
Malicious programs detected on users’ computers
The first Top Twenty list below shows malware, adware and potentially unwanted programs that were detected and neutralized by the on-access scanner when they were accessed for the first time.
| Position | Change in position | Name | Number of infected computers |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 304259 |
| 2 |  0 0 |
Virus.Win32.Sality.aa | 193081 |
| 3 |  0 0 |
Net-Worm.Win32.Kido.ih | 175811 |
| 4 |  0 0 |
Net-Worm.Win32.Kido.iq | 141243 |
| 5 |  new new |
Exploit.JS.Agent.bab | 134868 |
| 6 |  -1 -1 |
Trojan.JS.Agent.bhr | 130424 |
| 7 |  -1 -1 |
Worm.Win32.FlyStudio.cu | 102143 |
| 8 |  -1 -1 |
Virus.Win32.Virut.ce | 69078 |
| 9 |  -1 -1 |
Trojan-Downloader.Win32.VB.eql | 57578 |
| 10 |  -1 -1 |
Worm.Win32.Mabezat.b | 47548 |
| 11 |  new new |
P2P-Worm.Win32.Palevo.fuc | 44130 |
| 12 |  -2 -2 |
Trojan-Dropper.Win32.Flystud.yo | 40081 |
| 13 |  new new |
Worm.Win32.VBNA.b | 33235 |
| 14 |  0 0 |
Trojan.Win32.Autoit.ci | 32214 |
| 15 |  2 2 |
Trojan-Downloader.Win32.Geral.cnh | 31525 |
| 16 |  -5 -5 |
Worm.Win32.AutoIt.tc | 30585 |
| 17 |  -5 -5 |
Packed.Win32.Krap.l | 29149 |
| 18 |  new new |
Trojan.Win32.AutoRun.aje | 25890 |
| 19 |  return return |
Email-Worm.Win32.Brontok.q | 25183 |
| 20 |  new new |
Trojan.Win32.Autorun.ke | 24809 |
The first ten places on the above list remain virtually unchanged from last month, with the Kido network worm and the Sality virus continuing to occupy the top four places. Fifth place saw the appearance of Exploit.JS.Agent.bab, which shunted the next five programs down one place, but we’ll talk more about that exploit a little later.
The new variant of the popular P2P-Worm.Palevo claimed eleventh spot in the list. Palevo.fuc actively seeks out any confidential data entered into a user’s browser window. Peer-to-Peer file sharing using programs such as BearShare, iMesh, Shareaza and eMule is the main method by which this worm propagates. It makes multiple copies of itself in folders used to store files that are commonly downloaded and uploaded, giving catchy names to those copies in the hope that they will attract the attention of potential victims. Other means by which P2P-Worm.Win32.Palevo.fuc propagates include multiple copying to network folders and other network resources, sending links via instant messengers and by teaming up with Trojan.Win32.Autorun to infect any kind of removable device that it may come into contact with.
At least 50,000 removable devices fell victim to infection by the two new variants of Trojan.Win32.Autorun that currently occupy eighteenth and twentieth place in our first Top 20. Both malware samples are autorun.inf files that launch a worm on the same infected device that they themselves reside on as soon as the device is connected to a computer.
Last but not least for this section, there is Worm.Win32.VBNA.b in thirteenth place, a program written in Visual Basic and classified as a malicious packer.
Malicious programs on the Internet
The second Top Twenty list below shows data generated by the web antivirus component and reflects the online threat landscape. This table includes malware detected on web pages and malware downloaded to victim machines from web pages.
| Position | Change in position | Name | Number of attempted downloads |
| 1 |  0 0 |
Trojan-Clicker.JS.Iframe.bb | 490331 |
| 2 |  new new |
Exploit.JS.Agent.bab | 341085 |
| 3 |  return return |
Trojan-Downloader.JS.Pegel.b | 220359 |
| 4 |  -2 -2 |
Exploit.Java.CVE-2010-0886.a | 214968 |
| 5 |  0 0 |
Trojan.JS.Agent.bhr | 77837 |
| 6 |  new new |
Exploit.JS.Pdfka.clk | 74592 |
| 7 |  0 0 |
not-a-virus:AdWare.Win32.FunWeb.q | 65550 |
| 8 |  new new |
Exploit.JS.Pdfka.ckp | 59680 |
| 9 |  new new |
Worm.Win32.VBNA.b | 57442 |
| 10 |  1 1 |
Trojan-Clicker.JS.Agent.ma | 54728 |
| 11 |  new new |
Hoax.HTML.FakeAntivirus.f | 50651 |
| 12 |  new new |
not-a-virus:AdWare.Win32.FunWeb.ds | 49720 |
| 13 |  -5 -5 |
Exploit.JS.CVE-2010-0806.i | 48089 |
| 14 |  new new |
Exploit.JS.Pdfka.clm | 45489 |
| 15 |  0 0 |
not-a-virus:AdWare.Win32.Shopper.l | 44913 |
| 16 |  0 0 |
Trojan.JS.Redirector.l | 43787 |
| 17 |  -8 -8 |
Exploit.JS.CVE-2010-0806.b | 39143 |
| 18 |  new new |
Trojan.JS.Agent.bky | 36481 |
| 19 |  new new |
Trojan.JS.Fraud.af | 35410 |
| 20 |  -17 -17 |
Trojan.JS.Redirector.cq | 35375 |
Despite some significant changes to this Top 20, five entries, including the number one slot, were non-movers.
This month’s real surprise was the re-entry of Trojan-Downloader.JS.Pegel.b in third place, which is a repeat of the situation we wrote about in April regarding Trojan-Downloader.JS.Gumblar.x. The last time Pegel was highly active was back in February of this year when there were six variants of the family in our list of the most widespread malware on the Internet, with Pegel.b leading the way. Various PDF exploits and the Java CVE-2010-0886 exploit, which we described last month, were used in conjunction with Pegel.b. As well as Pegel and Gumblar, there are some very straightforward but widespread scripts about that are used by cybercriminals to infect legitimate sites. One of them is Trojan.JS.Agent.bky, currently in eighteenth place and on average 0x3B bytes, or a mere 59 symbols in length. Its sole function is to download the main piece of malicious code from a fixed URL.
The second most prevalent web antivirus component on the list, Exploit.JS.Agent.bab, was detected more than 340,000 times. It exploits the old CVE-2010-0806 vulnerability, downloading different malicious programs to victim machines. This is reminiscent of the more familiar scenario whereby Trojan-Downloader.Win32.Geral is downloaded, followed by Rootkit.Win32.Agent, Backdoor.Win32.Hupigon and then Trojan-GameTheif.Win32.Maganiz, Trojan-GameTheif.Win32.WOW etc.
Three new variants of Exploit.JS.Pdfka also made an appearance at sixth, eighth and fourteenth places. It looks like the representatives of this family could be around for a very long time in our second Top 20 as we witness a battle royal between Adobe updates and the latest variants of this exploit, each vying for supremacy over the other. All three modifications downloaded a wide variety of malicious programs.
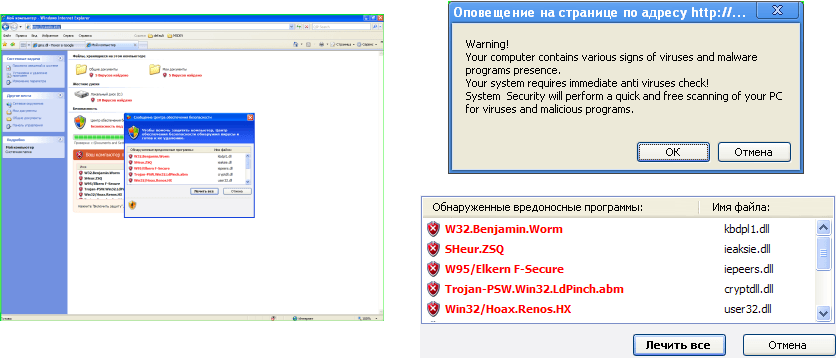
Internet pages informing users that their computer is infected have become the norm in recent months. Users are offered the chance to scan their machines by browser windows that resemble My Computer. After these ‘scans’ are performed, any click of the mouse, even if the user wants to close the page, downloads an ‘antivirus’ program which in most cases turns out to be a representative of the Trojan-Ransom family or Trojan.Win32.FraudPack. These pages are known to Kaspersky Lab’s users as Hoax.HTML.FakeAntivirus.f and Trojan.JS.Fraud.af.
Potentially unwanted software has also made it into our list this month, with the new variant of AdWare.Win32.FunWeb.ds occupying twelfth place. The raison d’être of this program is to gather data about users’ search requests and more often than not, this data is then used by a system for displaying the banners that frequently pop up during online surfing sessions.
For the majority of cybercriminals, confidential data offers rich pickings. By perfecting the packaging and propagation techniques of malware, seeking out new vulnerabilities and making sly use of phishing and social engineering, the malware writers are trying to harvest as much of this type of data as they can. Despite the fact that antivirus companies are constantly on the alert for this kind of thing, users also need to do their bit and remain vigilant. Remember, how and what you search for on the Internet can potentially reveal a whole lot more about you than you might want anyone to know!
Countries launching the most web-borne infections:





















Monthly Malware Statistics: June 2010