
While looking over some potentially malicious links from Brazil, I came across an interesting group of files. They were of varying sizes but had similar structures.

First I thought this was some type of steganography. The files has a jpeg extension, but were in fact bmp files in structure.
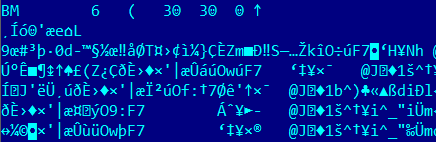
It was evident that they contained encrypted malware and some additional data. After further analysis, I discovered that this was a block cipher. As far as I know, this is the first time it has been used by malware writers anywhere in Latin America. This is what the malicious program looked like after decryption:
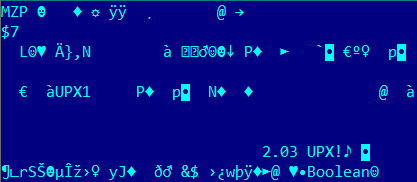
By using this technique, the virus creators kill several birds with one stone. Firstly, it may cause automatic malware analysis systems to function incorrectly: the file would be downloaded and analyzed by the antivirus program, and given the all-clear; with time the link will be exempted from checks altogether. Secondly, the
administrators of the sites where such encrypted malicious files are hosted won’t be able to identify them as malicious and will leave them as they are. Thirdly, some malware researchers may not have the time or necessary expertise to deal with them. All of this plays into the hands of the cybercriminals.
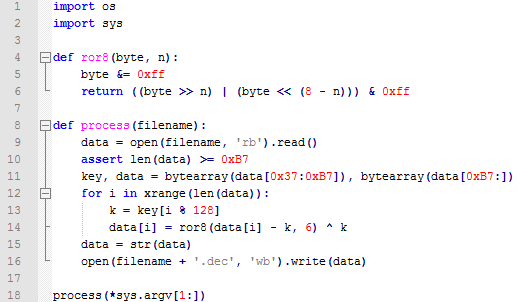
We have observed that the virus writers behind this specific attack publish new mirrors with the files and new malware every 2 days or so. So far, the encryption algorithm has been the same, but I’m sure it will be changed after this post is published. This is the decryption script for the current status:




















Steganography or encryption in bankers?