
Recent advances in browsers as seen in Netscape 8 or IE7 have made it harder for the bad guys to succeed with their phishing schemes. In the malware world, technological advances stimulate the development of new ways to evade detection. And we’ve came by some interesting e-mails which seem to indicate the same is happening in the phishing area as well.
Our colleague Michael Molsner in Japan got an odd phishing e-mail on his address. The text is the usual “help keep your identity safe” and it pretends to come from PayPal. What’s interesting is the URL to the spoofed site, which points to a page on www.aafe.cn – the “Academy of Armoured Force Engenering”.

While the website appears to be legit, the page from the PayPal e-mail is not. It redirects the browser to a page on http://www.skycar.net.cn/ which loads an interesting Javascript.
This script runs maximized in the browser and presents the user with a window which looks like this:
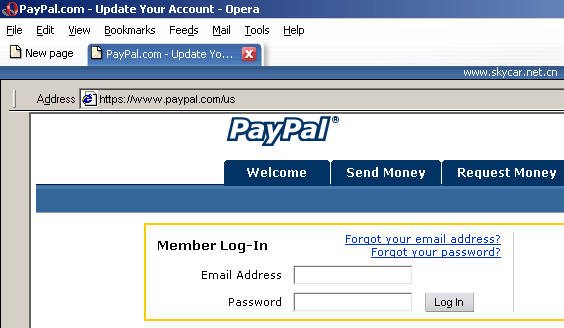
As you can see, there is an Address field in the window which says “https://www.paypal.com/us”, but it is not the real browser address editbox! It’s a special field inside the Java applet which makes it look like it’s part of the browser window. Do note the real website address, as displayed by Opera – www.skycar.net.cn, in the blue bar. However, users who aren’t too careful about entering their PayPal data on websites might well be fooled.
Interestingly, Firefox doesn’t fall for this “trick” – it shows the fake “address bar” for a short time, then it hides it.






















Phishing extreme