
Last week, Apple released two urgent updates to Mac OS X to:
1. Remove the Flashback malware about which we have already written
2. Automatically deactivate the Java browser plugin and Java Web Start, effectively disabling java applets in browsers
Particularly, the second step shows the severity of the CVE-2012-0507 vulnerability exploited by Flashback to infect almost 700,000 users via drive-by malware downloads.
Actually, it was the right decision because we can confirm yet another Mac malware in the wild – Backdoor.OSX.SabPub.a being spread through Java exploits.
This new threat is a custom OS X backdoor, which appears to have been designed for use in targeted attacks. After it is activated on an infected system, it connects to a remote website in typical C&C fashion to fetch instructions. The backdoor contains functionality to make screenshots of the user’s current session and execute commands on the infected machine.
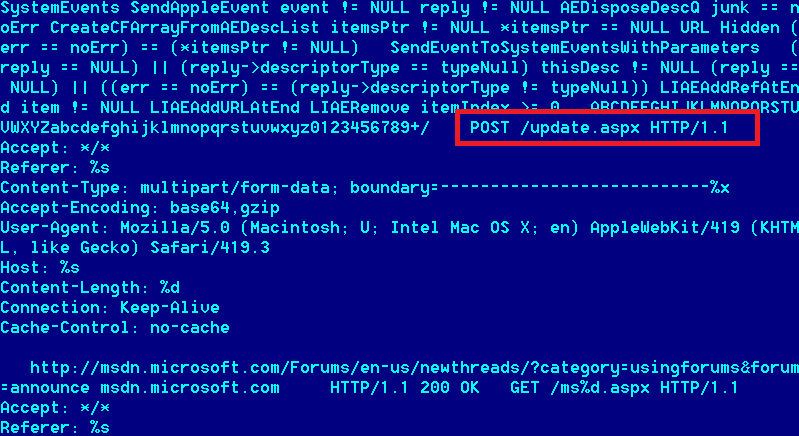
Backdoor connects to remote server to fetch work
The remote C&C website – rt***.onedumb.com is hosted on a VPS located in the U.S, Fremont, CA.
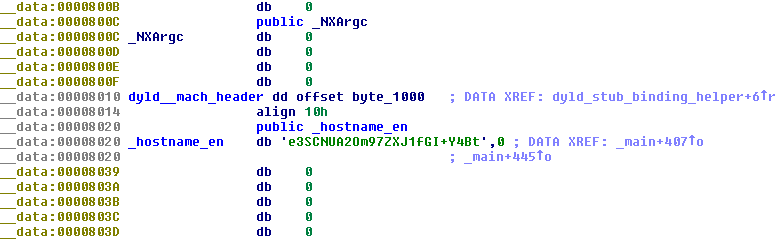
Encoded C&C address (“hostname_en”) in the backdoor
“Onedumb.com” is a free dynamic DNS service. Interesting, the C&C at IP 199.192.152.* was used in other targeted attacks (known as “Luckycat”) in the past.
If we are to believe the timestamps from the Java dropper, it was created on March 16, 2012 – so almost one month ago! The dropper Java class appears to have been sent to the ThreatExpert website on April 12th.
We detect the Java exploit used in the dropper as Exploit.Java.CVE-2012-0507.bf.
One of the components of the dropper, was also sent to the multi-scanner website “VirusTotal” on April 2nd. Ever since, it was sent another time – in both cases, from China.
The Java exploits appear to be pretty standard, however, they have been obfuscated using ZelixKlassMaster, a flexible and quite powerful Java obfuscator. This was obviously done in order to avoid detection from anti-malware products.
At the moment, it is not clear how users get infected with this, but the low number and it’s backdoor functionality indicates that it is most likely used in targeted attacks. Several reports exist which suggest the attack was launched through e-mails containing an URL pointing to two websites hosting the exploit, located in US and Germany.
The timing of the discovery of this backdoor is interesting because in March, several reports pointed to Pro-Tibetan targeted attacks against Mac OS X users. The malware does not appear to be similar to the one used in these attacks, though it is possible that it was part of the same or other similar campaigns.
One other important detail is that the backdoor has been compiled with debug information – which makes its analysis quite easy. This can be an indicator that it is still under development and it is not the final version.
We are continuing our research into this malware and will post updates as necessary.
In the meantime, you may want to check this article for 10 simple steps to boost the security of your Mac.























SabPub Mac OS X Backdoor: Java Exploits, Targeted Attacks and Possible APT link