
The fight against spam should include a complete set of measures to both protect users and counter the criminal organizations behind spam. The developments that took place at the end of 2010 demonstrated just how important the legal factor is, and just how effective the cooperation of law enforcement agencies in anti-spam operations can be.
The noticeable fall in the volume of spam traffic in the autumn of 2010 is clearly attributable to the joint efforts of the Internet crime units of many law enforcement authorities around the world.
Spam traffic slows down
In late August 2010, the closure of the command centers of the Pushdo/Cutwail botnet was announced. After these botnets were shut down, Kaspersky Lab noted a decline of approximately 2 percentage points in the volume of spam in all mail traffic. This number — which may seem insignificant at first glance — not only depends on the volume of spam, but on the volume of ‘clean’ correspondence as well. In absolute terms, based on Kaspersky Lab’s data, the volume of spam plummeted by 15% between 15 and 30 August.
Even though the shutdown of the Pushdo and Cutwail botnets did not have a dramatic effect on the spam world, it did set off its own kind of chain reaction that impacted the volume of spam traffic over the autumn period.
You decide: compared to August’s figures, in September spam fell by nearly 1.5 percentage points, and between 01 and 25 October it fell by another 2.4 percentage points. In absolute terms, that means that the amount of unwanted correspondence as of 24 October, 2010, dropped by nearly one quarter compared to the same figure from mid-August. Note that at this time, no events had taken place that would have directly impacted spammers’ capabilities. It is possible that some botnets just went very low-profile when law enforcement agencies started to get more actively involved. Readers may recall that in addition to the shutdown of the Pushdo and Cutwail botnets, which did directly affect the volume of spam, a lot of press attention was focused on the arrests of the members of the group that had stolen peoples’ money through the ZeuS botnet. Furthermore, over the first two months of autumn, law enforcement agencies turned their attentions to pharmaceutical spam, which primarily affected the content of spam and spam categories, but could also have had an effect on its volume as well.
On 25 October, spammers were hit by a second unwelcome surprise: law enforcement agencies in the Netherlands had struck several powerful blows against botnets comprised of computers infected with Bredolab. All in all, by the end of October, 143 command centers were neutralized and one person who was suspected of managing the botnets was arrested.

Fluctuations in the percentage of spam in email traffic
after the Bredolab botnet shutdown
After the Bredolab battle that raged from 25 October to 04 November, the volume of spam fell by one-third compared to mid-October. If we compare the volume of spam during the last week of October with the numbers from mid-August 2010, you can see it dropped by one half! This result, as we noted above, comes after a combination of events and factors, including the shutdown of the Pushdo and Bredolab command centers, caution on the part of the owners of targeted botnets over this period and the pressure exerted on pharmaceutical spammers by law enforcement agencies. About ten days later, the volume of spam bounced back to its mid-October levels.
The graphic below illustrates recent spam developments. It starts with a relative spam volume of 100% at the beginning of August and tracks the subsequent onset of the “crisis” and its fluctuations over the course of the last six months of 2010 through to the beginning of 2011.

Fluctuations in spam traffic volumes between August 2010 and January 2011
No comment is necessary — the above graph illustrates the unprecedented success achieved in the fight against spam on a global scale.
Turf wars: losses and gains
The shutdown of botnet command centers did not only have an effect on the quantity of spam emails — in late 2010, the geography of spam also changed. What that means is that there was a change not only in the countries from which spam originated, but also in the countries that were the recipients of the largest amounts of spam. As we saw from the developments in late 2010, mass mailings with malicious attachments targeting certain regions preceded an upsurge in the spam activity based within those regions. The reason is simple: when building a botnet in a particular geographical region, cybercriminals first infect users’ computers with spambots, including via malicious mailings, then those infected computers also start to send spam.
The geography of spam: countries of origin
The most notable change in the so-called geography of spam was the impressive drop in the volume of unwanted correspondence sent from the US. The reason is obvious: a large number of computers infected with Cutwail were located in the US, and in late August, the command centers for the Pushdo and Cutwail botnets were shut down. In September, the amount of unwanted correspondence that spread from the US was reduced by a factor of about three. In October, the US moved from first or second position in the Top 20 down to eighteenth place, accounting for just 1.6% of all spam traffic, and in November it did not appear in the Top 20 at all.
A drop in outgoing spam traffic was also seen in Asia.
Instead, spammers tried to compensate for their losses with more proactive operations in South America and Europe.

Changes in the distribution of the sources of spam around the world
between August and December 2010
As you can see from the chart, in September it was Europe, both eastern and western, that compensated for the downswing in US-based spam traffic. In early autumn, the amount of spam sent from all European countries, with the exception of Italy, Bulgaria and Lithuania, increased to some extent.
As far as Latin America is concerned, Brazil saw an increase in the amount of outgoing spam in September. It was due to Brazil’s spam surge that the percentage of spam originating from Latin America grew by more than 3 percentage points.
However, the spammers were not able to fully redeem their losses in the United States.
In October, spam originating from western European countries was again on the decline. It appears that the fight against botnets had spread to western Europe and forced the botnet controllers to become more cautious, particularly in Germany, Austria, France, Great Britain and the Netherlands.
Meanwhile, email traffic contained more unwanted correspondence coming from Asia and eastern Europe, primarily from India and Russia. It seems that the guilty party here is Bredolab, which was still going strong in September and October.
Most of the computers infected by Bredolab were, according to Kaspersky Lab, located in India and Russia. However, Bredolab was shut down and in November the amount of spam coming from Russia, and as a result, from across Eastern Europe, experienced a sharp drop.
At this point, spammers again turned their attentions to sending mass mailings from western Europe. As a result, spammers kept the region riding a kind of spam rollercoaster — one minute, western European countries were sending out huge volumes of spam, and the next, practically nothing.
Countries in Asia — namely Vietnam and Indonesia — were also used by spammers to make up for their autumnal losses.
Malicious code through the post
Spammers have done everything they can to get their botnets back up and running. One of the things that malicious users traditionally resort to in order to build or develop a botnet is to distribute malicious code via emails. In autumn, we paid particular attention to the countries where these types of emails originated, since the target regions were likely to become the centers of new or restored botnets.
As soon as law enforcement agencies in countries with developed legislative systems noted the spambot activity, the malicious users running them seemed to lose interest in operating from there. The percentage of detected threats from our email antivirus products running in the regions that were previously at the top of the list has shown that these numbers are now falling steadily:

Threats detected by Kaspersky Lab email antivirus programs
between August 2010 and January 2011
As you can see from the graph, the volume of detected threats in email within the US, Spain, Italy and Great Britain began to fall in October and November, 2010. In Japan and France, the number of detected threats started dropping as early as September.
The only unusual developments in the chart above are associated with Germany’s curve. In October, we saw more antivirus threat detections in this region than in September and November. However, in this case the surge is not related so much to the mailings sent out by spambots as it is with a different type of malicious program.
While the number of detected email threats was falling in developed countries, the amount of detected threats in Asia and eastern Europe began to climb steadily. When using spambots to generate mass mailings in western countries, malicious users were aiming to take advantage of the high levels of computer use in those countries. However, by sending malicious programs to eastern countries, the cybercriminals were hoping to take advantage of the low levels of computer literacy among local users and the either inadequate or non-existent anti-spam and anti-malware legislation.
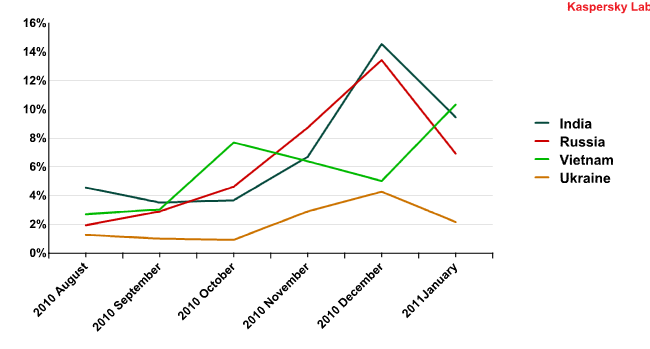
Detected email threats in eastern countries
between August 2010 and January 2011
On the subject of content
The spam industry experienced more than just a drop in spam volume and changes in the regions from which spam was sent. Let us now take a look at the categories of spam and the changes in the structure of the spam market, i.e., spam clients.
Choosing a partner
The October shutdown of the SpamIt partner program had the biggest impact on the distribution of categories of spam. SpamIt, one of the leading spammer “partnerships”, announced its closure in the latter half of September 2010.
The partner program, or partnership, is a marketing approach in which a goods retailer pays a spammer on a per-purchasing-client basis rather than for the actual advertising. In some cases, a partnership may be organized directly by the retailer. But more frequently, the arrangement is organized by third-parties that serve as facilitators, linking retailers with spammers. In such cases, the money for each purchasing client, or a percentage of each purchase, is received not only by the spam partner, but also by the party that set up the partnership.
SpamIt was one of the leading partnerships and specialized in pharmaceutical spam. Its closure primarily affected the amount of spam advertising so-called medications, or in other words, the volume of spam advertising counterfeit Viagra, etc. After 20 September, this type of spam fell by one third and its percentage of the total spam traffic fell from 31% to 21%. This happened over the course of just one week. At the same time, the number of emails in which malicious code was planted started to rise, as spammers transitioned from advertising pharmaceuticals to mass mailings of malicious code. Notably, in early September Kaspersky Lab saw a considerable rise in the percentage of Pharmaceutical and Health-Related Goods and Services spam. In all probability, the partners who knew about the closure of the program before the general public did attempted to cash in on the pharmaceuticals bandwagon while it was still possible to do so.
SpamIt was a major partnership involved in pharmaceutical spam, but its closure did not mean the end of Viagra-type spam as we know it. The Glavmed partnership is still alive and well on the Internet. However, on 26 October, 2010, the investigative arm of the Department of the Interior of the Moscow Central Administration struck a major blow against this partnership. On that day criminal proceedings were filed against Igor Gusev, the General Director of Despmedia, whom it appears, was the person behind the Glavmed partnership.
Remarkably, during mid-October when the spammers had already recovered from the SpamIt closure and the Glavmed furore had not yet started, the amount of pharmaceutical spam again began to climb. One gets the impression that the spammers regrouped after SpamIt’s closure and again decided to return to mass mailings of Viagra-style advertisements. However, the Gusev affair curtailed their plans and the volume of mailings once again began to drop. Throughout November and December, the amount of spam advertising Viagra hit a record low of between 8 and 12%. This highlights a major increase in the amount of attention afforded by law enforcement agencies to pharmaceutical spam, which caused most malicious users to desist from any involvement.
After losing income from pharmaceutical spam, spammers tried to find another source of revenue. This turned out to be a little more difficult than they first thought as they jumped from one partner program to another during the latter part of the year, particularly November.

Fluctuations among spam categories
between September 2010 and January 2011
Advertisements for fake luxury goods experienced two major boosts. The first came when the amount of pharmaceutical spam dropped between late September and early October and the volume of spam advertising fake luxury goods more than doubled to around 20% of all spam. However, this type of mailing seems to have disappointed spammers and did not bring in the expected returns, as mailings started to decline throughout October, ending the month at barely more than 5%. Then in December, right before the holidays, spammers once again placed their hopes of making some money on the sale of fake luxury goods, providing the second upsurge of activity in this spam category.
Closer to the end of October, when the volume of pharmaceutical spam had already dropped significantly and attempts to fill the gap with advertisements for fake luxury goods had failed; we saw a jump in the number of spam emails advertising online casinos. In early November, these mailings already represented over 15% of all spam traffic. Yet by the end of the month, this category had all but completely disappeared from users’ inboxes, which means that these mailings had failed to find their targets.
Spam with advertisements for adult content websites and dating sites increased during the third week of the last month of autumn before falling again a little later. Remarkably, the percentage of adult content spam mailings were minimal prior to late August 2010, then began to increase at the start of autumn 2010, stabilizing at about 4-5% of all spam traffic.
Conclusion
The tumultuous events in the world of spam in late 2010 again reminded the Internet community of the simple truth: the fight against spam is effective only when law enforcement agencies are actively involved.
The anti-spam industry works solely to protect users’ inboxes and is not involved in the capture of spammers or the shutdown of spambots. We have different objectives and different capabilities.
The effective actions of law enforcement agencies in 2010 led to a two-fold decrease in the volume of spam, which is without doubt a major achievement. Nevertheless, spammers and malicious users running botnets are not the types who give up their lucrative game quite so easily. Just two months of reduced activity in December and January gave them the time they needed to make substantial progress towards restoring what they had lost. By late January, the volume of spam had already reached the levels recorded in September 2010, right before Bredolab was shut down.
Spammers had no hope of getting things up and running again in early January. At that time of year, during the extended New Year’s holidays, many infected machines were turned off, which led to a palpable reduction in the amount of spam between the 01 and 10 January. On several of those days, the volume of spam in the total email traffic fell by a factor of five.
The distribution of email threats detected by antivirus programs in various countries in early 2011 also looks typical in terms of numbers, with users in developed, highly-computerized countries again receiving malicious code by mail more often, while users in eastern European countries are less frequently targeted.
In January, we saw quantitative spam indicators and spam categories stabilize.
In January, the amount of spam advertising Viagra rose again. A sharp jump was noted in early January when emails advertising pharmaceuticals accounted for one quarter of all spam traffic. However, it is also worth considering that at the beginning of the year, overall spammer activity was at a low point. It is altogether possible that this surge in pharmaceutical spam could be explained by the botnet owners taking some time off. It seems as though many holidaying botnet controllers programmed their bots to send out mass mailings of pharmaceutical spam without worrying about searching for new solutions or clients. At the end of the long winter holiday, the percentage of spam advertising pharmaceuticals again saw a gradual decline. By the end of the month, this spam category amounted to just 13.5% of all spam mailings, although that number is still 4 percentage points higher than the mid-month average for December.
A third quiet month — February — was marked by a continued increase in the amount of spam in total email traffic (up by 1.1 percentage points) and an increase in the volume of spam sent from the US (total of 3.5%). Additionally, the number of threats detected in spam by email antivirus products in the US amounted to 10.6%.
Based on developments in 2010, we can draw one clear conclusion; inadequate and ill-planned anti-spam legislation only serves to create more favorable conditions for malicious users. The cybercriminals easily avoid liability by relocating from one country to the next. If there is any threat of a shutdown, they simply relocate their botnets. The key to improving the fight against an international evil like spam is to have a solid legislative base in place, and not just in a handful of developed countries, but right around the world — the Internet exists everywhere, after all.
By May, we expect to see spam traffic restored to the levels experienced in summer 2010. This is bound to happen — unless law enforcement agencies strike another blow against this criminal business.






















A Short, Sharp Shock for Spam