
I was browsing through compromised websites used for spreading malware and found one from Argentina which belongs to a veterinary supplier. The admin panel got p0wned and, worst of all, it had a tab with the personal details of people who had posted their CVs (curriculum vitae). So, what exactly has happened? Well, basically lots of confidential information has been leaked and we are talking about home addresses, telephone numbers, details of education centers attended, mobile phone numbers, email addresses, marital status, children and even personal references. This is very bad because the same information can easily be used for all kinds of fraudulent activities: on-line ID theft, targeted attacks and so on. Here are just a few examples of real CVs uploaded and saved on the compromised site:
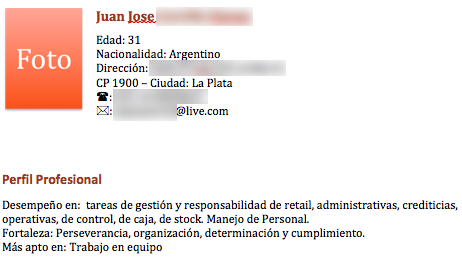

Most of the victims are from Argentina or are living there.
So, who is behind the attack? It’s hard to say, but there are a couple of interesting things to consider. The first one is related to a fake ID used to submit a CV.
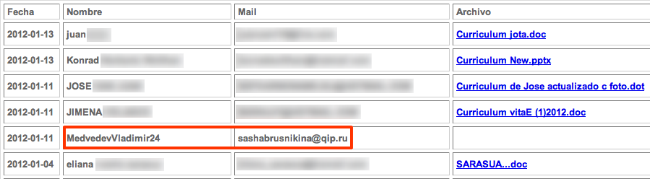
It looks like someone from a Russian-speaking country has at least tried to sniff the site. The second interesting thing is that the same website has been used for spreading Brazilian Trojan bankers.
So, it’s hard to say who’s definitely behind this particular attack. Is it Russians or Brazilians? Or maybe it’s a combined effort between Brazilian and Russian-speaking cybercriminals. If that is the case, it wouldn’t be the first time they have worked together; we have recently seen Brazilian cybercriminals using well-known Russian cybercrime web resources.






















Two-pronged attack: Argentine site hit by malware and data leak