
Internet fraud has been around for just about as long as the Internet itself. Each year, cybercriminals come up with new techniques and tactics designed to fool their potential victims. This article will examine different types of fraud and what you can do to protect yourself against them.
There is one thing in particular that sets fraud apart from other Internet threats like viruses, Trojans, spyware, SMS blockers, spam, etc: the target of the cybercriminals is not a computer, whose security has to be circumvented, but a human who, as we all know, has his/her own weaknesses. That is why no program can ever provide users with 100% protection; the users themselves have to take a proactive stance in ensuring their own online security.
We have already addressed the technical aspects of fraud and typical fraud schemes employed by cybercriminals in a previous article. However, simply knowing how fraud and scams work isn’t always enough – this article offers some simple rules that can help users avoid many of the traps on the Internet.
Types of fraud
Phishing
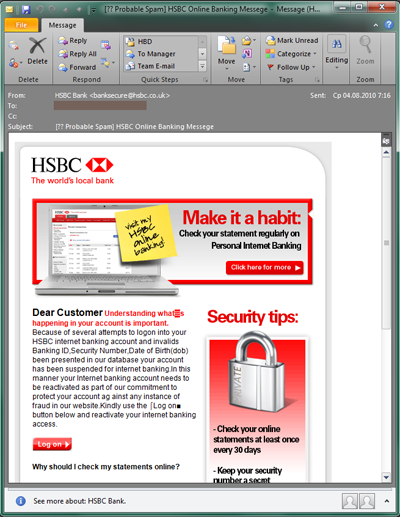
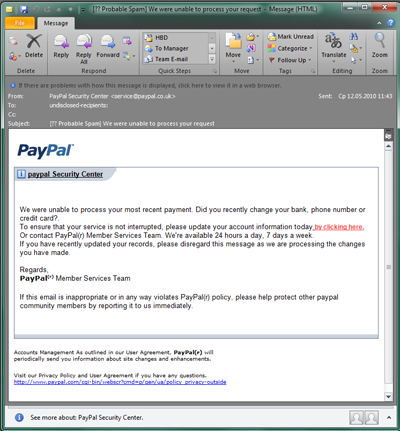
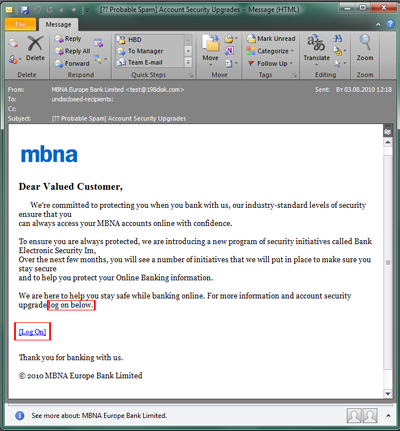
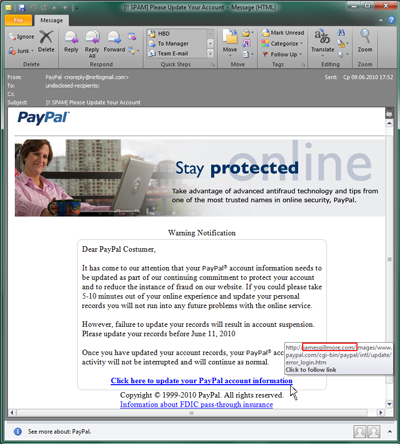
Phishing emails include fake notifications from banks, e-payment systems, and email providers, social networks, online games, etc. The aim of these emails is to obtain a user’s confidential data (username, password, etc.). Bank phishing is one of the most commonplace tactics aimed at gaining access to your online bank account, or your e-payment account details. Once a malicious user gets ahold of your login and password, he has access to your account.
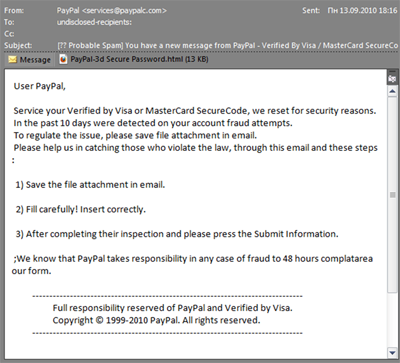
Phishers are skilled at creating authentic-looking emails which are disguised as official emails from various organizations. In particular, they use organizations’ official logos and copy the overall style of legitimate correspondence. As a rule, the email will suggest that the recipient click on a link in order to enter their personal information (usually the suggestion claims that recent measures were allegedly taken by the company’s administration to improve website security, and state that the user needs to log in again). When a user clicks on the link, he is taken to a fraudulent website that looks just like the official site where he can enter his username and password; the data is then sent to the cybercriminals. Quite often, these fraudulent sites contain exploits that install spyware on a victim computer. So even if you don’t enter your username or password and you just click on the link out of curiosity, you may still inadvertently download malware to your computer that could subsequently steal a range of personal data.
How to recognize a phishing email
Example 1. You receive an email from a bank, e-payment system, or email provider. If you do not use the services of said bank, e-payment system or email provider, then the email is definitely fraudulent — just delete it.
Example 2. You receive an email from a bank, e-payment system, or email provider where you do have an account. In this case, read the text carefully: if the email asks you to enter your login or password, then the email is fraudulent. Legitimate companies and organizations do not ask users to log in in this manner.
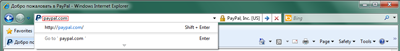
For example, an email from PayPal will have a link as follows: http://anything.paypal.com/anything
But links like those below and any other links that have something other than “paypal.com” directly before the backslash are fraudulent.
http://paypal.confirmation.com/anything,
http://anything.pay-pal.com/anything,
http://anything.paypal.com.anything.com/anything
Also beware of emails with attachments. These emails may not only be phishing emails designed to obtain your confidential data, but the attachment itself may be malicious.
Bear in mind that scammers aren’t only interested in your online bank account or e-payment account. They are interested in any personal information, which is why phishers also target email systems, social networking sites, online games, and really any system that requires a login and password.
Phishing: social networks
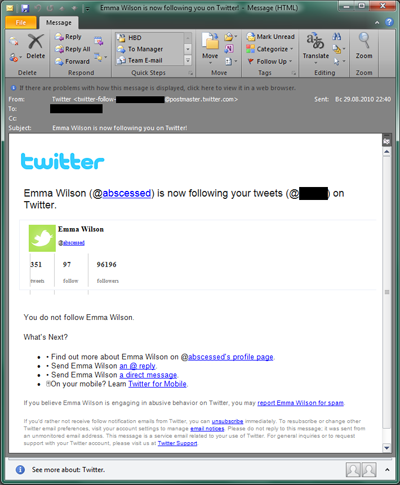
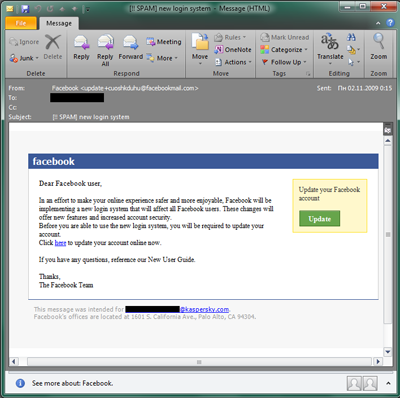
Do you have an account on Facebook, Twitter, Orkut, LinkedIn, or any other popular social network? If so, you already know what their official email notifications look like.
However — fake notifications can look almost exactly the same. These fake emails are designed to steal your personal data and gain access to your social network account. The scheme is much like the bank phishing schemes described above: you receive a notification allegedly sent from a social network claiming that someone left you a message or wants to add you as a friend, or that you need to update your account information. You click on a link, but instead of taking you to the official site, you are led to a fraudulent website that looks exactly like the real thing. Then you enter your login and password, which are sent to the scammers, before you are redirected to the official website.
Fake social network notifications may not ask you to enter your username or password and the email may look 100% genuine except for the links. Take a very close look at the actual address of the site that you are being led to.
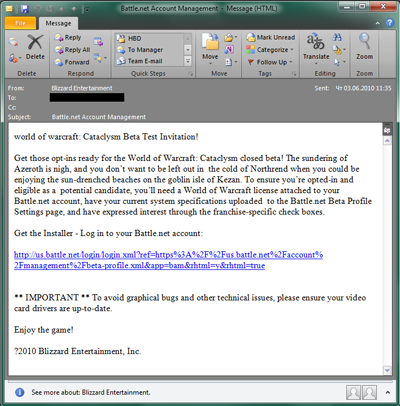
Phishing: online games
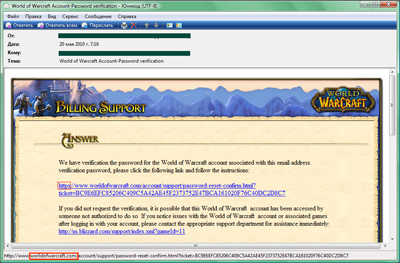
Even free online games frequently feature certain elements that users may pay money for: special gear, items, an original avatar etc. in addition to other additional bonuses. And where ever there is money, you are sure to find fraud not far behind. The scheme is pretty standard: trick users into visiting a bogus website. Just like with other types of phishing, the address of the fake site may be very similar to the official website’s address.
Only a very detail-oriented user will notice that the domain name of the suggested site contains the extra letter “I” in worlidofwarcraft.com. However, users who are familiar with phishing will immediately recognize the trap: real emails will never ask users to follow a link to enter their password!
In order to attract users’ attention, scammers sometimes come up with more clever tactics. You may be asked to be a beta-tester for a new game, or receive an offer for something free — just follow the link! However, if you do, you could fall into their trap and end up on a bogus website, where malicious users will attempt to steal your personal data. You could also end up on an infected site that will download all sorts of malware to your computer.
Other types of phishing
There are many different types of phishing — scammers create bogus emails for all kinds of Internet resources that require a username and password. Services like hosting, online magazines, etc. can all be targeted; cybercriminals generally look to copy a well known online resource that is trusted by users.
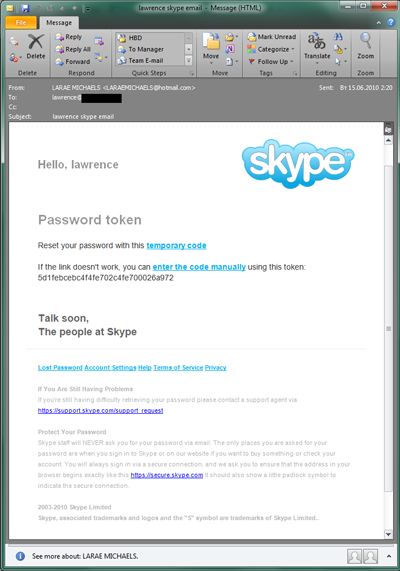
The email above is rather interesting: the scammers here are using boilerplate which is genuinely used by Skype, but obviously hope that recipients don’t read the fine print, which clearly reads: “Skype staff will NEVER ask you for your password via email.”
Other traditional types of fraud
The saying “knowledge is power” holds true for protecting yourself against online fraud. Sometimes all you really need to know are the different tactics that cybercriminals use in order to see when someone is trying to trick you. The most prevalent types of fraud are covered below.
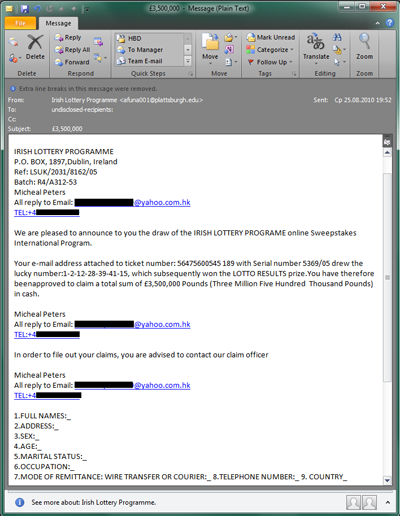
- Fake notifications about lottery winnings
(Learn more).These are emails that tell you that you have allegedly won the lottery. The scammer ultimately wants to trick you into getting some of your money by demanding payment in returned for winnings being “transferred”.
- 419 emails, or Nigerian scam emails (Learn more)
These are emails that ask you to transfer money to a remote country, more often than not one located in Africa, in return for the promise of high interest payments. Later, the scammers will ask for the number of your account allegedly in order to transfer your share of the money. However, instead of transferring money to your account, they actually withdraw funds from your account. There is also another variation of this scam where the scammers may ask you to send some funds, allegedly for the purpose of paying for legal services or transportation. After the money is sent, they simply cut off all contact with the victim, who is left waiting for the promised millions in cash.
There is still another, more dangerous variation in which the scammers use your account in such a way that you are the one who is actually guilty (under their guidance) of committing money laundering. These victims can actually end up in jail instead of the true criminals.
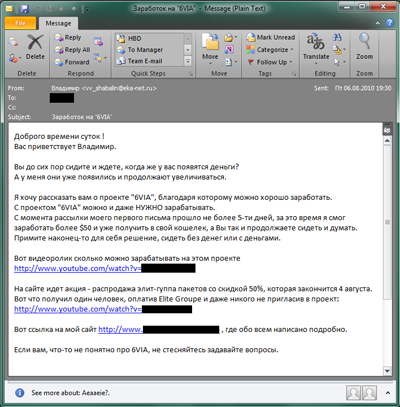
- Pyramid schemes and easy money
In these schemes, potential victims are asked to invest a small sum of money in order to receive high returns later on. But in fact, victims typically don’t receive anything at all.In this email, the recipient is urged to pay a fee to participate in an allegedly lucrative project
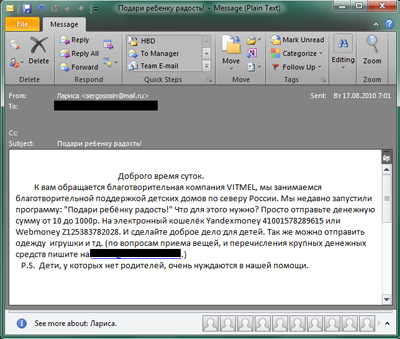
- Online panhandling
This type of fraud includes emails that are meant to look as though they come from charity organizations or the needy. In fact, these emails are often outright fabrications, or contain links to actual organizations and funds, but the payment details given ensure that funds transferred end up with the scammers.
In this email, the recipient is asked to donate money to help support orphanages in northern Russia via an e-payment system (two different e-payment system accounts are named). The scammers attempt to pull at the heartstrings of their potential victims by ending their message with: “P.S. Children without parents are in great need of our assistance.”
Always remember: charities do not send out spam — they have other methods for securing funds. If you still want to verify the information in a similar type of email, find the address of the organization that is named, called them directly, and find out how you can make a donation that way.
- Text message fraud using spam
This type of fraud involves emails that use various tactics to try to persuade users to send a text message to a short number. This type of scam also includes emails containing links to websites where users are asked to send a text message to a short number as payment for an alleged service. Whatever the conmen are promising, you will end up paying $10, or more, for nothing at all.
What should you do? Start by deleting the emails you get with special offers that involve money which are sent by people you don’t know, such as:
- offers to make easy money (get-rich-quick schemes, help transferring money, high-return investments)
- requests to help someone with a donation of money (for treatment, a poor Nigerian beauty, etc.);
- any “winnings”;
- offers for free software, movies, etc.
Recognizing the technical signs of fraud
There will, of course, be types of fraud that are not addressed in this article. Sometimes, we can recognize fraud based on not necessarily on the information contained in an email, but on how it’s written and laid out. That’s why we will also address some of the technical signs of fraud. Once you know them, you will have no problem recognizing legitimate emails from fraudulent emails.
The following signs indirectly confirm that an email originates with cybercriminals:
The “To:” field contains a name other than your own:
this means that this is a mass mailing where the “To” field is not real or is selected randomly.There is an unfamiliar address in the “From” field:
this means that the email did not come from the organization being impersonated. Bear in mind, that no major organization is going to be sending out emails from a free email client.Some of the words are CAPITALIZED:
this is one of the tactics spammers use in order to attract users’ attention.Some of the words are distorted (‘Lloan’ instead of ‘loan,’ or ‘Youwon’ instead of ‘You won’):
this is a spammer tactic used to get around anti-spam filters.The link does not match the address of the organization’s official site:
as described above, this is a sure sign that someone is trying to lure you onto a fraudulent website.An impersonal greeting (Dear Friend, Dear Customer, Dear Subscriber, Hello!):
this type of greeting means that the sender doesn’t know your name, and that the email is simply a mass mailing.A little about social engineering
As we all know, the weakest link in protection against any form of fraud, including Internet fraud, is the human factor. There are no technological methods that can protect us if we are careless. Let us take a closer look at the human weaknesses targeted most frequently by scammers.
Greed
Greed is one of the main aspects of human nature that conmen take advantage of.
Easy money, lottery winnings, or abusing e-payment or other systems — all of these scams are designed in the same way, on the principle of “give us a little money first, and you’ll get millions later.”
Of course, there is no “later.” Just bear that in mind and don’t let yourself get fooled.Fear
Cybercriminals also exploit another human weakness: fear. Messages such as: “Click on this link or your account will be blocked,” “if you don’t send a text message to this number 10 minutes after reading this email, your email account will be deleted,” and other similar threats are meant to play on fear and provoke users into doing certain things immediately, without thinking twice.
Always keep in mind that no provider will block your account in this manner. As we have already mentioned above, no provider will ever ask you to click on a link in an email to enter your personal data. As a rule of thumb, no legitimate service will try to rush you to do anything. Any emails that try to scare the recipient or convey a sense of urgency can be dismissed as fraudulent.
Naïveté / a desire to help / gullibility
Unfortunately, scammers also try to take advantage of our good nature.
Always remind yourself that any requests for assistance that come in the form of spam are fake. If you really want to make a contribution, there are dedicated channels which can be used for this purpose — and they never send out spam.
Curiosity
Remarkably, people sometimes send money to scammers out of curiosity. Even if we do not fully understand what is being said in the email, and we don’t really expect to get one hundred thousand million dollars, sometimes we just wonder what might happen if we click on that link — what’s that? How does it work? What will happen?
Want to know what happens? You will lose your money – that’s it!
Carelessness
Typically, the pace of life on the Internet is faster than our off-screen lives. Like Caesar, we often do seven things at once: work, check our mail, read the news, chat on IM, listen to music, etc. As a result, we become a bit scattered and inattentive — which could cause us to believe a fraudulent email is legitimate, even though a careful reading would immediately expose it as a scam.
Don’t rush to take action. First take the time to think, and read the email once more.
Security on the Internet: the rules
It is important to remember that in addition to fraud, there are many other types of threat — namely a wide range of malicious programs that are capable of stealing your passwords, usernames, credit card information, and other personal information — without any obvious scammer involvement, such as phishing emails.
Internet users should follow these simple rules to protect themselves:
- Use an antivirus program:
modern antivirus programs that are updated regularly will provide reliable protection against a number of different Internet threats.
- Download updates regularly:
program updates patch vulnerabilities that can be exploited by cybercriminals.
- Don’t leave your personal data on open resources:
the data you leave on the Internet is collected by robots that report back to cybercriminals, who may later use your data for their own purposes (for example, sending more spam to your email address).
- Do not download anything from unknown websites:
there is a high probability that whatever program, book, or movie you are downloading will be accompanied by malware.
- Do not click on any links in suspected spam emails:
these links often lead to fraudulent sites or sites infected with malicious programs.
- Do not open email attachments if you have any doubts at all about the sender:
there is a high probability that the attachment will contain a malicious program (even if it is a Word document).
- Do not attempt to “unsubscribe” from spam (especially if the spam email has an “unsubscribe” link):
this will not help you get rid of spam — instead, it could actually increase the volume of spam sent your way. There are two possibilities here: your address could be added to a database of people who really do want to read the emails and, correspondingly, in the future you will get more spam. Or, if you click on the alleged “unsubscribe” link, you may be taken to an infected site and end up with malware on your computer.
- Do not fall for any seemingly very attractive offers, particularly if they promise easy money:
these offers are really ploys, either to take your money, or to manipulate you into taking unlawful action for which you could be held criminally liable.
A few words in conclusion
Fraud will always exist. It can be found everywhere across the spaces of the Internet: in email, on social networks, and on various and sundry websites. Over the years, cybercriminals have invented new tactics, but the scams are ultimately the same. Only users themselves can guarantee their own protection in the virtual space. We hope that you find the advice and information in this article helpful.



















Internet fraud for dummies: practical advice for protecting yourself against online scams