
We love social networking sites, and phishers are no exception. They’ve been sending out fake Twitter notifications for a while now. The one we’ve just received doesn’t have much in common with previous phishing attacks.
The message looks like this:
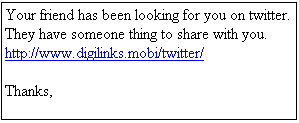
Lots of suspicious things about this message: the word “twitter” comes at the end of the link, rather than the beginning, and the English is a bit dodgy as well. None of the addresses in the “From” fields have any strong associations with Twitter:
- From: “Donald” VanceShade@qoodly.com
- From: “Michael” KirbySchulte@filepages.net
- From: “Jeff” JeremiahSilver@savingssavingsandmoresavings.net
Click on the link (aren’t people getting tired of all this clicking?) and you end up on a site which is very generously offering to let you into the secret of how to make money on Twitter. All you have to do is enter your details.
And once you’ve done that, you get asked for your credit card details:
So here’s the $64,000 question: is it really a good idea to enter your credit card details on a site telling you how to make money from home, a site that you reached by clicking on a spam link? (On second thoughts, no prizes, because we should all know the answer by now!)
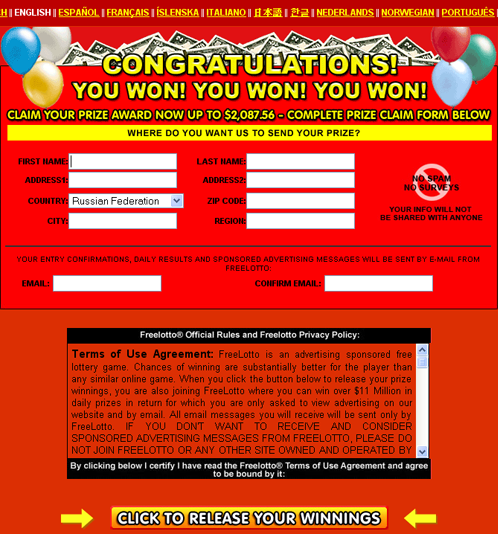
But the story doesn’t end here – out of sheer curiosity, I put http://www.digilinks.mobi/facebook into my browser (instead of http://www.digilinks.mobi/twitter/) and got this:

And then got redirected to a site telling me I’d won a stack of money. Great news – why should I put in time ‘earning’ money on Twitter when I can just win the lottery? All I need to do is give them my details…
We love social networks for some of the oddities they throw up. And phishers love them too, because there’s always someone who’s willing to click, and click, and click again.























Tweet’n’earn