
Out of all instant messaging clients out there, ICQ is probably the easiest to spam, because the accounts are based on relatively small integer numbers. From what we’ve seen, we suspect the bad guys have already created robots which randomly pick out ICQ numbers and send URLs to them.
That’s why we’ve started experimenting with an ICQ honeypot – a custom software which is monitoring about 10 ICQ accounts and logs all received messages into a database for later inspection. So far we’ve been receiving about 30 malware URLs per month, which most of the time point to HTML pages filled with exploits which download and install trojans.
Of these, an URL received last Friday caught my attention. When I first tried to fetch the page with WGET, it went like this:
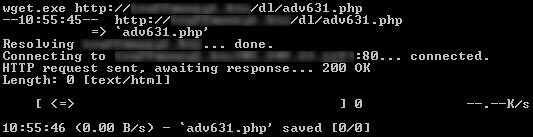
So, why would anybody spam a page which is 0 bytes long? Loading the page on a goat machine running IE and connected to the Internet brought a slighly different result: a trojan was downloaded in the system, installed, then it went out and fetched another trojan. Could it be that the guys behind that page check for the type of agent which comes to them and only send out the exploit for the “right” browser?
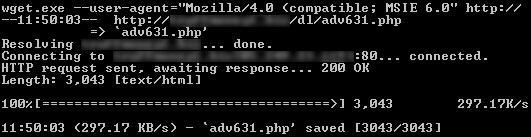
I wondered what would happen if we went to that page using WGET but faking an IE 6.0 user agent header? This time it works – we get a 3043 bytes page.
But what’s inside?
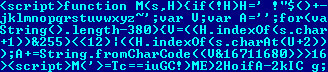
As you can see, it is a script, but it’s encrypted! Actually, it’s encrypted in such a way that if you change the script in any way it will not decrypt properly, so it takes some poking to find that inside it, there’s… another encrypted Javascript.
The script inside the encrypted script which you only see when you fetch page with IE goes to another page and loads (between other things) a Java Applet.
We decompiled the Java Applet to find that inside – you guessed it – there’s another applet, which gets loaded dynamically by the first applet. Which then loads a page which runs another javascript which goes to a website and fetches a Trojan Downloader. Which then fetches yet another trojan – which is encrypted in the already popular way, with FPU instructions. Interestingly, this last trojan changes on a daily basis – last week it was a keylogger, but this morning it became a banking trojan.
Welcome to the malware matrioshka.





















A malware matrioshka