
Executive summary
The Cybercrime Ecosystem is a series of articles explaining how cybercriminals operate, what drives them, what techniques they use and how we, regular Internet users, are part of that ecosystem. The articles will also cover technical details and up-to-date research on the threat landscape to provide a more realistic understanding of why this is a problem and how we can prevent it.
This article describes current problems with cybercriminals infecting websites with malicious code. It is very common to see cybercriminals exploit vulnerabilities in blogging software such as WordPress and Joomla! for injecting their malicious code. This is very effective, as many blogs are allowlisted, are not detected as suspicious websites by anti-virus software and get a lot of traffic. In my research, I decided to investigate this further and see what the current threat landscape looks like by researching the most visited blogs in Sweden.
In my research, I noticed that the majority of the blogs were running outdated versions of not just the WordPress core, but plugins, too. Their vulnerabilities would allow both authenticated and unauthenticated users to execute system commands, inject malicious code, such as JavaScript, and perform SQL injections to get access to the database. Please note that none of the vulnerabilities have been verified; they are simply based on the publicly available version number identified in the research.
Introduction
Attacking websites and infecting them with malicious code is probably one of the most common types of attacks by cybercriminals. It will allow criminals to perform multiple attacks against visitors to the website. They can basically control all the visitors and redirect their browsers to any website they want, while the visitor may not be aware it is happening. The link to the infected website can be sent by email, in a personal message on a social media platform or any other common way.
By redirecting the visitors to a website under the criminals’ control, they can, for example, exploit vulnerabilities in the browser or other client software such as Java, Flash, Acrobat Reader, VLC, Microsoft Office and tons of others.
They can also redirect the user to scam/spam sites, for example, by tricking users into downloading a fake software update or scaring them to make them pay a ransom. Lately, we have also seen that criminals can utilize the browser itself for cryptocurrency mining, etc. or use it as a zombie in a larger botnet for denial-of-service attacks.
Cybercriminals can hack into blogs by using many different methods, such as exploiting software vulnerabilities or getting access to admin panels, getting remote access (SSH, telnet) with known or leaked passwords, or in some cases, even buying legitimate ads, poisoning these with malicious code, and displaying on the targeted website. This technique is called Malvertising.
I decided to look at the biggest CMS system (WordPress) and the top 50 biggest and most visited blogs in Sweden to see if they were vulnerable against any common and known vulnerabilities. Not all of the top 50 websites where running WordPress; some of them were running custom software or another CMS system. Another obstacle was that it was not possible to ascertain the exploitability of the identified vulnerabilities. I could only base my research on the version of the software/plugin they were running, whereas not all plugins disclose their version numbers, so this report is based only on the version numbers that I have been able to identify.
Tools and techniques used
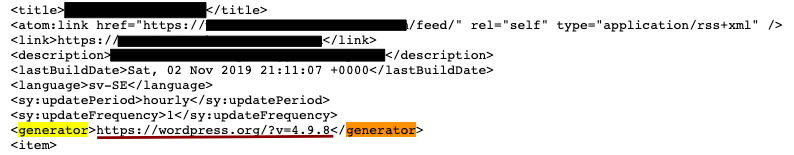
Determining the version number of a specific plugin or piece of software is straightforward enough: you simply need to look at the source code of the website and follow the links on the website. WordPress provides a few common methods of determining the version number: one of these is to see if the system has RSS (feeds) enabled. By accessing the feed, you also get the version number: it will have a
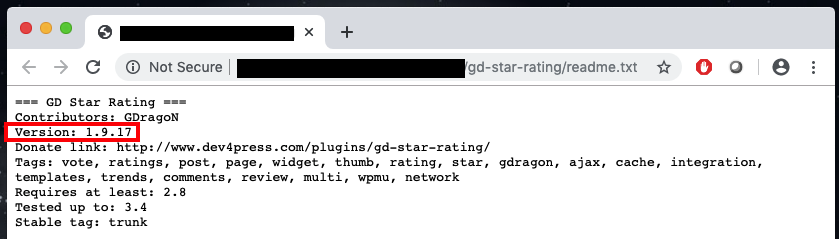
In addition to this, you can also start enumerating the plugins directory and see if there are any “readme” or installation notes. Most of the plugins have their version number written down in the readme/changelog/installation files or even print the version on the page.
Once the version number has been identified, there is a plenty of public resources you can use to check if that specific plugin is vulnerable to any known attacks. I used mainly two sources, which were www.exploit-db.com and www.wpvulndb.com.
To automate this process, I teamed up with the WPscan team who have a tool/API allowing users to scan WordPress sites and automatically query the wpvuldb.com database via a nice API to check if the identified plugins and versions are prone to any known vulnerabilities. I thank WPscan for their support in this project! It would have taken me much longer to do this manually.
Statistics
The results were very interesting: I noticed that the most visited blogs in Sweden where running outdated software. Thirty-seven percent of the top 40 blogs in Sweden where running an outdated version of WordPress, with the oldest version being from 2012, vulnerable to a lot of exploits—even full remote code execution allowing the attacker to compromise not just the WordPress installation, but the server it is running on, too. When checking the server hosting this extremely old WordPress installation, I found that 13 other websites were running on the same server. Most of the outdated WordPress installations where from 2018.
| RELEASE DATE | VERSION | VULNERABILITIES |
| 2012-06-27 | 3.4.1 | 41 |
| 2013-06-21 | 3.5.2 | 19 |
| 2016-06-21 | 4.3.5 | 19 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2018-08-02 | 4.9.8 | 11 |
| 2019-03-13 | 5.1.1 | 1 |
| 2019-06-18 | 5.2.2 | 8 |
| 2019-09-05 | 5.2.3 | 6 |
| 2019-09-05 | 5.2.3 | 6 |
Source: cvedetails.com and wpvulndb.com
Another interesting fact is that 55% of the researched sites where running the latest version of WordPress, and out of those systems, 50% had a plugin with a history of being vulnerable, but due to the fact that the version number could not be determined, we do not know if they are still vulnerable. Only four out of these 22 systems had vulnerabilities which were verified via the version number.
Spreading the malware
As mentioned before, this is a very common way for cybercriminals to spread malware, but how does it work in real life? After the WordPress site is compromised, the most common technique is to redirect the user to a so-called exploit kit. This is a system which will enumerate the browser, and if a list of requirements is met, deliver the malicious payload to the victim. For example, some of the requirements may be to exploit a certain browser only, if the exploit kit only has exploits for Firefox. In that case, nothing will happen if you visit the website in Chrome or Internet Explorer.
More advanced exploit kits also enumerate certain users from certain countries, possibly even excluding certain IP addresses from known security companies, law enforcement agencies and other people. The exploit kit also keeps track of successfully infected victims, so the cybercriminals can easily perform their operations or sell access to the infected computers.
Exploit kits do not just deliver malware—they can deliver any payload, e.g. by simply redirecting a user to another website or displaying ads. You yourself may have been redirected to a survey or some kind of “amazing” offer. This could have been done using the same techniques as mentioned above.
Examples of recent and large attacks:
- https://www.kaspersky.com/blog/malicious-websites-infect-iphones/28493/
- https://securelist.com/whos-who-in-the-zoo/85394/
- https://securelist.com/largest-website-in-sweden-spreading-malicious-code/58250/
- https://www.tripwire.com/state-of-security/security-data-protection/cyber-security/thousands-compromised-websites-spreading-malware-via-fake-updates/
- https://news.drweb.com/show/?i=13388&lng=en&c=5
Database leaks
One of the biggest motivators for cybercriminals is financial gain, and although that does not apply to everyone—some attackers have political motivation, others just do it for the adrenaline—making money is still a strong incentive. The cybercriminal ecosystem is huge, and cybercriminals benefit from everything they compromise. Simple things, such as email databases, access to compromised systems or infected computers, email and password combinations, and a lot more are all sold on the black market.
Almost exactly one year ago, I wrote about how much stolen data was being sold on the black market.
Blogs are a goldmine for collecting user data, as they get a lot of visitors who, in many cases, maintain an account on the website to be able to comment on posts. Another reason is that it is very easy to perform social engineering attacks against the visitor, display a fake login page and trick the user into logging in to access “hidden” content.
However, cybercriminals can also exploit SQL injection vulnerabilities both in the WordPress core and many plugins that have these. The vulnerability will allow an attacker to query the underlying database, retrieve data from it, and in some cases, even modify and read/write files in the file system.
Fortinet has written a very good article on some of the SQL injection vulnerabilities they found a few months ago.
Are we doomed?
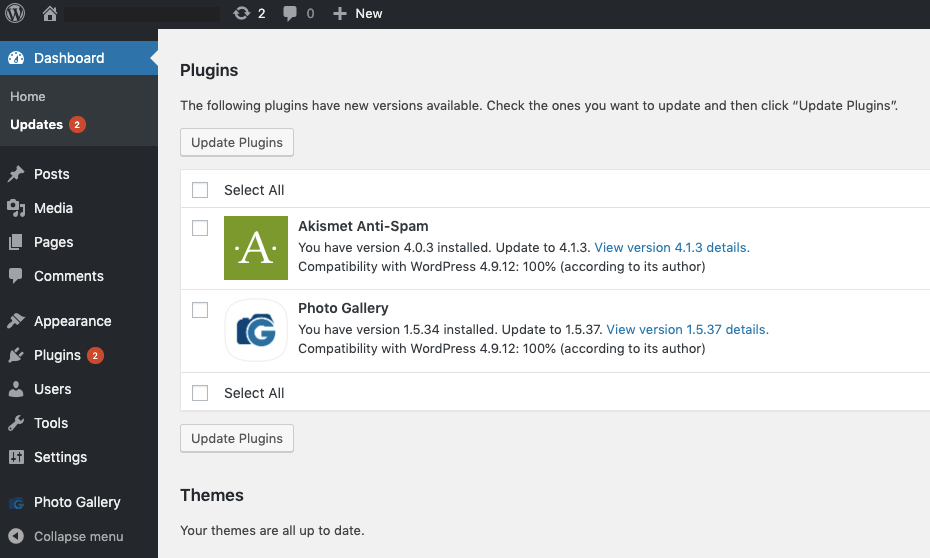
I personally think that this is not a problem we can blame on the technology, because if you look at, say, WordPress, the system is very good at informing you as an administrator that there are updates available. As you can see from the screenshot below, the available updates are shown in two places: Plugins and Dashboard, where WordPress core updates will show up as well.
One reason why the plugins or software is not updated might be that the current theme is not designed to work with the latest version of the plugin and might not function properly if the plugins are updated. Another reason might be that the people administrating the WordPress installation are marketing/PR agencies or web designers, who are only responsible for the layout, not security.
I think that anyone running a website should take a little more responsibility, not just for their brand, but for the systems they use, too. Regardless of whether you are an influencer, personal blogger or e-commerce website, it should be your best interest to ensure that you are not making the life of cybercriminals easy. If you are only a customer using these blogging platforms, please ask your provider what their policy is for making sure that the blog is secure.
As a regular Internet user, you need to make sure that you are securing your device and keeping your digital identity safe. A very good tip is to use protection against malicious code, which will identify and prevent these attacks even if the blog or website is infected.
You also need to ensure that you are not reusing your passwords on every site. One example of how you can create strong and unique passwords for every site, without using any additional software, can be found here.
Even if you do all of these, it is also very important that you make sure your device and any software installed on it is up to date with the latest security patches. Running the latest and secure versions makes a great difference.
I am also very glad that you took the time to read this article. It means that we are actually starting to make a difference, and the effort that we, security nerds, do reaches people such as yourself. Thank you and please share this knowledge with people who you believe might benefit from it. We cannot solve everything with technology, and we need to use our common sense and share knowledge among ourselves. We need your help with doing just that!






















The cybercrime ecosystem: attacking blogs