
Is this malicious campaign familiar to you?
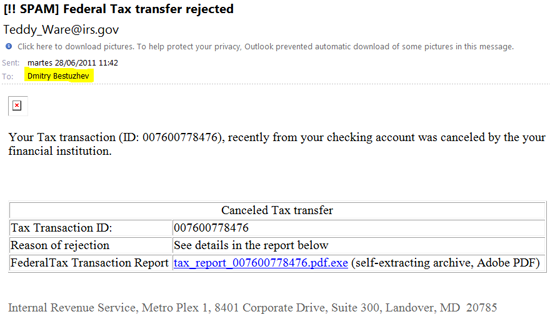
Yes, it’s Zeus (Zbot). If your system is fully patched and you click on the link you won’t get the binary; a special PHP script on sddghdskfgjr.cz.cc won’t release it and you will only get an error message. It’s standard filtering the criminals use for anti-automated malware collection.
The mentioned .cc domain is shorted twice with 2 different short name services. The first one is http://3cm.kz/. Despite the official info of the services (a legitimate one) it has a strange slogan that is really close to the Russian speaking cybercriminals slang “Short your beast”:

I found an interesting “bug” in the malicious .php script on the .cc domain. If you go to the short link with any of the special characters at the end and even if it’s the same system and it’s fully patched, you will get the binary again and again. For example, instead of clicking on http://3cm.kz/example, just put at the end http://3cm.kz/example+ or http://3cm.kz/example* or any other and for each new special char you will get the binary. One special char per one new download. The second short URL service used by the criminals is http://shortn.me
When you check statistics on how many users have been clicking, you will find a big difference between the first shortened URL and the second one:
(Clicks on 3cm – only 24 clicks)
(Clicks on Shortn – 200 clicks)
Not so many clicks, but we should remember first of all it’s a targeted attack and second that the impact is quiet high. Here the importance it’s not the quantity but the quality.
On the other hand the difference between clicks show the criminals use the Shortnme link as a general one for many targets, while the short link from 3Cm is specially prepared for each particular target (company). This way the cyber criminals can track possibly better infections from each target.
At the moment of download of the malicious sample it was detected by UDS (Cloud technology) of Kaspersky and now it’s detected as Trojan-Spy.Win32.Zbot.bvmv




















Tracking bugs in Zeus campaigns