
The year in figures
According to Kaspersky Lab, in 2016:
- The proportion of spam in email flows was 58.31%, which is 3.03 percentage points more than in 2015.
- 62.16% of spam emails were no more than 2 KB in size.
- 12.08% of spam was sent from the US.
- Trojan.Win32.Bayrob was the most popular malware family distributed via email.
- Germany (14.13%) was the country where email antivirus was triggered most often.
- There were 154,957,897 instances of the Anti-Phishing system being triggered.
- A total of 15.29% unique users were attacked by phishers.
- Brazil suffered the highest number of phishing attacks, with 27.61% of the global total.
- 47.48% of incidents triggering the heuristic component in the Anti-Phishing system targeted clients of various financial organizations.
World events in spam
In 2016, fraudulent spam exploited the theme of major sporting events: the European Football Championship, the Olympic Games in Brazil, as well as the upcoming World Cups in 2018 and 2022. Typically, spammers send out fake notifications of lottery wins linked to one of these events. The content of the fake messages wasn’t exactly very original: the lottery was supposedly held by an official organization and the recipient’s address was randomly selected from millions of other addresses. To get their prize, the recipient had to reply to the email and provide some personal information.
With these sport-themed emails more details were often included in DOC, PDF or JPEG attachments that also contained graphic elements such as official emblems, event and sponsor logos. Messages that displayed the spam text directly in the body of the email were not very numerous. To add a bit of variety to their messages, spammers resorted to an old trick: they changed the text, the email addresses used for feedback, sender addresses, the attachment names, the size, etc. At the same, emails with the same attachment could be found in our traps on numerous occasions over a period of several months.
In the fourth quarter of 2016, spammers turned their attention to the future World Cup tournaments scheduled for 2018 and 2022. Spam traffic often included fraudulent notifications of lottery wins exploiting this theme.
The football theme was also used in malicious spam. In particular, cybercriminals sent out fake notifications with scans taken from a website that publishes news about computer games and the world of football, apparently in an attempt to arouse interest among recipients. The attached ZIP archive included a JavaScript downloader detected by Kaspersky Lab as Trojan-Downloader.Script.Generic. This malware, in turn, downloaded other malicious software to the victim’s computer.
The subject of terrorism, which has remained an important global issue in recent years, was also exploited in spam mailings. Numerous so-called Nigerian letters were sent to users on behalf of both state organization employees and individuals. The details of the stories may have differed, but the senders’ intention was the same – to get the recipient’s attention with promises of large sums of money and make them join in a conversation. Nigerian letters exploiting the tense situation in Syria remained popular in 2016 and were actively used to trick users.
Malicious spam exploiting the theme of terrorism was less common. It was used to steal personal information, organize DDoS attacks and install additional malware on victims’ computers.
Email offers from Chinese factories
In the email traffic for 2016, we often came across messages from Chinese factories and plants advertising their products. These spammers offered both finished products as well as spare parts for a variety of different spheres.
The text of a typical spam message began with an impersonal greeting to the recipient, followed by the name and surname of the factory manager. Often, the email described the merits of the company, its achievements and types of certification. The products offered by the company were either listed in the email or sent at the request of the recipient. For greater clarity, some of the emails also contained pictures of the goods on offer. At the end of the message, there were contact details (phone, mobile phone and fax numbers, email address, various messengers). Sometimes the contact details were specified in the image attached to the email.
The authors of the emails were representatives of the manufacturers, but the sender addresses were registered with both free email services and the companies’ domain names. Sometimes the messages included a company website, if the company had one.
In many countries, there was a time when small and medium-sized businesses preferred to use spam to promote their products. But users began to view this kind of advertising as undesirable, anti-spam laws were introduced, and, most importantly, new, more targeted, convenient and less intrusive advertising platforms appeared, with social networking sites prominent among them. We can only presume why Chinese businesses have not followed this trend (given that China has passed its own anti-spam law, which is one of the strictest in the world). The fact is that social networks in China are mainly internal, with global giants such as Facebook not permitted. As a result, Chinese entrepreneurs have far fewer legal means of entering the international market.
A year of ransomware in spam
In 2016, we recorded a huge amount of malicious spam. In previous years, Fraud.gen was the program most often used in malicious attachments. It appears in the form of an HTML page and is designed to steal the victim’s credit card data. In 2016, the absolute leaders in spam were Trojan downloaders that download ransomware to the victim’s computer. The most popular were mass spam mailings sent out to infect user computers with the Locky encryptor. However, other ransomware such as Petya, Cryakl and Shade were also widespread.
The number of malicious programs began to increase in December 2015 and continued to grow in waves throughout the year. The sharp falls were mainly caused by the fact that cybercriminals temporarily disabled the Necurs botnet, responsible for the majority of spam spreading Locky. Once the botnet was up and running again, the cybercriminals changed the spam templates.
Quantity of malicious emails in spam, 2016
In 2016, the Anti-Phishing system was triggered 239,979,660 times on the computers of Kaspersky Lab users, which is four times more than the previous year.
Such extensive use of ransomware may be due to the availability of this sort of malware on the black market. Currently, cybercriminals can not only rent a botnet to send out spam but also connect to so-called Ransomware-as-a-Service. This means that the attacker may not be a hacker in the traditional sense, and may not even know how to code.
Malicious spam messages often imitated personal correspondence, prompting recipients to view attached documents under various pretexts. Cybercriminals also sent out fake bills, or receipt notifications or even messages from office equipment with scanned documents allegedly attached.
Both examples above contain an attachment in the form of a malicious file with a .wsf extension, detected by Kaspersky Lab as Trojan-Downloader.JS.Agent.myd. The malicious file is written in JavaScript and downloads a Locky encryptor modification to the victim’s machine.
This screenshot shows an attachment containing a malicious file with a .jse extension, detected by Kaspersky Lab as Trojan-Downloader.JS.Cryptoload.auk. This is yet another malicious file written in JavaScript that downloads a Locky encryptor modification to the victim’s machine.
Overall, a wide variety of malicious attachments were used. As a rule, these were archives containing programs written in Java and JavaScript (JS files, JAR, WSF, WRN, and others), but there were also office documents with macros (DOC, DOCX, XLS, RTF) as well as classic executable files (EXE). Sometimes rare archive formats such as CAB were used.
When launched, ransomware programs encrypt the data on a user’s computer and demand a ransom (usually in bitcoins via the Tor network). More details about these programs can be found in our report Kaspersky Security Bulletin 2016. The ransomware revolution.
Spammer tricks
Adding ‘noise’ to text
To make each email unique, spammers insert random sequences of characters in their messages that are invisible to the user. This trick is not new, but spammers continue to use it, perfecting their methods. Below we describe the most popular tricks of 2016 used by spammers to add ‘noise’. All the examples below are taken from real-life spam messages.
-
Small letters and/or white text.
The easiest and oldest trick: the text can be written in white font (ffffff – 16 hexadecimal code written in white).
In this example, the random sequence of letters written in very small print and in white are arranged between words of a standard size in the sentence “You have received a £500”.
-
Text that is not displayed.
With the help of the attribute style = “display: none;” text in an email is simply not displayed. In standard situations, this tag is used in rough drafts, for example. When it comes to spam, these tags, containing random text, are inserted in messages in large quantities and if the anti-spam filter is not set up to process such tags, the text of an email practically disappears.
The same effect can be achieved by inserting a random sequence written in zero font:
-
Placing text outside the screen range.
Yet another way to make junk text invisible to the user is to write it in standard font, but insert it in parts of the email that are beyond the screen frame (to the extreme left or right, or below the main part):
-
Using tags that by default are not visible to users.
Sometimes random text is inserted in tags that are not designed to display text to the user. Typically, comment tags are used, though there are other examples:
The content of the <noscript> tag is only displayed on computers with unsupported or disabled scripts, so most users will not see it.
-
Using tags to add noise
Rather than using random sequences of characters that are made invisible, sometimes text is obfuscated with tags that have no value and cannot be interpreted:
The number of these sorts of tags in some spam emails can be in the hundreds.
Sometimes a very random sequence is inserted inside a tag as its attribute, rather than between specific tags:
This attribute will, of course, not be interpreted either and will not be displayed in the email that the user sees.
Masking links
There may be numerous ways of altering text in an email, but when it comes to URLs in spam messages, the situation is different. There can be lots of URLs in a single mass mailing (even reaching into the thousands), but they are subject to more limitations, as spammers have to pay for the purchase of each domain. However, attackers have come up with different techniques to make each link unique while also ensuring it opens correctly when clicked.
-
Obfuscation of domains using the UTF range:
In last year’s report we described some spammer tricks that involved different ways of expressing domain names and IP addresses. The trend for writing domain names using symbols from different UTF ranges and using different numerical systems for IP addresses continued in 2016.
Especially popular with spammers were mathematical alphanumeric symbols. For example:
Domain written using mathematical bold script.
Domain written using mathematical monospace small.
The range is designed for specific mathematical formulas and must not be used in plain text or hyperlinks.
-
Mixing encodings
The above trick was diversified by mixing encodings: spammers use the Latin alphabet in Unicode to write some of the domain characters, while the rest are written using characters from special URL-encoded ranges.
The domain from the example above is first changed to:
and then to server119.bullten.org.
-
URL shortening services with added noise
In addition to the various ways of writing the actual spammer site, from time to time cybercriminals use another trick to avoid mentioning the site directly in an email. This involves the use of URL shortening services and redirects. In 2016, spammers also resorted to a variety of other methods to add noise to each URL.
They inserted characters, slashes and dots between the URL shortening service and the actual link identifier (the meaningful part is marked in bold; the rest is noise):
Sometimes comment tags end up there:
To deceive filters further, the names of different, usually well-known, sites are inserted in the noise part:
All these parts will be dropped when the link is clicked.
Yet another way to obfuscate a link is to add non-existent parameters to the end of the link:
Everything that comes after the question mark in the link is not actually part of the URL – these characters are, in fact, parameters. The parameters can include a variety of information: for example, the unsubscribe link often contains the email address that needs to be entered in the unsubscribe form. However, URL shortening services, like many other sites, do not require or accept any parameters, so this part of the URL is simply dropped during the redirect process. Spammers take advantage of this and insert random sequences of parameters. In this particular case, the .pdf extension is added to the end of the parameters. This is not done to confuse the filters but rather the user, who is likely to think the link leads to a PDF file.
-
Prefixes
As well as parameters that can be added to the end of a link, noise elements can also be added to the beginning. These elements may include symbols that are ignored by the link interpreter when a redirect occurs, for example:
(In this example, in addition to the noise at the beginning of the link and nonexistent parameters at the end, the link itself is an IP address written partially in octal and partially in hexadecimal encoding.)
The most common technique for adding noise at the beginning of a link is to use the @ symbol. The @ symbol inserted before the domain can be utilized to identify the user in the domain (something that is no longer really applied these days). For sites that do not require identification, everything that comes before @ will simply be ignored by the browser.
The symbol is useful for spammers because it allows them not only to add noise to the link but also to make it look more trustworthy to the user by specifying a well-known site before the @ symbol.
-
Masked redirects
Redirects have long been used by spammers to hide the main domain. We have already written about this in some detail. In 2016, the redirect methods used were not that diverse, but links with redirects were also obfuscated. The methods used were the same as those used with URL shortening services: the @ symbol, parameters and additional characters.
Cybercriminals often used several techniques at once – concealing and obfuscating the original link:
In the example below, the name of the site used to distract the user’s attention comes before the @ symbol, followed by the redirect to the URL shortening service (which is also just noise with several @ symbols), and it is only from this part that the user will get to the spammer’s site.
Statistics
Proportion of spam in email traffic
In 2016, the proportion of spam in email traffic was 58.31%, which is 3.03 percentage points higher than the previous year.
The proportion of spam in email traffic, 2016
The lowest volume – 54.61% – was registered in February of 2016. After that, the proportion of spam grew steadily and reached a peak by the end of the year – 61.66% in November.
Interestingly, the last time there was an annual increase in the proportion of spam in email traffic was eight years ago. Since then, the percentage of spam has fallen continuously from its peak of 85.2% in 2009, to 55.28% in 2015. We believe this was due to legitimate small and medium-sized businesses gradually phasing out their use of spam, turning instead to legal advertising platforms.
The proportion of spam in global email traffic, 2009-2016
This downward trend may now have come to a halt because all those who wanted to or could refrain from using spammer services have, for the most part, already done so. This slight growth is the result of a sharp increase in spam containing malicious attachments.
Sources of spam by country
Sources of spam by country, 2016
In 2016, the top three sources of spam saw some changes: India climbed to third place with 10.15% due to a substantial growth in the volume of spam distributed (+7.19 p.p.). Such a dramatic increase may have been caused by botnets being organized in the region. Vietnam (10.32%) added 4.19 p.p. to its share and also moved up the rankings to second place. The US (12.08%) remained the clear leader despite a decrease of 3.08 p.p.
China’s share (4.66%) fell by 1.46 p.p., though it remained in fourth. Following close behind were two Latin American countries – Mexico (4.40%) and Brazil (4.01%). Russia (3.53%), among the top three in 2015, ranked seventh in 2016 after seeing a 2.62 p.p. decrease in its share of distributed spam.
France (3.39%, +0.22 p.p.) and Germany (3.21%, -1.03 p.p.) came eighth and ninth respectively. Turkey rounded off the Top 10 with a share of 2.29%, which is 0.34 p.p. more than in 2015.
The size of spam emails
The proportion of super-short spam emails (under 2 KB) dropped in 2016 and averaged 62.16%. This is 16.97 p.p. lower than in the previous year. The share of emails sized 2-5 KB also fell to 4.70%.
The size of spam emails in 2016
Meanwhile, the proportion of bigger emails increased considerably: 5-10 KB (6.15%), 10-20 KB (14.47%) and 20-50 KB (10.08%). It means that 2016 saw a trend towards fewer super-short spam emails and more emails of average size – from 5-50 KB. This was caused by a sharp increase in the proportion of spam with malicious attachments.
Malicious attachments in email
Malware families
TOP 10 malware families, 2016
In 2016, Trojan-Downloader.JS.Agent was the most widespread malware family. A typical representative of this malware family is an obfuscated Java script using ADODB.Stream technology to download and run DLL, EXE and PDF files.
The Trojan-Downloader.VBS.Agent family occupied second place. They are VBS scripts utilizing ADODB.Stream technology to download ZIP archives and run software extracted from them.
In third place was Trojan-Downloader.MSWord.Agent. These malicious programs are DOC files with an embedded macro written in Visual Basic for Applications (VBA) that runs when the document is opened. The macro downloads another malicious file from a malicious site and runs it on the user’s computer.
Trojan-Downloader.JS.Cryptoload in fourth is a malware family whose representatives are an obfuscated JavaScript that downloads and runs encryptors.
Trojan.Win32.Bayrob rounded off the top five. The malicious programs from this Trojan family can download and run additional modules from the command server, as well as act as a proxy server. They are used to send out spam and steal personal data.
The Trojan-PSW.Win32.Fareit family came sixth. These malicious programs are designed to steal data, such as the credentials of FTP clients installed on the infected computer, login details for cloud storage, cookie files in browsers, email passwords. Fareit Trojans send the collected information to a malicious server. Some members of the family are able to download and run other malware.
The representatives of the Trojan-Downloader.JS.SLoad family in seventh are JS scripts that download and run other malware, mostly encryptors, on the victim computer.
Eighth place was taken by the Trojan.Java.Agent family. The malicious programs of this family are written in Java and have the JAR extension. These applications exploit vulnerabilities in Sun Java Runtime and can delete, block, modify or copy data, as well as download and run other malware.
Ninth place was occupied by Backdoor.Win32.Androm. This malware belongs to the family of Andromeda/Gamarue universal modular bots. Key features of these bots include the ability to download, store and run a malicious executable file, download and boot a malicious DLL (without saving it to disk), and update and delete itself. The bot functionality is extended with the help of plugins that can be uploaded by the intruders at any time.
Completing the Top 10 is the Worm.Win32.WBVB family. It includes executable files written in Visual Basic 6 (both in P-code and Native mode) that are not trusted by KSN.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, 2016
In 2016, Germany (14.13%) remained in first place, despite a decrease of 4.93 p.p. Second and third were occupied by countries from the Asia-Pacific region – Japan (7.59%) and China (7.32%) – that were both outside the Top 10 in 2015.
Russia (5.6%), which was third in the previous year’s rating, came fourth in 2016 after the proportion of email antivirus detections in the country decreased by 0.7 p.p. It was followed by Italy (5.44%), the UK (5.17%) and Brazil (4.99%), which also dropped out of the top three.
The US came eighth, accounting for 4.03% of email antivirus detections, 0.89 p.p. less than the previous year.
Austria (2.35%) rounded off the Top 10 with an increase of 0.93 p.p.
Phishing
In 2016, the Anti-Phishing system was triggered 154,957,897 times on the computers of Kaspersky Lab users. That is 6,562,451 more times than in 2015. Overall, 15.29% of our users were targeted by phishers.
Hot topics of the year
Phishers, predictably, could not pass up the most high-profile event of the year – the Olympic Games in Brazil. The scammers targeted both the organizers of the Olympic Games and ordinary netizens who received fake notifications of lottery wins, allegedly organized by the Brazilian government and the Olympic Committee.
The US presidential elections were also seen as a good media event for phishers. This theme was exploited to mislead internet users not only in the US but also in other countries.
Yet another interesting theme that became the subject of a dedicated study was holiday season sales. Scammers took advantage of the busy shopping period in the run-up to the festive season by creating fake websites of payment systems and online stores and luring potential victims by promising generous discounts.
A fake online store page
In addition, the holiday season itself often becomes an excellent cover for the fraudsters. For example, they may ask users to update their account information prior to the New Year.
Phishing page exploiting the New Year theme in the subdomain name
Methods of distributing phishing content
In 2016, cybercriminals used all possible means to reach users and make them pass on confidential information or money: social networks, pop-up ads, banners, text messages.
Among the most interesting methods were scams involving services for buying and selling used items. Cybercriminals collected phone numbers from ads placed on these services and then sent text messages to the numbers offering something in exchange at an extra cost. The message contained a link allegedly leading to a photo of the item on offer, but which actually led the victim to a phishing page.
Fraudsters often exploit social networks, and it is not restricted to personal messages. In 2016, many Facebook users around the world, for instance, were prompted to install a malicious extension for their browser, when they were added to a post containing a phishing link that supposedly led to a provocative video.
In Europe, the most widespread malicious extension was ‘xic. graphics’. It was soon removed from an online store, but according to the available whois information, over 50 other domains were registered in the name of the owners of the domain that hosted the fake page. Those domains were probably used for similar purposes.
Phisher tricks: referrer cleaner services
In Q4 2016, scammers showed a tendency to use referrer cleaner services. The victim was sent an email on behalf of a well-known company containing a link whose parameters included the address of the victim.
After clicking the URL, the user is taken to a page that shows a 302 error and then redirects the user to the address of a referrer cleaner service, which in turn redirects them to the legitimate website of a bank.
http://nullrefer.com/?https://www.cartalis.it/cartalis/prepagata/index.jsp
This way the user does not know that they have received a phishing email, while the bank does not receive a phishing domain in its referrers. At the same time, the phishers get confirmation that the user clicked on the link, which means that in future they will be able to send them more phishing emails, for example, in order to steal credit card data. In this way, the attackers ‘cleanse’ their databases of unused email addresses and vigilant recipients. They also detect clients of the bank whose name was used in the emails, allowing them to make their mass mailings more targeted.
The geography of attacks
Top 10 countries by percentage of attacked users
Brazil had the highest proportion of users subjected to phishing attacks (27.61%), a 5.98 p.p. increase on the previous year.
The percentage of users on whose computers the Anti-Phishing system was triggered out of the total number of Kaspersky Lab users in the country, 2016
In Brazil, we see lots of attacks targeting users of banks and online stores, so it is not surprising that the country often leads in the rating of countries with the highest proportion of users subjected to phishing attacks.
Phishers often place fake pages on the servers of government bodies in Brazil. This is one of the methods used to prevent phishing URLs from ending up on denylists. It also enhances the credibility in the eyes of the victim. In 2016, we registered 1,043 such cases.
Fake page on the gov.br domain
Top 10 countries by percentage of attacked users
Country % Brazil 27.61 China 22.84 Australia 20.07 Japan 19.16 Algeria 17.82 Russia 17.16 United Kingdom 16.64 Canada 16.03 United Arab Emirates 15.54 Saudi Arabia 15.39 China was second in this rating (22.84%). It didn’t make the Top 10 in 2015, but added 5.87 p.p. to its share in 2016. Australia (20.07%), which was seventh last year, came third following an increase of 2.39 p.p. Apart from Saudi Arabia (+ 4.9 p.p.), the shares of the other Top 10 countries barely changed.
The distribution of attacks by country
Russia (16.12%, +1.68 p.p.) topped the rating of countries where the Anti-Phishing system was trigged most often (out of the total number of the Anti-Phishing system detections around the world in 2016)
Distribution of Anti-Phishing system component detections by country, 2016
As in 2015, Brazil (8.77%) came second behind Russia, although its growth was negligible. The US added 0.5 p.p. (8.01%), which was enough to push India (6.01%) down to fourth. The top five also included China (7.86%).
Organizations under attack
The statistics on organizations used in phishing attacks are based on the triggering of the heuristic component in the Anti-Phishing system. The heuristic component is triggered when a user tries to follow a link to a phishing page and there is no information about the page in Kaspersky Lab’s databases.
Organizations under attack by category
In the second half of 2016, the proportion of phishing attacks targeting customers of financial institutions increased significantly (44.16% in the first quarter vs 48.14% in Q4). We have been following this growth over the last few years: in 2014, the average figure for the year was 28.74%; in 2015, it was 34.33%; and it was 47.47% in 2016.
In 2016, we saw significant growth in the proportion of phishing attacks on organizations belonging to the ‘Banks’ category (25.76%, + 8.31 p.p.). Of particular note was the increase in the percentage of targeted organizations in the ‘Online stores’ (10.17%, +1.09 p.p.) and ‘Payment systems’ (11.55%, +3.75 p.p.) categories.
Distribution of organizations subject to phishing attacks by category, 2016
At the same time, the share of the main categories decreased. For instance, the ‘Global Internet portals’ category (24.10%) lost 7.77 p.p. while the share of ‘Social networking sites’ (10.91%) fell by 5.49 p.p.
Overall, the priorities of the phishing scammers have not changed over the years. Attacks primarily exploit the names of popular brands, whose clients are numerous and likely to bring maximum financial profit.
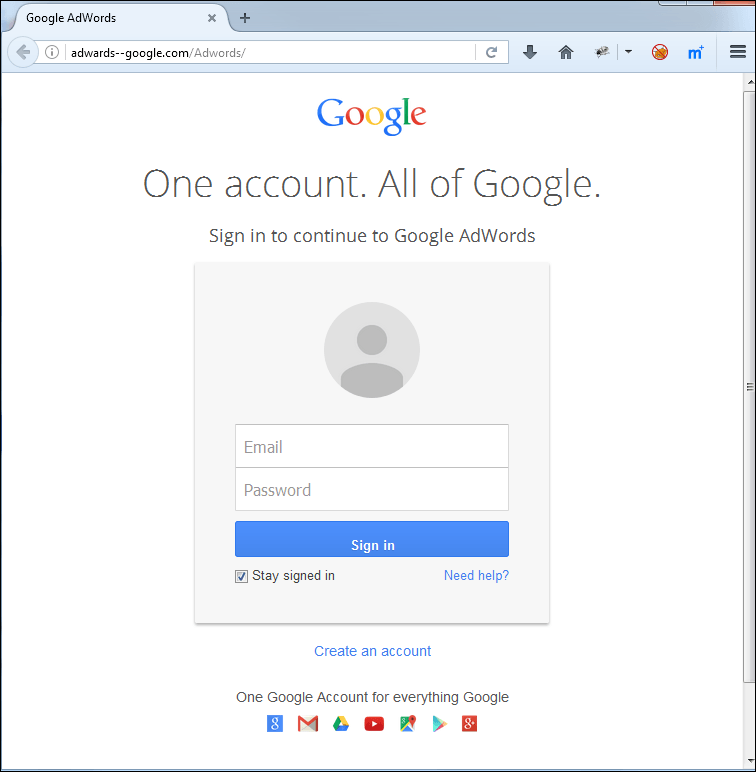
Another priority is attacks that could lead to the acquisition of confidential information and, subsequently, money. For example, some portals from the ‘Global Internet portals’ category (Google, Yahoo!, Microsoft (live.com), etc.) use the same account to access multiple services. A successful phishing campaign can therefore give fraudsters access to several of the victim’s accounts.
Phishing page to attack Google users
Top 3 attacked organizations
Organization % of detected phishing links Yahoo! 7.84 Facebook 7.13 Microsoft Corporation 6.98 Yahoo! (7.84%) again topped the ranking of organizations used by fraudsters to mask their attacks, although the proportion of Anti-Phishing system detections of fake pages mentioning this brand declined considerably in 2016 – by 6.86 p.p. (vs 10 p.p. in 2015). It is clear that the company is actively fighting phishing attacks, for example, by registering obfuscated domains in its own name (yshoogames.com, ypyahoo.com.cn, yhoonews.com, yhoooo.com, yayoo.com, yahou.com). However, phishers often place their content on legitimate sites (without the owners being aware of it) rather than create phishing domains.
Example of a web page using the Yahoo! brand
Second in popularity with the fraudsters was Facebook (7.13%). Over the year its share decreased by 2.38 p.p.
In 2016, we came across both classic phishing pages imitating the Facebook login page and various pages designed to steal data. One popular way of luring a victim is to promise them access to age-restricted content after entering their username and password, i.e., logging in to the system.
To increase the chances of hitting their target, mass phishing campaigns use the names of the most popular brands. Since these brands are often international, the attacks target users around the world. Naturally, phishing messages are written in many languages. One phisher trick was described in our report Spam and phishing in Q3 2016. By using information about the IP address of a potential victim, phishers determine the country in which they are located. Cybercriminals will then display pages in the language of the country that is identified.
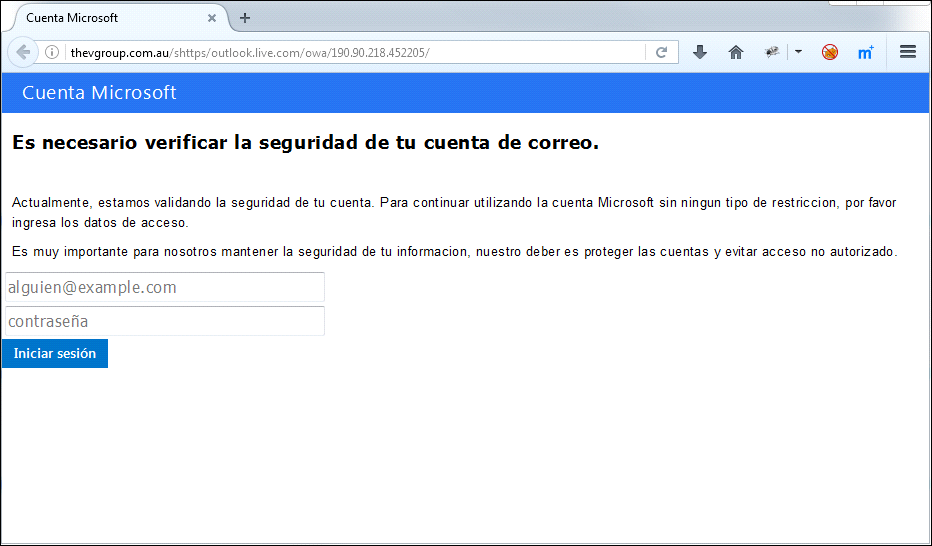
Third place in our Top 3 was occupied by Microsoft (6.98%). Using this brand to hide their attacks, fraudsters often try to steal data from user accounts on the live.com portal. They tend to use pages imitating the login page of the company’s email service.
There are also other schemes, such as simulation of account verification:
Conclusions and forecasts
2016 saw a variety of changes in spam flows, with the increase in the number of malicious mass mailings containing ransomware being the most significant. These programs are readily available on the black market, and in 2017 the volume of malicious spam is unlikely to fall.
Spam became very popular with small and medium businesses in China in 2016. One possible reason for this is the Great Firewall of China, which makes it difficult for Chinese businesses to use legal international platforms for advertising.
Of all the techniques used by spammers in 2016, the various ways of adding noise to text and links with the help of HTML capabilities are worth noting. This is nothing new, but spammers are constantly coming up with new types of obfuscation, and they will obviously continue to do so in the future.
The proportion of spam in email traffic was 58.31%, which is 3.03 p.p. higher than 2015. This was the first registered growth since 2009 – this was partially down to the surge in malicious spam.
For several years in a row, the number of fraudulent schemes targeting clients of financial institutions has been increasing, and we expect this trend to continue. The attacks are becoming more versatile: the fraudulent pages adapt to the user and display information in the local language as well as other relevant data.
The methods for distributing fraudulent pages have gone far beyond the scope of email. Cybercriminals are using all available means to contact potential victims: text messages, advertising or social networks. The latter are not only a good channel of communication but also a useful resource helping intruders gather information to carry out a more effective attack on users.











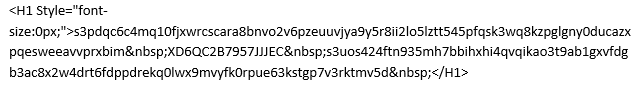















































Spam and phishing in 2016