Why in Dubai? First, I was there recently. Second, Dubai has become one of the most important cities in the world for holding IT conferences.
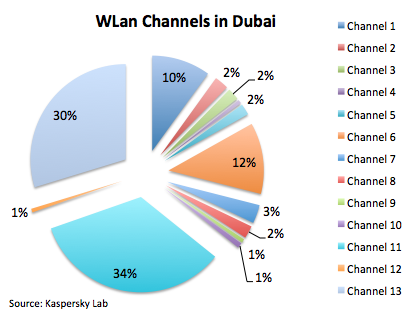
All statistics are based on around 3 thousand found WiFi access points. Let’s begin with the channels Dubai’s WiFi is running on:
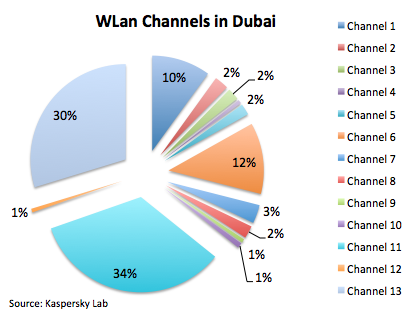
It’s logical to see that channel 6 and 11 are used widely; they’re often the channels used by default by access point vendors. The interesting thing is to see that channel 13 is the second most used channel in the city. Just FYI, the use of this channel is prohibited in the United States of America, but it’s allowed in most parts of the world. Channel 13 is being used in 802.11g/n networks, which shows that most of the access point in Dubai are new and probably use the 802.11n standard.
Since most of the hardware is modern it would be logical to conclude that the encryption in Dubai WiFi networks must be WPA2, right? But unfortunately this is not true.
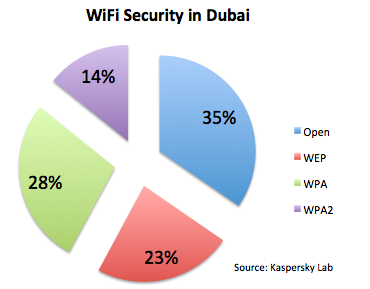
Indeed, WPA2 is the least-used encryption method. Most of the networks are open. Maybe in those networks some additional security filters are applied, like authorization by MAC address or via captive portals. However, such networks can’t be called secure and if a user doesn’t have their own VPN connection their data can be at risk.
Another interesting point is that many SSID names are hidden and not broadcast publicly.
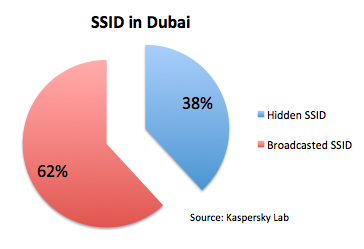
Maybe this is another reason why WiFi administrators in Dubai think their networks don’t need WPA2 encryption. If they think so, they are mistaken, since there are techniques which allow to hidden SSIDS to be revealed. And if we think about MAC filtering as a security concept, any MAC address can be sniffed and then spoofed. So it’s not a good security approach.
Finally if we look at the most popular vendors of access points in Dubai, we can highlight three of the biggest: Cisco, Linksys (which is also a subsidiary of Cisco) and Aruba networks share half of the market in Dubai:
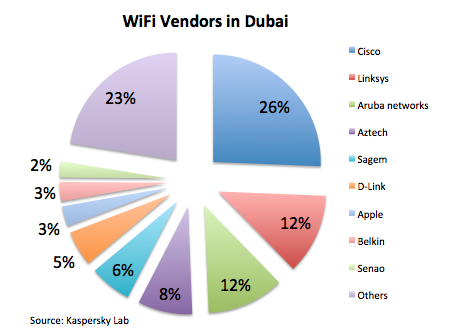
There are other players, but not as significant as the three mentioned above.
You may know that many VPN services are prohibited in Dubai. So if an attacker is able to open a non-protected WiFi network, it exposes users and their sensitive data.
As we have seen, the hardware used in access points allows better security management, but it looks like there is no a good practice or policy to enforce this. It exposes users’ sensitive data to many kind of network attacks.




















WiFi study in Dubai