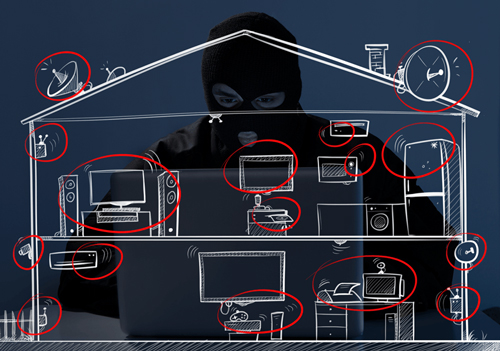
Our homes today look more like small offices. We have tons of different devices connected to our network, everything from storage devices and network equipment to wireless network printers. The entire “home entertainment” industry is getting connected: it is very difficult to buy a TV, DVD or Blu-ray player that’s does not have WIFI… the same thing goes for the gaming industry: all new gaming consoles require Internet connectivity.
I do love the fact that we are applying new technology to old concepts, and improving functionality. I personally even have my old retro computers connected to the Internet – and we are talking about old computers such as Commodore 64, Amiga 500 and Atari computers – because I love the fact of adding new functionality to old things.
And as we know, with great power comes great responsibility. But this is not something that the consumer product vendors are really adopting when adding extra functionality to their “old” products. I did some research where I looked into the devices that were connected to my own home network, and the result was extremely scary! Within minutes I was able to fully compromise some of my devices, turning them into zombie machines in botnets, bypassing all the security and accessing files on storage devices that I did not have the authority to access.
Many people still believe that these attacks are difficult, and require someone to sit on the same network as your devices, for example on your private WIFI connection, but this is false perception. There are very easy and effective ways to compromise the network of connected devices behind your personal firewall remotely over the Internet.
My colleague, Marta Janus, also did some very interesting research where she looked into the (in)security of home modems and routers, and we both came to the same conclusion. We need to act now! This is not a futuristic problem, this problem exists now. Cybercriminals are exploiting these weaknesses right now and the industry is not doing enough about this.
This is not only a technical problem that can be resolved with a patch. Consumers in general are very bad at understanding how these network connected devices should be installed. All of these devices have different usage, and because of that also require different network configurations. We are very lazy, and without proper installation instructions we simple connect the devices to our network; and when that is done, we consider the installation complete.
What is happening is that you are sharing the same network configuration among all devices. This results, for example, in having a TV, Blu-ray player and network storage device on the same network as the laptop you use to do online banking, home finances, online shopping and maybe even work.
The vendors also need to take more responsibility when shipping consumer products. Most people don’t understand that the support lifecycle of these devices is only about six months; after that there will be no more updates or support from the vendor, because they need to support the next upcoming products.
From talking to friends and family, it’s clear that they have a problem realizing that this is actually a threat! People still believe that it’s always “someone else” who will get infected with malicious code, or who will get their credit card details or identity stolen. Please wake up to the real world – this is happening right here, right now! Some really good examples of these types of attacks are:
- Customers to one of the largest ISPs in Sweden were sent vulnerable routers by the ISP, allowing attackers to remotely compromise the device though a “god-like” account with an very weak password; and all devices had the same account with the same password.
- A large amount of money was stolen from the customers of five popular Polish banks, following an attack in which cybercriminals changed the settings of hundreds of vulnerable SOHO routers in order to redirect users to the fake banking websites.
- Malware (Psyb0t) targeted home SOHO routers exploiting software weaknesses, but also weak passwords in the administrative interface – turning the device into a zombie in a botnet.
- Malware (BlackEnergy2) implemented additional modules, designed to run on Internet-of-Things devices, in order to perform DDoS (Distributed Denial of Service) attacks, steal passwords and sniff network traffic.
- Malware (Flasher) replaced the firmware on vulnerable SOHO devices with a modified system image that eavesdrops on users’ network activity.
As researchers it is very easy to identify security weaknesses and flame the vendors about them, but it is a bit more challenging to come up with an effective conclusion. Together with Marta, we compiled a little list of easy tips and tricks that you should apply if you have network connected devices. It’s only general tips because finding one solution that works on multiple devices is very complex; all products look and feel different and have different usages.
- Change default passwords on the device; attackers will try to exploit this!
- If possible try to update the firmware to the latest version!
- If you do not use the network connectivity on the device, TURN IT OFF! If you use it, or if it’s necessary for the device to work, make sure that there is NO REMOTE ACCESS to the management interface of the device from the outside world.
- Apply strong network segmentation for your connected devices
- Does the device require access to the INTERNET?
- Does the device, for example a TV, require access to the same network as your personal data?
- Switch off unnecessary features. Contemporary IoT devices usually implement a variety of different functionalities, some of which you might not even be aware of. It’s good practice, after buying each new device, to learn about all its features and disable the ones that you are not going to use. Having all the features enabled increases the potential attack surface.
- Read The Fascinating Manual. Every device is shipped with a manual, which documents its features and configuration settings. Also, there is usually a lot of additional documentation available online. To keep your home secure, you should always familiarize yourself with any new device that you are going to incorporate into your network and take all the recommended steps to make the device as secure as possible.
- Please contact the support team of the vendor if you do have questions. When buying consumer products, you also pay for support. Use it! They will offer guidance for your specific device!
Guidelines for securing your home



















Ed
Great Article, please send me more about a step by step list of how to secure my home more….
Thanks Again
ED
Darrell Pickett
I recieved my kindle fire hd in 2012. Jesus christ. Between now and then darn near two Billion people got hijacked electronically. We consumers must wake up. Protection of assets is critical. Thank you for your blogs. Today I subscribe.