
Windows may be ubiquitous, but there’s a thriving variety of alternative operating systems for enterprise and home use. However, the alternatives aren’t as risk free as some people might think.
If you read online IT publications and message boards, you’ll know the story: as soon as a new Trojan is reported, there’ll be a flood of comments along the lines of “That would never have happened with Linux!” And let’s be honest: at least 99 % of the time this is true. The fact is that the majority of malicious programs identified to date (well over 2 million) target Windows. Linux, on the other hand, with a mere 1898 malicious programs targeting the operating system, appears to be relatively secure. And to date, only 48 malicious programs for Apple’s OS X have been identified.
Turbulent beginnings
In the early 1970s – long before the appearance of Microsoft – the Creeper virus was infecting computers running DEC’s TENEX operating system. This malware could be seen as being ahead of its time, as it used the ARPANET – the forerunner of today’s Internet – to spread. Creeper was followed by Pervade in 1975. Pervade was coded for UNIVAC systems and had been created in order to distribute a game called “Animal”. Finally, in 1982, it was Apple’s turn; users had the dubious pleasure of dealing with Rich Skrenta’s Elk Cloner, a virus that spread via floppy disks and regularly caused systems to crash.
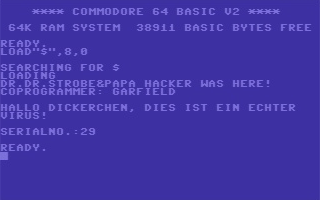
Fig.1 Back in the day…message displayed by the BHP virus
Four years later, C64 users joined the virus victims – the BHP virus (believed to have been created by the German “Bayerische Hacker Post” group) caused the screen to flicker at irregular intervals, greeting the unfortunate victim with a message which read “HALLO DICKERCHEN, DIES IST EIN ECHTER VIRUS!” (which translates as “HALLO FATTY, THIS IS A REAL VIRUS!”). The text was followed by a serial number, which increased by an increment of one with each new infection. The virus also ensured it would be able to survive a system reset by hooking a number of interrupts.
It was only in 1986 that the first MS-DOS-compatible malware finally appeared. Brain was a boot sector virus; conveniently, the malware code included the names, addresses and telephone numbers of its authors. Amjad and Basit Farooq Alvi were brothers who asserted they had created Brain in an effort to determine the level of computer piracy in India. However, they subsequently had to admit that they had lost control over their experiment.
Fig. 2: Shellcode in Backdoor.UNIX.Galore.11
In the years that followed, the virus scene really started to flourish, and soon there were viruses for every operating system. Over 190 pieces of malware were identified for the Commodore Amiga, with another two dozen targeting the Atari ST. These included the “C’t” virus [http://www.stcarchiv.de/am88/06_viren.php], which was actually published in 1988 in iX’s sister publication C’t as an assembler listing that readers could reproduce – proof indeed of the casual attitude towards malware still prevalent at the time.
An undesirable malware monopoly
Viruses, worms, and other malware only really started to flourish when private households gained access to the World Wide Web. Previously, malicious code had only been able to crawl slowly from floppy disk to floppy disk, but now malicious programs such as Melissa or ILOVEYOU were able to travel around the world in a matter of minutes. An increased variety of platforms was to play a deciding role. Malware which spread by email was only able to realize its full potential (and pose a threat to the majority of Internet users) once Windows and Outlook gained a significant market share. The largely heterogeneous system landscape, typical of the private sector during the 1980s, was replaced by MS-DOS and Windows. And something else changed with the arrival of the Internet: for the first time, there was a way in which malicious programs could communicate with their creators.
While the spread of viruses and worms had previously been a matter of chance, and something that couldn’t be controlled, data could now be taken from a target computer or commands relayed to an agent on a remote hard disk. This created ideal conditions for DdoS attacks and mass spam mailings, and, in turn, created a golden opportunity to earn money by distributing malicious programs. Obviously, a person who earns their money from conducting attacks of this kind is always going to target which offers the greatest number of targets. For this reason, the millions of Trojans that are sent by email every day target Windows users – malicious code targeting BeOS or Plan 9 would be unlike to have the desired effect. Whether or not these systems are actually more secure than Windows XP is therefore a moot point – even if such a thing as an unhackable operating system existed, there would still be more than enough vulnerable applications on the hard drive with security loopholes that could be exploited for the purpose of attack.
The status quo
Microsoft Windows thus effectively became the standard for malware due to its high market share. Not only was the number of new malicious programs targeting Windows far higher than the number targeting non-Windows users, there was also a difference in the type of malware targeting each environment. Two distinct worlds were established.
| Operating system | Total | Backdoors, Hacktools, Exploits & Rootkits | Viruses and Worms | Trojans |
| Linux | 1898 | 942 (50%) | 136 (7%) | 88 (5%) |
| FreeBSD | 43 | 33 (77%) | 10 (23%) | 0 (0%) |
| SunOS/Solaris | 119 | 99 (83%) | 17 (15%) | 3 (2%) |
| Unix | 212 | 76 (36%) | 118 (56%) | 3 (1%) |
| OSX | 48 | 14 (29%) | 9 (19%) | 11 (23%) |
| Windows | 2247659 | 501515 (22%) | 40188 (2%) | 1232798 (55%) |
Fig 2: While Windows users are targeted by Trojans, other operating systems are targeted by
worms and rootkits.
In the case of Windows malware, the goal in the majority of cases is to take over a computer and use it to conduct DDoS attacks, send out spam, and where possible use a worm component to take over as many other computers as possible. Even if it does become clear to the user that his/ her machine is infected, that’s not a disaster for the cybercriminals: botnets are so large (for instance, it’s estimated that several million zombie machines make up the Kido/ Conficker botnet) that the loss of one isn’t really a problem.
In the case of attacks targeting Unix-like systems, however, the goal is to remain unnoticed, in order to obtain credit card details from online shops, or individual users’ passwords. For the most part, attacks are not conducted using Trojans but by exploiting known security loopholes in server services.
New friends for OS X
Until October 2007, the malware landscape for Apple’s OS X had been largely unspectacular. Two exploits, four worms, one virus and one rootkit – and these were all essentially proof of concept creations, without any obvious financial returns for an attacker. However, this changed with the appearance in autumn of the first Trojan for OS X: OSX.RSPluga.A. As mentioned above, there’s little point in sending Trojans for non-Windows systems via spam. And the creators of this particular malicious program apparently thought the same, choosing instead to advertise what appeared to be a porn site on various Mac user forums. However, anyone clicking on one of the videos was instead shown a message indicating that a codec was missing. The user was naturally also offered the option of downloading the codec. Users had to enter their administrator account password in order to install the “codec”, but in their enthusiasm, some Mac users showed themselves to be no less gullible than Windows users in similar situations. OSX.RSPluga.A manipulates DNS entries in such a way that numerous addresses – including those of several banks, as well as eBay and PayPal – are no longer correctly resolved. As a result, the victims are redirected to phishing sites.
In mid-January, the Finnish antivirus company F-Secure reported the first rogue antivirus solution. This free program “detected” several pieces of malware on computers that were 100 % clean; to remove the supposed threat, the customer had to purchase the product. This type of scam is nothing new for Windows users, but just how trusting Mac users will be is something that the developers of such programs are keen to find out.
No need to panic
Given the numbers, some people will ask what the big deal is. After all, any non-Windows system is security heaven when compared to Windows systems. But here’s a quick wake-up call: Trojans don’t need root privileges in order to spy on data or to phone home on port 80. And in a world where even IT newbies can be heard saying “Isn’t that Ubuntu?” Linux users have to be prepared for the cybercriminals targeting inexperienced users to look in their direction too.
At the end of the day, what poses the greatest risk is the belief that a system is impregnable. These days even computers from discount stores come with antivirus protection preinstalled but at the same time many Linux users refuse to even install free scanners such as ClamAV, arguing that it simply isn’t necessary. The open source community in particular offers a range of very high-performance solutions, with technologies such as SELinux, AppArmor, and a range of intrusion detection systems. Those who don’t use these solutions (either because they feel it takes too much effort or because they think there’s no need) probably won’t notice when their computer gets taken over by someone looking for rich pickings.
Protecting businesses
Businesses in particular can’t allow themselves to subscribe to security myths. There’s no question that every server needs antivirus protection, even if only to protect the numerous Windows users on the network.
In order to stop malicious attacks at the gateway, it’s worth the trouble of implementing firewalls, intrusion detection and intrusion prevention systems. Whether server appliances or dedicated servers are deployed, Linux or Unix-like systems often act as the first line of protection for the internal network in the case of gateway installations. In addition to defining available services and providing the first line of defense against hacker attacks, a properly configured firewall can also be deployed to prevent self-propagating malware (worms) from replicating across network connections. For instance, it’s possible to protect a network against “Lovesan.a” simply by blocking TCP ports 135 and 4444.
However, a firewall can also have a damage limitation function. If the network does have infected clients, targeted blocking of ports can prevent connections from being established so that the affected system cannot be exploited. In order to minimize the overall risk of infection and attack, a number of scenarios should be considered when configuring a firewall, and authorized services and ports should be clearly defined.
Resourceful programmers have nevertheless found ways to circumvent simple security of this type. It’s still possible to smuggle data packets out using tunnel connections and authorized services (e.g. DNS and HTTP). This is why intelligent add-on modules such as intrusion detection or intrusion prevention systems, and application level firewalls, are a useful addition to classic firewalls.
Thanks be to Proxy!
It’s also possible to install a proxy rather than allowing employees to access the Internet directly. This not only reduces traffic, but can also increase security, as a significant amount of malware is spread via malicious websites. In Linux/Unix installations, Squid is probably the proxy most frequently used. It also offers its own dedicated interface: “ICAP”, the Internet Content Adaption Protocol (RFC 3507). Here, user requests are processed using RESPMOD (response modification), which analyses objects requested by web servers, and REQMOD (request modification), which scans objects sent to web servers. Parent proxies such as HAVP (http://www.server-side.de) are often deployed so that both HTTP traffic and native FTP traffic can be scanned. So-called transparent proxies are also popular, as they are easy to integrate. These are connected upstream of the actual gateway (firewall or similar) in this case, and do not require client configuration (browser configuration settings). The technical implementation of this solution can, for example, be made up of a server in bridge mode, from which a proxy either relays the requests to the content filter. Alternatively the proxy receives HTTP requests that have been redirected from the firewall as a dedicated server, and in small networks, this can be integrated with the firewall itself (TransProxy http://transproxy.sourceforge.net). Both options can be deployed relatively easily in Linux/Unix installations using standard tools.
Of course, proxies can’t guarantee complete protection either. Even the best virus scanner can’t crack password-protected files – and the limitations of proxy technologies are also clear when it comes to encrypted VPN connections.
Protecting email traffic
Email traffic remains one of the primary methods for spreading malware. Depending on the size of the network (number of users), a mail gateway system is deployed upstream in gateway installations for (for example) Exchange, Lotus Domino or alternative groupware solutions. Linux or Unix (Solaris) or derivatives (*BSD) with MTAs (Mail Transfer Agents) such as postfix, exim, qmail or sendmail are also often deployed here. These offer their own filter interfaces for virus scanners and spam filters. The most common method is what is known as dual MTA. This means that each email is delivered twice to the MTA. First an email is received from the remote host. This is then relayed to the content filter for verification, and from there back to the MTA. Sendmail also offers an API interface (the Milter API). With these upstream systems, linked filter solutions which are made up of multiple virus scanners and spam filters (e.g. 2-3 virus scanners and 2 spam filters) are also deployed for mail traffic. The advantage is that the actual scanner can also run on a dedicated system and be addressed which obviously reduces the load on the mail gateway. In this way, high-availability solutions such as a mail gateway cluster (MTA) and content filter cluster can also be integrated very easily. However, fully integrated cluster and HA solutions are also widely used (MTA and filter in a single system). Internal mail servers also benefit from upstream filter systems due to fewer resources being used for scanning, and storing malware and spam. Fewer resources are also used for processing in cases where there is a significant amount of email traffic. This is why a relay server solution is also worth considering for smaller companies. Some manufacturers also offer integrated “out of the box” solutions in order to simplify administration.
Protecting file servers
Data which has been saved electronically is generally an important asset for a company, regardless of whether this information relates to production plans, warehouse inventories or other data. Personal data in particular, or data that requires special protection such as employee lists, accounts and CVs, is often stored on file servers. These central repositories in the network should always be protected in order to prevent theft, data manipulation or espionage.
Many networks feature alternative systems with Samba services together with Windows servers. In such cases, integration is possible using a VFS (virtual file system) module that redirects data traffic via the virus scanner. This provides on-access (read and/or write) data scanning.
Kernel modules (Linux, FreeBSD) are also available for some alternative systems. These not only protect the Samba service itself, but also check all objects on the system. These are available both for NFS, and also for FTP and web servers. The disadvantage of this solution is that support for the new kernel has to be checked and the module will need to be recompiled following kernel updates.
The deployment of non-Windows servers is widespread. From AS/400 to Solaris, HP-US, IRIX, and AIX, to name but a few, these systems offer everything from file systems to database systems, industry-specific applications and financial management software. Here, the difficulty in finding appropriate security solutions lies not only in the OS (operation system) platforms, but also in the diverse CPU architectures (SPARC, PPC, Itanium, Alpha, MIPS, PA-RISC, etc. in addition to Intel). If a solution is not available for the actual systems in question, these systems should be isolated from the rest of the network in order to reduce risk as far as possible. Options include separate networks with dedicated firewalls, access restriction, IDS or IPS.
A varied client landscape
99% of all client-side implementations are made up of Windows computers – however, Linux, BSD and Mac OS X workstations obviously also need to be protected, as attacks can never be entirely ruled out. Media such as CD-ROMs and DVDs represent one attack vector, with floppy disks and Zip disks also still posing a risk in some cases. USB flash drives and USB/FireWire external hard drives also tend to get passed from system to system, giving malware the opportunity to spread.
One particular problem is that in addition to workstations and laptops, an increasing number of smartphones and PDAs are now in use, which obviously also have to be protected. In standard network configurations, the attack vector was clear: the Internet. These days, system administrators and security advisors have to address the issue of safeguarding internal nodes. This task is not made any easier by the fact that the range of platforms continues to expand. In addition to various versions of Windows Mobile, systems such as Symbian and Linux, and also proprietary systems, are now being deployed. Finding security solutions for these systems is a difficult and sometimes impossible task.
Conclusion
Using non-mainstream technologies does offer certain security advantages but this is by no means guaranteed: for instance, while a Solaris desktop system may be considered unconventional, its server counterpart is a standard system that is subject to attack like any other server. Those who care about the security of their data should therefore ensure their computers are protected, regardless of the operating system. Ideally this should be done by using a combination of technologies that complement one another. And even then, caution is still advisable – increasing use is being made of web applications rather than applications on the local computer. One typical example is forums and message boards with poor security: HTML code can be injected to facilitate cross-site scripting attacks, regardless of the operating system. So in closing, the message remains the same: Be careful, Tux, be careful!




















Malware beyond Vista and XP