
This week has been one of the most hectic weeks in a very long time, I’ve been working day and night to finish everything for the Kaspersky Security Analyst Summit. I was not in the mood for new work because of the very late and hectic nights. I am on my way out from the door to drop off the kids and wife at her parents place and suddenly the phone rings, its Magnus Lindkvist, who was the Security Evangelist at Microsoft in Sweden. It is always nice to talk to Magnus, but this time he had a different tone on his voice, he was not really up for any chit chat, and just asked me if I was close to a computer. The mood for something exciting suddently just came back to me! I was in the game again! 🙂
As a security researcher, I always have at least one computer running 24/7, he tells me that the largest website in Sweden; Aftonbladet is spreading malware. I quickly up boot my virtual machine, launch Chrome and open the website. Nothing happen… what did I miss? Was Magnus joking? Then on the other side of the phone I hear Magnus say: “You need to use Internet Explorer”.
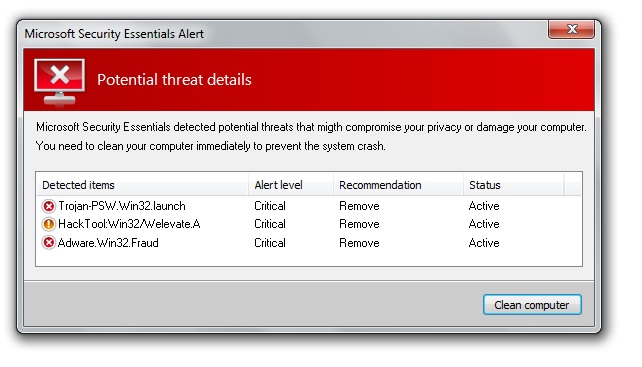
The malicious ad that was running on Aftonbladet also had a script to check the browser, probably to avoid false infections, and was only triggered when a user running Internet Explorer. When you visit Aftonbladet and you are using Internet Explorer you will get redirected to another website, hxxp://[CUT].windowsdefence-sn.nl on this page a static image of a fake warning from Microsoft Security Essentials that they have detected viruses on your computer, and you need to fix it. The picture is not really from the Microsoft Security Essentials tool, but something that the bad guys created to scare people that they are infected. This is a very common techniques by malware writers. When you click on the picture, you do not fix anything, you actually download the malicious file. The file was an obfuscated Visual Basic Executable and is still under analysis by us.
First I asked myself, is this really important? Because the malicious ad was removed very quickly from Aftonbladet, it was not exploiting any vulnerabilities, it was a “simple” social engineering attempt. But I think this is a very interesting and important story to tell. Most users today have the perception they need to visit shady websites to get infected, but look at what happened here, the largest website in Sweden was spreading malware, not because they got hacked, but because someone most likely bought or compromised the ads running on the website. Large websites often include content from other websites, and if the bad guys compromise any of those websites they can also manipulate the content which is getting included by the large website.
At the time of writing I do not know exactly what the malicious code is doing, but I still want to warn everyone about this! Please keep your protection up to date! I also want to encourage Aftonbladet to inform their readers if any of their sites are infected and spreading malicious code, and not just silently remove the malicious ad. This would help alot, because im pretty sure that there are alot of people out there now who ask themself if their computer is infected, and if the infection is still going on.
I really want to thank Magnus Lindkvist at Microsoft for reporting this to us!




















Largest Website in Sweden Spreading Malicious Code