise the server first and then to know your password. There was no way even for Lavabit to decrypt emails without a user’s password. A detailed description of how the Lavabit technology worked is available here: pastebin.com/rQ1Gvfy0
Few hours later, Silent Circle, another secure e-mail provider, announced shutting down its Silent Mail service too.
In general in order to make an e-mail server secure there are several criteria to match:
- Secure encrypted connections between the user and the e-mail server (it must be encrypted with a strong algorithm and to have a validation process to avoid the risk of a man-in-the-middle attack)
- Strong user passwords to withstand brute force or dictionary attacks
- Secure encrypted e-mail storage (this was the primary feature that Lavabit implemented. Encrypting all locally stored emails on the server.)
- Secure encrypted e-mail sent over the Internet (it’s important to cipher messages with technologies like PGP, so once an e-mail leaves the original server, it travels over the Internet to the final destination in encrypted form. Even if intercepted, it cannot be read or at least not easily so)
- Secure end-points with no password storage in the browser and with the best defense technolgoies possible to protect against end-point malware attacks. (This last point is very important because you may match all previous criteria but if your end-point is compromised, there is no value of any encryption. All your passwords and other sensitive information will be open to the attackers hands)
Nowadays most email servers supports the first of the criteria listed above. The end user, i.e. us, may also accomplish criteria 2, 4 and 5. For criteria 3, in most cases, it is something which e-mail providers either do not offer or they implement it poorly. For example, sometimes the encryption and decryption keys are one and the same and managed by the e-mail provider.
With the closing of Lavabit, a secure e-mail platform, perhaps the best that was available, is no longer available to the masses.
The questions to all of you are, if an e-mail service meets all 5 requirements will it sooner or later shut down or start collaborating with governments? And which equivalent or alternative service do you recommend or use?
Securing Your Email Space






















michael blake
how long does this action against independent services to be finished? How does one follow the discussion to a cleaner service? Is their anymore independent services providers in the email business? Trust is now only a word to the wise or my elders once began a letter to me, “I put pencil to paper to say Hello”. So swings the clock’s pendulum to a time of yesterday. I can only wonder what’s in the marrow. thanks for sharing.