
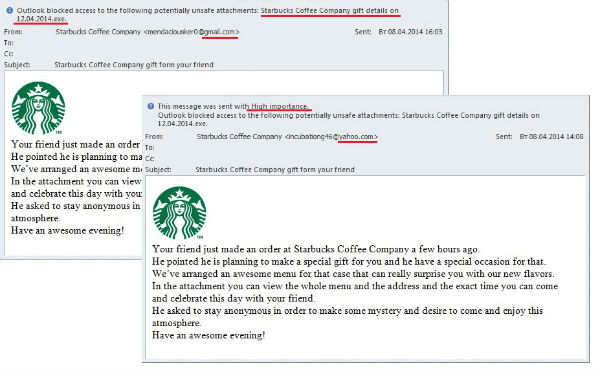
Cybercriminals often like to use a bogus letter to trick people into opening malicious attachments. There are two tricks that make this work: a message from a familiar name (a bank, social network, service provider or other organization that might interest the recipient) and an intriguing or alarming subject. An attack based on fake messages supposedly from coffee chain Starbucks combined the two.
The detected distribution claimed that a few hours ago a recipient’s friend made an order for him to celebrate a special occasion in a Starbucks coffee shop. That mysterious friend wished to remain anonymous, enjoying the intrigue he was creating, but was sending out invitations with details of a special menu, which is available in the attachment. In the end they wished the recipient an awesome evening.
All the messages were sent out with high importance. Besides, the addresses, created on the Gmail and Yahoo! free mail services, changed from letter to letter and seemed to be randomly generated combinations like incubationg46@, mendaciousker0@ and so on.
The attachment was a .exe file and the cybercriminals made no effort to mask it with an archive or double filename extension. They seemed to be sure a happy recipient would open the attachment without any suspicion. Kaspersky Lab detects the attached file as Rootkit.Win32.Zbot.sapu – a modification of one of the most notorious spyware family Zbot (ZeuS). These applications are used by cybercriminals to steal confidential information. This version of Zbot is able to install a rootkit Rootkit.Win32.Necurs or Rootkit.Win64.Necurs, which disrupts the functioning of antiviruses or other security solutions.
Would You Like Some Zeus With Your Coffee?





















corey
I like kaspersky
Sandra
As do I. This is our second two year subscription to the service. I have never owned a better computer Security service. They have always kept harm from reaching me. Hope they keep up the good work.