
Two Top Twenties have been compiled from data generated by the Kaspersky Security Network (KSN) throughout January 2009.
The first Top Twenty is based on data collected by Kaspersky Lab’s 2009 antivirus product and gives details of malicious, advertising, and potentially unwanted programs detected on users’ computers.
| Position | Change in position | Name | |||
| 1 |  0 0 |
Virus.Win32.Sality.aa | |||
| 2 |  0 0 |
Packed.Win32.Krap.b | |||
| 3 |  1 1 |
Worm.Win32.AutoRun.dui | |||
| 4 |  -1 -1 |
Trojan-Downloader.Win32.VB.eql | |||
| 5 |  3 3 |
Trojan.Win32.Autoit.ci | |||
| 6 |  0 0 |
Trojan-Downloader.WMA.GetCodec.c | |||
| 7 |  2 2 |
Packed.Win32.Black.a | |||
| 8 |  -1 -1 |
Virus.Win32.Alman.b | |||
| 9 |  5 5 |
Trojan.Win32.Obfuscated.gen | |||
| 10 |  10 10 |
Trojan-Downloader.WMA.GetCodec.r | |||
| 11 |  New New |
Exploit.JS.Agent.aak | |||
| 12 |  -1 -1 |
13 |  -3 -3 |
Worm.Win32.AutoIt.ar | |
| 14 |  1 1 |
Email-Worm.Win32.Brontok.q | |||
| 15 |  New New |
Virus.Win32.Sality.z | |||
| 16 |  New New |
Net-Worm.Win32.Kido.ih | |||
| 17 |  Return Return |
Trojan-Downloader.WMA.Wimad.n | |||
| 18 |  -2 -2 |
Virus.Win32.VB.bu | |||
| 19 |  -2 -2 |
Trojan.Win32.Agent.abt | |||
| 20 |  New New |
Worm.Win32.AutoRun.vnq |
There were no major changes to the composition of the first Top Twenty during the first month of 2009. Exploit.JS.Agent.aak took the place of Trojan.HTML.Agent.ai and Trojan-Downloader.JS.Agent.czm which appeared in the December ratings. The AutoRun.eee worm, which has vanished from this month’s Top Twenty, has now been replaced by Worm.Win32.AutoRun.vnq. This is not surprising, as frequent new modifications are characteristic of these types of malicious program.
Trojan-Downloader.WMA.Wimad.n, which dropped out of the ratings in November, has also returned to the game. The result of this activity is a Top Twenty with three non-standard downloader programs; evidence of the mass spread of this type of Trojan program, and the trusting attitude users have towards multi-media files. The sharp rise of Trojan-Downloader.WMA.GetCodec.r by ten places confirms that the propagation method described in last month’s Top Twenty, whereby malicious programs use peer-to-peer networks and multimedia downloaders to spread has been very effective.
While Sality.aa still retains its leading position, it has been joined by Sality.z, making Sality one of the most widespread and dangerous families of the recent past.
The notorious Kido family, network worms which use a critical vulnerability in Microsoft Windows to spread, is also present. The current epidemic, the propagation method used, and the number of potentially vulnerable computers mean the appearance of Kido variants in this month’s Top Twenty are no surprise.
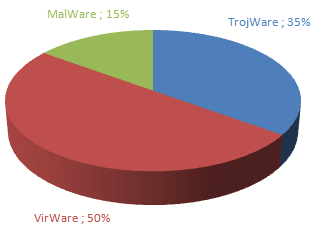
All malicious, advertising and potentially unwanted programs in the first Top Twenty can be grouped according to the main classes of threats which we detect. Self-replicating programs again prevail over Trojan programs.
In total, 46014 unique malicious, advertising, and potentially unwanted programs were detected on users’ computers in January. It should be noted that the holiday period did not result in a drop in threats found ‘in-the-wild’; on the contrary, there were 7800 more ‘in-the-wild’ samples detected than in December (38190).
The second Top Twenty presents data on which malicious programs most commonly infected objects detected on users’ computers. Malicious programs capable of infecting files make up the majority of this ranking.
| Position | Change in position | Name |
| 1 |  0 0 |
Virus.Win32.Sality.aa |
| 2 |  0 0 |
Worm.Win32.Mabezat.b |
| 3 |  2 2 |
Net-Worm.Win32.Nimda |
| 4 |  -1 -1 |
Virus.Win32.Xorer.du |
| 5 |  1 1 |
Virus.Win32.Alman.b |
| 6 |  3 3 |
Virus.Win32.Sality.z |
| 7 |  0 0 |
Virus.Win32.Parite.b |
| 8 |  2 2 |
Virus.Win32.Virut.q |
| 9 |  -5 -5 |
Trojan-Downloader.HTML.Agent.ml |
| 10 |  -2 -2 |
Virus.Win32.Virut.n |
| 11 |  1 1 |
Email-Worm.Win32.Runouce.b |
| 12 |  1 1 |
Worm.Win32.Otwycal.g |
| 13 |  1 1 |
P2P-Worm.Win32.Bacteraloh.h |
| 14 |  4 4 |
Virus.Win32.Hidrag.a |
| 15 |  5 5 |
Virus.Win32.Small.l |
| 16 |  -5 -5 |
Virus.Win32.Parite.a |
| 17 |  Return Return |
Worm.Win32.Fujack.bd |
| 18 |  New New |
P2P-Worm.Win32.Deecee.a |
| 19 |  -4 -4 |
Trojan.Win32.Obfuscated.gen |
| 20 |  New New |
Virus.Win32.Sality.y |
Sality.z was the latest representative of Virus.Win32.Sality to make it into the first Top Twenty. Sality.y has appeared in the second Top Twenty, confirming again the high activity of this family of self-replicating programs.
An interesting newcomer to the second rating is P2P-Worm.Win32.Deecee.a. This worm spreads via the DC++ peer-to-peer network, and is capable of downloading other malicious files. It has gained a place in the second Top Twenty not so much because of the number of machines it has infected, but because of the number of copies of itself on every infected computer – it copies itself multiple times when installing. Once installed, this worm makes the copies of itself publicly accessible. The executable files which spread in this way have names which follow a set pattern: a prefix such as ‘(CRACK)’, ‘(PATCH)’, then the name of a popular application: ‘ADOBE ILLUSTRATOR (All Versions)’, ‘GTA SAN ANDREAS ACTION 1 DVD’, etc.
Worm.VBS.Headtail.a, which returned to the rankings in November, has disappeared again, continuing to exhibit the unstable behaviour which we noted towards the end of 2008.

















Monthly Malware Statistics: January 2009