
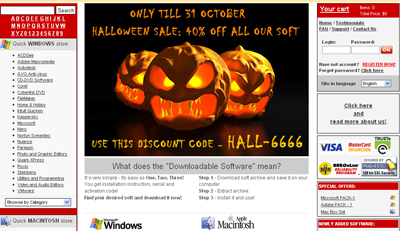
Halloween’s almost here. And it’s not just the witches, ghosts and ghouls you need to watch out for, but the latest wave of Internet scams. As ever, the spammers are out in force, offering cheap software:
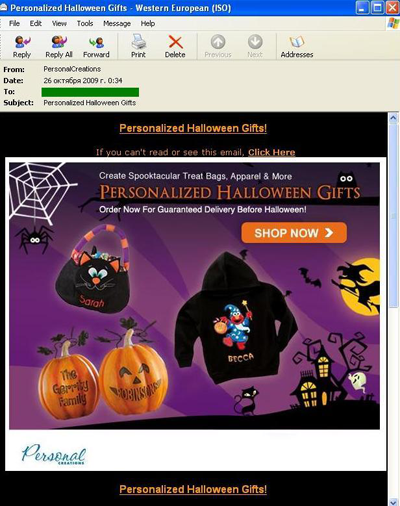
costumes and personalized gifts:
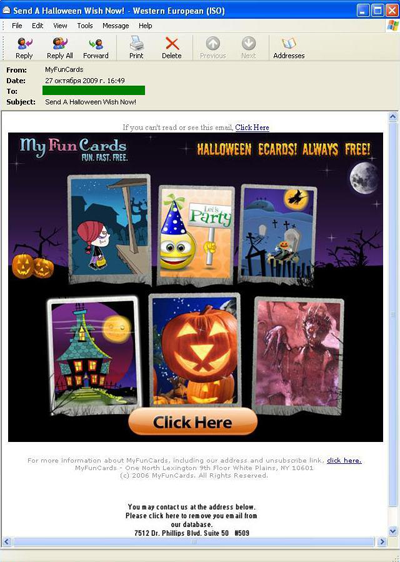
and even e-cards!
If you want to send a card, you need to install a special browser utility. Do this, and as long you’re in the US, Canada, or a number of other Western countries, the spammer will get paid by the guys who developed the utility.
If you’re coming from a Russian IP address, though, you’ll see this message:
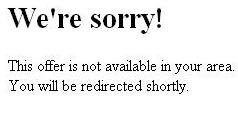
and get redirected to a lottery site:
If you’re a regular reader of this blog, you might find the last two screen shots familiar; in fact, the scam is identical to one I wrote about back in June this year.
The spammers haven’t changed their tried and trusted methods for this holiday, and we haven’t changed our advice – take up an offer like the ones above, and you’ll be putting money into spammers’ pockets, giving away your personal details, or opening the door to malware. And I think all of that is a lot scarier than any Halloween monster…

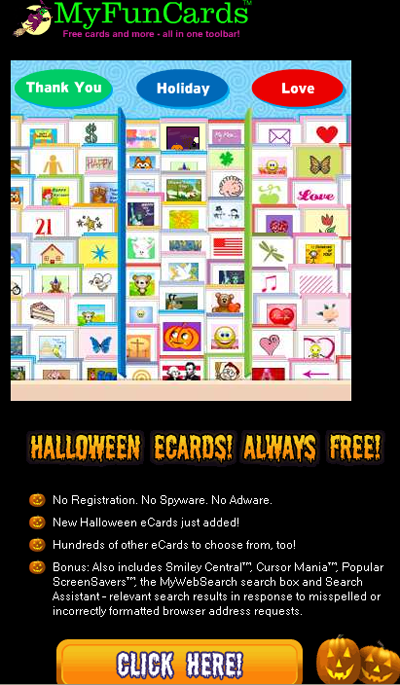






















Trick or treat?