Introduction
In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98% of the dropped drives were picked up by staff and students, and at least half were plugged into a computer in order to view the content. For a hacker trying to infect a computer network, those are pretty irresistible odds.
USB devices have been around for almost 20 years, offering an easy and convenient way to store and transfer digital files between computers that are not directly connected to each other or to the internet. This capability has been exploited by cyberthreat actors, most famously by the Stuxnet worm in 2010, which used USB devices to inject malware into the network of an Iranian nuclear facility.
Today, cloud services such as Dropbox have taken on much of the heavy lifting in terms of file storage and transfer, and there is greater awareness of the security risks associated with USB devices. Their use as an essential business tool is declining. Despite this, millions of USB devices are still produced and distributed annually, with many destined for use in homes, businesses and marketing promotion campaigns like trade show giveaways.
USB devices remain a target for cyberthreats. Kaspersky Lab data for 2017 shows that every 12 months or so, around one in four users worldwide is affected by a ‘local’ cyber incident. These are attacks detected directly on a user’s computer and include infections caused by removable media like USB devices.
This short report reviews the current cyberthreat landscape for removable media, particularly USBs, and provides advice and recommendations on protecting these little devices and the data they carry.
Methodology and key findings
The overview is based on detections by Kaspersky Lab’s file protection technologies in the drive root of user computers, with a specific scan filter and other measures applied. It covers malware-class attacks only and does not include detections of potentially dangerous or unwanted programs such as adware or risk tools (programs that are not inherently malicious, but are used to hide files or terminate applications, etc. that could be used with malicious intent). The detection data is shared voluntarily by users via Kaspersky Security Network (KSN).
Key findings
- USB devices and other removable media are being used to spread cryptocurrency mining software – and have been since at least 2015. Some victims were found to have been carrying the infection for years.
- The rate of detection for the most popular bitcoin miner, Trojan.Win64.Miner.all, is growing by around one-sixth year-on-year.
- One in 10 of all users hit by removable media infections in 2018 was targeted with this crypto-miner (around 9.22%, up from 6.7% in 2017 and 4.2% in 2016).
- Other malware spread through removable media/USBs includes the Windows LNK family of Trojans, which has been among the top three USB threats detected since at least 2016.
- The 2010 Stuxnet exploit, CVE-2010-2568, remains one of the top 10 malicious exploits spread via removable media.
- Emerging markets are the most vulnerable to malicious infection spread by removable media – with Asia, Africa and South America among the most affected – but isolated hits were also detected in countries in Europe and North America.
- Dark Tequila, a complex banking malware reported on August 21, 2018 has been claiming consumer and corporate victims in Mexico since at least 2013, with the infection spreading mainly through USB devices.
The evolving cyberthreat landscape for USBs
Infections caused by removable media are defined as local threats – those that are detected directly on a user’s computer, for example, during a scheduled, installation or user-initiated security scan. Local threats differ from threats targeting computers over the internet (web-borne threats), which are far more prevalent. Local infections can also be caused by an encrypted malicious program hidden in a complex installer. To isolate the data for malware spread by removable media such as USB devices, we took the detections triggered in the drive root of affected computers – a strong indicator that the infection source is removable media.
This data shows that the number of removable media (drive root) threat detections has declined steadily since 2014, but the overall rate of decline may be slowing down. In 2014, the ratio between a user affected by a removable media threat and the total number of such threats detected was 1:42; by 2017 this had dropped by around half to 1:25; with the estimate for 2018 around 1:22.
These numbers pale in comparison to web-borne threats: in 2017, Kaspersky Lab’s file antivirus detected 113.8 million likely removable media threats, while its web antivirus repelled just under 1.2 billion attacks launched from online resources. In light of this, it can be easy to overlook the enduring risks presented by removable media, even though around four million users worldwide will be infected in this way in 2018.
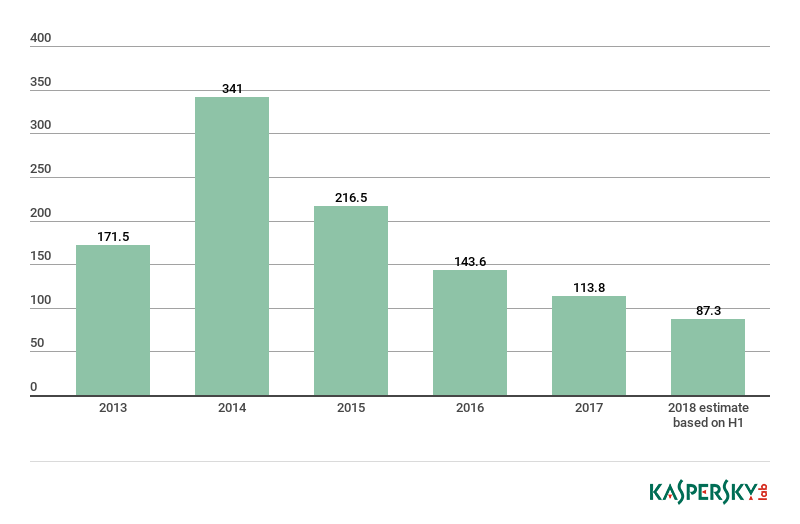
*Total number (in millions) of malware detections triggered in the drive root of user computers, a strong indicator of infection by removable media, 2013 – 2018. Source: KSN
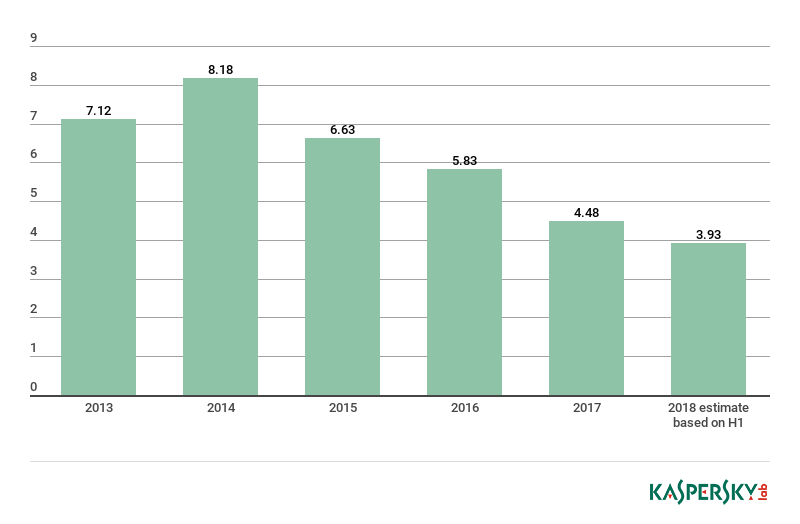
*Number of unique users (in millions) with malware detections triggered in the drive root of computers, a strong indicator of infection by removable media, 2013 – 2018. Source: KSN
USBs as a tool for advanced threat actors
USB devices appeal to attackers targeting computer networks that are not connected to the internet – such as those powering critical national infrastructure. The most famous example of this is probably the Stuxnet campaign. In 2009 and 2010, the Stuxnet worm targeted Iran’s nuclear facilities in order to disrupt operations.
USB devices were used to inject malware into the facilities’ air-gapped networks. Among other things, the devices included an exploit to a Windows LNK vulnerability (CVE-2010-2568) that enabled remote code execution. Other advanced threat actors, including Equation Group, Flame, Regin and HackingTeam, have all integrated exploits for this vulnerability into removable media to use in attacks.
Further, the structure of most USB devices allows them to be converted to provide hidden storage compartments, for the removal of stolen data, for example. The ProjectSauron 2016 toolkit was found to include a special module designed to move data from air-gapped networks to internet-connected systems. This involved USB drives that had been formatted to change the size of the partition on the USB disk, reserving some hidden space (several hundred megabytes) at the end of the disk for malicious purposes.
The Stuxnet survivor CVE-2010-2568
Microsoft fixed the last of the vulnerable LNK code path in March 2015. However, in 2016, as many as one in four Kaspersky Lab users who encountered an exploit through any attack medium, including web-borne threats, faced an exploit for this vulnerability, (although it was overtaken in 2017 by the EternalBlue exploit). However, CVE-2010-2568 continues to feature in malware distributed by USB devices and other removable media: where, despite rapidly falling numbers of detections and victims, it still ranks among the top 10 drive root threats detected by KSN.
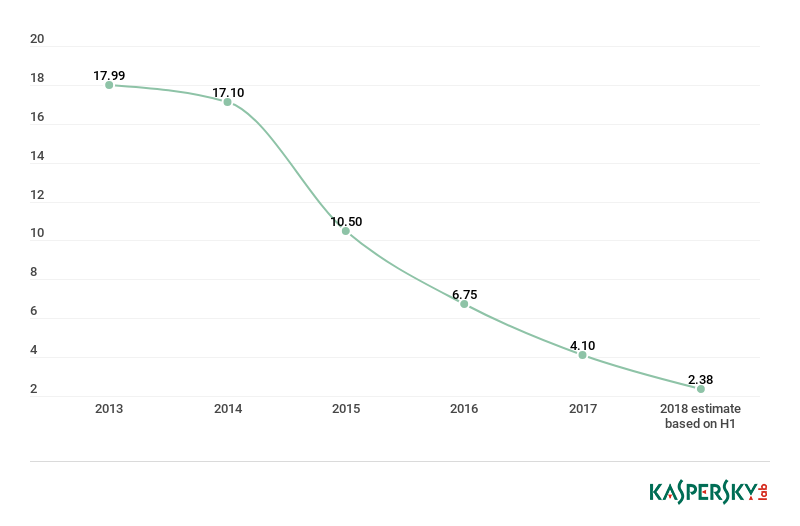
Total drive root (removable media) detections (in millions) of an exploit for CVE-2010-2568, 2013 – 2018. Source: KSN
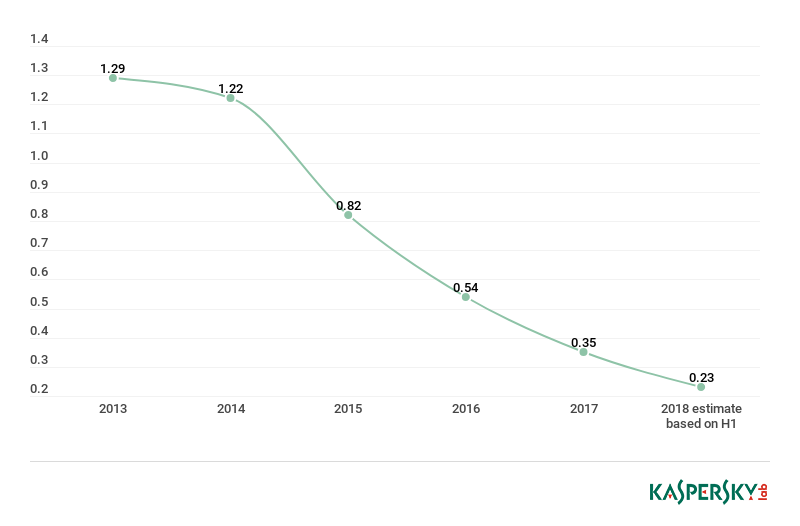
Users with drive root (removable media) detections (in millions) of an exploit for CVE-2010-2568, 2013 – 2018. Source: KSN
If the exploit detections provide an indication of the volume of malware being transmitted via removable media such as USBs, the following illustrate the kind of malware being distributed in this way.
Malware delivered via removable media
The top malware spread via removable media has stayed relatively consistent since at least 2016. For example, the family of Windows LNK malware, Trojans containing links for downloading malicious files or paths for launching a malicious executable, has remained among the top three threats spread by removable media. This malware is used by attackers to destroy, block, modify or copy data, or to disrupt the operation of a device or its network. The WinLNK Runner Trojan, which was the top detected USB threat in 2017, is used in worms for launching executable files.
In 2017, 22.7 million attempted WinLNK.Agent infections were detected, affecting nearly 900,000 users. The estimate for 2018 is around 23 million attacks, hitting just over 700,000 users. This represents a 2% rise in detections and a 20% drop in the number of users targeted year-on-year.
For the WinLNK Runner Trojan the numbers are expected to fall more sharply – with a 61% drop in detections from 2.75 million in 2017 to an estimated 1 million in 2018; and a decline of 51% in the number of users targeted (from around 920,000 in 2017 to just over 450,000 in 2018).
Other top malware spread through USB devices includes the Sality virus, first detected in 2003 but heavily modified since; and the Dinihou worm that automatically copies itself onto a USB drive, creating malicious shortcuts (LNKs) that launch the worm as soon as the new victim opens them.
Miners – rare but persistent
USB devices are also being used to spread cryptocurrency mining software. This is relatively uncommon, but successful enough for attackers to continue using this method of distribution. According to KSN data, a popular crypto-miner detected in drive roots is Trojan.Win32.Miner.ays/Trojan.Win64.Miner.all, known since 2014.
Malware in this family secretly uses the processor capacity of the infected computer to generate the cryptocurrency. The Trojan drops the mining application onto the PC, then installs and silently launches the mining software and downloads the parameters that enable it to send the results to an external server controlled by the attacker.
Kaspersky Lab’s data shows that some of the infections detected in 2018 date back years, indicating a lengthy infection likely to have had a significant negative impact on the processing power of the victim device.
Detection data for the 32-bit version of Trojan.Win32.Miner.ays is as follows:
| Year | Detection data for Trojan.Win32.Miner.ays | Unique user count |
| 2017 | 778,620 | 236,000 |
| 2018 (estimate based on H1) | 600,698 | 196,866 |
Between H1 2017 (136,954 unique users) and H1 2018 (93,433 unique users), there was a fall of 28.13 percentage points in the number of people affected by the 32-bit version of the miner.
The other version, Trojan.Win64.Miner.all, saw an expected surge in the first year of detection, after which the number of users hit has levelled out to a steady growth rate of around one-sixth per year. This small but steady growth rate can also been seen when the number of users targeted with this mining malware is compared against the overall number of users hit by removable media threats. This shows that around one in 10 users hit with a removable media threat in 2018 will be targeted with this miner, about a two-fold rise in two years.
These results suggest that propagation via removable media works well for this threat.
Detection data for Trojan.Win64.Miner.all is as follows:
| Year | Detection data for Trojan.Win64.Miner.all |
Unique user count | YoY change | Unique user count as share of all users hit with a removable media threat |
| 2016 | 4,211,246 | 245,702 | +70.15% | 4.2% |
| 2017 | 4,214,785 | 301,178 | +18.42% | 6.7% |
| 2018 (estimate based on H1) | 4,209,958 | 362,242 | +16.42% | 9.2% |
Dark Tequila – advanced banking malware
In August 2018, Kaspersky Lab researchers reported on a sophisticated cyber operation code-named Dark Tequila that has been targeting users in Mexico for at least the last five years, stealing bank credentials and personal and corporate data with malware that can move laterally through the victim computer while offline.
According to Kaspersky Lab researchers, the malicious code spreads through infected USB devices and spear phishing and includes features to evade detection. The threat actor behind Dark Tequila is believed to be Spanish-speaking and Latin American in origin.
Target geography
Emerging markets appear to be the most vulnerable to infection by removable media.
The annual numbers for 2017 show that in many such countries, around two-thirds of users experienced a ‘local’ incident, which includes drive root malware infections from removable media, compared to less than one in four in developed economies. These figures appear to be remaining consistent into 2018.
For the LNK exploit spread through removable media, the most affected countries in 2018 to date are Vietnam (18.8% of users affected), Algeria (11.2%) and India (10.9%), with infections also found in the rest of Asia, Russia and Brazil, among others, and a few hits in a number of European countries (Spain, Germany, France, the UK and Italy), the U.S. and Japan.
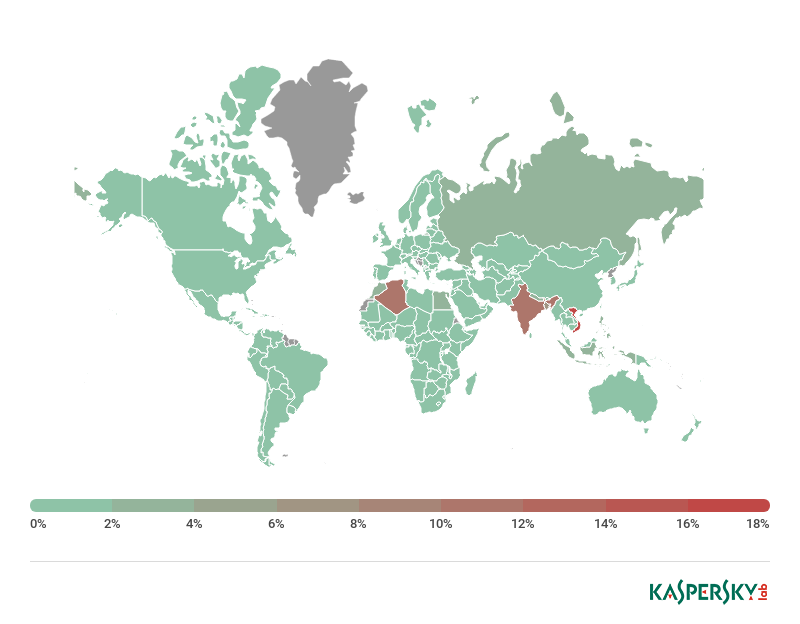
Share of users affected by an exploit for CVE-2010-2568 through removable media, 2018. Source: KSN (only countries with more than 10,000 Kaspersky Lab customers are included)
The reach is broader for the miner. Trojan.Win32.Miner.ays/Trojan.Win.64.Miner.all detections are mainly found in India (23.7%), Russia (18.45% – likely to be impacted by a larger customer base) and Kazakhstan (14.38%), with infections also found in other parts of Asia and Africa, and a few hits in several European countries (the UK, Germany, the Netherlands, Switzerland, Spain, Belgium, Austria, Italy, Denmark and Sweden), the U.S., Canada and Japan.
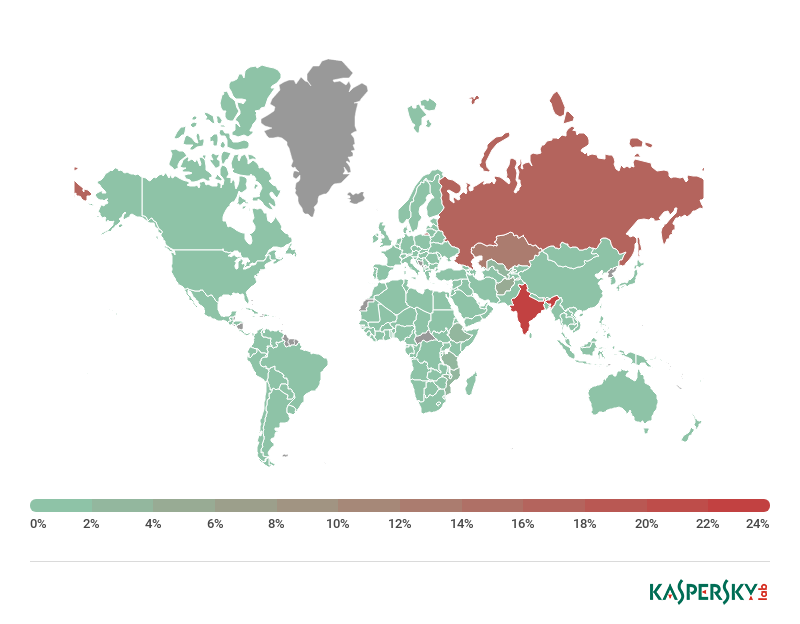
Share of users affected by the bitcoin cryptocurrency miner through removable media, 2018. Source: KSN (only countries with more than 10,000 Kaspersky Lab customers are included)
Conclusion and advice
The main purpose of this short paper is to raise awareness of a threat that consumers and businesses may underestimate.
USB drives offer many advantages: they are compact and handy, and a great brand asset, but the devices themselves, the data stored on them and the computers they are plugged into are all potentially vulnerable to cyberthreats if left unprotected.
Fortunately, there are some effective steps consumers and organizations can take to secure the use of USB devices.
Advice for all USB users:
- Be careful about the devices you connect to your computer – do you know where it came from?
- Invest in encrypted USB devices from trusted brands – this way you know your data is safe even if you lose the device
- Make sure all data stored on the USB is also encrypted
- Have a security solution in place that checks all removable media for malware before they are connected to the network – even trusted brands can be compromised through their supply chain
Additional advice for businesses:
- Manage the use of USB devices: define which USB devices can be used, by whom and for what
- Educate employees on safe USB practices – particularly if they are moving the device between a home computer and a work device
- Don’t leave USBs lying around or on display
Kaspersky Lab’s security solutions, such as Kaspersky Endpoint Security for Windows, provide security and encryption for all removable media including USB devices.





















USB threats from malware to miners