
There are almost no spam-free zones left in the world today. For many years, spammers have fought hard for areas from which they could launch their attacks, constantly trying to maintain conquered territories while annexing new ones. Meanwhile law-enforcement agencies, anti-spam vendors and other interested parties are constantly battling this ‘invasion’. In this article we will examine the factors which affect the migration of spam sources, analyze shifts in the distribution of spam sources by country and discuss the trends of this migration.
2003-2009: the chronicle
Across the world, anti-spam companies, law enforcement agencies and others have targeted spammers, forcing them to search for alternative methods of distributing their spam, spreading mass mailings and bypassing filters.
In 2003, many European countries adopted new anti-spam legislation as a result of Directive 2002/58/EC of the European Parliament and of the Council of 12 July 2002 concerning the processing of personal data and the protection of privacy in the electronic communications sector (Directive on privacy and electronic communications). This directive also demanded safeguards against unsolicited commercial communications. In the same year, anti-spam legislation was passed in the US and Australia. The latter is still considered to have some of the world’s most effective anti-spam laws.
Despite this legislation, the amount of spam in mail traffic continued to grow. In 2004 it increased by 14% compared with the previous year and accounted for 80% of all mail traffic. It maintained this level up to and including 2006. In order to combat spam, all major email service providers installed anti-spam filters and many antivirus vendors began to integrate anti-spam engines into their products.
The US’s newly-adopted anti-spam legislation could not stop it becoming by far the most prolific source of spam, with some estimates putting its output at nearly 50% of all the spam emails in the world.
The year 2006 saw a second wave of anti-spam laws, and during the period 2006-2007 such legislation was adopted in China, Pakistan, Singapore and New Zealand. Russia also made amendments to the federal law ‘On Advertising’. Additionally, technology was introduced to combat spam, so the spammers had to improve distribution methods and ways to evade spam filters. It was in 2006 when the ‘open relay’ system used by spammers for spreading unsolicited emails was finally discredited and abolished, pushing distributors to turn to zombie networks. In the meantime spam became much more technically diverse: the first graphical spam with background noise appeared, and spammers began using different features of HTML to bypass filtering.
By 2006 Russia and China had joined the US in the top three sources of global spam. In the Russian-speaking sector of the Internet, Russia was the number one distributor of spam: unsolicited mails from the country accounted for 22% of all mail traffic. The US was second with 20%, followed by China on 11%. In western Europe and America the US remained the principal source of spam, followed by Russia, China and numerous western European countries.
On 30 March 2006, China passed legislation concerning ‘Regulations on Internet E-Mail Services’ and from 2007 onwards the amount of spam originating from the country decreased considerably.
In 2007, the US topped the rating as the most prolific spam source with 11.2% of all distributed spam, closely followed by Russia on 10.8%. Poland came third, being the only other eastern European representative in the Top 20. India was a Top 10 newcomer in 2007 – four years later this country was set to become the world’s most prolific distributor of spam. China occupied a lowly 9th position. The rating also included five Latin American countries.
The same year saw owners of bot networks begin their ‘geographical search’. Having effectively been run out of town in China by a policy of stringent Internet regulation, they switched to less protected countries in Asia, the Middle East and Latin America. In addition to the absence of any legislative base, these regions are also known for low levels of computer literacy and a lack of antivirus software. This gives the fraudsters easy access to users’ computers.
In 2008, the US and Russia swapped places in the rating of the most prolific spam sources: Russia was responsible for 22% of all distributed spam, the US came second with 16%, with the others much further behind. In the same year another eastern European country, Ukraine, entered the Top 10.
In the second half of 2009 the amount of spam emails coming from the US increased considerably, accounting for 24.4% of all spam traffic. At the same time the number of infected American domains was growing. This could be interpreted as either a heightened interest in the US by virus writers, or the launch of combined attacks which aimed to infect US domains in order to harvest vulnerable computers for use in botnets (e.g. the attacks using Bredolab). In 2009, the US’s contribution to the total volume of spam in circulation averaged 16%. Conversely, Russia’s share of spam was gradually decreasing, dropping to 8.5%. Behind these two major players came Brazil with 7.6%, India on 5.9% and South Korea on 4.8%. The bot owners were strengthening their positions in developing countries: the Top 10 did not include a single western European country.
2010: closure of botnets and affiliate programs
Prior to 2010, the US and Russia topped the rating of countries hosting the most developed spam businesses. There were years during which the total share of these two countries reached 22-42% of all the spam in circulation. However, in 2010 the situation changed.
The year 2010 will go down in history as the year in which those fighting botnets struck back. Various botnet command centers had been closed before – the McColo hosting provider which hosted the command centers of several botnets was shut down in 2008 – but never before had the struggle been so large-scale and so effective. In addition, criminal proceedings against several spammers and botnet owners were initiated in 2010. It is good to know that these were not isolated incidents and similar initiatives are continuing: for instance, in March 2011 the Rustock command centers were closed.
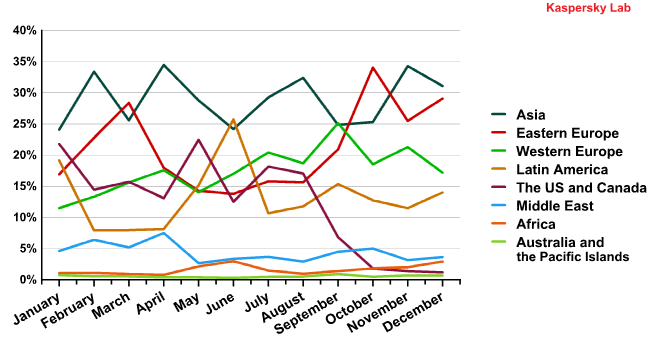
The 2010 anti-botnet campaign no doubt forced a great many sources of spam to relocate. This graph of the distribution of spam sources by region shows the dynamics of those changes.
Interestingly, the share of spam coming from eastern Europe grew in March and October, but the figures for Latin America were higher in June. Meanwhile the US and Canadian contributions started to decrease in September and continued to fall.
This considerable reduction in the amount of spam originating from the US was caused by the closure of the Pushdo/Cutwail botnet command centers. The closure of the pharmaceutical affiliate program SpamIt probably also had an effect on the quantity of spam sent from the US.
The anti-botnet campaign forced cybercriminals to explore new and more convenient territories from which to launch their spam mailings. In October, the amount of spam from Russia, Ukraine and other eastern European countries increased considerably. The trend continued in November with a rise in the output from Vietnam, India and Indonesia. Almost every region of the world contributed to spam distribution in the year 2010. Even Africa, which had not previously been a source, appeared for the first time with 1.64% of the total quantity of spam.
An analysis of the amount of emails with malicious attachments can help us to spot any new areas of the globe from which spammers are beginning to launch unsolicited mailings. When setting up a botnet it is standard practice for spammers to send malicious emails to users. These emails contain bots which infect users’ computers to spread spam. Between October and December 2010, email antivirus detection rates in the US and western Europe decreased considerably, while in eastern Europe and Asia the amount of malware detected in mail traffic grew.

Email antivirus detection activity in a selection of Top 10 countries in October-December of 2010
2011: stabilization
Unlike the previous year, in 2011 the share of spam distributed from different regions stopped fluctuating. Overall, the first quarter of 2011 was relatively stable.

Spam by region in the first half of 2011
One of the most marked trends of the first half of 2011 was the gradual rise of Asia and Latin America’s share of spam worldwide, accompanied by a decrease in spam traffic originating in western and eastern Europe. As mentioned above, Asia and Latin America are attractive to the spammers for a number of reasons and that is why the number of infected computers used for sending spam in these regions increased.
In 2011, the rating of the most prolific spam producing countries underwent major changes: no more do we see three countries responsible for half of the spam output of the world. The zombie machines used to spread spam emails are distributed fairly evenly.

Sources of spam by country in the first half of 2011
This distribution signals the end of the spammers’ geographical expansion. There are no “botnet free” territories left: infected computers sending spam are now found as far afield as South Africa and remote islands in the middle of the Pacific Ocean. Developing countries attract botnet owners due to the absence of anti-spam legislation and low IT security levels, while developed countries are of interest because of their fast, widely available Internet connectivity.
Following the effective anti-botnet campaign of 2010, we are now witnessing a new growth in the number of botnets. They are relatively small, so the spammers can easily switch to another botnet if one of them is shut down. This also leads to a more even distribution of infected computers by country.
Reasons for the migration of spam sources
Armed with this information we can now highlight several reasons for the relocation of spam sources by region.
- Progress on the legal front
China’s example illustrates how spam distribution depends on the effectiveness of a country’s anti-spam legislation: after adopting such laws, the quantity of unsolicited email originating from this country decreased dramatically and is now less the 1% of the world’s spam traffic. Additionally, the introduction of far more stringent registration policies for Internet addresses using the ‘.cn’ domain at the end of 2009 resulted in a considerable reduction in the number of malicious and spammer sites in this zone. The new rules now allow only legal representatives to register domains. Of course, not only is it important that anti-spam and anti-malware laws are passed; nations must also provide their authorities with the tools necessary to enforce them, and it seems that China has.Australia is another shining example. The graph of spam sources by region shows that Australia and the Pacific Islands spread less spam than any other region, even though Australia is a big country with widely available Internet connectivity. The reason for this is the Australian Spam Act 2003, the harshest anti-spam legislation currently in existence. The Australian government actively involves Internet providers in the struggle against spam: they are required to detect zombie computers on their networks (infected end-user computers which distribute malware and spam) and help their users to treat infected machines. Additionally, users are offered an easy spam notification tool: one mouse click is enough to send a sample of an unsolicited email to the state anti-spam agencies. - Geographical expansion
The development of the Internet and its worldwide expansion has led to a rise in the number of countries where spam originates. Over the last five years spam has started to emanate from countries in Latin America, Asia, the Middle East and Africa. The spammers’ geographical expansion is now virtually complete. - Closure of botnets
The closure of botnets affects the amount and distribution of spam in real-time. Though some zombie networks may include computers located worldwide, they are usually concentrated in one region. The closure of botnet command centers within a specific region drastically reduces the volume of spam originating from that area. - Closure of affiliate programs
Such cases are rare and to a great extent depend on the activity of the law enforcement agencies. The best example was the closure of the pharmaceutical affiliate program SpamIt in October 2010 which affected the content of spam and the geography of its distribution.
Conclusion and forecasts
Currently, the lion’s share of spam is distributed with the help of botnets; networks of infected computers connected to botnet command centers. Other spam is still sent directly from the spammers’ servers. The location of such servers and botnets depends on many factors, including the presence and effectiveness of anti-spam legislation in different countries and the anti-botnet activities of both governmental and non-governmental initiatives. Additionally, the spammers consider such factors as the level of computer literacy and IT protection in each country, and the frequency of software updates on users’ machines.
According to statistics, spam sources are now more evenly distributed throughout the world. This can easily be explained by the fact that currently the developing world is catching up in terms of computer access while the quality of communication channels is growing. Of course, it is a process that may take decades, but eventually it will lead to a situation whereby all countries are equally attractive to botnet owners.
Meanwhile the BRICS and other rapidly developing countries will top the rating of the most prolific sources of spam because they are especially interesting to the spammers from the ‘legislation/IT protection/number of users/bandwidth’ point of view.
We expect the amount of spam originating from the US to grow, although it will not reach its previous level. Widely available Internet connectivity and a large number of users attract the attention of botnet owners despite the raft of anti-spam legislation adopted in this country and the high level of IT protection in use. Notably, in May 2011 the US took 2nd place in the rating of countries where mail antivirus detected malware most frequently and since then it has not fallen below 4th position, which indirectly proves the presence of botnets on its territory.
The year 2010 demonstrated that spam could be effectively combated both by way of filtering and by other means such as closing down botnet command centers and bringing those responsible to justice. We hope that the comprehensive anti-spam measures taken so far will continue long into the future.



















The Planet of the Spammers