
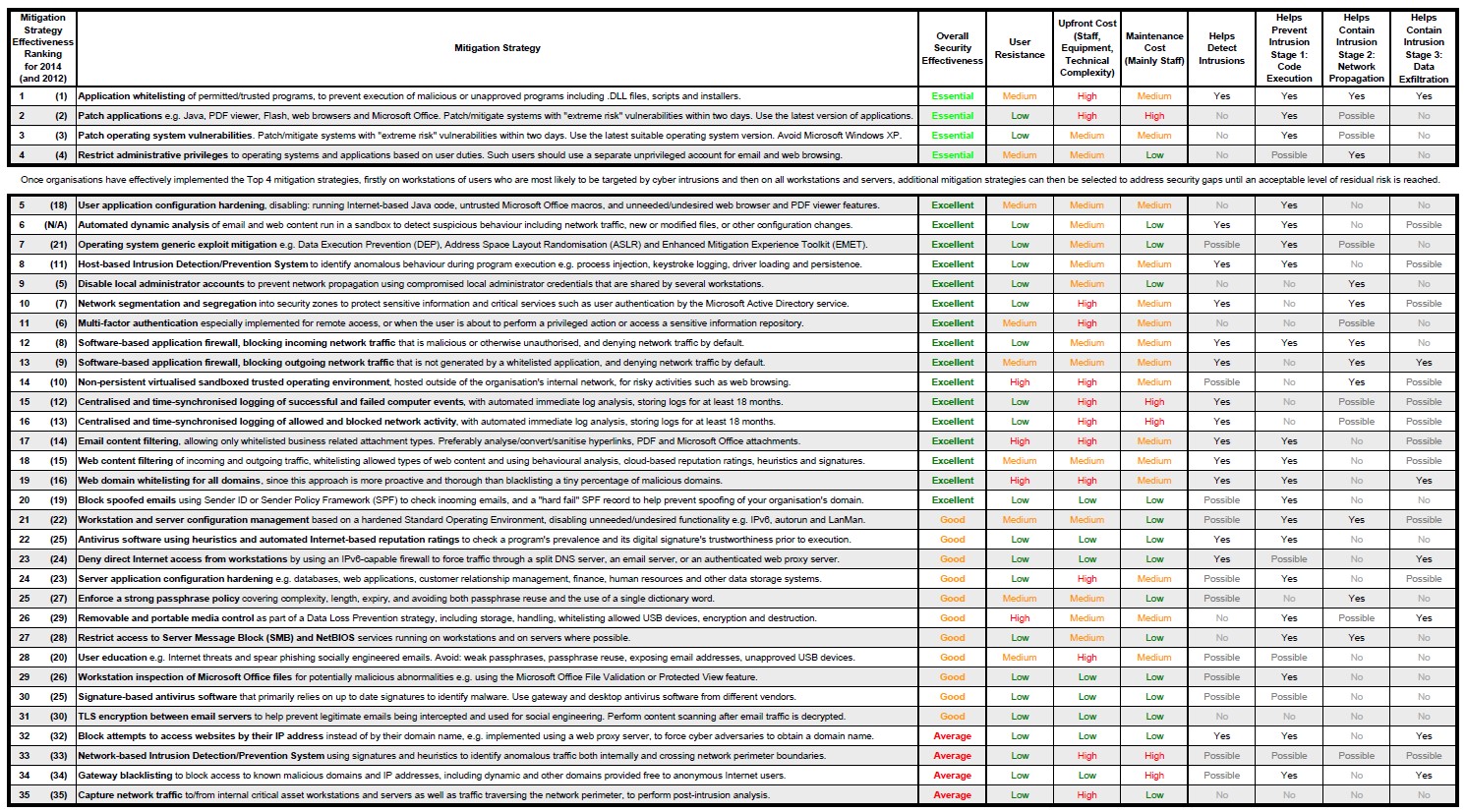
The Australian Signals Directorate Top35 list of mitigation strategies shows us that at least 85% of intrusions could have been mitigated by following the top four mitigation strategies together. These are: application allowlisting, updating applications, updating operating systems and restricting administrative privileges. Kaspersky Lab has technological solutions to cover the first three of these (i.e. all the technology-based strategies) as well as the most of the others from Top35 ASD’s list.
Many respected technology-focused organizations have already developed strategies for coping with targeted attacks. Gartner, for example, has issued guidelines for dealing with social engineering techniques, including keeping pace with an evolving threat landscape through ongoing information security education1. While no ICT infrastructure can ever be 100% secure, there are reasonable steps every organization can take to significantly reduce the risk of a cyber-intrusion.
Among all the available strategies, here at Kaspersky Lab we consider the Australian Signals Directorate (ASD) document to be the best publicly available guidelines from a government organization on how to successfully fight APTs. But we don’t just like this list of strategies; we also want to make sure that Kaspersky Lab technologies cover as many of them as possible. Please check the list below. Bear in mind, of course, that not all technologies have something in common with security software:
The Australia’s Signals Directorate’s full Mitigation Strategies list comprises 35 points.
This list of mitigation strategies can be roughly divided into four logical types, according to the implementation approach:
| Measures | Brief description |
| Administrative | Training, physical security |
| Networking | These measures are easier to implement at a network hardware level |
| System administration | The OS contains everything needed for implementation |
| Specialized security solutions | Specialized security software is applicable |
Through comprehensive, detailed analysis of local attacks and threats, ASD has found that at least 85 per cent of the targeted cyber-intrusions it responds to could be mitigated by four basic strategies. Three of them are related to specialized security solutions. Kaspersky Lab products include technological solutions to cover these first three major strategies:
- Use application allowlisting to help prevent malicious software and unapproved programs from running
- Patch applications such as Java, PDF viewers, Flash, web browsers and Microsoft Office
- Patch operating system vulnerabilities
- Restrict administrative privileges to operating systems and applications, based on user duties2.
In addition, over half of the ASD list could be implemented using our specialized information security solutions. Take a look at the strategies (those related to specialized security solutions) mapped to Kaspersky Lab technologies. We have highlighted the ones that ASD believes account for 85% mitigation:
| ASD rank | Mitigation strategy, short name | Kaspersky Lab technologies |
| 1 | Application allowlisting | Dynamic allowlisting |
| 2 | Patching application vulnerabilities | Vulnerability Assessment and Patch Management |
| 3 | Patching OS vulnerabilities | |
| 5 | User application configuration hardening | Web control (blocking scripts in web-browsers) , Web Anti-Virus |
| 6 | Automated dynamic analysis of email and web content | Mail Anti-Virus and Web Anti-Virus, Security for Mail Server, Security for Internet Gateway, DLP for Mail and Collaboration add-ons |
| 7 | OS generic exploit mitigation | Automatic Exploit Prevention |
| 8 | HIDS/HIPS | System Watcher and Application Privilege Control |
| 12 | Software-based application firewall for incoming traffic | Advanced Firewall |
| 13 | Software-based application firewall for outgoing traffic | Advanced Firewall |
| 15 | Computer event logging | Kaspersky Security Center |
| 16 | Network activity logging | Kaspersky Security Center |
| 17 | E-mail content filtering | Kaspersky Security for Mail Sever |
| 18 | Web content filtering | Web Control |
| 19 | Web domain allowlisting | Web Control |
| 20 | Block spoofed e-mails | Anti-Spam |
| 22 | AV software using heuristics and automated Internet-based reputation ratings | Anti-Malware |
| 26 | Removable and portable media control | Device Control |
| 29 | Workstation inspection of Microsoft Office files | Anti-Malware |
| 30 | Signature-based AV software | Anti-Malware |
ASD Strategies that can be implemented effectively using Kaspersky Lab’s product range.
For more detailed data about ASD strategies please consult the mitigation strategies document in the Securelist encyclopedia: part 1, part 2 and part 3. We hope that this information will be useful for system administrators, CIO/CISOs and researchers fighting targeted cyber intrusions.
1 Gartner: Best Practice for Mitigating Advanced Persistent Threats (document ID G00256438). >>>
2 Australian Signals Directorate, Strategies to Mitigate Targeted Cyber Intrusions >>>






















How to mitigate 85% of threats with only four strategies