
A lot of tools and services change hands – for money – in the criminal underground. For example bot-packs are offered by the creator or his business partners for a defined amount of money. The customer gets a package with all needed files and additional support, like updates against anti-virus detection. Mostly there are different levels of support the customer can subscribe to.
But all is not perfect even in the criminal world.
In February this year an individual who names himself “Till7” started offering his new web panel Bot called “v0id Bot”. The official distributor – named “3lite” -started to offer this bot-pack in underground forums.
The bot itself is written in VisualBasic.Net and comes with a php-based Web-Panel offering several features:
- Visiting a specified website
- Downloading and executing a file from a specified website
- Email spamming/ bombing functions,
- Credential Stealer (for DynDNS, Filezilla and others)
- HTTP and UDP flooding
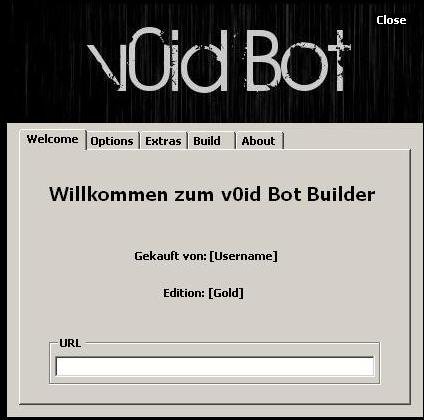
C&C URL
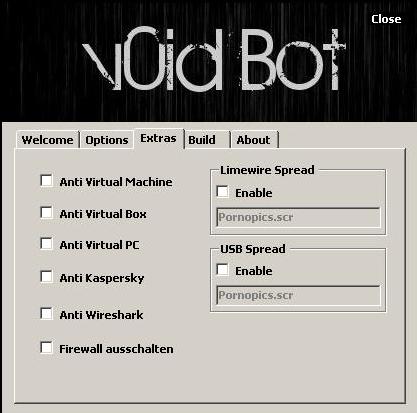
List of “popular’ features
I tracked messages from people who bought this pack. But by mid-March some posts came up in forums, where customers complained that they didn’t get any support from the creator nor from the partner.
One customer got so angry that he just posted the whole pack he had bought for public access. This leak was the end of the commercial pack and soon some other people released modified packs of this bot with different changes and bug-fixes.
The customer who leaked the pack first argued that “the bot is crap”, “the creator doesn’t care about his customers” and the “support wasn’t available at the end”. A second leak in another forum was also due to the fact, that several anti-virus scanners detected the bot and so the creator didn’t fulfill his promised “FUD” (fully undetected) guarantee for the bot.
In March a short tutorial was posted, with three steps to “own” the v0id-bot – aka a ‘how-to’ on changing some of the bot binary so it can be controlled by someone else than the original owner.
The bad thing about all this is, that the bot didn’t just disappear, but now can be used by anyone. Ambitious newcomers in the cybercriminal business just need to download the leaked package. Some days ago the full source code of the bot was released, so the bad guys now can fully create their own bot based on void-bot.
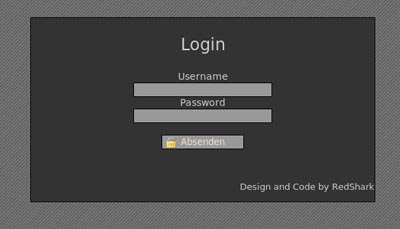
Log-in from one installation of the original C&C
The most interesting features of the case, to my mind are the speed of the cycle and the language.
The entire process – from the moment when the original pack was posted for sale to the final leak of the source code took only 1 month. And the process was all in German – clearly proving that the German cybercrime underground is alive and well – too well, IMHO.



















No honor among thieves – even in Germany