
Whenever an important event takes place, new opportunities for cyber criminals, especially for those who develop
attacks based on social engineering, arise. Currently, the whole world has its eyes glued to TV screens watching the London 2012 Olympic Games. Worldwide interest on this event is so strong that cyber criminals were quick to take advantage of this opportunity and launched multiple campaigns promoting alleged paid online TV programming that would allow users to see live broadcasts of the Olympic Games via the Internet. Several fake pages were found with titles such as:
Best way to watch London 2012 Olympics online live stream HD
London 2012 Live Streaming

For this scam, cybercriminals create websites that are very appealing; some even look very professional that they make it seem that you are close to having access to live programming. At the instance you click on the link provided, you are redirected through a series of affiliate pages until finally the victim sees a site where they can make a payment of US$49.95 to start streaming live video of the Olympic Games:
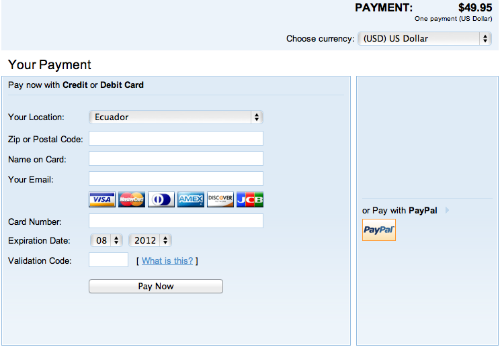
From July 22-30, Kaspersky Lab registered more than 80 malicious domains using this same fraud scheme.
Following are the statistics of some of these fraudulent domains involved in the campaign afore mentioned:
Total number of clicksredirected to fraudulent Olympic programming sites: 38,303.
Victims stem from 100 different countries. The greatest numbers of victims live in Indonesia and the United States.
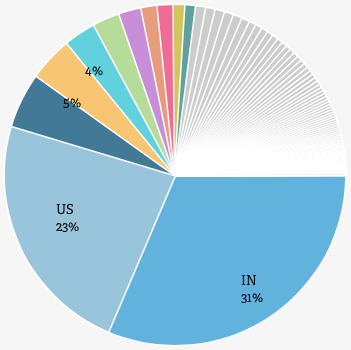
The campaign continues to be very active as on August 1st, when I wrote this post, there were 9,447 clicks, which correspond to almost the same number of potential victims.
Supposing that from all of the potential victims only 1% go through with the payment for the fraudulent TV programming, cybercriminals would make close to US$19,000 in profits. The actual figure may be higher.
A way that consumers can protect themselves from becoming a victim of these types of online scams is by learning about social engineering so they can recognize it and avoid falling into these traps. Also, the public should only visit official websites, such as http://www.london2012.com/, and the sites of established news organizations they know well and have been using for some time.





















Television Fraud of Olympic proportions