
Yesterday I uploaded my first ever HD movie to YouTube. Once this was finished, I immediately got an email from YouTube saying “Congratulations on your first YouTube upload!” along with further hints and tips on getting the best out of it. Only a couple of hours later, I got another email, this time, saying “Hello, Have you tryed YouTube Toolbar?”
The typo in the subject line should be a good indication to anyone that this was most likely not from YouTube. Indeed, the message – which was rather poorly formatted – contained a link to a Backdoor.IRC.Zapchast variant.
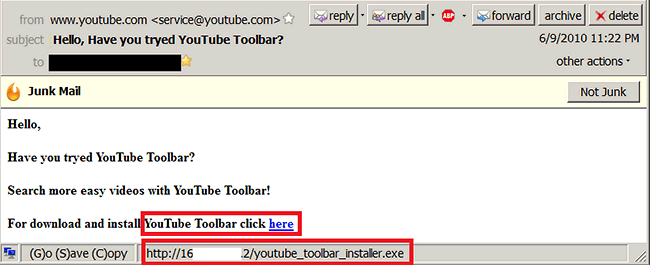
Backdoor.IRC.Zapchast.i spam email
The executable that the link in the email points to is a RAR SFX archive. It has a number of files inside:
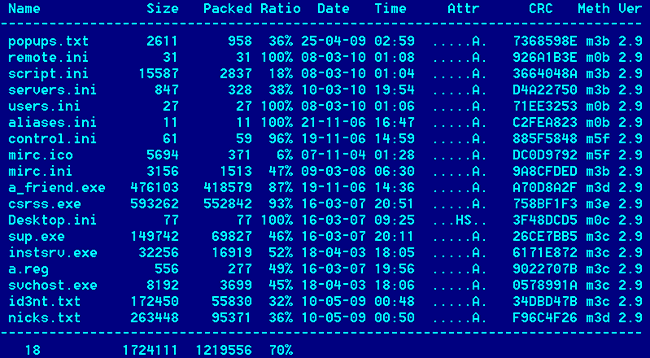
Almost all Zapchast variants look like this – with very minor differences. What about the origin of this backdoor? There are a number of clues in the files which seem to indicate these come from Romanian malware authors, from things such as Romanian specific passwords, to links to Romanian specific websites.
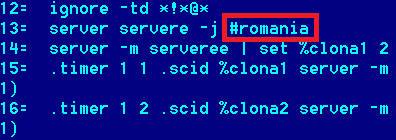
The way these Backdoors work is through mIRC scripts – they have a copy of the mIRC executable (version 6.01, packed with UPX) and the backdoor code itself is written as a mIRC script. The screenshot above shows the ’csrss.exe’ file. Once activated, they connect to the Undernet network and join a particular channel to receive commands, as well as notifying the owner of the botnet about a new infected user. The handling of the commands is implemented in the ‘script.ini’ file.
Aside from the handling of mIRC commands that it receives from its master, there is no further code designed to steal confidential data or financial information from the victim’s computer. This is rather uncommon nowadays and things such as Zapchast are slowly dying out, making way for the more advanced Trojans, like Zbot or Sinowal.






















YouTube Toolbars