
I guess the news about the death of Osama Bin Laden is starting to reach everyone around the world. We have noticed that every time something big as this happens, people get curious and start searching on the Internet. This is something that my colleague Fabio also noticed. During his research he found that cybercriminals are spreading Rogueware via Blackhat SEO and Google Images. You can read more about his finding here.
This triggered me to do a quick search on Facebook and see what was happening over there. I directly saw that Facebook ads are already spreading using videos of the death of Osama Bin Laden as a trigger. On one Page we can see multiple users posting the same URL, with the following message:“Sweet! FREE Subway To Celebrate Osamas Death – 56 Left HURRY!” or “2 Southwest Plane Tickets for Free – 56 Left Hurry” and then a link to a short URL service (http://tiny.cc/).

When you click the link, you will be redirected to a page, where it says that you need to post a message to get more instruction on how you can win.

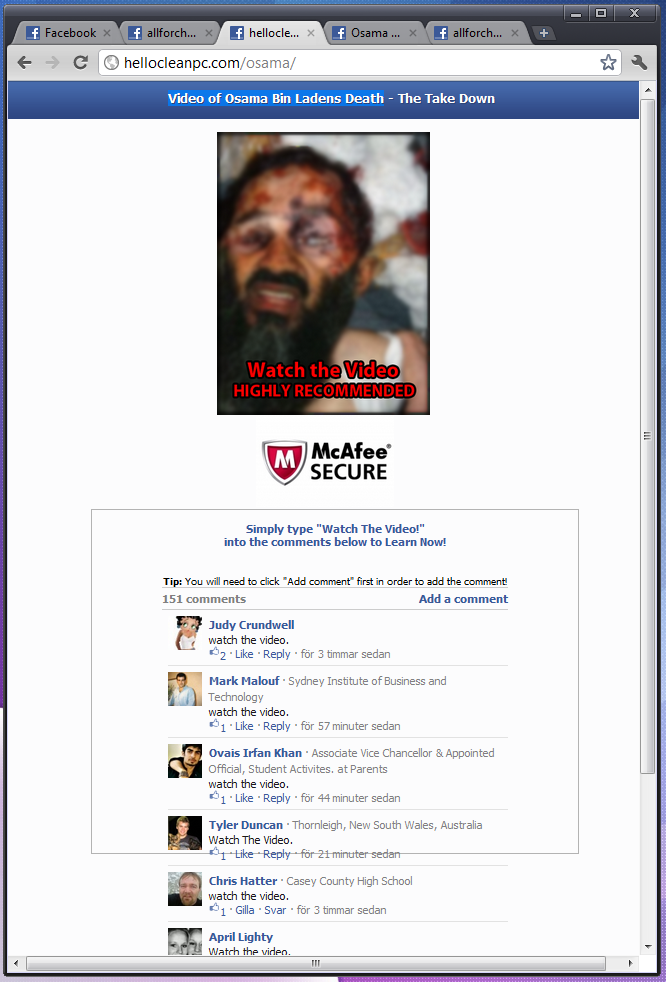
If the user writes the message, it will post a new message on the user’s wall, to spread the message further, and then just redirect you to another page where you can win something else. The scheme of this scam is to keep redirecting you to pages where you have to enter information such as email, and eventually get money for all new users or clicks.

Please make sure that your computer is up to date with all the security patches, that your antivirus is updated and if you do click on the links from Facebook and other social media pages, make sure that you don’t give out any important information (username, passwords).
Since the bad guys seem to be taking advantage of this opportunity quite heavily, we expect to see more malicious code getting triggered by the death of Osama Bin Laden.





















Osama Bin Laden Spam/Ads on Facebook