Q3 in figures
- According to KSN data, Kaspersky Lab products detected and neutralized a total of 978 628 817 threats in the third quarter of 2013
- Kaspersky Lab solutions detected 500 284 715 attacks launched from online resources located all over the world
- Kaspersky Lab antivirus programs successfully blocked a total of 476 856 965 attempts to locally infect user computers connected to the Kaspersky Security Network
- 45.2% of web attacks neutralized by Kaspersky Lab products were performed using malicious web resources located in the USA and Russia.
Overview
Targeted Attacks / APT
NetTraveler’s new tricks
Kaspersky Lab researchers found a new attack vector used by NetTraveler, an advanced persistent threat that has already infected hundreds of high-profile victims in more than 40 countries. NetTraveler’s known targets include Tibetan/Uyghur activists, oil companies, scientific research centers and institutes, universities, private companies, governments and governmental institutions, embassies and military contractors.
Immediately after their operations were publicly exposed in June 2013, the attackers shut down all known NetTraveler command and control systems and moved them to new servers in China, Hong Kong and Taiwan from where the attacks continued unhindered.
In the last few days, several spear-phishing emails were sent to multiple Uyghur activists. The Java exploit used to distribute this new variant of the Red Star APT was only recently patched in June 2013 and has a much higher success rate. The earlier attacks used Office exploits (CVE-2012-0158) that were patched by Microsoft last April.
In addition to the use of spear-phishing emails, APT operators have adopted the watering hole technique (web redirections and drive-by downloads on rigged domains) to infect victims surfing the web.šKaspersky Lab intercepted and blocked a number of infection attempts from the “weststock[dot]org” domain, which is a known site linked to previous NetTraveler attacks. These redirections appear to come from other Uyghur-related websites that were compromised and infected by the NetTraveler attackers.
Icefog
Kaspersky Lab discovered “Icefog“, a small yet energetic APT group that focuses on targets in South Korea and Japan and hits supply chains for Western companies. The operation started in 2011 and has increased in size and scope over the last few years.š While most other APT campaigns infect victims for months or even years while attackers continuously steal data, Icefog operators process victims one by one – locating and copying only specific, targeted information. Once the desired information has been obtained, they leave. The attackers hijack sensitive documents and company plans, email account credentials, and passwords to access various resources inside and outside the victim’s network. In most cases, the Icefog operators appear to know very well what they need from the victims. They look for specific filenames, which are quickly identified and transferred to the C&C. Based on the profiles of identified targets, the attackers appear to have an interest in the following sectors: military, shipbuilding and maritime operations, computer and software development, research companies, telecom operators, satellite operators, mass media and television.
Kaspersky researchers have sinkholed 13 of the 70+ domains used by the attackers. This provided statistics on the number of victims worldwide. In addition, the Icefog command and control servers maintain encrypted logs of their victims together with details of various operations performed on them. These logs can sometimes help to identify the targets of the attacks and in some cases, the victims. In addition to Japan and South Korea, many sinkhole connections in other countries were observed, including Taiwan, Hong Kong, China, the USA, Australia, Canada, the UK, Italy, Germany, Austria, Singapore, Belarus and Malaysia. In total, Kaspersky Lab observed more than 4,000 unique infected IPs and several hundred victims (a few dozen Windows victims and more than 350 Mac OS X victims).
Based on the list of IPs used to monitor and control the infrastructure, Kaspersky Lab’s experts assume some of the players behind this threat operation are based in at least three countries: China, South Korea and Japan.
Kimsuky
In September Kaspersky Lab’s security research team published a report that analyzed an active cyber-espionage campaign primarily targeting South Korean think-tanks.
This campaign, named Kimsuky, is limited and highly targeted. According to technical analysis, the attackers were interested in 11 organizations based in South Korea and two entities in China including the Sejong Institute, the Korea Institute For Defense Analyses (KIDA), South Korea’s Ministry of Unification, Hyundai Merchant Marine and the Supporters of Korean Unification.
The earliest signs of Kimsuky’s activity date back to April 3, 2013, and the first Kimsuky Trojan samples appeared on May 5, 2013. This unsophisticated spy program includes several basic coding errors and handles communications to and from infected machines via a Bulgarian web-based free email server.
Although the initial delivery mechanism remains unknown, Kaspersky researchers believe the Kimsuky malware is most likely delivered via spear-phishing emails and has the ability to perform the following espionage functions: keystroke logging, directory listing collection, remote control access and HWP document theft (related to the South Korean word processing application from the Hancom Office bundle, extensively used by the local government). The attackers use a modified version of the TeamViewer remote access application to serve as a backdoor to hijack any files from the infected machines.
The Kimsuky malware contains a dedicated malicious program designed to steal HWP files, which suggests that these documents are one of the main objectives of the group.
Clues found by Kaspersky Lab’s experts make it possible to surmise that the attackers are North Korean. First of all, the profiles of the targets speak for themselves – South Korean universities conducting research on international affairs and producing defense policies for government, a national shipping company, and supporters of Korean unification.
Secondly – a compilation path string containing Korean words (for example, some of them could be translated as the English commands “attack” and “completion”).
Third – two email addresses to which bots send reports on status and transmit infected system information via attachments – iop110112@hotmail.com and rsh1213@hotmail.com – are registered with the following “kim” names: “kimsukyang” and “Kim asdfa”. Even though this registration data does not provide hard data about the attackers, the source IP addresses of the attackers fit the profile: there are 10 originating IP addresses, and all of them lie in the Jilin Province Network and Liaoning Province Network in China. The ISPs providing Internet access in these provinces are also believed to maintain lines into parts of North Korea.
Malware Stories
Author of Blackhole exploit kit arrested
The Blackhole developer known as Paunch and his alleged partners were arrested in Russia in early October. Blackhole has been arguably the most successful exploit kit of recent years. Blackhole is leased out to cybercriminals who want to spread malware via drive-by downloads, today’s prevailing attack vector. The criminals use the malicious links leading to compromised websites to infect users’ machines and the exploit kit selects working exploits, depending on the software versions of, for example Flash, Java or Adobe Reader installed on the victim machine.
This case of arrested cybercriminals is considered as one of the most significant in recent history, following the arrest of members of the Carberp gang in March and April this year. While in the case of Carberp the source code was publicly made available afterwards, it’s still unclear whether Blackhole will vanish, be taken over by others or be replaced by competitors in future.
New router botnet emerged
In September this year Heise reported a new botnet consisting of routers had been discovered. Routers are the backbone of every home user network, and infecting this affects every device connected to it – PCs, Macs, tablets, smartphones and even your smart-TV. The bot, named Linux/Flasher.A, extracts any login credentials transmitted from any device. The infection happens through a vulnerability in the webserver of routers running DD-WRT, a piece of open source router firmware. A malformed HTTP request leads to the execution of arbitrary code. The loot in the form of captured login credentials is then transferred to compromised web servers.
The exploited vulnerability used by Flasher.a dates back to 2009 and although it got fixed after it was found, more than 25,000 devices are still unsafe, according to Heise. This shows the great threat coming from routers: the firmware hardly ever gets updated by the users, making them easy targets when new vulnerabilities are found. For more information on router malware, Kaspersky Lab’s Marta Janus wrote an analysis of the first router malware seen in the wild – Psyb0t.
Web security and data breaches
Vodafone Germany breached
Vodafone Germany experienced a data breach in mid-September, in which two million customer data records got copied. Records contained not only names and addresses but also bank details. Vodafone assumes an inside job due to the traces and volume of breached data. A suspect was quickly identified, but a hacking group called Team_L4w confessed to the attack and claimed that one of their members used an infected USB thumb drive to infect the machine of a Vodafone employee.
Vodafone informed all affected customers via postal service. For transparency reasons, Vodafone created a web form, with which customers can check if their data is affected.
Apple Developer Area hacked
July saw Apple take down its Apple Developer portal for more than three weeks, after an intruder gained access to personal information of registered developers. The ‘who’ and ‘how’ of the hack still remains unclear, as there are several possible explanations. Shortly after the incident became public, an alleged security consultant released a video on YouTube confessing to the attack.
He claims to have copied more than 100,000 records from Apple’s databases, which he promised to delete, and used a cross-site scripting flaw on the Developer portal. The attacker then shared 19 records with the Guardian newspaper, which found that some addresses were invalid and the others appeared to be deserted. This shed doubts on the truth of the confession.
Interestingly, two days before Apple took the Developer portal offline, someone posted a message about a new vulnerability on the Apache forums. As well as explaining the details he also made a full working exploit publicly available. According to a Chinese website this led to large-scale attacks – Apple might just be one victim of many.
High Profile Domains Hijacked
At the beginning of October several high profile domains were defaced, including whatsapp.com, alexa.com, redtube.com and two prominent security companies. It seems that instead of compromising the actual webservers, the attackers, a group called KDMS, opted for hijacking the DNS or domain registrars. All compromised domains were sharing the same DNS registrar and had been recently updated at the time this case came to light. According to Softpedia, the ISP of the affected websites was attacked by sending fake password-reset requests via mail. After gaining control of the domain with new credentials, the attackers changed the entries and spread political statements.
Mobile malware
The third quarter of 2013 was a busy time in the battle against mobile malware, as a whole set of new tricks emerged.
New developments from malware writers
The past quarter was undoubtedly the quarter of mobile botnets. The cybercriminals behind the most widespread SMS Trojans are trying to add some interactivity to the way they manage their assets. This is why malware writers are now using Google Cloud Messaging (GCM) to manage their bots. The service enables them to send short messages in the JSON format to mobile devices, serving as an additional C&C for their Trojans.
Detecting this kind of interaction is a major challenge for security solutions. Commands received from GCM are handled by the system, which means they cannot simply be blocked on infected devices. The only way of preventing this channel from being used by malware writers to communicate to their malware is to block the GCM accounts of developers who use them to spread malware.
Not many mobile malicious programs can use GCM, but those that can are often very popular.
In mid-July 2013, we recorded the first third-party botnets, i.e., mobile devices infected with other malicious programs and used by other cybercriminals to distribute mobile malware.
This is how the most sophisticated Android Trojan, known as Obad, was distributed – using mobile devices infected with Trojan-SMS.AndroidOS.Opfake.a. Upon receiving a command from the C&C server, Opfake began sending text messages to all of the victim’s contacts, inviting them to download a new MMS message. If a user who received the text followed the link provided in the message, this resulted in Backdoor.AndroidOS.Obad.a being automatically downloaded onto the device.
As usual, mobile malware is mostly used to steal money from phone owners. A new malicious program appeared in Q3, which enables cybercriminals to steal money from victims’ bank accounts as well as their mobile phone accounts. In July, we detected Trojan-SMS.AndroidOS.Svpeng.a, which the malware writer can instruct to discover whether a mobile number is associated with online banking services from various Russian banks. The Trojan’s second modification included code implementing this functionality:
A phone associated with a mobile banking service usually allows its owner to top up any mobile phone account by sending a text message based on a certain template. This enables attackers to use the mobile banking service to transfer amounts accessible to their mobile numbers and subsequently convert them to cash, e.g., by transferring the money to accounts in an electronic payment system, such as QIWI Wallet.
Trojan-SMS.AndroidOS.Svpeng.a prevents the victim from communicating with the bank. Specifically, it intercepts messages and calls coming from the bank’s numbers. As a result, victims often remain unaware that money is being stolen from their bank accounts for long periods of time.
These Trojans can cost individual users thousands of dollars.
Exploiting various vulnerabilities in Android OS is gaining popularity. For example, Svpeng.a password-protected a non-existent archive with a non-existent password and intercepted the dialog to cancel its DEVICE ADMINISTRATOR privileges, resulting in users being unable to remove the application on their own.
DEVICE ADMINISTRATOR privileges are currently being used by other malicious programs as well, enabling them to work effectively for long periods of time on most versions of Android.
Master keys: Android vulnerabilities allow applications to evade integrity checks
The beginning of the third quarter saw the discoveries of two very unpleasant Android vulnerabilities, both of which are referred to as “Master Key” vulnerabilities. These vulnerabilities enable the components of an application to be modified, bypassing the cryptographic signature so that Android OS continues to treat them as completely legitimate regardless of the new, potentially malicious content.
These vulnerabilities have a lot in common. The first vulnerability was detected back in February by Bluebox Security Company and then presented in more detail by Jeff Forristal at BlackHat in Las Vegas. According to Bluebox the vulnerability is present in all versions of Android since 1.6 and thus could affect almost any device released in the past four years. Applications are single files with a .APK extension (Android Package). They are normally ZIP-files with all resources packed in the form of specially named files (the application’s own code is usually stored in classes.dex). As a rule, any attempt to change the content of an APK file is stopped during the installation of an application on Android OS. The ZIP format itself does not rule out duplicate file names, and in case of “duplicated” resources, Android appears to successfully check one file, but run the other.
Information about the second vulnerability was published by Chinese experts. The problem here is the simultaneous use of two methods of reading and unpacking APK-files and two different interpretations of Java and C. Like the first vulnerability it can use different APK files under identical names to tamper with the system. It should be noted that one prerequisite of a successful attack is the length of the original classes.dex file – it has to be no longer than 64 kilobytes, and this is not found in most Android applications.
For more information, read the related blog post by Stefano Ortolani here.
Statistics
In Q3 2013, the number of mobile malware samples continued to grow:

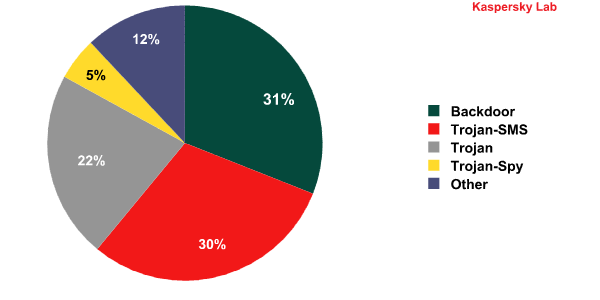
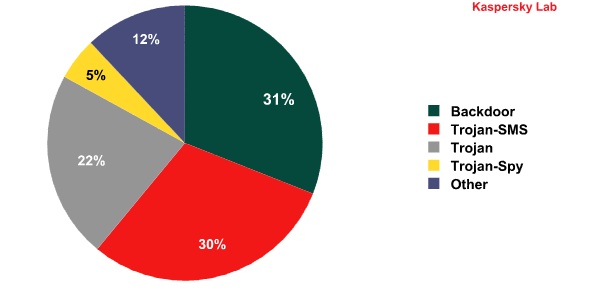
The distribution of mobile malware detected in Q3 2013 by type was similar to that in Q2:

The top position is still held by backdoors, although their share has fallen by 1.3 percentage points compared to Q2 2013. SMS Trojans (30%), which have gained 2.3 percentage points since the previous quarter, are in second place. As in Q2, they are followed by Trojans (22%) and Trojan-Spy malware, which accounts for 5% of the total. Together, backdoors and SMS Trojans make up 61% of all mobile malware detected during the third quarter – this is 4.5 percentage points more than in Q2.
It is common for a mobile malicious program to include several malicious components, which means backdoors often have SMS Trojan functionality and SMS Trojans may include sophisticated bot functionality.
TOP 20 mobile malicious programs
| Rank | Name | % of all attacks |
| 1 | DangerousObject.Multi.Generic | 29.15% |
| 2 | Trojan-SMS.AndroidOS.OpFake.bo | 17.63% |
| 3 | Trojan-SMS.AndroidOS.FakeInst.a | 8.40% |
| 4 | Trojan-SMS.AndroidOS.Agent.u | 5.49% |
| 5 | Trojan.AndroidOS.Plangton.a | 3.15% |
| 6 | Trojan-SMS.AndroidOS.Agent.cm | 3.92% |
| 7 | Trojan-SMS.AndroidOS.OpFake.a | 3.58% |
| 8 | Trojan-SMS.AndroidOS.Agent.ao | 1.90% |
| 9 | Trojan.AndroidOS.MTK.a | 1.00% |
| 10 | DangerousObject | 1.11% |
| 11 | Trojan-SMS.AndroidOS.Stealer.a | 0.94% |
| 12 | Trojan-SMS.AndroidOS.Agent.ay | 0.97% |
| 13 | Exploit.AndroidOS.Lotoor.g | 0.94% |
| 14 | Trojan-SMS.AndroidOS.Agent.a | 0.92% |
| 15 | Trojan-SMS.AndroidOS.FakeInst.ei | 0.73% |
| 16 | Trojan.AndroidOS.MTK.c | 0.60% |
| 17 | Trojan-SMS.AndroidOS.Agent.df | 0.68% |
| 18 | Trojan-SMS.AndroidOS.Agent.dd | 0.77% |
| 19 | Backdoor.AndroidOS.GinMaster.a | 0.80% |
| 20 | Trojan-Downloader.AOS.Boqx.a | 0.49% |
Twelve of the top 20 programs represent the Trojan-SMS class. This suggests that SMS Trojans are the most popular type of malware used by cybercriminals in attacks designed to make money from mobile devices.
The verdict DangerousObject.Multi.Generic ranks highest – this verdict means that we are aware of an application’s malicious character, but for one reason or another have not provided our users with signatures to detect it. In such cases, detection is available through cloud technologies implemented by the company in the Kaspersky Security Network, which enable our product to minimize the time it takes to respond to new and unknown threats.
The mobile malware samples in the next three positions are complicated applications used by malware writers to build mobile botnets.
Trojan-SMS.AndroidOS.OpFake.bo ranks second. This is one of the most sophisticated SMS Trojans. Its distinguishing features are a well-designed interface and the greed of its developers. When launched, it steals money from the mobile device’s owner – from $9 to the entire amount in the user’s account. There is also the risk of the user’s telephone number being discredited, since the Trojan can collect numbers from the contact list and send SMS messages to all of these numbers. The malware targets primarily Russian-speakers and users in CIS countries. Another malicious program from the same family and with similar functionality has made it into seventh place in the Top 20.
Third place is taken by Trojan-SMS.AndroidOS.FakeInst.a. Like OpFake, this malware has evolved during the past two years from a simple messaging Trojan to a fully functional bot controlled via various channels (including Google Cloud Messaging). The Trojan can steal money from a user’s account and send messages to numbers in the victim’s contact list.
Fourth place is occupied by Trojan-SMS.AndroidOS.Agent.u. This was the first Trojan to use a vulnerability in Android OS to gain DEVICE ADMIN privileges, thereby making its removal a very difficult task. In addition, it is capable of rejecting incoming calls and of making calls on its own. Possible damage: sending multiple SMS messages with costs totaling $9 or more.
Android accounted for 99.92% of all attacks on mobile platforms in Q3 2013. This comes as no surprise: the platform remains popular and open; in addition, even its latest versions support the installation of applications from unknown sources.
However, Google should get some credit – the system now does respond to some malicious applications:
This means that the developers of one of the most popular mobile operating systems have come to realize that Android is now the main target for mobile malware and are trying to provide at least some protection for the system’s users.
Statistics
All the statistics used in this report were obtained from the cloud-based Kaspersky Security Network (KSN). The statistics were collected from KSN users who consented to share their local data. Millions of users of Kaspersky Lab products in 213 countries take part in the global information exchange on malicious activity.
Online threats
The statistics in this section were derived from web antivirus components which protect users when malicious code attempts to download from infected websites. Infected websites might be created by malicious users, or they could also be made up of user-contributed content (such as forums) and legitimate resources that have been hacked.
Online threat detection
In the third quarter this year, Kaspersky Lab products detected 500 284 715 attacks launched from online resources around the world.
The Top 20 detectable online threats
| Rank | Name | % of all attacks** |
| 1 | Malicious URL | 89.16% |
| 2 | Trojan.Script.Generic | 3.57% |
| 3 | Adware.Win32.MegaSearch.am | 2.72% |
| 4 | Trojan-Downloader.JS.Psyme.apb | 1.19% |
| 5 | Trojan.Script.Iframer | 1.10% |
| 6 | Exploit.Script.Blocker | 0.37% |
| 7 | Trojan.Win32.Generic | 0.35% |
| 8 | Trojan-Downloader.Script.Generic | 0.28% |
| 9 | Trojan.JS.Iframe.aeq | 0.15% |
| 10 | Adware.Win32.Agent.aeph | 0.13% |
| 11 | Exploit.Java.Generic | 0.11% |
| 12 | Trojan-Downloader.Win32.MultiDL.k | 0.10% |
| 13 | Trojan-Downloader.Win32.Generic | 0.10% |
| 14 | Exploit.Script.Generic | 0.08% |
| 15 | Exploit.Script.Blocker.u | 0.06% |
| 16 | WebToolbar.Win32.MyWebSearch.rh | 0.06% |
| 17 | Packed.Multi.MultiPacked.gen | 0.06% |
| 18 | Trojan-SMS.J2ME.Agent.kn | 0.05% |
| 19 | Adware.Win32.Lyckriks.j | 0.05% |
| 20 | Exploit.JS.Agent.bnk | 0.04% |
*These statistics represent detection verdicts of the web-based antivirus module and were submitted by the users of Kaspersky Lab products who consented to share their local data.
**The percentage of unique incidents recorded by web-based antivirus on user computers.
This rating once again demonstrates that most antivirus detections occur at the URL level. 89.2% of all web-based antivirus detections were for denylisted malicious links (Malicious URL, 1st place).
Half of the Top-20 rating was made up of various verdicts assigned to malicious objects involved in drive-by attacks which are currently one of the most common methods used to penetrate user computers. These are both heuristic verdicts (Trojan.Script.Generic, Trojan.Script.Iframer, Exploit.Script.Blocker, Trojan-Downloader.Script.Generic, Exploit.Java.Generic, and Exploit.Script.Generic) and non-heuristic.
The non-heuristic verdicts in this rating include mostly advertising programs: their share rose by 2.4 percentage points from Q2, 2013.
An unexpected entry to the rating in Q3 was Trojan-SMS.J2ME.Agent.kn designed to target the Java Platform Micro Edition mobile platform. Representatives of this family have been out of the Top-20 since 2011. This mobile malware’s main function is to send out text messages to premium numbers. It is distributed via spam messages in ICQ which contain a link to Java applications as well as to themed sites from which the user is prompted to download applications. Once the user clicks the link, the field User-Agent is checked on the site side to identify the type of the operating system used by the visitor. If the User-Agent matches an Android-based web browser, a malicious Android application is downloaded. In all other cases, including use of a web browser on a standard PC, the malware owners preferred to use a J2ME app “by default”. It is when clicking such links that the web antivirus on computers produces the Trojan-SMS.J2ME.Agent.kn verdict.
Countries where online resources are seeded with malware
The following stats are based on the physical location of the online resources, which were used in attacks reported to the Kaspersky Security Network š(web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). The respective percentage share is based on the number of web-attacks reported to KSN. In order to determine the geographical source of web-based attacks, a method was used by which domain names are matched up against actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
81.5% of online resources used to spread malicious programs are located in 10 countries. This is 1.5 percentage points less than in Q2 2013.

The countries with the largest number of malicious hosting services changed just slightly from the second quarter of the year. The US (27.7%), Russia (18.5%), Germany (13.4%) and the Netherlands (11.6%) held on to their leading positions. In total, these four countries account for 70.15% of all malicious hosts. China and Vietnam dropped out of the Top 10 while newcomers Canada (1.3%) and the Virgin Islands (1.2%) took 8th and 9th places respectively.
Countries where users face the greatest risk of online infection
In order to assess the risk level for online infection faced by users in different countries, we calculated just how often users with Kaspersky Lab products encountered web-based antivirus detections over the course of the past three months.

* For the purposes of these calculations, we excluded countries where the number of Kaspersky Lab product users is relatively small (less than 10,000).
** The percentage of unique users in the country with computers running Kaspersky Lab products that blocked web-borne threats.
The list of countries in the rating remained unchanged from Q2 2013 except for the appearance of Germany in 12th place (35.78%) and Libya’s exit from the rating.
Noticeably, in Q3 2013 none of the individual country results exceeded 50%. For example, the figure for Russia (1st place in the rating) was 49.66%. šThis means that in Q3 2013 no countries qualified for the maximum risk group of countries where over 60% of users encountered an online threat at least once.š
All of the countries can be divided into three basic groups.
- High risk. The first eight countries from the Top 20 were in this group (two fewer than in Q2 2013) with percentages ranging from 41 up to 60%. They include Vietnam (43.45%) and countries from the FSU, specifically Russia (49.66%), Kazakhstan (49.22%), Armenia (49.06%), Azerbaijan (48.43%),š šTajikistan (45.40%), Belarus (40.36%) and Ukraine (40.11%).
- Moderate risk. This group includes countries where 21-40.99% of all users encountered at least one online threat, and included 76 countries in the third quarter of the year. These include Germany (35.78%), Poland (32.79%), Brazil (30.25%), the US (29.51%), Spain (28.87%), Qatar (28.82%), Italy (28.26%), France (27.91%), the UK (27.11%), the UAE (26.30%), Sweden (21.80%), the Netherlands (21.44%) and Argentina (21.40%).
- Low risk. In Q3 2013, this group included 62 countries with percentages ranging from 10 up to 21%.
The lowest numbers of web-based attacks were in Denmark (17.01%), Japan (17.87%), South Africa (18.69%), the Czech Republic (19.68%), Slovakia (19.97%), Finland (20.87%).
An average of 34.1% of computers connected to KSN were subjected to at least one attack while surfing the web during the past three months – a decrease of 1.1. percentage points compared to the second quarter of this year.
Local threats
This section contains an analysis of statistics based on data obtained from the on-access scanner and scanning statistics for different disks, including removable media.
Threats detected on user computers
In Q3 2013, Kaspersky Lab’s antivirus solutions successfully blocked 476 856š965 attempted local infections on user computers participating in the Kaspersky Security Network.
The Top 20 threats detected on user computers
| Rank | Name | % of individual users* |
| 1 | Trojan.Win32.Generic | 35.51% |
| 2 | DangerousObject.Multi.Generic | 32.43% |
| 3 | Trojan.Win32.AutoRun.gen | 13.56% |
| 4 | Adware.Win32.DelBar.a | 11.80% |
| 5 | Virus.Win32.Sality.gen | 9.52% |
| 6 | Adware.Win32.Bromngr.j | 7.81% |
| 7 | Exploit.Win32.CVE-2010-2568.gen | 7.56% |
| 8 | Adware.Win32.Bromngr.i | 6.60% |
| 9 | Adware.Win32.Agent.aeph | 6.55% |
| 10 | Worm.Win32.Debris.a | 6.24% |
| 11 | Trojan.Win32.Starter.lgb | 5.59% |
| 12 | Adware.Win32.WebCake.a | 5.06% |
| 13 | Expoit.Script.Generic | 4.31% |
| 14 | Trojan.WinLNK.Runner.ea | 4.17% |
| 15 | Adware.Win32.Bandoo.a | 4.00% |
| 16 | Virus.Win32.Generic | 3.71% |
| 17 | Virus.Win32.Nimnul.a | 3.67% |
| 18 | Trojan.Win32.Staser.fv | 3.53% |
| 19 | Trojan.Script.Generic | 3.52% |
| 20 | HiddenObject.Multi.Generic | 3.36% |
These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products that have consented to submit their statistical data.
* The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a malicious program was detected.
There still remains three clear leaders in this Top 20.
Trojan.Win32.Generic ranked first (35.51%) based on verdicts issued by the heuristic analyzer in the proactive detection of numerous malicious programs.
Malicious programs classified as DangerousObject.Multi.Generic, detected using cloud technologies, were ranked second with 32.43%. Cloud technologies work when there are still no signatures in the antivirus databases and no heuristics for detecting malicious programs, but when Kaspersky Lab’s cloud already has data about the threat. This is basically how the newest malicious programs are detected.
Trojan.Win32.AutoRun.gen (13.56%) came third, and includes malicious programs that use the autorun feature.
Countries where users face the highest risk of local infection
The figures below show the average rate of infection among user computers in different countries. KSN participants who provide Kaspersky Lab with information had at least one malicious file detected on nearly every third (31.9%) computer – either on their hard drive or a removable disk connected to the computer. That’s 2 percentage points more than last quarter.

* The percentage of unique users in the country with computers running Kaspersky Lab products that blocked web-borne threats.
** When calculating, we excluded countries where there are fewer than 10,000 Kaspersky Lab users.
For more than a year, the Top 20 positions in this category were held by countries in Africa, the Middle East, and South East Asia.
Local infection rates can also be broken down into four groups based on risk level:
- Maximum local infection rate (over 60%). Only one country – Vietnam – qualified for this category with 61.2%.
- High local infection rate (41-60%). A total of 29 countries in Q3 2013, including Nepal (55.61%), Bangladesh (54.75%), India (51.88%), Morocco (42.93%) and the Philippines (41.97%).
- Moderate local infection rate (21-40.99%). A total of 87 countries, including: the UAE (39.86%), Turkey (38.41%), Brazil (36.67%), China (36.07%), Mexico (34.09%), Germany (24.31%) and the UK (21.91%).
- Low local infection rate (under 21%). A total of 29 countries, including: the US (20.36%), Canada (19.18%), the Netherlands (18.39%), Sweden (16.8%), Japan (12.9%) and the Czech Republic (12.65%).
The Top 10 countries with the lowest risk of local infection were:
| Rank | Name | Country |
| 1 | Denmark | 11.93% |
| 2 | Czech Republic | 12.85% |
| 3 | Japan | 12.90% |
| 4 | Finland | 14.03% |
| 5 | Slovenia | 14.93% |
| 6 | Norway | 15.95% |
| 7 | Seychelles | 16.32% |
| 8 | Estonia | 16.46% |
| 9 | Slovakia | 16.72% |
| 10 | Sweden | 16.80% |
In Q3 2013, three new countries appeared in this Top 10 – Seychelles, Estonia and Slovakia, pushing out Ireland, the Netherlands and Martinique.
























IT Threat Evolution: Q3 2013