
The statistics presented here draw on detection verdicts returned by Kaspersky products and received from users who consented to providing statistical data.
Quarterly figures
According to Kaspersky Security Network, the third quarter saw:
- 1,189 797 detected malicious installers, of which
- 39,051 packages were related to mobile banking trojans;
- 6063 packages proved to be mobile ransomware trojans.
- A total of 16,440,264 attacks on mobile devices were blocked.
Quarterly highlights
In Q3 2020, Kaspersky mobile protective solutions blocked 16,440,264 attacks on mobile devices, an increase of 2.2 million on Q2 2020.

Number of attacks on mobile devices, Q1 2019 – Q3 2020 (download)
It is worth noting that in Q3 2020, the share of users attacked by malware increased, whereas the number of users who encountered adware and grayware decreased.
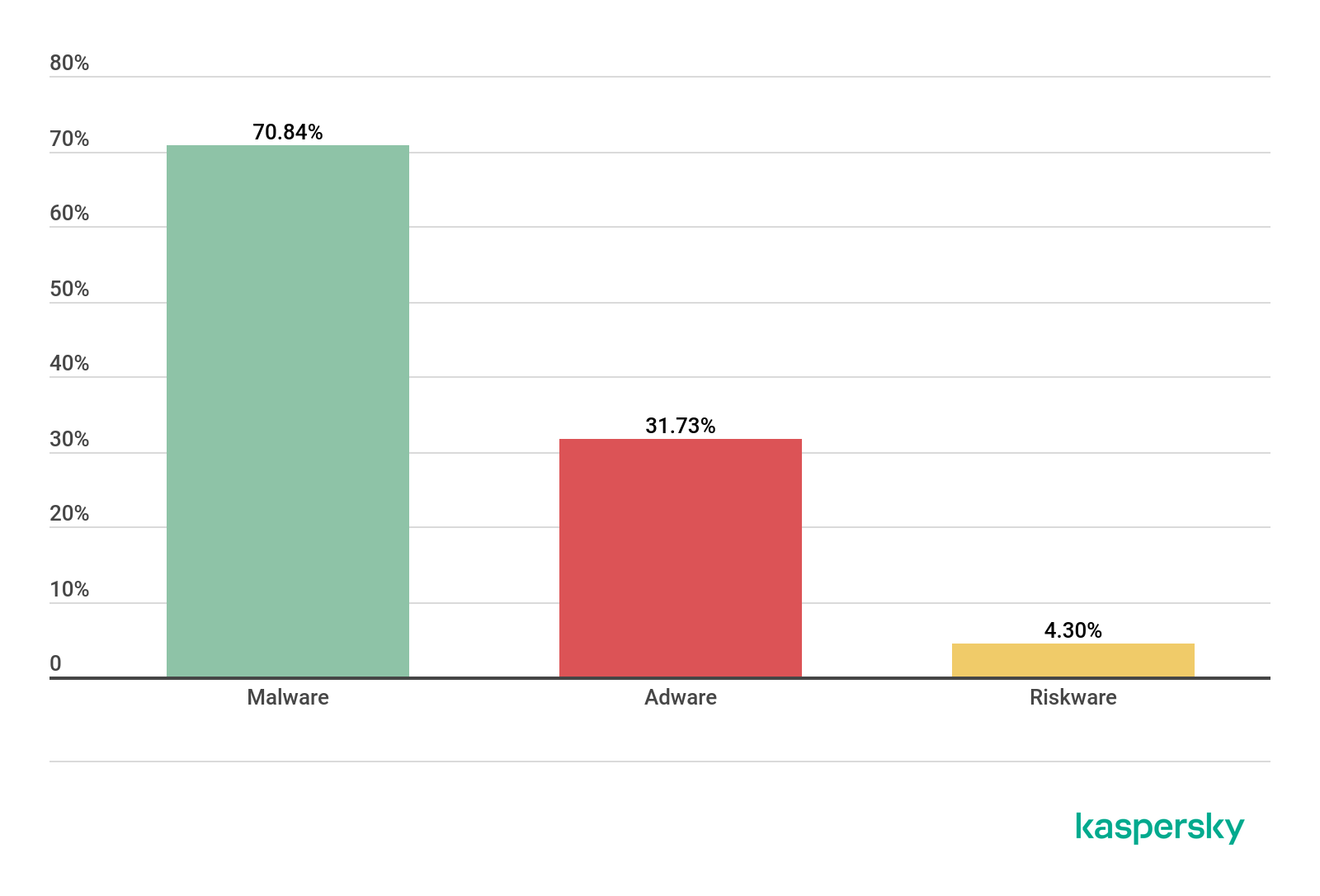
Proportions of users who encountered various threat classes in the total number of attacked users, Q3 2020 (download)
The third quarter reinforced the trend for the number of mobile users encountering stalkerware to drop.

Number of devices running Kaspersky Internet Security for Android on which stalkerware was detected in 2019 – 2020 (download)
Mobile threat statistics
In Q3 2020, Kaspersky solutions detected 1,189,797 malicious installation packages, 56,097 more than in the previous quarter.
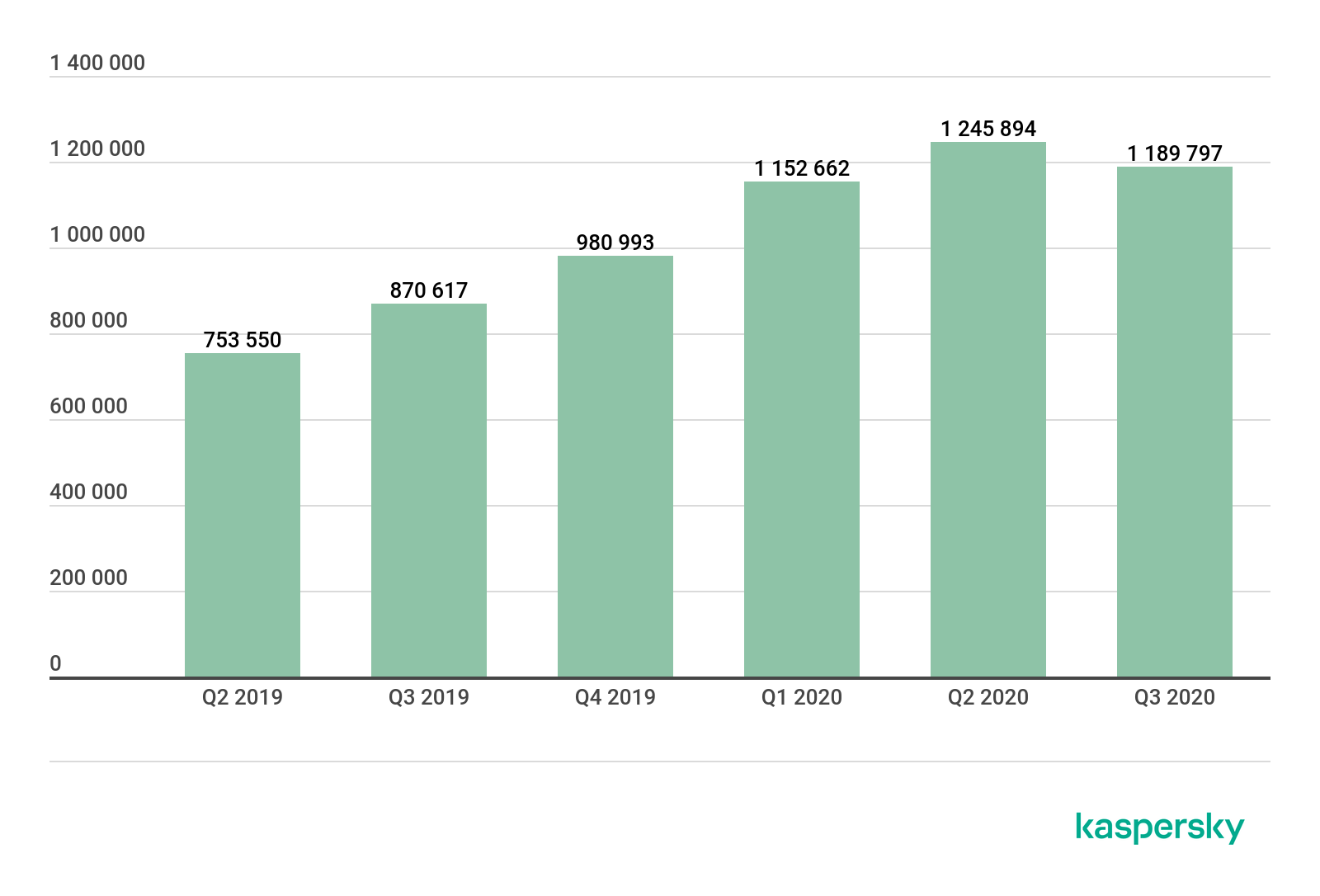
Number of detected malicious installers, Q2 2019 – Q3 2020 (download)
Distribution of detected mobile applications across types

Distribution of newly detected mobile applications across types, Q2 and Q3 2020 (download)
The Ewind adware family (48% of all adware detected) was most common in Q3, followed by the FakeAdBlocker family with 32% and HiddenAd with 6%.
The only class of threats that displayed significant growth in Q3 2020 was grayware, i.e. RiskTool (33.54%), with its share rising by more than 13 percentage points. The greatest contributor to this was the Robtes family with 45% of the total detected grayware programs. It was followed by Skymoby and SMSreg, with 15% and 13%, respectively.
The share of trojan-clickers rose by one percentage point in Q3 2020 on account of the Simpo family with its 96% share of all clickers detected.
Twenty most common mobile malware programs
Note that the malware rankings below exclude riskware or grayware, such as RiskTool or adware.
| Verdict | %* | |
| 1 | DangerousObject.Multi.Generic | 36.22 |
| 2 | Trojan.AndroidOS.Boogr.gsh | 8.26 |
| 3 | DangerousObject.AndroidOS.GenericML | 6.05 |
| 4 | Trojan-SMS.AndroidOS.Agent.ado | 5.89 |
| 5 | Trojan-Dropper.AndroidOS.Hqwar.cf | 5.15 |
| 6 | Trojan.AndroidOS.Hiddad.fi | 4.65 |
| 7 | Trojan.AndroidOS.Piom.agcb | 4.28 |
| 8 | Trojan-Downloader.AndroidOS.Necro.d | 4.10 |
| 9 | Trojan.AndroidOS.Agent.vz | 3.90 |
| 10 | Trojan-Downloader.AndroidOS.Helper.a | 3.42 |
| 11 | Trojan.AndroidOS.MobOk.v | 2.83 |
| 12 | Trojan-Downloader.AndroidOS.Agent.hy | 2.52 |
| 13 | Trojan-SMS.AndroidOS.Agent.adp | 2.20 |
| 14 | Trojan.AndroidOS.Hiddad.fw | 1.81 |
| 15 | Trojan-Downloader.AndroidOS.Agent.ic | 1.75 |
| 16 | Trojan.AndroidOS.Handda.san | 1.72 |
| 17 | Trojan-Dropper.AndroidOS.Hqwar.gen | 1.55 |
| 18 | Trojan.AndroidOS.LockScreen.ar | 1.48 |
| 19 | Trojan-Downloader.AndroidOS.Malota.a | 1.28 |
| 20 | Trojan-Dropper.AndroidOS.Agent.rb | 1.14 |
* Unique users attacked by this malware as a percentage of all users of Kaspersky solutions who were attacked.
As usual, first place in the Q3 rankings went to DangerousObject.Multi.Generic (36.22%), the verdict we use for malware detected with cloud technology. The technology is triggered when antivirus databases do not yet contain data for detecting the malware at hand, but the anti-malware company’s cloud already contains information about the object. This is essentially how the latest malicious programs are detected.
Second and third places went to Trojan.AndroidOS.Boogr.gsh (8.26%) and DangerousObject.AndroidOS.GenericML (6,05%), respectively. These two verdicts are assigned to files recognized as malicious by our systems Powered by machine learning.
Fourth and thirteenth places went to the Agent family of SMS trojans. Around 95% of users attacked by these trojans were located in Russia, which is unusual, as we have always found the popularity of SMS trojans as a threat class to be very low, especially in Russia. The names of the detected files often allude to games and popular applications.
Fifth and seventeenth places were taken by members of the Trojan-Dropper.AndroidOS.Hqwar family. This was the most numerous family in its class in Q3 2020, with 40% of the total detected droppers. It was followed by Agent (32%) and Wapnor (22%).
Sixth and fourteenth positions in the rankings were occupied by the Trojan.AndroidOS.Hiddad malware, which displays ad banners.
Interestingly enough, our rankings of mobile threats for Q3 2020 include five different families of the Trojan-Downloader class. Two malware varieties, Trojan-Downloader.AndroidOS.Necro.d (4.10%) and Trojan-Downloader.AndroidOS.Helper.a (3.42%) belong to one infection chain, so it is little wonder their shares are so close. Both trojans are associated with spreading of aggressive adware. Two others, Trojan-Downloader.AndroidOS.Agent.hy (2.52%) and Trojan-Downloader.AndroidOS.Agent.ic (1.75%), were discovered back in 2019 and are members of one family. The final trojan, Trojan-Downloader.AndroidOS.Malota.a (1.28%), has been known since 2019 and appears unremarkable. All of the listed trojans serve the main purpose of downloading and running executable code.
Eleventh position belongs to Trojan.AndroidOS.MobOk.v (2.83%), a member of the MobOk family. This malware can auto-subscribe the target to paid services. It attempted to attack mobile users in Russia more frequently than residents of other countries.
Trojan.AndroidOS.LockScreen.ar (1.48%), in eighteenth place, is worth a separate mention. This primitive device-locking trojan was first seen in 2017. We have since repeatedly detected it with mobile users, 95% of these in Russia. The early versions of the trojan displayed an insulting political message in a mixture of Russian and poor English. Entering “0800” unlocked the device, and the trojan could then be removed with stock Android tools. LockScreen.ar carried no other malicious functions besides locking the device. However, it was accompanied by two Windows executables.
Both files are malicious, detected as Trojan-Ransom.Win32.Petr.a and Trojan-Ransom.Win32.Wanna.b, the most infamous among Windows ransomware trojans. Neither poses any threat to Android, and LockScreen.ar does not use them in any way. In other words, a mobile device infected with LockScreen.ar cannot infect a Windows workstation, so the presence of these two executables has no rational explanation.
In recent versions of LockScreen, the cybercriminals changed the lock screen design.
The unlock code changed, too, to 775. The trojan’s capabilities were unchanged, and the Windows executables were removed from the package.
Geography of mobile threats

Map of infection attempts by mobile malware, Q3 2020 (download)
| Country* | %** | |
| 1 | Iran | 30.29 |
| 2 | Bangladesh | 17.18 |
| 3 | Algeria | 16.28 |
| 4 | Yemen | 14.40 |
| 5 | China | 14.01 |
| 6 | Nigeria | 13.31 |
| 7 | Saudi Arabia | 11.91 |
| 8 | Morocco | 11.12 |
| 9 | India | 11.02 |
| 10 | Kuwait | 10.45 |
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Share of unique users attacked in the country as a percentage of all users of Kaspersky Security for Mobile in the country.
The three countries where mobile threats were detected on Kaspersky users’ devices most frequently remained unchanged. Bangladesh and Algeria exchanged positions, with the former rising to second place with 17.18% and the latter dropping to third place with 16.28%. Iran retained its leadership even as it lost 12.33 percentage points: 30.29% of users in that country encountered mobile threats in Q3 2020.
The AdWare.AndroidOS.Notifyer adware was the most frequent one. Members of this family accounted for nearly ten of the most widespread threats in Iran.
Frequently encountered in Algeria was the Trojan-SMS.AndroidOS.Agent.adp trojan, which occupied third place in that country, as well as AdWare.AndroidOS.BrowserAd family malware (fourth place) and the Trojan-Spy.AndroidOS.SmsThief.oz spyware trojan (fifth place).
The most widespread adware in Bangladesh was the HiddenAd family which hides itself on the application list, and members of the AdWare.AndroidOS.Loead and AdWare.AndroidOS.BrowserAd families, which occupied fourth and fifth places, respectively, in that country.
Mobile web threats
The statistics presented here are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to providing statistical data.
In Q3 2020, we continued to assess the risks posed by web pages employed by hackers for attacking Kaspersky Security for Mobile users.
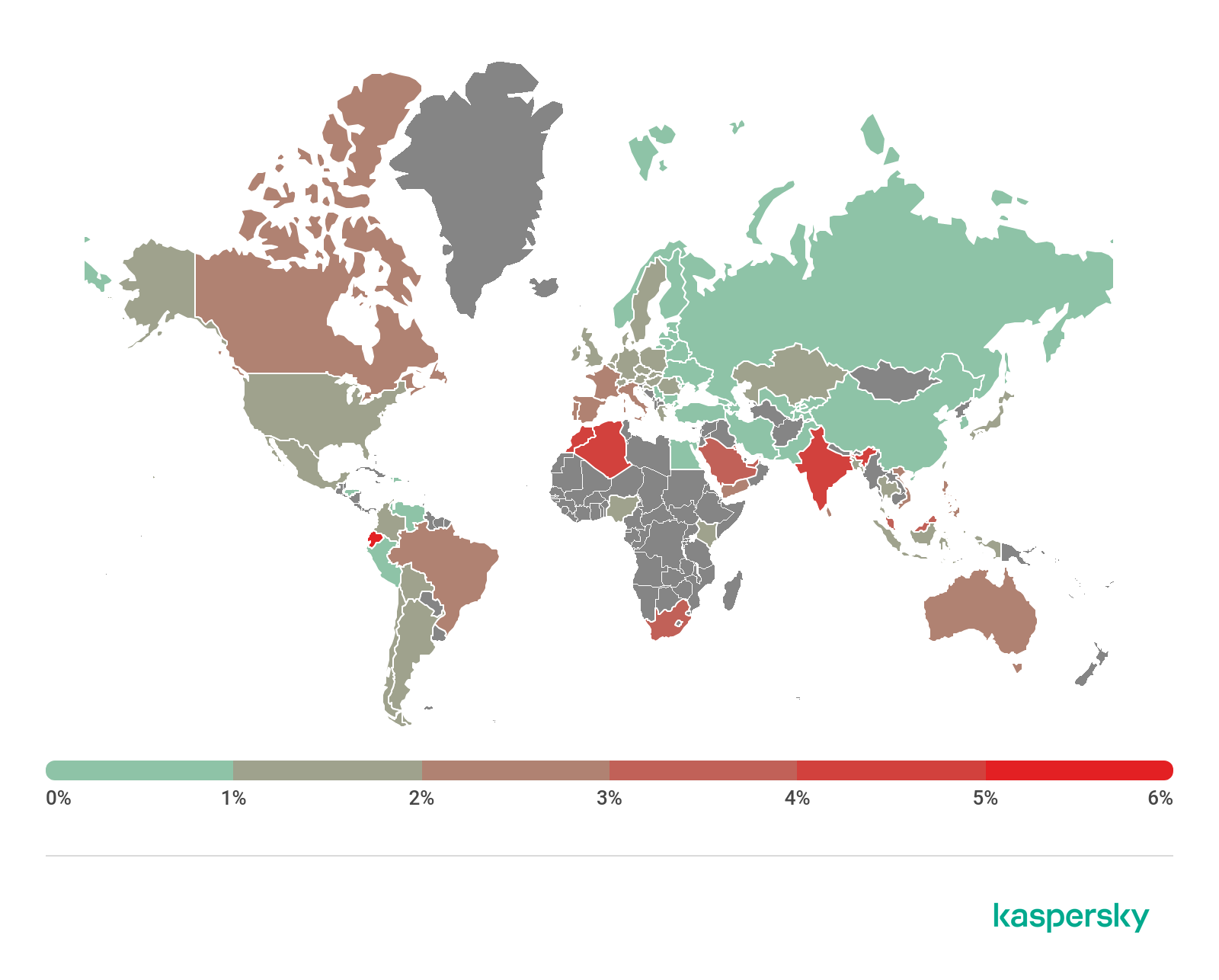
Geography of the countries with the highest risk of infection via web resources, Q3 2020 (download)
| Country* | % of attacked users** |
| Ecuador | 6.33 |
| Morocco | 4.51 |
| Algeria | 4.27 |
| India | 4.11 |
| Saudi Arabia | 3.78 |
| Singapore | 3.69 |
| Kuwait | 3.66 |
| Malaysia | 3.49 |
| South Africa | 3.31 |
| UAE | 3.12 |
* Excluded are countries with relatively few users of Kaspersky mobile products (under 10,000).
** Unique users targeted by all types of web attacks as a percentage of all unique users of Kaspersky mobile products in the country.
As in Q2 2020, residents of Ecuador (6.33%), Marocco (4.51%) and Algeria (4.27%) encountered various web-based threats most frequently during the reporting period.
Countries where mobile web threats originated

Geography of countries where mobile attacks originated, Q3 2020 (download)
| Country* | %* |
| Netherlands | 37.77 |
| Dominican Republic | 26.33 |
| USA | 24.56 |
| Germany | 4.60 |
| Singapore | 3.32 |
| Bulgaria | 0.88 |
| Ireland | 0.52 |
| Russia | 0.50 |
| Romania | 0.49 |
| Poland | 0.21 |
* Share of sources in the country out of the total number of sources.
As in Q2 2020, the Netherlands was the biggest source of mobile attacks with 37.77%. It was followed by the Dominican Republic (26.3%), which pushed the United States (24.56%) to third place.
Mobile banking trojans
During the reporting period, we found 39,051 mobile banking trojan installers, only 100 fewer than in Q2 2020.

Number of mobile banking trojan installers detected by Kaspersky, Q2 2019 – Q3 2020 (download)
Ten most commonly detected bankers
| Verdict | %* | |
| 1 | Agent | 71.27 |
| 2 | Rotexy | 9.23 |
| 3 | Wroba | 4.91 |
| 4 | Gustuff | 4.40 |
| 5 | Faketoken | 2.10 |
| 6 | Anubis | 1.79 |
| 7 | Knobot | 1.23 |
| 8 | Cebruser | 1.21 |
| 9 | Asacub | 0.82 |
| 10 | Hqwar | 0.67 |
* Unique users attacked by mobile bankers as a percentage of all Kaspersky Security for Mobile users who faced banking threats.
Speaking of specific samples of mobile bankers, Trojan-Banker.AndroidOS.Agent.eq (11.26%) rose to first place in Q3 2020. Last quarter’s leader, Trojan-Banker.AndroidOS.Svpeng.q (11.20%), came second, followed by Trojan-Banker.AndroidOS.Rotexy.e (10.68%).
Ten most common mobile bankers
| Verdict | %* | |
| 1 | Trojan-Banker.AndroidOS.Agent.eq | 11.26 |
| 2 | Trojan-Banker.AndroidOS.Svpeng.q | 11.20 |
| 3 | Trojan-Banker.AndroidOS.Rotexy.e | 10.68 |
| 4 | Trojan-Banker.AndroidOS.Asacub.ce | 6.82 |
| 5 | Trojan-Banker.AndroidOS.Asacub.snt | 6.60 |
| 6 | Trojan-Banker.AndroidOS.Anubis.n | 4.66 |
| 7 | Trojan-Banker.AndroidOS.Hqwar.t | 4.08 |
| 8 | Trojan-Banker.AndroidOS.Agent.ep | 3.67 |
| 9 | Trojan-Banker.AndroidOS.Knobot.h | 3.31 |
| 10 | Trojan-Banker.AndroidOS.Asacub.a | 3.04 |
* Unique users attacked by this malware as a percentage of all Kaspersky Security for Mobile users who encountered banking threats.
It is worth noting that the Agent.eq banker has a lot in common with the Asacub trojan whose varieties occupied three out of the ten positions in our rankings.

Geography of mobile banking threats, Q3 2020 (download)
| Country* | %** | |
| 1 | Japan | 1.89 |
| 2 | Taiwan Province, China | 0.48 |
| 3 | Turkey | 0.33 |
| 4 | Italy | 0.31 |
| 5 | Spain | 0.22 |
| 6 | Korea | 0.17 |
| 7 | Tajikistan | 0.16 |
| 8 | Russia | 0.12 |
| 9 | Australia | 0.10 |
| 10 | China | 0.09 |
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Unique users attacked by mobile banking trojans as a percentage of all Kaspersky Security for Mobile users in the country.
The geographical distribution of financial mobile threats underwent a significant change in Q3 2020. The largest share (1.89%) of detections were registered in Japan, with the prevalent malware variety, which attacked 99% of users, being Trojan-Banker.AndroidOS.Agent.eq. Taiwan (0.48%) presented the exact same situation.
Turkey, which was third with 0.33%, had a slightly different picture. The most frequently encountered malware varieties in that countries were Trojan-Banker.AndroidOS.Cebruser.pac (56.29%), followed by Trojan-Banker.AndroidOS.Anubis.q (7.75%) and Trojan-Banker.AndroidOS.Agent.ep (6.06%).
Mobile ransomware trojans
In Q3 2020, we detected 6063 installation packages of mobile ransomware trojans, a fifty-percent increase on Q2 2020.

Number of mobile ransomware installers detected by Kaspersky, Q2 2019 – Q3 2020 (download)
Judging by KSN statistics, the number of users who encountered mobile ransomware increased as well.
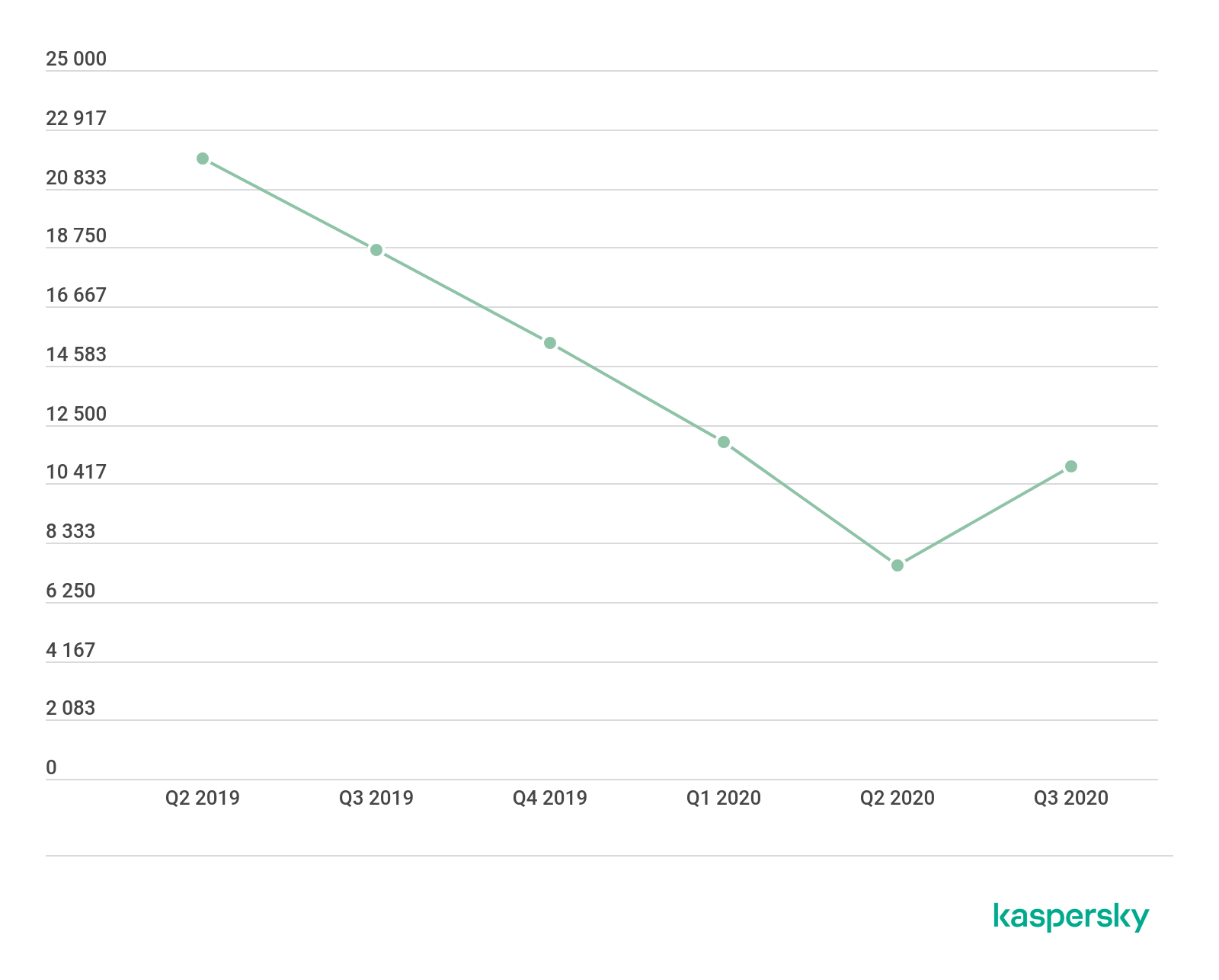
Number of users who encountered mobile ransomware, Q2 2019 – Q3 2020 (download)
| Verdict | %* | |
| 1 | Trojan-Ransom.AndroidOS.Small.as | 13.31 |
| 2 | Trojan-Ransom.AndroidOS.Small.o | 5.29 |
| 3 | Trojan-Ransom.AndroidOS.Piom.ly | 5.21 |
| 4 | Trojan-Ransom.AndroidOS.Agent.bq | 4.58 |
| 5 | Trojan-Ransom.AndroidOS.Rkor.z | 4.45 |
| 6 | Trojan-Ransom.AndroidOS.Congur.y | 3.80 |
| 7 | Trojan-Ransom.AndroidOS.Small.ce | 3.62 |
| 8 | Trojan-Ransom.AndroidOS.Congur.am | 2.84 |
| 9 | Trojan-Ransom.AndroidOS.Soobek.a | 2.79 |
| 10 | Trojan-Ransom.AndroidOS.Rkor.x | 2.72 |
* Unique users attacked by the malware as a percentage of all Kaspersky Mobile Antivirus users attacked by ransomware trojans.
Trojan-Ransom.AndroidOS.Small.as (13.31%) retained its leadership in Q3 2020. It was followed by Trojan-Ransom.AndroidOS.Small.o (5.29%), a member of the same family.

Geography of mobile ransomware trojans, Q3 2020 (download)
| Country* | %** | |
| 1 | Kazakhstan | 0.57 |
| 2 | Kyrgyzstan | 0.14 |
| 3 | China | 0.09 |
| 4 | Saudi Arabia | 0.08 |
| 5 | Yemen | 0.05 |
| 6 | USA | 0.05 |
| 7 | UAE | 0.03 |
| 8 | Indonesia | 0.03 |
| 9 | Kuwait | 0.03 |
| 10 | Algeria | 0.03 |
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Unique users attacked by ransomware trojans as a percentage of all Kaspersky Security for Mobile users in the country.
Kazakhstan (0.57%) Kyrgyzstan (0.14%) and China (0.10%) saw the largest shares of users attacked by mobile ransomware trojans.
Stalkerware
This section uses statistics collected by Kaspersky Internet Security for Android.
Stalkerware was encountered less frequently in Q3 2020 than in Q3 2019. The same can be said of the entire year 2020, though. This must be another effect of the COVID-19 pandemic: users started spending much more time at home due to the restrictions, and following their family members and housemates did not require stalkerware. Those who took an interest in their coworkers’ lives had a much harder time gaining physical access to their targets’ devices amid self-isolation. Besides, the cybersecurity industry, not without our contribution, zeroed in on stalkerware, with protective solutions starting to warn users explicitly.

Number of devices running Kaspersky Internet Security for Android on which stalkerware was detected in 2019 – 2020 (download)
- AndroidOS.CallRec.a
- AndroidOS.Dromon.a
- AndroidOS.Hovermon.a
- AndroidOS.InterceptaSpy.a
- AndroidOS.Manamon.a
- AndroidOS.Spydev.a
- AndroidOS.Tesmon.a
Ten most common stalkerware varieties
| Verdict | %* | |
| 1 | Monitor.AndroidOS.Cerberus.a | 13.38 |
| 2 | Monitor.AndroidOS.Anlost.a | 7.67 |
| 3 | Monitor.AndroidOS.MobileTracker.c | 6.85 |
| 4 | Monitor.AndroidOS.Agent.af | 5.59 |
| 5 | Monitor.AndroidOS.Nidb.a | 4.06 |
| 6 | Monitor.AndroidOS.PhoneSpy.b | 3.68 |
| 7 | Monitor.AndroidOS.Reptilic.a | 2.99 |
| 8 | Monitor.AndroidOS.SecretCam.a | 2.45 |
| 9 | Monitor.AndroidOS.Traca.a | 2.35 |
| 10 | Monitor.AndroidOS.Alltracker.a | 2.33 |
* Share of unique users whose mobile devices were found to contain stalkerware as a percentage of all Kaspersky Internet Security for Android users attacked by stalkerware
Cerberus (13.38%) has topped our stalkerware rankings for a second quarter in a row. The other nine contenders are well-known spyware programs that have been in the market for a long time.

Geography of stalkerware distribution, Q3 2020 (download)
| Country* | Number of users |
| Russia | 15.57% |
| Brazil | 12.04% |
| India | 9.90% |
| USA | 8.02% |
| Germany | 3.80% |
| Mexico | 3.17% |
| Italy | 2.50% |
| Iran | 2.36% |
| Saudi Arabia | 2.19% |
| Great Britain | 1.83% |
A decrease in the number of users who encountered stalkerware in Q3 2020 is typical both globally and for the three leaders.




















IT threat evolution Q3 2020 Mobile statistics