
It is clear that cybercriminals do not have any code of ethics. Consequently, even the most innocent are not exempt from a malicious attacker’s perspective, and are often used as a means to allow them to generate higher economic returns, in this case, through the abuse of clicks.
The following image provides clear evidence of this. Designed with an interface that’s “user friendly” for kids, this website invites you to download a threat detected by Kaspersky Lab as not-a-virus: AdWare.Win32.BHO.tbz.
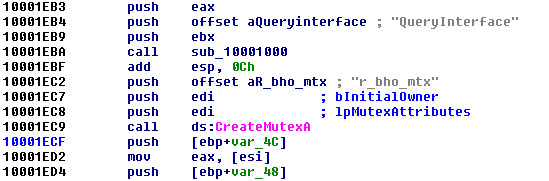
This adware registers a DLL file called iifebxxY.dll, detected by Kaspersky Lab as not-a-virus:AdWare.Win32.BHO.tca, and injects a malicious BHO (Browser Helper Object) into Internet Explorer. The name of this DLL is random, so the name may change. It also creates two mutexes with the names r_bho_mtx and ruleset_sync_mtx. This means that once infected the system, prevent malware infected again.
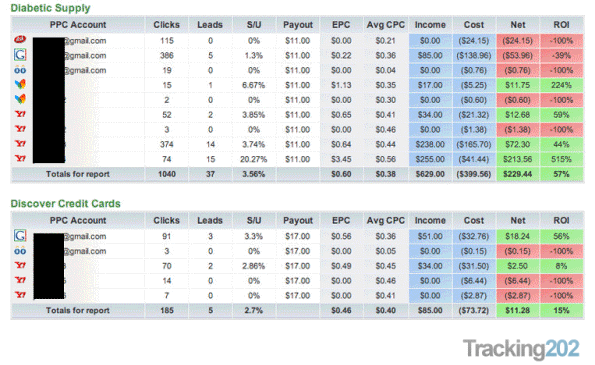
While on the face of it the adware programs are there to issue several publications, in reality they pose a serious risk. Usually behind these maneuvers are affiliate systems – on this occasion the PPC (Pay-Per-Click) programs DealsMint and Tracking202 [also known as Prosper202]. The above are used mutexes to prevent reinfection in the same computer and by the same cyber-criminal.
Business schemes that exploit such affiliate systems are not new. Basically, profits are generated by every click on certain web resources that make regular campaigns, so… the more clicks, the more profits.
Historically there have been legal disputes between anti-virus companies and organizations that are responsible for the development of adware programs, which is why these programs are often included under the generic term of “potentially dangerous application”, or “undesirable applications”.
However, despite seemingly innocuous activity, the reality is that they are programs that have a fundamental role in cyber-business, and therefore they’re in great demand by cyber-criminals. For this reason, Kaspersky Lab is constantly monitoring such activities to provide security for users, not only directly in detection processes, but also through its ongoing research.




















The most innocent as vectors to increase the Pay-per-Click business