Maybe you’re one of the increasing number of users on the lookout for new ways to protect your machine against the malware that’s always in the news. Maybe you’re even one of the users running a sandbox on your machines. (If you’re not, and you don’t know what a sandbox is – it’s an isolated area on a computer, often running on a virtual machine, where you can run code without infecting the main or host machine. Sometimes a sandbox is a separate program that functions within the framework of the local OS – this type is easier for a novice to use as you don’t need to install a virtual machine.)
I was trying to download a sandbox application of the second type when I stumbled on something interesting. I got unexpectedly re-routed to download.com – it’s part of cnet.com and one of the most popular software repositories on the Internet.
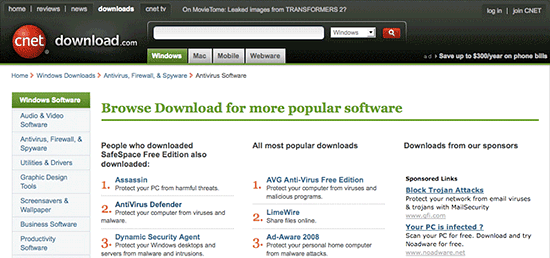
The download went smoothly, but then I got re-routed to another page on download.com. This page contained recommendations for other popular software available for download.

The list of recommended software includes AntiVirus Defender, an adware program that we detect as not-a-virus:AdWare.Win32.OneStep.z. We’ve notified cnet so they are aware of the issue.
I think there’s a pretty clear moral here. You’re security conscious and you want to protect your computer. You’re looking for useful utilities. Download.com assures users that all programs available via the website have been analysed, and don’t contain any malicious code. So maybe you relax your vigilance. But with both businesses and bad guys making use of sponsored links on sites like download.com and Google, you’ve got to stay very alert indeed to make sure that you don’t get caught out.

















Unexpected redirects