
Microsoft released another heap of patches today, twelve to be exact.
Most interesting is the IE CSS parser vulnerability that was exploited with a new Eleonore Exploit Pack release, v1.6.3a, selling for over $2,000 with the 0day, some new exploits, and interesting anti-research and tracking functionality. The vulnerability has been publicly disclosed by a Chinese researcher since at least late November.
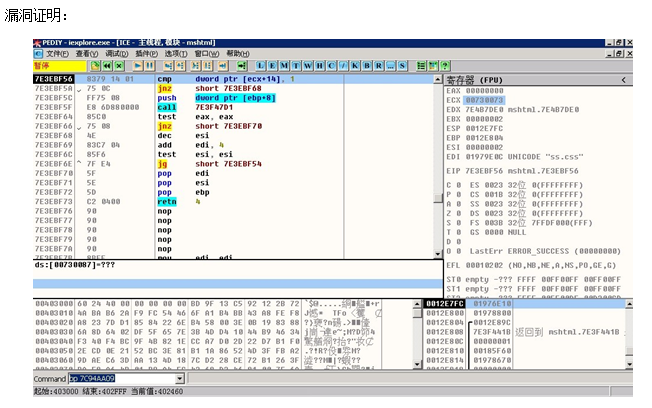
Also interesting enough to deserve a security advisory and FixIt patch, is a vulnerability documented as CVE-2011-0096, addressing XSS-identical results due to a flaw in the browser’s code.
The Microsoft advisory arrived eleven days prior, providing mitigation advice along with a “Fix it” installer. This patch cycle is 24 days after the Chinese zine release date. The writeup was originally authored by d4rkwind and added to a 5th edition Chinese mag “Ph4nt0m Webzine 0x05”.
According to its CVE entry, “The MHTML implementation in Microsoft Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista SP1 and SP2, Windows Server 2008 Gold, SP2, and R2, and Windows 7 does not properly handle a MIME format in a request for content blocks in a document, which allows remote attackers to conduct cross-site scripting (XSS) attacks via a crafted web site that is visited in Internet Explorer.”
The Microsoft Security Advisory (not the Bulletin) was published 1/28/2011 on the last Friday of January.
A blog post describing it as “MHTML script injection” showed up on the Microsoft Security Research and Defense blog on the 28th of January. “Any service that allows user input to be reflected back to the user could be affected by this issue. However the impact of scripting injected into a service is dependent on how the service itself is implemented. In this way, the impact is the same a server-side cross-site scripting issue but the vulnerability lies in the client.”
In the meantime, Microsoft released a “Fix It” tool. It was digitally signed by Microsoft on the 27th and posted or publicly offered on the 28th. The file “MicrosoftFixit50602.msi” was a 649 kb file. The file automates configuration of the recommended workaround, which is to lockdown the MHTML protocol to prevent running scripts like javascript. Minor issues were involved with the running the Fix it tool. “Impact of workaround: the MHTML protocol will be restricted to prevent the launch of script in all zones within an MHTML document. Any application that uses MHTML will be affected by this workaround. Script in standard HTML files is not affected by this workaround.” The advisory is posted but the patch still has not arrived. The exploit is reported to be used in the wild, installing the “Fix it” workaround is recommended. (post updated 3/2011)
While this post was being written, Adobe released some major patches and joined the club.





















Tuesday’s Interesting IE Patch