
Surprising findings in the Windows exploits landscape
At Kaspersky Lab we regularly conduct threat studies dedicated to a particular type of cyber threat. This summer we decided to look closely at what versions of Windows Operating System are most popular among our users and also at what kind of vulnerabilities are used in cyber-attacks involving exploits. As a result we prepared a study called “Windows usage and vulnerabilities’. Some of its results were rather predictable – but some were really surprising.
The summer of 2010 saw the appearance of Stuxnet, a computer worm which, as it turned out later, had been designed specifically to sabotage the uranium enrichment process at several factories in Iran. Stuxnet was a real sensation which demonstrated what malware was capable of when precisely targeted and rigorously prepared. To proliferate, the worm used an exploit for the CVE-2010-2568 vulnerability. It is an error in processing tags in Windows OS enabling the download of the random dynamic library without the user’s awareness. The vulnerability affected Windows XP, Vista, and Windows 7 as well as Windows Server 2003 and 2008.
The first malware exploiting this vulnerability was registered in July 2010. The worm Sality uses this vulnerability to distribute its own code: Sality generates vulnerable tags and distributes them through the LAN. If a user opens a folder containing one of these vulnerable tags, the malicious program immediately begins to launch. After Sality and Stuxnet this vulnerability was used by the well-known Flame and Gauss spyware.
In autumn 2010, Microsoft released a security update which patches this vulnerability. Despite this, Kaspersky Lab detection systems are still registering tens of millions of detections of CVE-2010-2568 exploits. Over the study period, more than 50 million detections on more than 19 million computers worldwide were recorded.
It’s worth noting the distribution of computer operating systems on which detections of the exploit for LNK vulnerability were registered. The lion’s share of detections (64.19%) registered over the last eight months involved XP and only 27.99% were on Windows 7. Kaspersky Lab products protecting Windows Server 2003 and 2008 also regularly report detection of these exploits (3.99% and 1.58% detections respectively). The large number of detections coming from XP users suggests that most of these computers either don’t have an installed security solution or use a vulnerable version of Windows – or both. The detections coming from server systems prove the presence of malicious tags exploiting the CVE-2010-2568 vulnerability on network folders with open access.
The geographical distribution of all registered CVE-2010-2568 detections is also interesting.
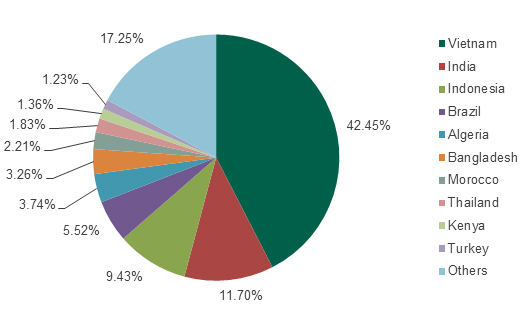
CVE-2010-2568 detections, country distribution Nov 2013 – June 2014
Vietnam (42.45%), India (11.7%) and Algeria (5.52%) are among the leaders for the number of Kaspersky Lab detections of one of the most dangerous Windows vulnerabilities currently known. Interestingly, according our research, the outdated XP OS is also widely used in all these countries. Here are the top countries for XP use in June 2014:
| Vietnam | 38.79% |
| China | 27.35% |
| India | 26.88% |
| Algeria | 24.25% |
| Italy | 20.31% |
| Spain | 19.26% |
| Russian Federation | 17.40% |
| France | 12.04% |
| Germany | 8.54% |
| United States | 4.52% |
Top 10 countries with largest share of Windows XP users
in overall volume of users of Kaspersky Lab products.
It’s not surprising that CVE-2010-2568 exploits are still popular in some of these countries. So many users of outdated versions of Windows mean these exploits are effective even though almost four years have passed since the disclosure and patching of the vulnerability.
Other findings from this research are available in the full report.



















The echo of Stuxnet