
Introduction
You’re on holiday at last! You remembered to pack everything you need, and of course you didn’t forget your laptop. After all, a computer is an essential everyday tool; you want to be able to organize and archive your photos and check your personal (and work!) email accounts while you’re away. The hotel at the resort offers WiFi Internet access; this was one of the deciding factors in choosing a hotel, because as everyone knows, it’s important to keep on top of things.
So you sit in your hotel room, open your laptop, activate the WLAN card and search for the hotel’s Internet network. There are several access points within range, and you choose the one which displays the hotel name in the SSID (Service Set Identifier). Once the connection’s established, the first page you’re shown is – as usual – a hotel login page asking the user to select a payment method. And as usual, the price is exorbitantly high. The hotel is charging 20 euros for 24 hours’ access – as much as you’d pay nowadays for an entire month’s worth of high-speed DSL access at home. But when you’re staying at a hotel you haven’t got a choice…or have you? There’s another access point within range which looks tempting, and it’s advertising high speeds and extra security, all for the ridiculously low rate of just 6 euros a day. Ever price-conscious, you connect, select credit card as your payment method and pleased with your bargain, you enter your credit card information.
In no time at all, you’ve got access to the big wide world via the Internet. You check your email, and then you decide to do a price comparison on the digital camera you saw on sale earlier that day. As usual, you compare the local price with those online. You find the local price is much higher than that offered by your preferred Internet retailer, so you decide to order it, thus ensuring that you’re optimally equipped for your next holiday. And again you pay by credit card, because it’s so convenient.
The scene above is typical and most people will be familiar with it at least to some extent. While one or two people might have security concerns about using an unknown access point, most people wouldn’t think twice. After all, what could possibly go wrong?
Although it seems as the answer is “nothing”, in fact there are significant risks lurking beneath the surface; they’re examined in more detail below.
Beneath the surface
What happened in the example above is known as a “man-in-the-middle” attack. Someone at the hotel created a simple login page, or copied the hotel’s own page, with the aim of presenting the user with something that looks like an official WiFi login screen. (Doing this doesn’t require much specialized knowledge. It’s even possible to emulate this type of access point using many commercially available WiFi routers and modified firmware or with a laptop that has WiFi activated and which is used to form part of an ad-hoc network.) Behind this page is an already logged-in Internet connection, designed to make the user think the login process is hassle free.
Any data entered can be harvested by the cybercriminals who set up the attack. One of the aims of such attacks is to gain access to credit card information; another is to gather additional account information for email accounts, online shops or financial institutions.
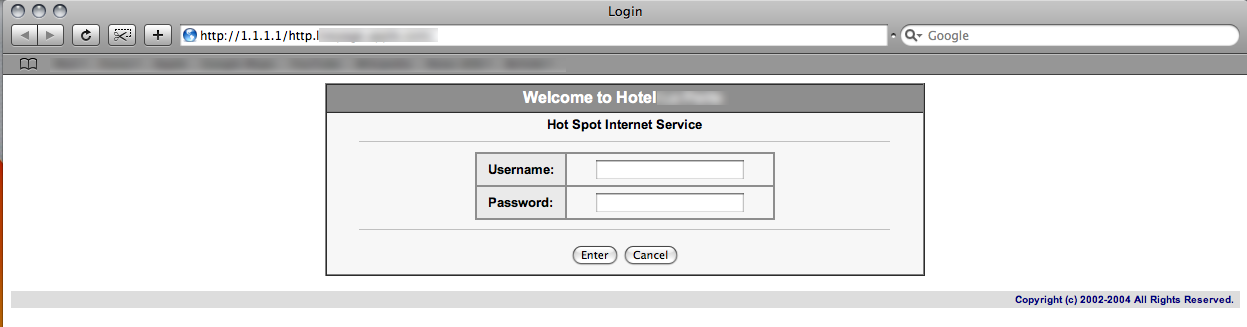
Figure 1: Hotel login page with pre-paid access
All the criminals have to do is wait – if even one victim takes the bait, their efforts will have been more than worthwhile. From a victim’s perspective, it would have been cheaper to pay the somewhat higher rate for the genuine WiFi connection provided by the hotel after all. However, even legitimate networks aren’t entirely risk-free.
As data is not transmitted via a physically restricted medium, it can be easily intercepted. Specially-designed programs can be used to fish data packets directly out of the air and – provided the packets are unencrypted – instantly and easily interpret them. The range within which this is possible depends on the strength of both the access point signal and the WiFi standard deployed. A commercially available WiFi router using the 802.11b standard has a range of almost 100 metres, with the signal emanating spherically from the device. Walls and other objects will reduce the radius of the signal, but the service won’t be limited to the building where the router is located. This usually means that information can be captured from outside the building, e.g. from the street.
The distance mentioned above, however, relates only to the network card’s internal antennae. Special aftermarket antennae are capable of receiving even very weak signals, thus considerably expanding their range, while microwave antennae can increase transmission distance by many times. Instructions for making such antennae yourself are available in multiple places on the Internet, and doing so requires the most basic of materials and very little effort.
Many of the programs known as sniffer programs also include functions for interpreting SSL-encrypted data; this means even the integrity of allegedly secure connections to login pages cannot be guaranteed. Depending on the strength of the encryption used, this may require a little more effort from the cyber criminals; effort they can put in while their victims, lulled into a false sense of security, perform online banking transactions and check their email.
Consequences
The potential consequences of falling for a man-in-the-middle attack depend on the actions performed by the user during this type of session.
In the example mentioned above, the login information for the email account accessed is first logged. This enables the account to be placed on a list of accounts which are then used to send spam. Having log in details to an account also means the attacker can sniff out other personal data stored in emails e.g. when users register with online shops, social networking platforms and online forums, they are usually sent an email containing their new access information. If the email account is a corporate one, the potential damage is much higher. If financial data is stolen, not only are the losses incurred extremely difficult to calculate, but it may, in some cases, take years to assess the precise total of the damage incurred. If an attack of this type results in confidential information – such as company reports, technical documentation or even customer data – being stolen and made public, the effect on the company’s reputation are usually catastrophic: loss of customer and partner confidence, sales slumps and even the collapse of business relationships. Particular caution is, therefore, advised whenever a work email address is used.
If credit card information falls into the wrong hands, the consequences can be particularly serious. The card details can be used to pay for goods and services all over the world – at the victim’s expense. This works until the victim becomes aware of the problem, which is often only at the end of the month when s/he receives a credit card bill. Normally the credit card company will reimburse the victim, provided there is proof that 1) you did not make the purchases yourself and 2) that you have not been grossly negligent with your credit card information. While the first point is usually resolved relatively easily, the second can be much more difficult to prove and is handled differently by each credit card company. Even if you are successful in getting your losses reimbursed, this can take a lot of time an effort. On the other hand, making a payment via an unsecured WLAN connection – whether this is done knowingly or unwittingly – could certainly be considered negligent or even reckless. In such cases, the costs are borne by the victim themselves – and this is usually an expensive lesson.
Most websites with a login area are secured using SSL. Although there are plenty of tools available a cybercriminal can use to crack – and read – this type of encryption, there is still some login information which remains hidden. There are, however, other means of accessing this information. Even before login information is transmitted to the Internet, it can be logged locally on the user’s computer using spyware or a simple keylogger. When a user logs into the putative hotspot site, it’s very simple to perform what’s known as a drive-by download. This involves placing JavaScript, an IFrame or a browser exploit, for example, in the HTML source code of an infected page; this will then download malicious code directly onto the victim’s computer. Infecting a machine with malware ensures that it remains open to cybercriminals, and the havoc which can be wrought by this type of program is limited only by the malware author’s imagination.
All this can happen in a matter of moments, without the user being aware that anything untoward is happening. This is in contrast to the past, when malware and network attacks were performed simply in order to wreak havoc. Back then it was sometimes possible to discern that something strange was happening, but that era is long gone. Today cybercriminals try to operate as stealthily as possible, giving them the chance to capture as much sensitive information as possible over a long period of time.
There are ways for users to protect themselves against such attacks. We will, therefore, first examine several options for encrypting and configuring the operating system, a strategy which can eliminate potential weak points on public networks.
Encrypting Data Traffic
The most effective method of encrypting data traffic is by using a VPN (Virtual Private Network). In simple terms, this involves setting up what is known as a VPN tunnel between the laptop (the client computer) and a destination point, or server. All traffic sent between these two points is encrypted, meaning that any intermediate devices processing or forwarding the traffic are unable to interpret the content. Moreover, all data traffic is processed via this route, thus bypassing any port blocks set up by the hotspot provider. Port 80, used for HTTP requests, is often one of the ports which is not blocked, while many other services, such as instant messaging or email via POP3 or IMAP, are blocked.
The VPN server acts as the connection target and must, therefore, be a trusted computer, one which is part of a secure environment. This server functions as the client computer’s “long arm”, making requests to target servers on the Internet and routing the desired content back to it in encrypted form. Users sign into the VPN using the classic username and password approach.
This type of VPN server can be set up in a number of different ways and anyone can do it, providing they have a little specialist knowledge. When it comes to choosing a location for the computer which is to function as a platform, there are basically three options:
A server can be a leased computer in a data centre. This applies to both physical and virtual servers. This option is particularly attractive to people who already use this kind of computer, for example as a host for their own email or web server. A static IP is also required (or the use of DynDNS if a dynamic IP is used), in order to be able to connect at any time. Virtual servers are a particularly attractive option, as these are available from as little as 10 euros a month and the VPN server service requires very little in the way of resources. It is, however, important to take into account the increase in traffic as, when using a VPN, all traffic is routed through it.
Alternatively, this service can also be performed by a home computer. Provided that you have a home broadband connection, such as DSL, with a flat-rate usage plan, you can add the external computer as part of your home network. This option also has the added advantage of allowing you to access your personal data at any time, provided that you have an appropriate means of doing so – either a computer with network shares which is kept switched on at all times or a NAS (Network Attached Storage) device.
VPNs are often provided by employers, particularly by those which permit teleworking or whose employees spend much of their time at customer sites. In such cases, companies provide VPNs to enable employees to perform work-related tasks, such as checking work email accounts or accessing network drives or company intranets from outside. Whether or not this service may also be used for non-work purposes varies from company to company – users should check the service’s terms of use or ask the service’s administrators.
Last but not least, there are a number of different service providers who offer VPN services for travellers. These companies provide servers which can be used to create secure VPN connections from around 10 euros per month. There are usually a range of tariffs available, with users choosing the one best suited to their needs. Here, too, the company’s terms and conditions of use must be taken into consideration.
While using a VPN does slow down transfer speeds, the advent of Draft N (which theoretically enables WiFi transfer speeds of 300 Mb/s) renders this negligible. This applies particularly in cases where no large volumes of data are to be exchanged.
A more independent alternative is provided by UMTS. This option enables users to access the Internet at any time independent of WiFi technology, provided that they are currently in an area which gets reception. Coverage is, however, available across large areas (between 60 and 90% of Europe currently gets reception, with the percentage varying according to country and metropolitan area). This is in complete contrast to hotspots, which, although they’re numerous, usually have only a small effective radius. This technology is now available relatively cheaply. From a monthly basic rate of 5 euros plus provider-dependent volume-based tariffs or around 30 euros a month for flat-rate use, this method of getting online is more than competitive, particularly when compared to the often extremely costs of hotel WiFi access. An additional advantage is that the cost is transparent from the outset, meaning you won’t be unpleasantly surprised by charges when you reach your holiday destination.
While the UMTS network is based on second-generation GSM for reasons of compatibility, third-generation GSM is also supported. This is preferable for security reasons, as the user and network authentication algorithms have been optimised. The transfer speeds, which can, theoretically, reach 14.6 Mb/s via HSDPA and HSUPA, are also more than adequate for most purposes.
UMTS is, therefore, likely to prove a welcome alternative to WiFi, particularly for frequent travellers, as the basic rates are calculated on a monthly basis rather than for shorter periods of time.
Basic Security Precautions
In addition to data encryption – performed mainly for security reasons – there are other factors that should be taken into account when configuring and equipping your own computer.
To facilitate the convenient exchange of data between computers, folders and files can be shared on a network. This means that these objects can be accessed from within the network, regardless of whether it is wireless or wired. Depending on how the shared items are configured, network users can either access them directly (with read and/or write permissions) or request access authorisation via a username and password. It is, therefore, essential that – after stocking up on music and other media for your holiday, as well as any internal company documents you may want to work on – you disable the sharing function once the data has been transferred. You wouldn’t want to be issuing an open invitation to all your network neighbours to browse your files! While many hotspot setups feature technologies designed to shield each computer from others on the network, there is no way to directly verify the presence of this function.
Although deactivating all shares considerably increases the level of data security, there is still the risk of a direct hacker attack which could render all data on the computer visible. While this is dangerous under any circumstances, it becomes even more so when sensitive data is involved. In order to further increase the level of protection specifically for this type of data, it should be backed up in encrypted form only to other storage media. There are even free programs available for this very purpose, distributed under the GPL (General Public License). These can be used to create encrypted container files that can only be opened with a password. The encryption used to create these containers is extremely strong – even a supercomputer would take years to crack it using the brute force method. a prerequisite for sufficiently strong security is, of course, a sufficiently strong password, which consists of more than eight characters and contains both upper and lower case letters, as well as numbers and non-alphanumeric symbols. Here, too, the same principle applies: this type of secured container should be opened only when required and closed again immediately afterwards. After all, even the securest of vaults is useless if the door is left open. As well as increasing the security of WiFi networks, taking such precautions also delivers another great advantage: if your laptop is lost, sensitive data will remain private.
It’s also very important to implement an effective Internet security solution. In addition to the basic functionality (protection against malware), the application area under discussion also requires network protection modules, specifically a firewall and a HIPS (Host Intrusion Prevention System). After all, what good is the most secure network connection if the source system itself has already been compromised? The program conducts complex analysis to evaluate unknown applications being run on the PC and provide a threat rating. This rating serves as a basis for the allocation of access rights to the programs. If an application is classed as suspicious, it will be given no, or limited, access to important resources such as the operating system, network, confidential data, system privileges or certain devices. This limits the possibility of infection by malicious code.
To many, it’s a source of exasperation: every few days, one of the installed programs – or the operating system itself – announces that a new update is available. Installing these updates invariably involves some waiting around, when all you wanted to do was catch up on the latest global news. One reason for users’ unwillingness to accept these updates lies in the fact that the changes made to the system through installing such updates are very rarely obvious to the user. However, these updates are designed to close security vulnerabilities in order to better protect the machine from attack. It is, therefore, important to be patient and to always install these updates – they are purely for your own protection.
Last but not least, technology doesn’t bear sole responsibility for improved security; users themselves should always be mindful of their activities. In this particular case, it is important to estimate the extent to which you can trust the WiFi network you’re connecting to. This is not always easy. As a rule, unfamiliar networks should always be regarded with a healthy dose of scepticism, for the simple reason that you have next to no control over how the data is transferred and who could potentially have access to it. This should enable you to deduce what you should and what you shouldn’t do. Sometimes, it’s just better to wait until you can access a more trustworthy network.
Conclusion
The hotspot business is booming. Global sales are projected to increase from $969 million in 2005 to $3.46 billion in 2009. This strong increase is primarily due to the growing number of hotspots. While there were 100,000 of them in 2005, this figure is set to almost double in 2009, with the fastest-growing sector being the catering industry. While it’s major fast-food chains leading the field with large-scale WiFi installations, cafés and restaurants are also jumping on the bandwagon (www.itfacts.biz/revenue-from-wireless-hotspots-to-reach-969-bln-in-2005-346-bln-in-2009/4941). And it’s a trend which has been favourably received: in the USA, 25% of all adults (or 34% of all Internet users) use their laptops and a hotspot service to go online when they’re away from their homes or workplaces (www.itfacts.biz/34-of-us-internet-users-used-wifi-away-from-homework/11477). This development has also been encouraged by the laptop market, as the price of these devices has fallen sharply over the past few years. In fact, more laptops than desktop computers were purchased in 2008 – the first time this has ever happened.
Unfortunately the methods currently available for encrypting wireless data traffic often exceed user knowledge. There is, as yet, no such thing as a plug-and-play solution. Were such a solution to be introduced, it would need to be accepted and offered by the hotspot providers, and ultimately supported by operating systems. It is thus clear that, even once a standard has been developed, its success still depends on a large number of factors.
On the non-technical side, a good awareness of security issues is key to protecting your data and your system. If you can’t completely trust a network – which is usually the case with unfamiliar access points – you should always be very conscious of what sort of information you’re releasing to the “outside world”. You should never enter sensitive information, such as your login details for online banking or Paypal under such circumstances. It’s far better to be a little overcautious than to end up with an empty bank account.
Ultimately, then, there are many factors involved in security. Nevertheless, it’s possible for anyone to considerably increase their level of security with relatively little knowledge and effort. Users need to research the issues at hand and to develop a nose for potential hazards – something which, in view of the risks and consequences, is more than worthwhile!























Summertime is Wireless Time